#cyberglossary search results
#CyberGlossary | The rising prominence and distribution of malware through infected files has become a significant challenge in the cybersecurity domain, much of it enabled by the deployment of malicious Dynamic Link Libraries (DLLs). Learn more about it here. More information…

#CyberGlossary | Evaluating organizational security posture is as critical as placing the necessary guards. Therefore, hospitals across the nation are utilizing Breach and Attack Simulation (BAS) to keep up with the evolving cyber domain. More information is available at:…

#CyberGlossary💡 | Cloud computing makes on-demand network access possible! The advantages are manifold, especially for those with limited resources. To explore further on cloud computing, download our report 'Accelerating Public Service Delivery through Cloud Adoption':…

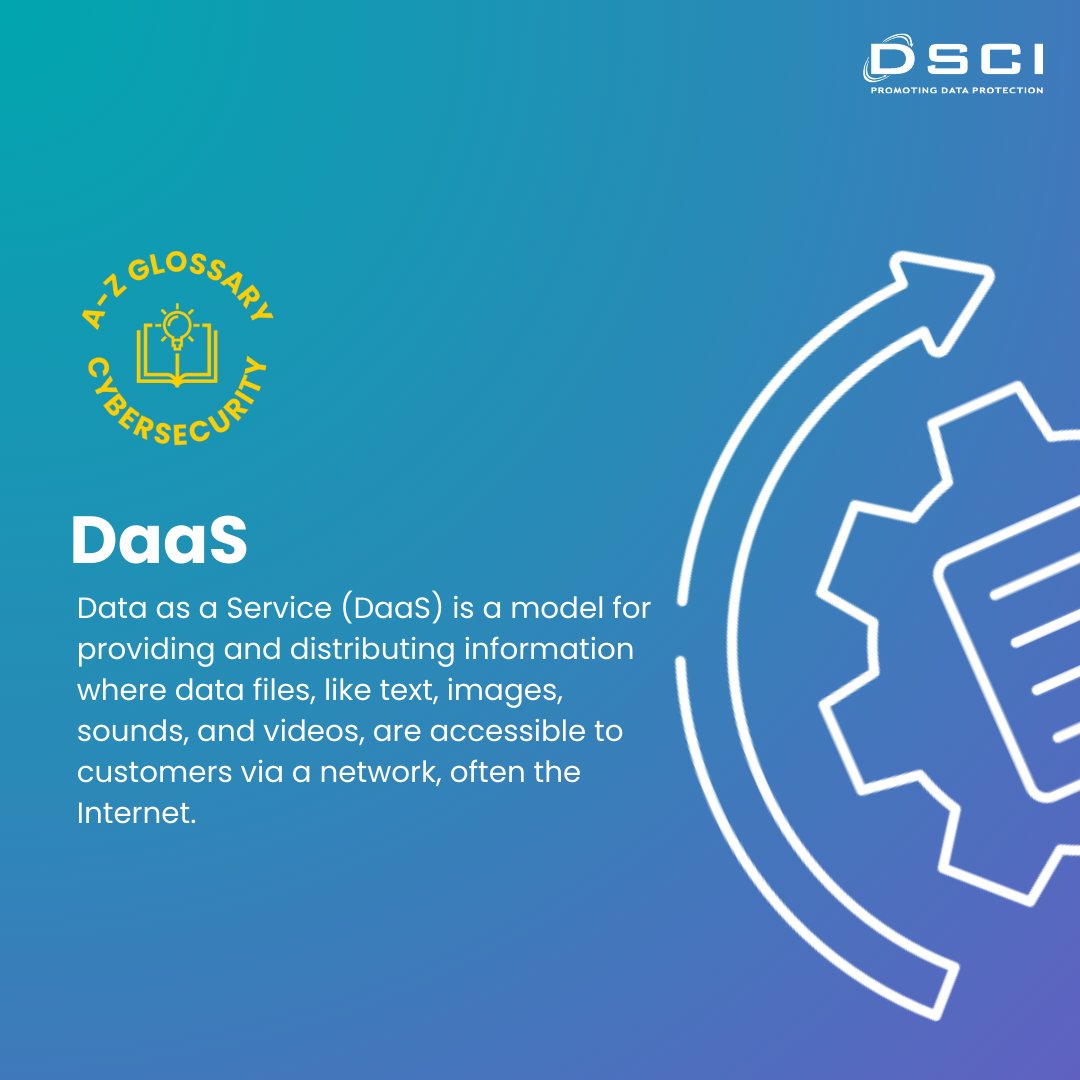
#CyberGlossary💡 | Familiar with Data as a Service (DaaS)? It is a cloud-based model that helps users access data on demand irrespective of the location! For comprehensive details on cloud service models and its implications, explore our report 'Accelerating Public Service…
What #MachineLearning? 📚 Explore our cyber glossary to read more about machine learning and it's role in your email security strategy. Learn more here: hubs.ly/Q02mCfnV0 #IRONSCALES #CyberGlossary
#CyberGlossary💡| Deep Learning, a subset of machine learning, is the force behind teaching computers to process data like humans do! More of this is detailed in the discussion here at: dsci.in/resource/conte… #cybersecurity #DSCI #DeepLearning #AI

Nuestro amigo Atom 🤖 está de regreso con un nuevo término de 🛡️ #Ciberseguridad, aprende lo que es un #Spyware añádelo a tu #CyberGlossary. Aprende más de #Ciberseguridad en todas nuestras redes sociales. #SomosTotalCyberSec 🌐
📩 ¡Cuidado con correos urgentes! #ElFraudedelCEO busca engañar. Verifica siempre y protege tu empresa. 🛡️💼 Encuentra todos los #CyberGlossary que #Atom tiene para ti en nuestras redes sociales. #TotalCyberSec #SeguridadEmpresarial
#CyberGlossary💡| Malicious inputs in the GenAI systems can cause disruptions in the LLM's functional potential. Read more here at: dsci.in/resource/conte… #GenAI #AI #DSCI #PromptInjection

#CyberGlossary💡| Convolutional Neural Networks feed on massive chunks of data and are crucial in pattern finding. More on deep learning algorithms is available at: dsci.in/resource/conte… #cybersecurity #DSCI #CNN #GenAI

#CyberGlossary💡| Migration to and delivery of cloud services brings us one step closer to better data control. However, data sovereignty here raises questions about the amount of control. To learn more, visit: dsci.in/resource/conte… #cybersecurity #DSCI #neuralnetworks #AI

#CyberGlossary | File-based encryption's offering of more granular control allows for better security and protected access. More information available at: dsci.in/resource/conte… #DSCI #FBE #IphoneForensics #CCITR #encryption

#CyberGlossary | The advent of machine learning has also introduced threats like Model Inversion Attacks, which exploit model outputs to infer sensitive data. More details are available at: dsci.in/resource/conte… #DSCI #AIThreats #CyberAttacks #MachineLearning

#CyberGlossary 💡| Jailbreaking exploits the system's restrictions to gain otherwise restricted access. Learn more on the details at: dsci.in/resource/conte… #cybersecurity #DSCI #jailbreaking #AI

#CyberGlossary | A backdoor attack is a vicious way to gain unauthorized access to systems while bypassing the existing security. More details are available at: dsci.in/resource/conte… #malware #cybersecurity #privacyrisks

#CyberGlossary | Edge computing's distributed computing model does give an edge, as it reduces latency while improving performance. More information available at: dsci.in/resource/conte… #DSCI #edgecomputing #dataprocessing #GenAI

#CyberGlossary | Data minimization is an important privacy principle that reduces the risk of data breaches and helps protect individuals' privacy. More information is available on: dsci.in/resource/conte… #DSCI #cybersecurity #dataprotection #privacy

#CyberGlossary | A standard industry protocol for delegation, OAuth enables users to share their information without passwords! To learn more on the subject, visit: dsci.in/resource/conte… #DSCI #cybersecurity #informationsecurity #OAuth

#CyberGlossary💡 | Recurrent neural networks are important in content generation due to their ability to generate desired outputs, making them highly sought after in speech recognition applications. To learn more, visit: dsci.in/resource/conte… #cybersecurity #DSCI…

#CyberGlossary | RCE is one of the biggest threats today when it comes to exploiting system vulnerability. More details on the subject are available at: dsci.in/resource/conte… #RCE #cyberattack #cybersecurity #remoteaccess

#CyberGlossary | The rising prominence and distribution of malware through infected files has become a significant challenge in the cybersecurity domain, much of it enabled by the deployment of malicious Dynamic Link Libraries (DLLs). Learn more about it here. More information…

#CyberGlossary | Edge computing's distributed computing model does give an edge, as it reduces latency while improving performance. More information available at: dsci.in/resource/conte… #DSCI #edgecomputing #dataprocessing #GenAI

#CyberGlossary | File-based encryption's offering of more granular control allows for better security and protected access. More information available at: dsci.in/resource/conte… #DSCI #FBE #IphoneForensics #CCITR #encryption

#CyberGlossary | The advent of machine learning has also introduced threats like Model Inversion Attacks, which exploit model outputs to infer sensitive data. More details are available at: dsci.in/resource/conte… #DSCI #AIThreats #CyberAttacks #MachineLearning

🔍👩💻 Dive into the world of cybersecurity with the TechCrunch Cyber Glossary! From APTs to Zero-Day exploits, get the definitions you need to navigate the complex landscape of tech. Stay informed and secure! 💡 #CyberSecurity #TechTerms #CyberGlossary 🚀✨……
#CyberGlossary | Evaluating organizational security posture is as critical as placing the necessary guards. Therefore, hospitals across the nation are utilizing Breach and Attack Simulation (BAS) to keep up with the evolving cyber domain. More information is available at:…

#CyberGlossary | Data minimization is an important privacy principle that reduces the risk of data breaches and helps protect individuals' privacy. More information is available on: dsci.in/resource/conte… #DSCI #cybersecurity #dataprotection #privacy

📩 ¡Cuidado con correos urgentes! #ElFraudedelCEO busca engañar. Verifica siempre y protege tu empresa. 🛡️💼 Encuentra todos los #CyberGlossary que #Atom tiene para ti en nuestras redes sociales. #TotalCyberSec #SeguridadEmpresarial
#CyberGlossary | Side-channel attacks pose a great threat to the hardware security of a system. It is therefore crucial to implement stringent measures to safeguard confidential data. More information is available on: dsci.in/resource/conte… #DSCI #cybersecurity #GenAI…

#CyberGlossary | A standard industry protocol for delegation, OAuth enables users to share their information without passwords! To learn more on the subject, visit: dsci.in/resource/conte… #DSCI #cybersecurity #informationsecurity #OAuth

Cyber Term Tuesday! Malware - A family of negative-acting software that includes spyware. #CyberTermTuesday #CyberGlossary #SecurityTerm #CyberTerms #Malware #Spyware

Cyber Term Tuesday! Key Logging - Monitoring or recording of keystrokes in order to obtain login credentials, for instance. #CyberTermTuesday #CyberGlossary #SecurityTerm #CyberTerms #KeyLogging

Cyber Term Tuesday! IP Address - A computer's inter-network address that is assigned for use by the Internet Protocol and other protocols. An IP version 4 address is written as a series of four 8-bit numbers separated by periods. #CyberTermTuesday #CyberGlossary #SecurityTerm

Hey #CyberSecurity enthusiasts! Want to up your tech lingo game? Check out The TechCrunch Cyber Glossary for all the latest jargon explained! 💻🔒 #TechTerms #CyberGlossary #TechCrunch ift.tt/p3Nqxrt: ift.tt/1WKadD3
Hey there! Thanks for reaching out. Here's a tweet for you: 🔒 Stay #cybersafe with The TechCrunch Cyber Glossary! Educate yourself on essential tech terms and improve your digital literacy. Emojis. #TechCrunch #CyberGlossary Feel free to let me know … ift.tt/L5e3kqJ
#CyberGlossary | A backdoor attack is a vicious way to gain unauthorized access to systems while bypassing the existing security. More details are available at: dsci.in/resource/conte… #malware #cybersecurity #privacyrisks

#CyberGlossary | RCE is one of the biggest threats today when it comes to exploiting system vulnerability. More details on the subject are available at: dsci.in/resource/conte… #RCE #cyberattack #cybersecurity #remoteaccess

Nuestro amigo Atom 🤖 está de regreso con un nuevo término de 🛡️ #Ciberseguridad, aprende lo que es un #Spyware añádelo a tu #CyberGlossary. Aprende más de #Ciberseguridad en todas nuestras redes sociales. #SomosTotalCyberSec 🌐
#CyberGlossary💡| Malicious inputs in the GenAI systems can cause disruptions in the LLM's functional potential. Read more here at: dsci.in/resource/conte… #GenAI #AI #DSCI #PromptInjection

#CyberGlossary 💡| Jailbreaking exploits the system's restrictions to gain otherwise restricted access. Learn more on the details at: dsci.in/resource/conte… #cybersecurity #DSCI #jailbreaking #AI

#CyberGlossary💡 | Cloud computing makes on-demand network access possible! The advantages are manifold, especially for those with limited resources. To explore further on cloud computing, download our report 'Accelerating Public Service Delivery through Cloud Adoption':…

#CyberGlossary💡 | Familiar with Data as a Service (DaaS)? It is a cloud-based model that helps users access data on demand irrespective of the location! For comprehensive details on cloud service models and its implications, explore our report 'Accelerating Public Service…

#CyberGlossary | Evaluating organizational security posture is as critical as placing the necessary guards. Therefore, hospitals across the nation are utilizing Breach and Attack Simulation (BAS) to keep up with the evolving cyber domain. More information is available at:…

#CyberGlossary | The rising prominence and distribution of malware through infected files has become a significant challenge in the cybersecurity domain, much of it enabled by the deployment of malicious Dynamic Link Libraries (DLLs). Learn more about it here. More information…

#CyberGlossary💡| Deep Learning, a subset of machine learning, is the force behind teaching computers to process data like humans do! More of this is detailed in the discussion here at: dsci.in/resource/conte… #cybersecurity #DSCI #DeepLearning #AI

#CyberGlossary💡| Migration to and delivery of cloud services brings us one step closer to better data control. However, data sovereignty here raises questions about the amount of control. To learn more, visit: dsci.in/resource/conte… #cybersecurity #DSCI #neuralnetworks #AI

#CyberGlossary💡| Malicious inputs in the GenAI systems can cause disruptions in the LLM's functional potential. Read more here at: dsci.in/resource/conte… #GenAI #AI #DSCI #PromptInjection

#CyberGlossary | A backdoor attack is a vicious way to gain unauthorized access to systems while bypassing the existing security. More details are available at: dsci.in/resource/conte… #malware #cybersecurity #privacyrisks

#CyberGlossary | The advent of machine learning has also introduced threats like Model Inversion Attacks, which exploit model outputs to infer sensitive data. More details are available at: dsci.in/resource/conte… #DSCI #AIThreats #CyberAttacks #MachineLearning

#CyberGlossary💡 | Recurrent neural networks are important in content generation due to their ability to generate desired outputs, making them highly sought after in speech recognition applications. To learn more, visit: dsci.in/resource/conte… #cybersecurity #DSCI…

#CyberGlossary 💡| Jailbreaking exploits the system's restrictions to gain otherwise restricted access. Learn more on the details at: dsci.in/resource/conte… #cybersecurity #DSCI #jailbreaking #AI

#CyberGlossary💡| Convolutional Neural Networks feed on massive chunks of data and are crucial in pattern finding. More on deep learning algorithms is available at: dsci.in/resource/conte… #cybersecurity #DSCI #CNN #GenAI

#CyberGlossary | RCE is one of the biggest threats today when it comes to exploiting system vulnerability. More details on the subject are available at: dsci.in/resource/conte… #RCE #cyberattack #cybersecurity #remoteaccess

#CyberGlossary | File-based encryption's offering of more granular control allows for better security and protected access. More information available at: dsci.in/resource/conte… #DSCI #FBE #IphoneForensics #CCITR #encryption

#CyberGlossary | A standard industry protocol for delegation, OAuth enables users to share their information without passwords! To learn more on the subject, visit: dsci.in/resource/conte… #DSCI #cybersecurity #informationsecurity #OAuth

#CyberGlossary | Data minimization is an important privacy principle that reduces the risk of data breaches and helps protect individuals' privacy. More information is available on: dsci.in/resource/conte… #DSCI #cybersecurity #dataprotection #privacy

#CyberGlossary💡| Variational Autoencoder brings you more control over your latent representation while exercising the potential of Generative AI! More on the subject is available at: dsci.in/resource/conte… #cybersecurity #DSCI #VAE #GenAI

#CyberGlossary | Edge computing's distributed computing model does give an edge, as it reduces latency while improving performance. More information available at: dsci.in/resource/conte… #DSCI #edgecomputing #dataprocessing #GenAI

#CyberGlossary | Side-channel attacks pose a great threat to the hardware security of a system. It is therefore crucial to implement stringent measures to safeguard confidential data. More information is available on: dsci.in/resource/conte… #DSCI #cybersecurity #GenAI…

Cyber Term Tuesday! IP Address - A computer's inter-network address that is assigned for use by the Internet Protocol and other protocols. An IP version 4 address is written as a series of four 8-bit numbers separated by periods. #CyberTermTuesday #CyberGlossary #SecurityTerm

Something went wrong.
Something went wrong.
United States Trends
- 1. Cynthia 73.5K posts
- 2. #WorldKindnessDay 10.8K posts
- 3. #GrabFoodMegaSalexหลิงออม 788K posts
- 4. Good Thursday 34.8K posts
- 5. Larry Brooks 1,690 posts
- 6. RIP Brooksie 1,127 posts
- 7. #thursdaymotivation 2,342 posts
- 8. Michael Burry 10K posts
- 9. $MYNZ N/A
- 10. Taylor Fritz N/A
- 11. #thursdayvibes 3,221 posts
- 12. Tommy James N/A
- 13. #ThursdayThoughts 1,930 posts
- 14. Rejoice in the Lord 2,731 posts
- 15. Bonhoeffer 1,228 posts
- 16. Happy Friday Eve N/A
- 17. Bongino 5,396 posts
- 18. RIP Larry 1,412 posts
- 19. MEDICA 15.3K posts
- 20. Mollie 2,301 posts






