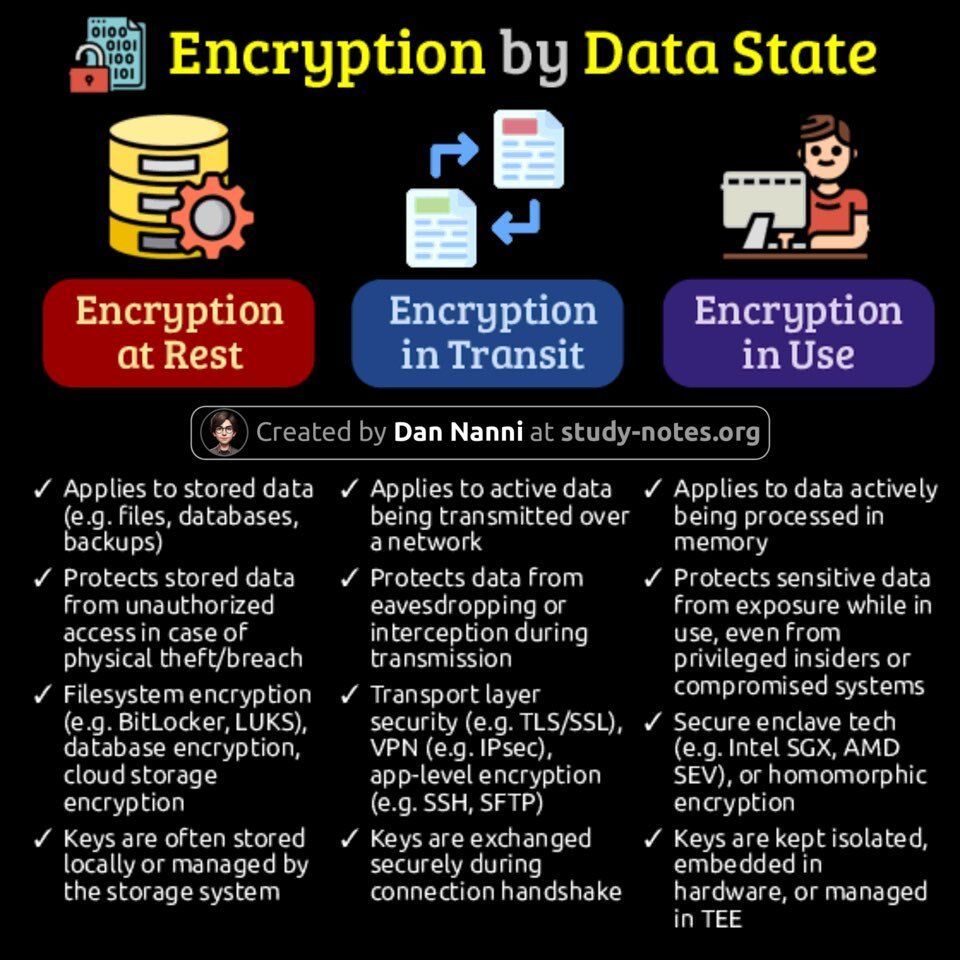
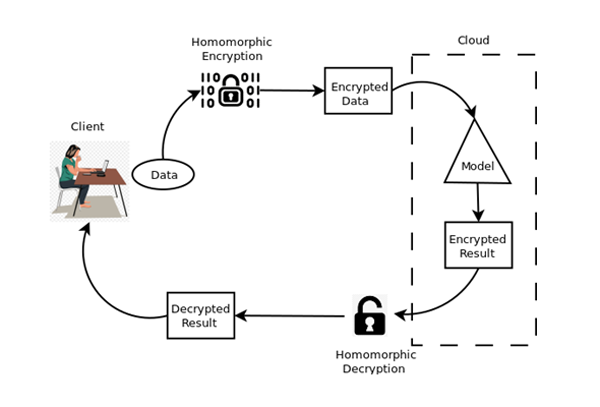
#encryption نتائج البحث
Advanced encryption and censorship-resistant platforms like Bitcoin show that even after bans, decentralized innovation empowers freedom more than ever before. #Decentralization #Encryption #DigitalFreedom
What is SHA-256, and how does it secure the digital world? 🔐 This powerful hashing algorithm keeps data safe & tamper-proof — from blockchain to everyday encryption. 💻 Learn how it works 👇 👉 101blockchains.com/sha-256-algori… #CyberSecurity #Blockchain #Encryption #SHA256 #Tech

Michigan lawmakers are undermining encryption, which protects everything from trade secrets to critical infrastructure. This could push businesses to move operations out of the state. #VPN #Encryption #Michigan
Travel is going digital, and so are the threats ✈️💻 Thales is securing the journey with #biometrics, digital IDs & post-quantum #encryption. Because trust shouldn’t stop at the border 🔐 Explore how 👇 thls.co/xZ2M50XkfF6
Homomorphic Encryption allows us to compute on ciphertexts as if we would do them on plaintexts, with the decrypted result matching the plaintext operations. It does refer to homomorphism in algebra. @Wipro bit.ly/2ZkvMwX RT @antgrasso #encryption
A personal journey with encrypted backups using rclone: secrary.com/posts/rclone/ #rclone #backup #encryption #ZFS

Gmic @SeismicSys fam 🎨 Hope the community doing fine 💕 Here’s the most fav Three Leaders of seismic encryption Family 💫 Hope they will like this what i draw. @NoxxW3 @BharatWormie @snow_blis @revvETH #seismic #seismicleaders #encryption
EU may force providers to scan all messages - even encrypted ones. As demand for real privacy grows, #STRTalk offers decentralized, full-privacy chats with no central point to scan or sell. Take back your communication: strtalk.net #Encryption
Making arts for @SeismicSys with Rocky is always fun 🤩 Here’s another art with Rocky …… evyerytime it turns out more interesting 😁👀 #seismic #rocky #encryption Magnitude is the key 🔑 @NoxxW3 @xealistt @heathcliff_eth

“These capabilities provide a secure environment, protect sensitive business information and maintain privacy.” @BizTechMagazine shares why SMBs should prioritize end-to-end #Encryption and 2FA for meetings. dy.si/jCVG5

Michigan lawmakers are undermining encryption, which protects everything from trade secrets to critical infrastructure. Normalizing VPN bans sets a dangerous precedent, potentially pushing businesses out of the state. #VPN #Encryption #Michigan
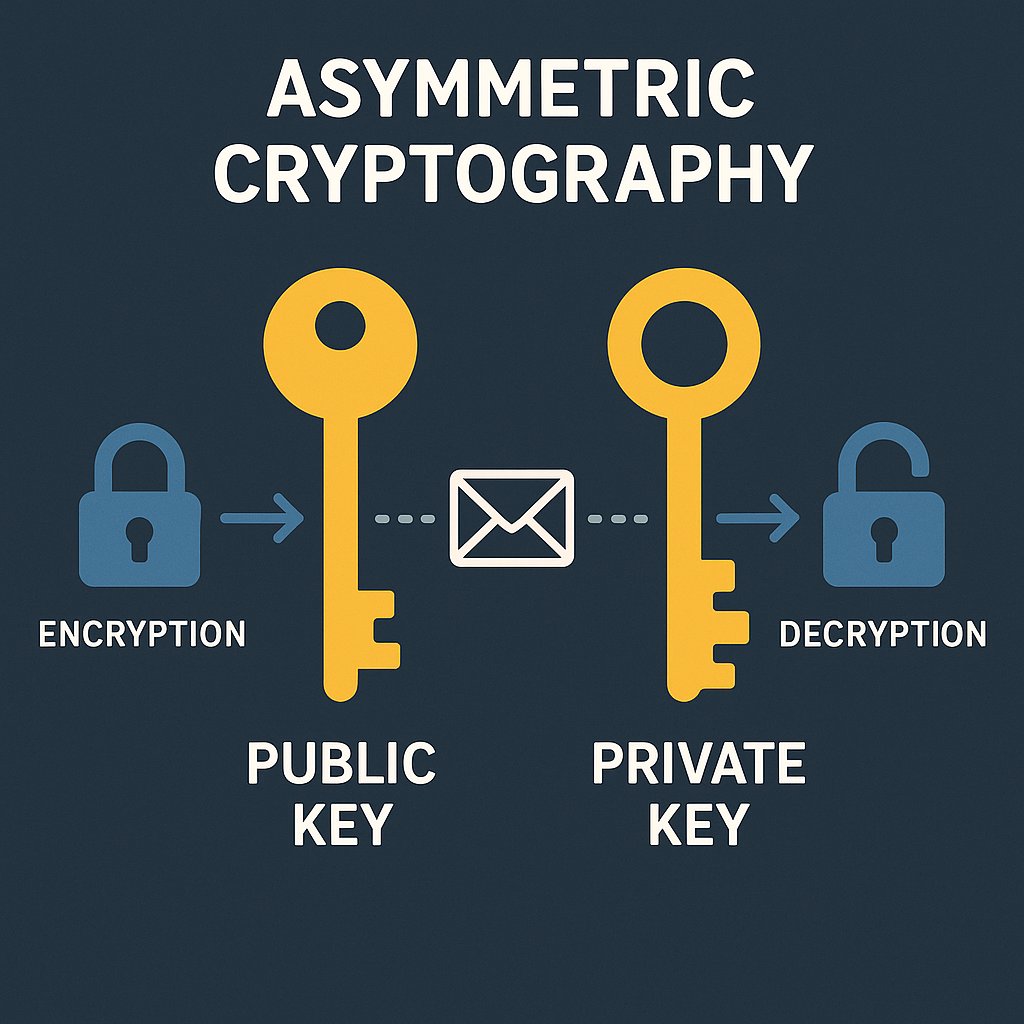
That is where it began! Asymmetric cryptography = two keys, one truth. Public key locks 🔒, private key unlocks 🔓. It’s how trust travels safely through the chaos of the internet. #Blockchain #Encryption #CyberSecurity
🔐 Every message you send and every transaction you make is protected by #cryptography. Explore how #encryption works and why it matters today 👉 capl.ink/48K5Qiy

TD Tech proudly presents Captain Firewall, hero of terminal security and encryption! Fear not the leaking or disruption of your valuable data, TD Tech's hero will protect your systems! #TDTech #Encryption #Protection #Security #DigitalTransformation

WhatsApp introduces passkey-encrypted backups, enhancing user security and reducing reliance on passwords. Stay protected with biometric authentication. #CyberSecurity #Encryption helpnetsecurity.com/2025/10/30/wha…
4. Trust without surveillance . Users stay protected, institutions stay compliant. It’s the balance the financial world has been missing. @heathcliff_eth @xplanettt #encryption #Gmic
Your emails say more than you think — protect them with encryption. 🔐 Learn how to lock down email communication in 2025: 🌐 cyberphore.com/secure-email-e… #CyberPhore #EmailSecurity #Encryption #CyberSecurity #InfoSec #PrivacyMatters #DataProtection

"if only there was a #chat app that had end-to-end #encryption, without phone numbers or any private data for registration, #decentralized, easy to use, with multi-profile and multi-device support and available in all platforms"

🔐 Every message you send and every transaction you make is protected by #cryptography. Explore how #encryption works and why it matters today 👉 capl.ink/48K5Qiy

“These capabilities provide a secure environment, protect sensitive business information and maintain privacy.” @BizTechMagazine shares why SMBs should prioritize end-to-end #Encryption and 2FA for meetings. dy.si/9BtHrA

“These capabilities provide a secure environment, protect sensitive business information and maintain privacy.” @BizTechMagazine shares why SMBs should prioritize end-to-end #Encryption and 2FA for meetings. dy.si/jCVG5

#encryption Let’s go team Europe 🇪🇺 Looking forward to reading results / outcome #acme

Thales and @cea_officiel are collaborating on post-quantum cryptography evaluations for the GIVERNY project, enhancing EU digital sovereignty. GIVERNY is a full-scale laboratory where FAEST and HAWK, two promising algorithms, are tested against real-world scenarios inspired by…

World’s first open-source P2P post-quantum E2E encrypted distributed messenger is coming. No servers. No control. No compromise. Just pure privacy. Stay tuned. The quantum-safe era of communication is about to begin. ⚡ #PostQuantum #Encryption #P2P #OpenSource #Cpunk

What is SHA-256, and how does it secure the digital world? 🔐 This powerful hashing algorithm keeps data safe & tamper-proof — from blockchain to everyday encryption. 💻 Learn how it works 👇 👉 101blockchains.com/sha-256-algori… #CyberSecurity #Blockchain #Encryption #SHA256 #Tech

EU may force providers to scan all messages - even encrypted ones. As demand for real privacy grows, #STRTalk offers decentralized, full-privacy chats with no central point to scan or sell. Take back your communication: strtalk.net #Encryption

Gmic @SeismicSys fam 🎨 Hope the community doing fine 💕 Here’s the most fav Three Leaders of seismic encryption Family 💫 Hope they will like this what i draw. @NoxxW3 @BharatWormie @snow_blis @revvETH #seismic #seismicleaders #encryption

In @idOS_network,every user holds their own encryption keys meaning even we can’t access or leak your data. Just like Signal can’t read your messages,idOS can’t read your data. Privacy by design,not by policy. #idOS #Web3Security #Encryption #كاريزما76
Rocky holds the key, Seismic holds the future.Magnitude is the key 🔐🪨 Created with love ❤️ hope it resonates #Encryption #Seismic @SeismicSys @NoxxW3 @xealistt

🖥️ When #QuantumComputers become commercially available, what was considered best-in-class #encryption will be easily cracked. Even now, threat actors are actively stealing encrypted data from organizations with the intention to break into it with quantum computers in coming…

Making arts for @SeismicSys with Rocky is always fun 🤩 Here’s another art with Rocky …… evyerytime it turns out more interesting 😁👀 #seismic #rocky #encryption Magnitude is the key 🔑 @NoxxW3 @xealistt @heathcliff_eth

Encryption keeps Ireland secure. Blacknight has joined organisations & experts calling on the Irish Govt to rethink plans to give Gardaí access to encrypted messages. #Encryption #CyberSecurity #DigitalRights #Ireland #Blacknight #KeepEncryptionStrong

Just before the coming holidays, Rocky proved unbreakable, neutralizing an attempt to tamper with encrypted data. Thanks to robust encryption, user data integrity remains 100% secure. Merry Xmas in advance! 🎉 Gmic: @SeismicSys @lyronctk #encryption #Web3 #เขมจิราต้องรอดseries

That is where it began! Asymmetric cryptography = two keys, one truth. Public key locks 🔒, private key unlocks 🔓. It’s how trust travels safely through the chaos of the internet. #Blockchain #Encryption #CyberSecurity

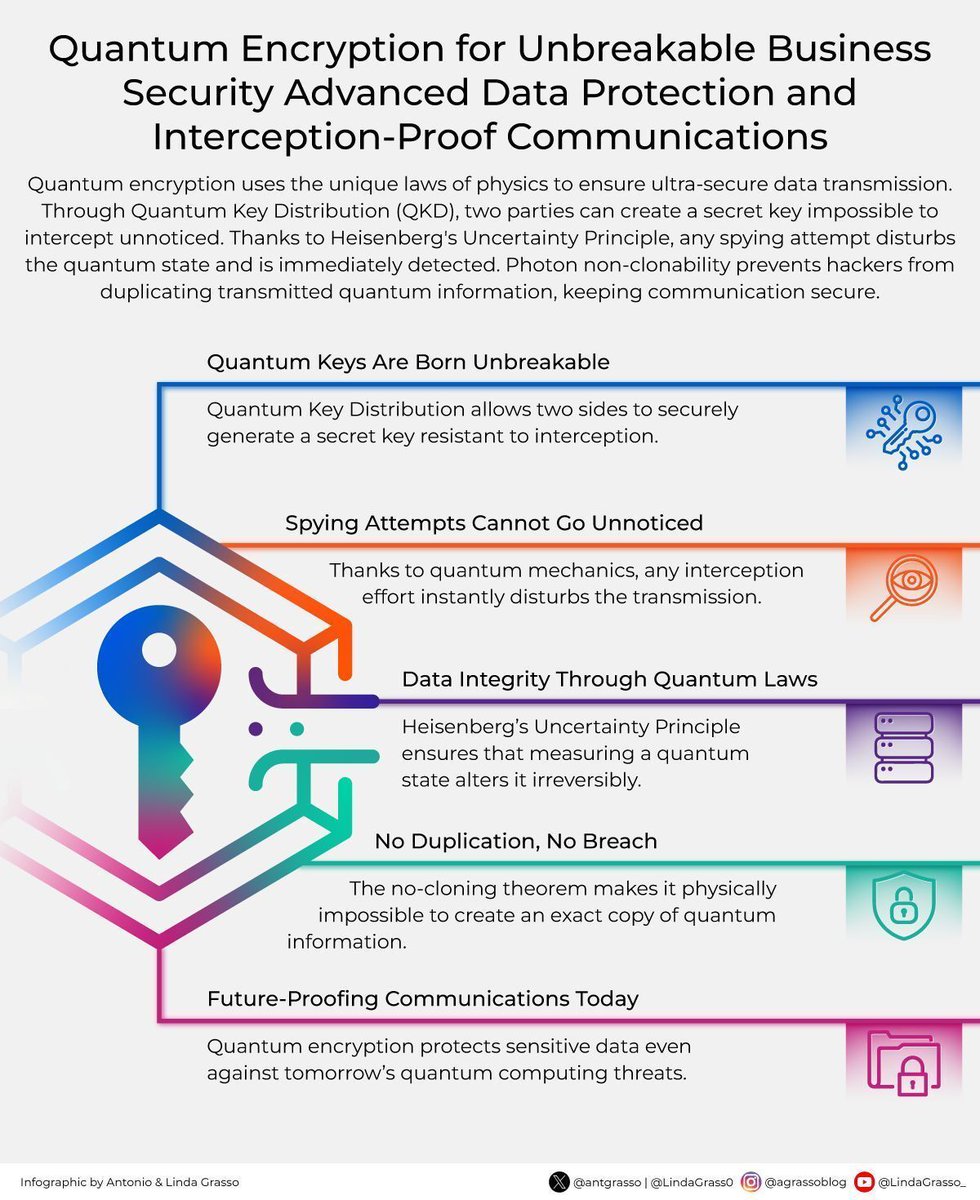
Quantum #Encryption for Unbreakable #Business Security by @antgrasso #CyberSecurity #Infosec #IT #Technology cc: @bernardmarr @marcusborba @JimMarous
Something went wrong.
Something went wrong.
United States Trends
- 1. Chris Paul 11.3K posts
- 2. Clippers 19.4K posts
- 3. Good Wednesday 23K posts
- 4. FELIX LV VISIONARY SEOUL 18.5K posts
- 5. #FELIXxLouisVuitton 21.8K posts
- 6. Pat Spencer 2,793 posts
- 7. jungkook 246K posts
- 8. rUSD N/A
- 9. Kerr 5,734 posts
- 10. Lawrence Frank N/A
- 11. Podz 3,394 posts
- 12. #ALLOCATION 255K posts
- 13. TOP CALL 9,665 posts
- 14. Shai 16.3K posts
- 15. Hield 1,624 posts
- 16. #JUPITER 152K posts
- 17. Jimmy Butler 2,692 posts
- 18. The BIGGЕST 274K posts
- 19. Seth Curry 5,279 posts
- 20. Carter Hart 4,278 posts