#cyberterms search results
Are you a Breacher’s Pet? Find out in today’s blog - buff.ly/3x68KZa - where we offer up some new cyber terms the world needs RIGHT NOW. And, if you have any additions to our list, drop them below. #Raxis #Cybersecurity #cyberterms #friday #infosec

They infiltrate a targeted network and stay dormant, waiting for the right time to create havoc. #cyberterms #cybersecurity #Cybertips

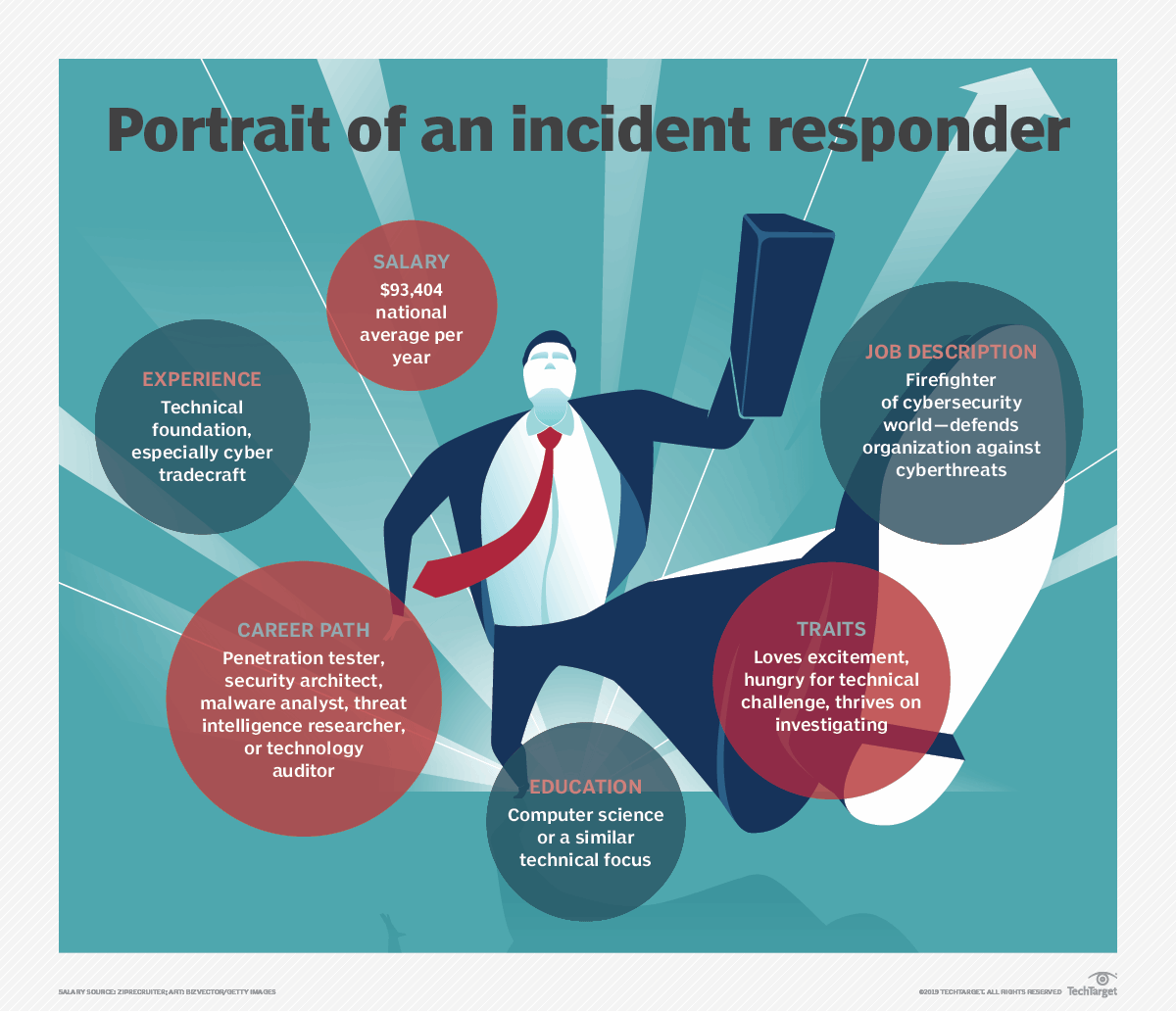
Love excitement and the thrill of hunting down #CyberThreats? Becoming an incident responder sounds like the job for you bit.ly/2RV3jsT #IncidentResponse #CyberTerms #Cybersecurity #DataSecurity #InformationTechnology
A database is information arranged for simple access, management, and amending. Computer databases mainly contain clusters of documents or files, like sales records, client information, financials, and product data. #CyberTerms

Let's review some key #cyberterms this month. Security attitute: the way you feel about making security judgment calls.
@martinmann_it | Know your phishing from your whaling? Don't panic! I do #harrogatehour - #cyberterms can leave you a little confused, that's why I speak in plain English martinmann.it

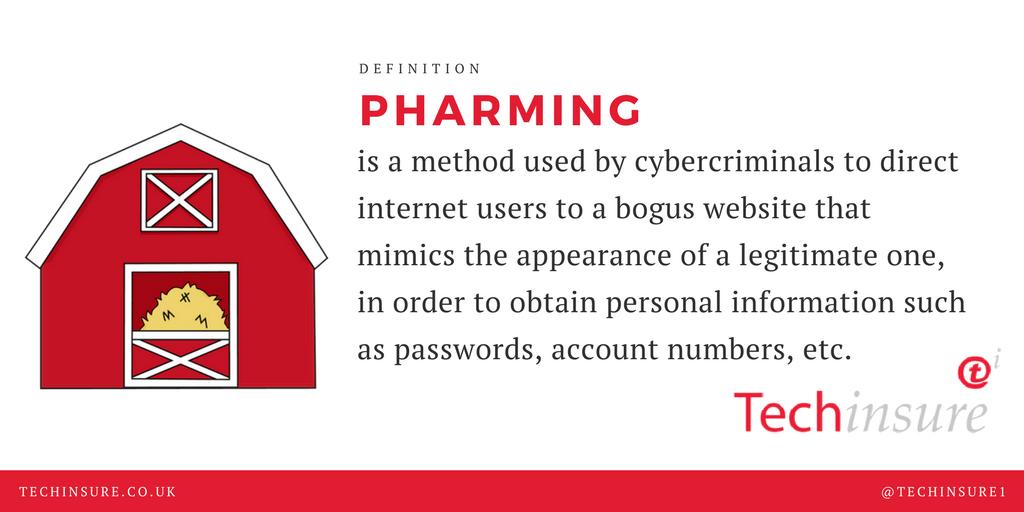
If you find that your Internet browser’s settings have changed on their own, including your selected search engine and default homepage, then you have got a #browserhijacker in your system. #cyberterms #cybersecurity

Do you know what a Distributed Denial of Service is or a 'DDOS'? #Techterms #Cyberterms #Cyberexplained

224 means "Today, Tomorrow, Forever." The number #224 is a cyber term used in text speak to express permanency in a romantic context. It is typically used when making a declaration of love and is often combined with other abbreviations to add emphasis #numbers #cyberterms
The term Antivirus is used a lot in the world of cyber and security but do you know what it refers to? Here is our simple definition! #Techtalk #Techterms #Cyberterms

The #KoreanRegister explains three #CyberTerms: Do you know what #ServiceSetIdentifier, #MACAddressAuthentication and #Sniffing mean? 📝ow.ly/XInz50ydb7m

#Security behaviors: actions and habits that individuals or organizations adopt to protect their digital and physical assets from harm or unauthorized access. #cyberterms #cybersecurity
The e-Glossary of #CyberTerms and #Hacking Lingo j.mp/2aIDE16 #english #cybersecurity #mediabodyguard #it

IAM isn't just keeping the bad actors out. An often-overlooked aspect of identity & access management is ensuring authorized users have timely access to needed resources . #cybersecurity #cyberterms #PCGL #IAM

A database is information arranged for simple access, management, and amending. Computer databases mainly contain clusters of documents or files, like sales records, client information, financials, and product data. #CyberTerms

#Security behaviors: actions and habits that individuals or organizations adopt to protect their digital and physical assets from harm or unauthorized access. #cyberterms #cybersecurity
Let's review some key #cyberterms this month. Security attitute: the way you feel about making security judgment calls.
Don’t fall victim to cyber attacks! Stay in the know by being aware of these common phrases and tactics. Download the FREE Cybersecurity Terms Cheat Sheet below! encompass.infusionsoft.app/app/form/click… #cybersecurity #cyberterms #staycybersafe #enableministrypartners

224 means "Today, Tomorrow, Forever." The number #224 is a cyber term used in text speak to express permanency in a romantic context. It is typically used when making a declaration of love and is often combined with other abbreviations to add emphasis #numbers #cyberterms

Are you a Breacher’s Pet? Find out in today’s blog - buff.ly/3x68KZa - where we offer up some new cyber terms the world needs RIGHT NOW. And, if you have any additions to our list, drop them below. #Raxis #Cybersecurity #cyberterms #friday #infosec

If you find that your Internet browser’s settings have changed on their own, including your selected search engine and default homepage, then you have got a #browserhijacker in your system. #Cyberterms #cybersecurity

If you find that your Internet browser’s settings have changed on their own, including your selected search engine and default homepage, then you have got a #browserhijacker in your system. #cyberterms #cybersecurity

If you find that your Internet browser’s settings have changed on their own, including your selected search engine and default homepage, then you have got a #browserhijacker in your system. #cyberterms #Cybersecurity

They infiltrate a targeted network and stay dormant, waiting for the right time to create havoc. #Cyberterms #cybersecurity #cybertips

They infiltrate a targeted network and stay dormant, waiting for the right time to create havoc. #cyberterms #cybersecurity #Cybertips

They infiltrate a targeted network and stay dormant, waiting for the right time to create havoc. #cyberterms #Cybersecurity #cybertips

An example of attack vectors are infected email attachments, malicious links, pop-ups. #Cyberattacks #cyberterms #cybertips

Are you a Breacher’s Pet? Find out in today’s blog - buff.ly/3x68KZa - where we offer up some new cyber terms the world needs RIGHT NOW. And, if you have any additions to our list, drop them below. #Raxis #Cybersecurity #cyberterms #friday #infosec

Love excitement and the thrill of hunting down #CyberThreats? Becoming an incident responder sounds like the job for you bit.ly/2RV3jsT #IncidentResponse #CyberTerms #Cybersecurity #DataSecurity #InformationTechnology

The #KoreanRegister explains three #CyberTerms: Do you know what #ServiceSetIdentifier, #MACAddressAuthentication and #Sniffing mean? 📝ow.ly/XInz50ydb7m

Do you know what a Distributed Denial of Service is or a 'DDOS'? #Techterms #Cyberterms #Cyberexplained

A database is information arranged for simple access, management, and amending. Computer databases mainly contain clusters of documents or files, like sales records, client information, financials, and product data. #CyberTerms

@martinmann_it | Know your phishing from your whaling? Don't panic! I do #harrogatehour - #cyberterms can leave you a little confused, that's why I speak in plain English martinmann.it

The e-Glossary of #CyberTerms and #Hacking Lingo j.mp/2aIDE16 #english #cybersecurity #mediabodyguard #it

224 means "Today, Tomorrow, Forever." The number #224 is a cyber term used in text speak to express permanency in a romantic context. It is typically used when making a declaration of love and is often combined with other abbreviations to add emphasis #numbers #cyberterms

The term Antivirus is used a lot in the world of cyber and security but do you know what it refers to? Here is our simple definition! #Techtalk #Techterms #Cyberterms

They infiltrate a targeted network and stay dormant, waiting for the right time to create havoc. #cyberterms #cybersecurity #Cybertips

If you find that your Internet browser’s settings have changed on their own, including your selected search engine and default homepage, then you have got a #browserhijacker in your system. #cyberterms #cybersecurity

An example of attack vectors are infected email attachments, malicious links, pop-ups. #Cyberattacks #cyberterms #cybertips

An example of attack vectors are infected email attachments, malicious links, pop-ups. #cyberattacks #cyberterms #Cybertips

They infiltrate a targeted network and stay dormant, waiting for the right time to create havoc. #cyberterms #Cybersecurity #cybertips

They infiltrate a targeted network and stay dormant, waiting for the right time to create havoc. #Cyberterms #cybersecurity #cybertips

Something went wrong.
Something went wrong.
United States Trends
- 1. #WWERaw 73.8K posts
- 2. Moe Odum N/A
- 3. Brock 39.9K posts
- 4. Bryce 20.9K posts
- 5. Panthers 37.5K posts
- 6. Finch 13.7K posts
- 7. Timberwolves 3,756 posts
- 8. Gonzaga 3,994 posts
- 9. Keegan Murray 1,433 posts
- 10. 49ers 41.7K posts
- 11. Canales 13.2K posts
- 12. #GMMTV2026 95K posts
- 13. Niners 5,854 posts
- 14. #FTTB 5,860 posts
- 15. TOP CALL 8,857 posts
- 16. Malik Monk N/A
- 17. Penta 10.5K posts
- 18. Alan Dershowitz 2,385 posts
- 19. Mac Jones 4,953 posts
- 20. Logan Cooley 1,159 posts