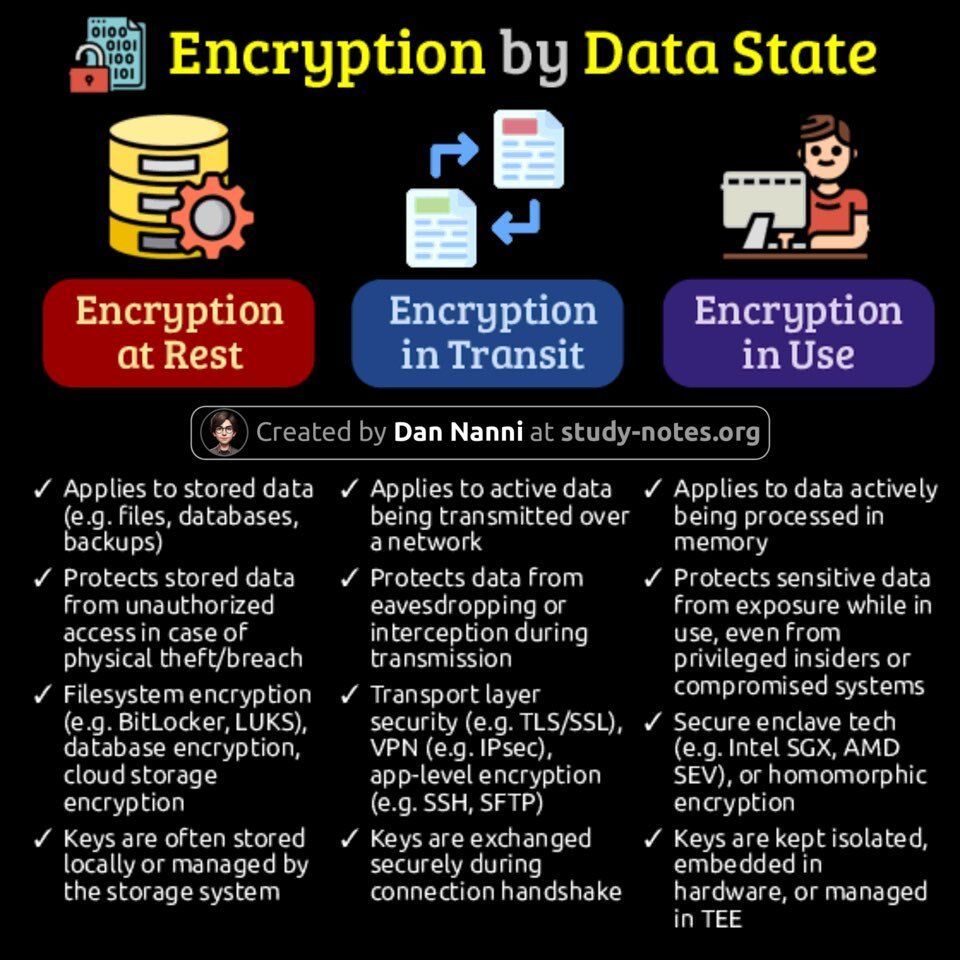
#encryption ผลการค้นหา
Michigan lawmakers are undermining encryption, which protects everything from trade secrets to critical infrastructure. This could push businesses to move operations out of the state. #VPN #Encryption #Michigan
Making arts for @SeismicSys with Rocky is always fun 🤩 Here’s another art with Rocky …… evyerytime it turns out more interesting 😁👀 #seismic #rocky #encryption Magnitude is the key 🔑 @NoxxW3 @xealistt @heathcliff_eth

Travel is going digital, and so are the threats ✈️💻 Thales is securing the journey with #biometrics, digital IDs & post-quantum #encryption. Because trust shouldn’t stop at the border 🔐 Explore how 👇 thls.co/xZ2M50XkfF6
What is SHA-256, and how does it secure the digital world? 🔐 This powerful hashing algorithm keeps data safe & tamper-proof — from blockchain to everyday encryption. 💻 Learn how it works 👇 👉 101blockchains.com/sha-256-algori… #CyberSecurity #Blockchain #Encryption #SHA256 #Tech

Advanced encryption and censorship-resistant platforms like Bitcoin show that even after bans, decentralized innovation empowers freedom more than ever before. #Decentralization #Encryption #DigitalFreedom
🔐 Encrypt AI training data and inference pipelines. Don’t let attackers see inside. #Encryption #AISecurity #DataPrivacy
Michigan lawmakers are undermining encryption, which protects everything from trade secrets to critical infrastructure. Normalizing VPN bans sets a dangerous precedent, potentially pushing businesses out of the state. #VPN #Encryption #Michigan
Homomorphic Encryption allows us to compute on ciphertexts as if we would do them on plaintexts, with the decrypted result matching the plaintext operations. It does refer to homomorphism in algebra. @Wipro bit.ly/2ZkvMwX RT @antgrasso #encryption
Gmic @SeismicSys fam 🎨 Hope the community doing fine 💕 Here’s the most fav Three Leaders of seismic encryption Family 💫 Hope they will like this what i draw. @NoxxW3 @BharatWormie @snow_blis @revvETH #seismic #seismicleaders #encryption
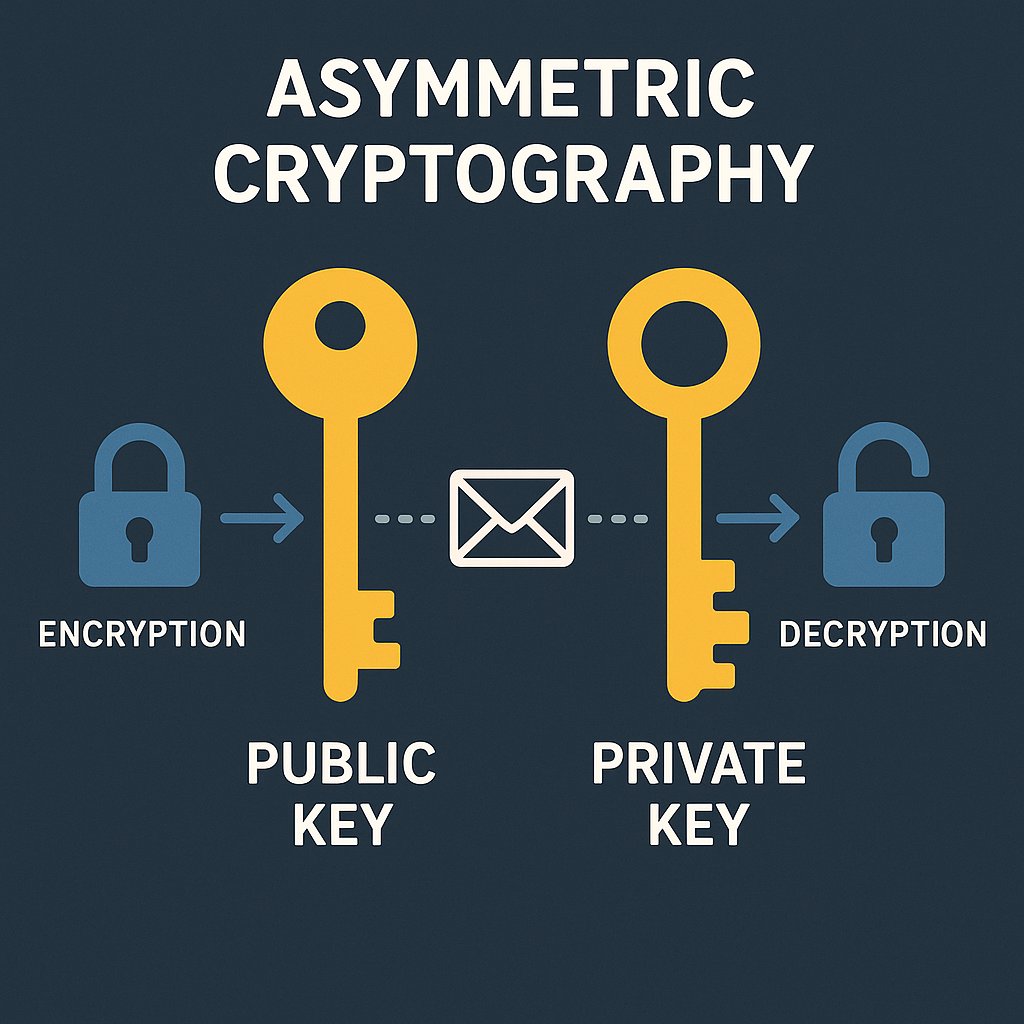
That is where it began! Asymmetric cryptography = two keys, one truth. Public key locks 🔒, private key unlocks 🔓. It’s how trust travels safely through the chaos of the internet. #Blockchain #Encryption #CyberSecurity
🔐 Encrypt AI training data and inference pipelines. Don’t let attackers see inside. #Encryption #AISecurity #DataPrivacy
Making arts for @SeismicSys with Rocky is always fun 🤩 Here’s another art with Rocky …… evyerytime it turns out more interesting 😁👀 #seismic #rocky #encryption Magnitude is the key 🔑 @NoxxW3 @xealistt @heathcliff_eth

INDUSTRY PERSPECTIVE: Encrypted Instrumentation Transforming Multi-Domain Training | Insight by Paul Averna | #encryption @CubicCorp Read now: bit.ly/48JaAVB

While #quantumcomputing threatens to break today’s #encryption, #QKD offers a promising #defence, allowing detection of any attempt to intervene in the #encrypted exchange: Shravishtha Ajaykumar or-f.org/35315
Lost USB? Keep all data encrypted and phone-unlocked: sovereignstore.io/product/istora… #CyberSecurity #Encryption #DataProtection
Good reminder, privacy should follow the user, not the platform. #Privacy #Encryption
Sending an email to someone outside Proton? You can still keep it end-to-end encrypted. Set a one-time password, share it separately, and you’re good.
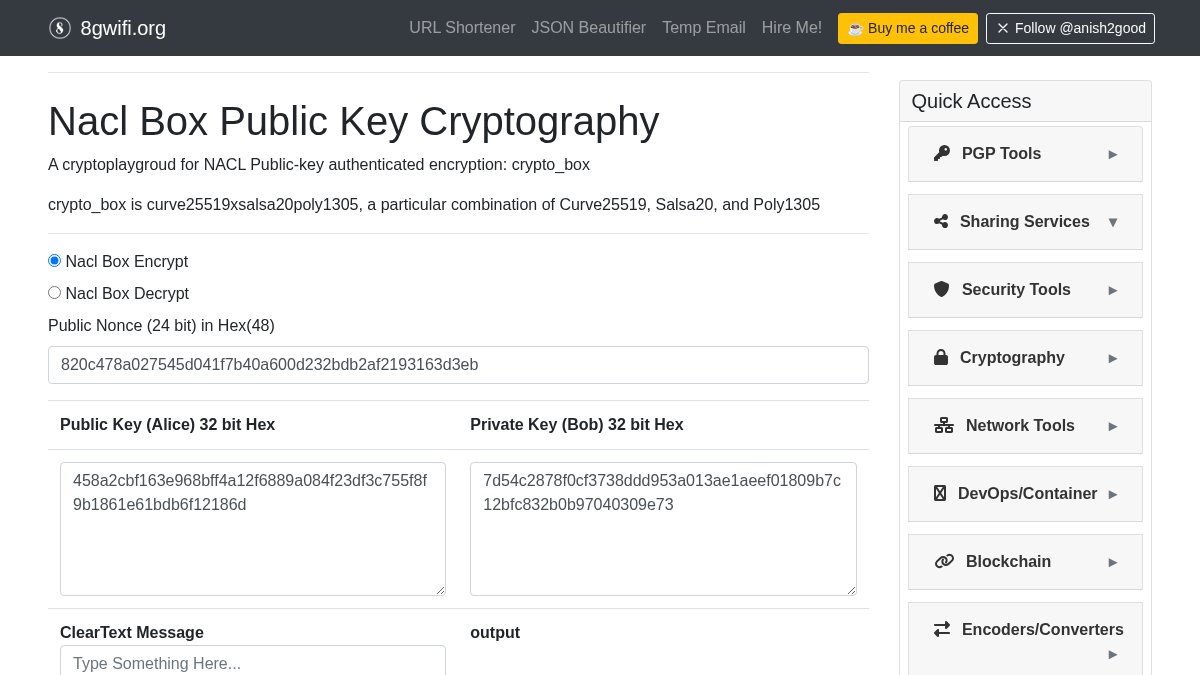
Explore the power of Nacl Box Public Key Cryptography for secure communication. Generate keys and encrypt/decrypt data effortlessly. Start protecting your information today! 🔒 Learn more: 8gwifi.org/naclboxenc.jsp #Cryptography #Encryption
The Quantum Countdown: Preparing Today for Tomorrow’s #Encryption Crisis by Aparna Achanta Tarnveer Singh @InfosecurityMag Learn more: bit.ly/45CPeb3 #CyberSecurity #InfoSec #IT #Tech #Technology

The Quantum Countdown: Preparing Today for Tomorrow’s #Encryption Crisis by Aparna Achanta Tarnveer Singh @InfosecurityMag Learn more: bit.ly/45CPeb3 #CyberSecurity #InfoSec #IT #Tech #Technology

🔒 BitLocker may be missing on some Windows editions, but fear not! VeraCrypt is here to save the day with open-source encryption for everything from folders to boot drives. Power users, rejoice! #Encryption #VeraCrypt #WindowsForum windowsforum.com/threads/veracr…
Explore Nacl Box Public Key Cryptography for secure communication. Easily encrypt and decrypt messages with the power of Curve25519, XSalsa20, and Poly1305. Protect your data today! 🔒 Try it: 8gwifi.org/naclboxenc.jsp #Crypto #Cryptography #Encryption

A personal journey with encrypted backups using rclone: secrary.com/posts/rclone/ #rclone #backup #encryption #ZFS

Homomorphic Encryption allows us to compute on ciphertexts as if we would do them on plaintexts, with the decrypted result matching the plaintext operations. It does refer to homomorphism in algebra. @Wipro bit.ly/2ZkvMwX RT @antgrasso #encryption

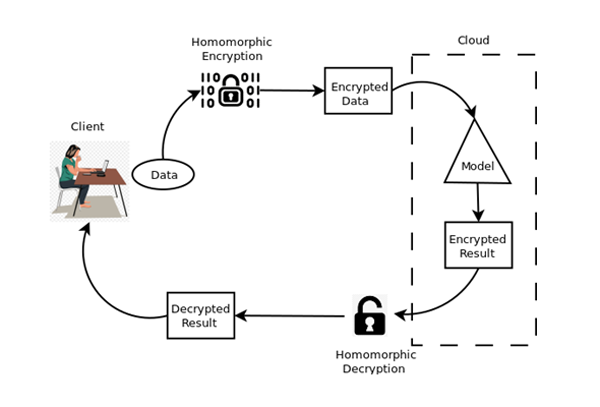
2/ What is Fully Homomorphic Encryption (FHE)? 🤔 Imagine a magic black box: You put encrypted data in, it computes, and an encrypted result comes out. No one—not even the box—sees the plain text data! That's FHE! #DataPrivacy #Encryption #TechExplained

We’re currently enhancing the security of our system with Futurecrypt (original encryption script by AOS – documentation will show how to use it). For obvious reasons, we’re keeping further details under wraps. #security #encryption #Futurecrypt #development @security…

Interesting perspective on the Zama Protocol Translator. While complexity exists, the potential for enhanced privacy and secure computation is significant. We look forward to seeing its evolution. #FHE #Privacy #Encryption
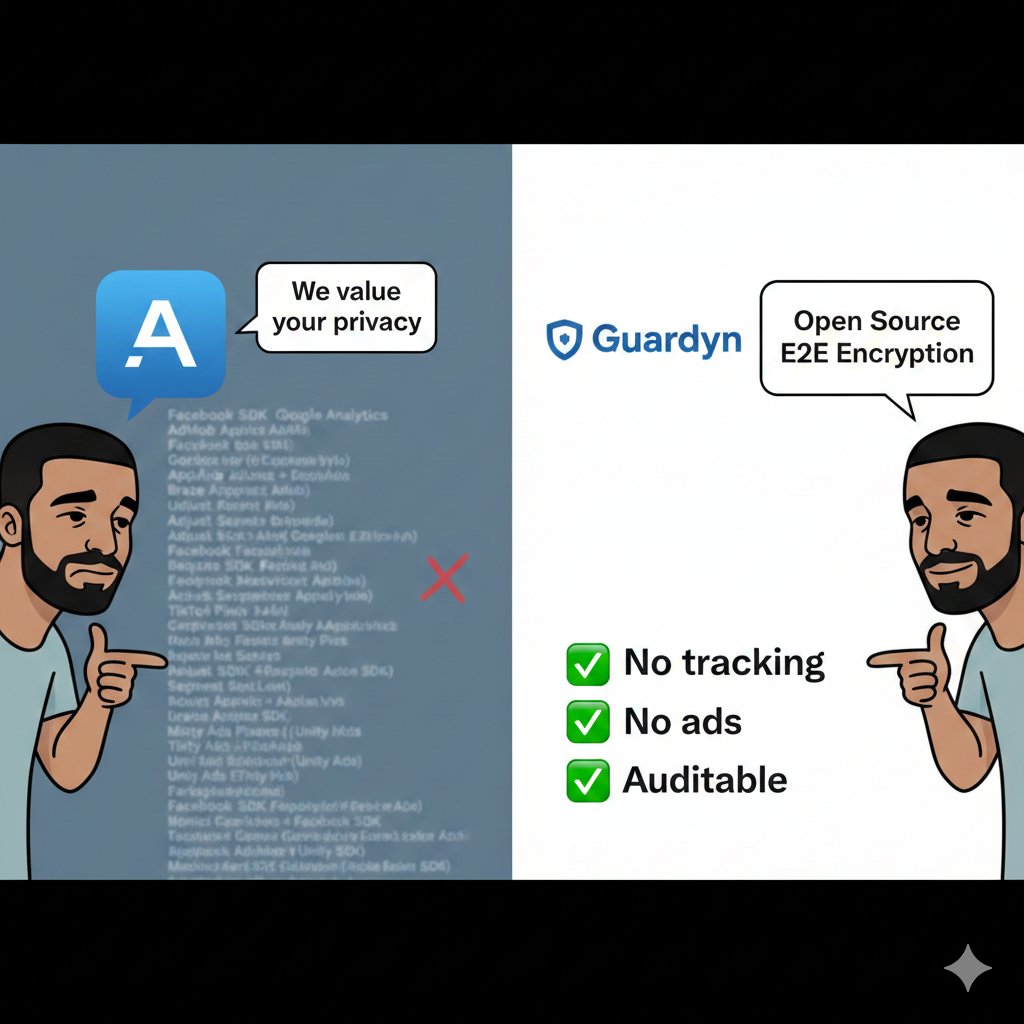
Every messaging app: "We value your privacy" 🙄 Also them: *sells your data to 47 ad networks* Guardyn: Actually E2E encrypted. Actually open source. Actually no tracking. Radical concept, I know. 🔗 guardyn.co #guardyn #privacy #encryption #securemessaging
Making arts for @SeismicSys with Rocky is always fun 🤩 Here’s another art with Rocky …… evyerytime it turns out more interesting 😁👀 #seismic #rocky #encryption Magnitude is the key 🔑 @NoxxW3 @xealistt @heathcliff_eth

What is SHA-256, and how does it secure the digital world? 🔐 This powerful hashing algorithm keeps data safe & tamper-proof — from blockchain to everyday encryption. 💻 Learn how it works 👇 👉 101blockchains.com/sha-256-algori… #CyberSecurity #Blockchain #Encryption #SHA256 #Tech

World’s first open-source P2P post-quantum E2E encrypted distributed messenger is coming. No servers. No control. No compromise. Just pure privacy. Stay tuned. The quantum-safe era of communication is about to begin. ⚡ #PostQuantum #Encryption #P2P #OpenSource #Cpunk

Gmic @SeismicSys fam 🎨 Hope the community doing fine 💕 Here’s the most fav Three Leaders of seismic encryption Family 💫 Hope they will like this what i draw. @NoxxW3 @BharatWormie @snow_blis @revvETH #seismic #seismicleaders #encryption

Rocky holds the key, Seismic holds the future.Magnitude is the key 🔐🪨 Created with love ❤️ hope it resonates #Encryption #Seismic @SeismicSys @NoxxW3 @xealistt

Just before the coming holidays, Rocky proved unbreakable, neutralizing an attempt to tamper with encrypted data. Thanks to robust encryption, user data integrity remains 100% secure. Merry Xmas in advance! 🎉 Gmic: @SeismicSys @lyronctk #encryption #Web3 #เขมจิราต้องรอดseries

In @idOS_network,every user holds their own encryption keys meaning even we can’t access or leak your data. Just like Signal can’t read your messages,idOS can’t read your data. Privacy by design,not by policy. #idOS #Web3Security #Encryption #كاريزما76
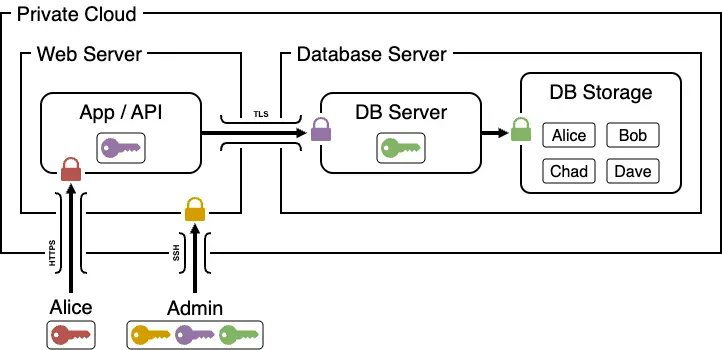
🖥️ When #QuantumComputers become commercially available, what was considered best-in-class #encryption will be easily cracked. Even now, threat actors are actively stealing encrypted data from organizations with the intention to break into it with quantum computers in coming…

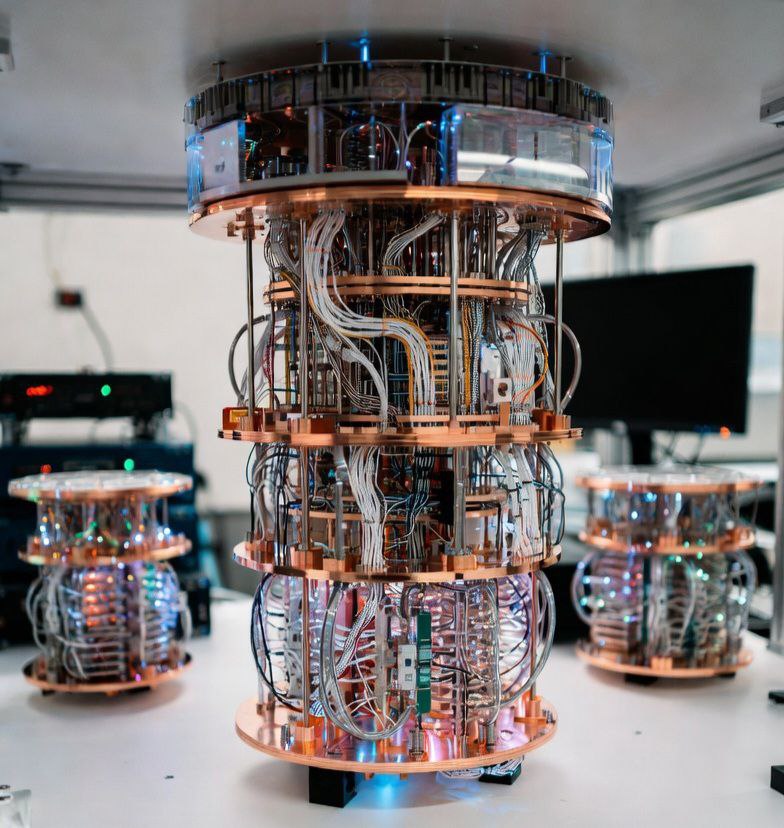
Did you know that quantum computing may threaten Bitcoin’s encryption and privacy? #quantum #encryption #Bitcoin
Something went wrong.
Something went wrong.
United States Trends
- 1. #ForTT_Telegram_sam11adel N/A
- 2. Broncos 47K posts
- 3. Mariota 13.1K posts
- 4. Ertz 3,113 posts
- 5. Happy New Month 194K posts
- 6. Commanders 33.2K posts
- 7. Bo Nix 10.1K posts
- 8. #RaiseHail 5,758 posts
- 9. Riley Moss 2,283 posts
- 10. #BaddiesUSA 26.2K posts
- 11. Treylon Burks 12.3K posts
- 12. Terry 20.3K posts
- 13. Bonitto 5,699 posts
- 14. Deebo 3,133 posts
- 15. Collinsworth 3,074 posts
- 16. #RHOP 12.5K posts
- 17. Sean Payton 1,646 posts
- 18. Chrisean 9,839 posts
- 19. Dan Quinn N/A
- 20. Zach Edey 3,160 posts