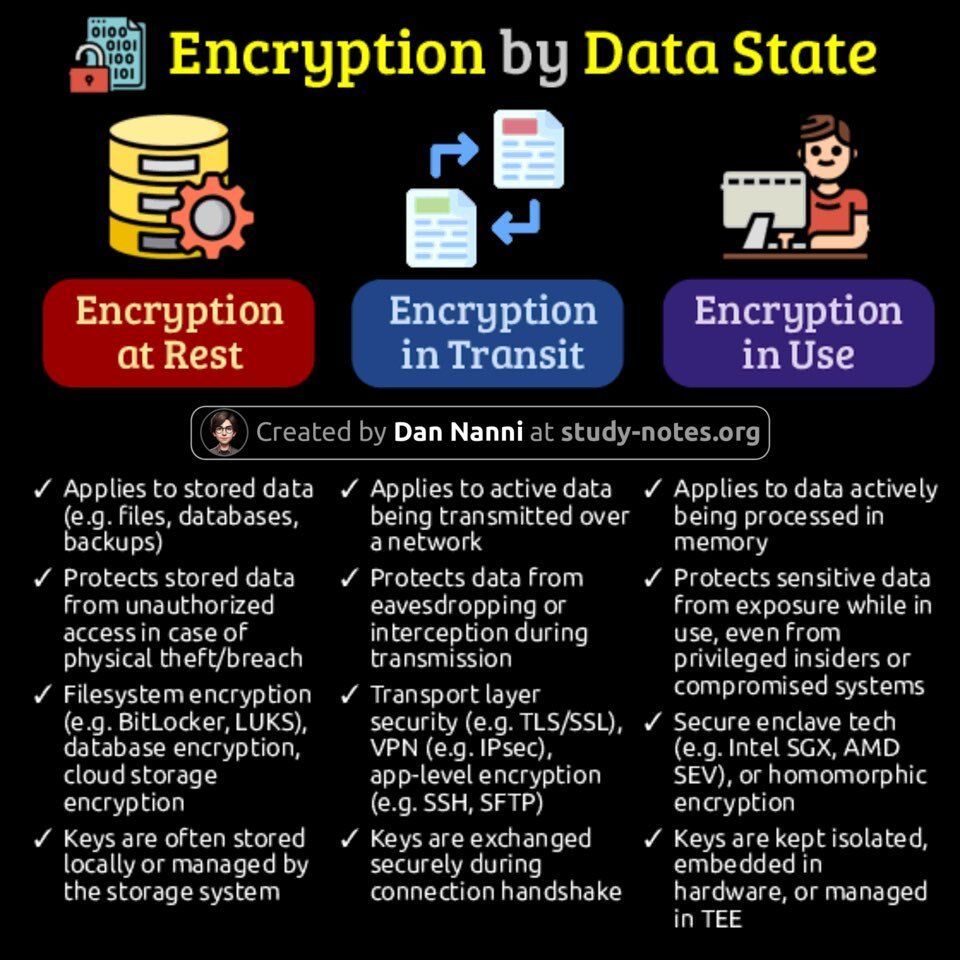
#encryption نتائج البحث
Michigan lawmakers are undermining encryption, which protects everything from trade secrets to critical infrastructure. This could push businesses to move operations out of the state. #VPN #Encryption #Michigan
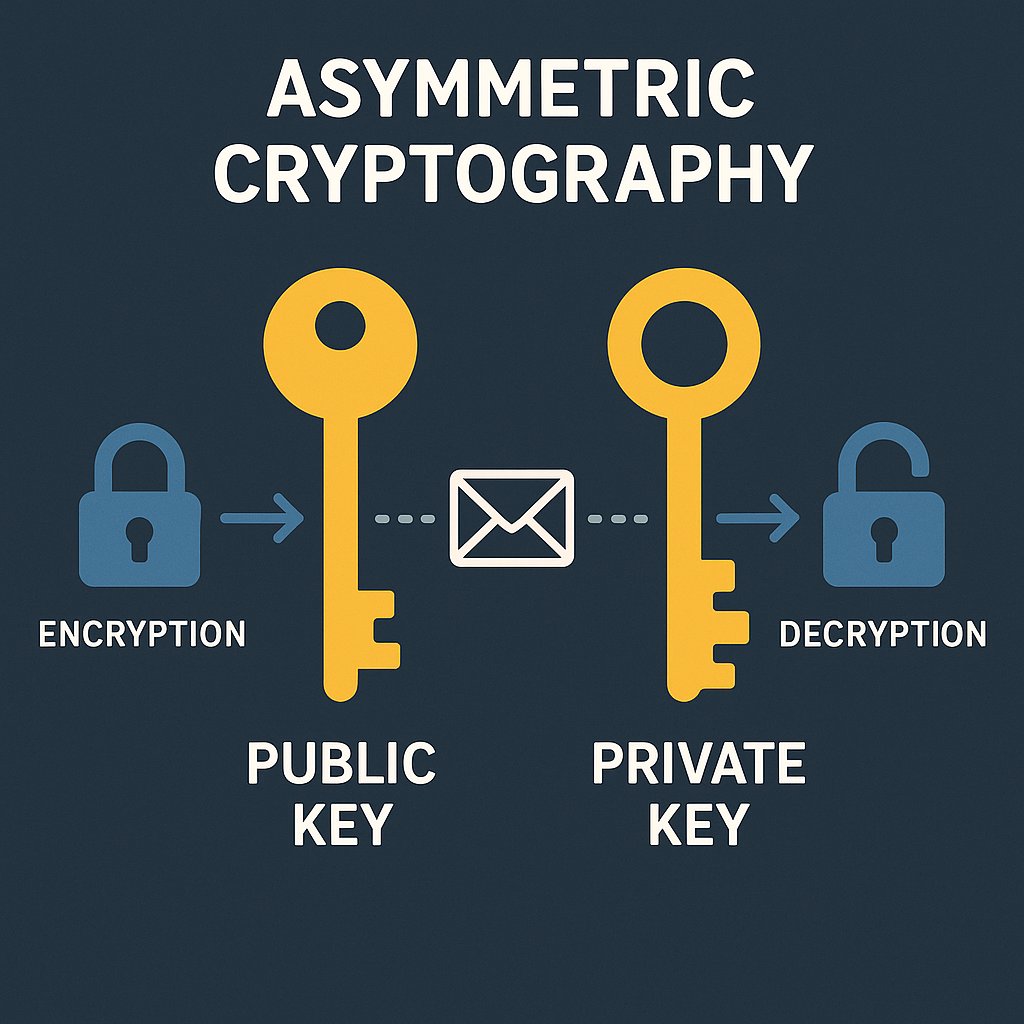
That is where it began! Asymmetric cryptography = two keys, one truth. Public key locks 🔒, private key unlocks 🔓. It’s how trust travels safely through the chaos of the internet. #Blockchain #Encryption #CyberSecurity
Proton launches encrypted spreadsheet tool Proton Sheets #Proton #sheets #encryption cyberinsider.com/proton-launche…
Travel is going digital, and so are the threats ✈️💻 Thales is securing the journey with #biometrics, digital IDs & post-quantum #encryption. Because trust shouldn’t stop at the border 🔐 Explore how 👇 thls.co/xZ2M50XkfF6
Gmic @SeismicSys fam 🎨 Hope the community doing fine 💕 Here’s the most fav Three Leaders of seismic encryption Family 💫 Hope they will like this what i draw. @NoxxW3 @BharatWormie @snow_blis @revvETH #seismic #seismicleaders #encryption
Your data, truly yours. With Zama Protocol, unlock the power of confidential computing, ensuring your sensitive information remains encrypted even during complex computations. The future of privacy is here.🔒 #Encryption #Cybersecurity #DataProtection @zama #ZamaCreatorProgram

What is SHA-256, and how does it secure the digital world? 🔐 This powerful hashing algorithm keeps data safe & tamper-proof — from blockchain to everyday encryption. 💻 Learn how it works 👇 👉 101blockchains.com/sha-256-algori… #CyberSecurity #Blockchain #Encryption #SHA256 #Tech

Europe is one step closer to scanning private messages. Critics call it “voluntary mass surveillance” and a “disaster waiting to happen.” Supporters say it protects children. The fight over privacy isn’t slowing down. #ChatControl #Privacy #Encryption #CyberSecurity #EU…

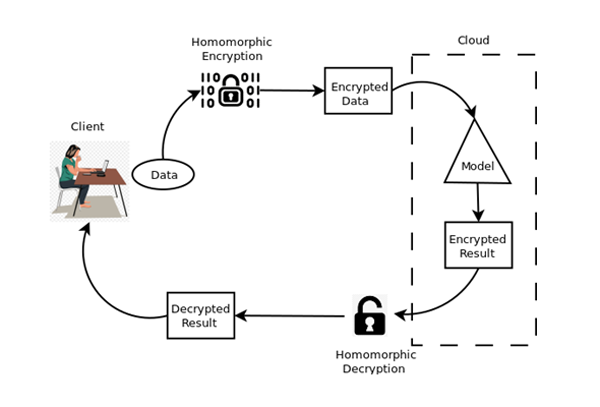
Homomorphic Encryption allows us to compute on ciphertexts as if we would do them on plaintexts, with the decrypted result matching the plaintext operations. It does refer to homomorphism in algebra. @Wipro bit.ly/2ZkvMwX RT @antgrasso #encryption
Stop trusting defaults! 🔒 Learn the 5 essential steps for Cloud Storage Security Read more here: privarase.com/post/how-to-us… #CloudStorageSecurity #CloudSecurity #Encryption #MFA #DataProtection

Michigan lawmakers are undermining encryption, which protects everything from trade secrets to critical infrastructure. Normalizing VPN bans sets a dangerous precedent, potentially pushing businesses out of the state. #VPN #Encryption #Michigan
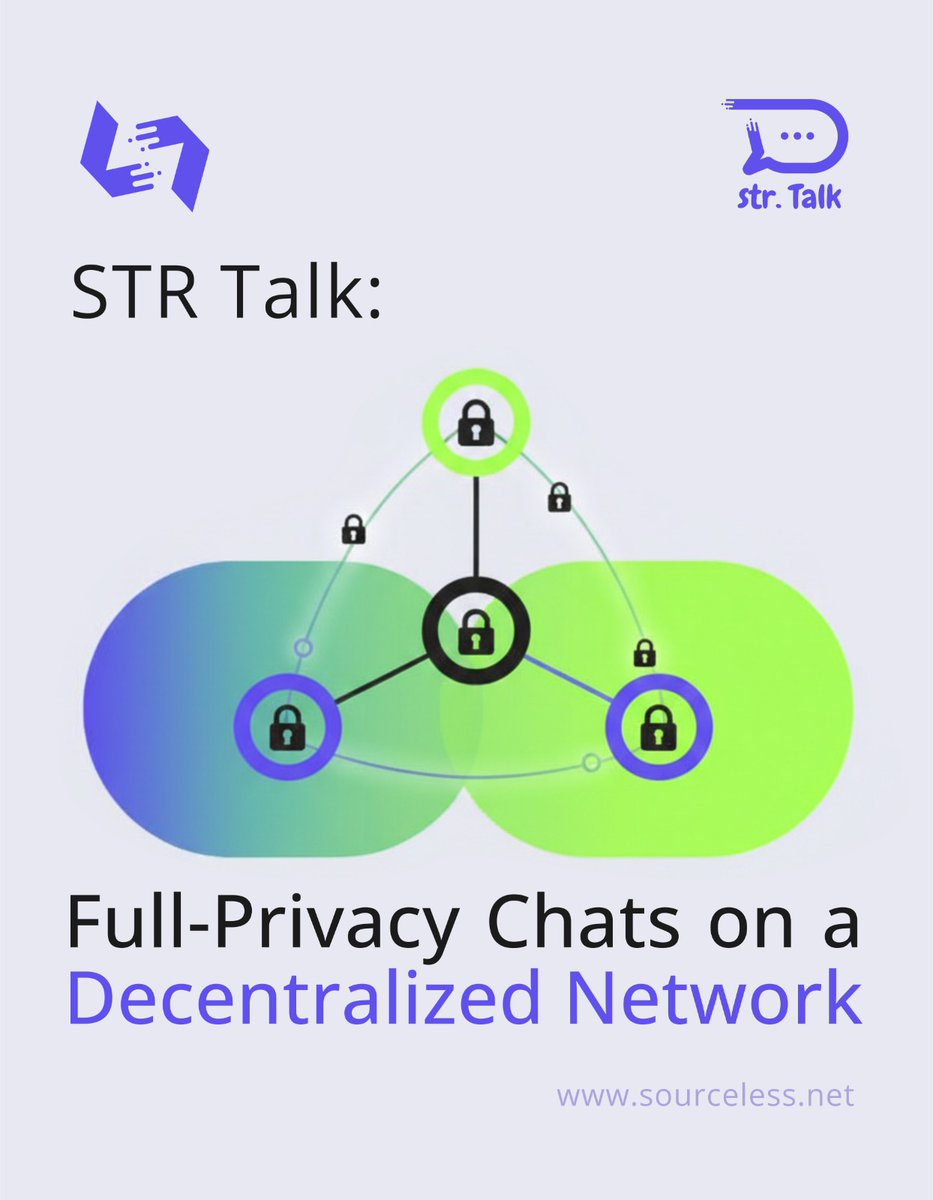
EU may force providers to scan all messages - even encrypted ones. As demand for real privacy grows, #STRTalk offers decentralized, full-privacy chats with no central point to scan or sell. Take back your communication: strtalk.net #Encryption
Making arts for @SeismicSys with Rocky is always fun 🤩 Here’s another art with Rocky …… evyerytime it turns out more interesting 😁👀 #seismic #rocky #encryption Magnitude is the key 🔑 @NoxxW3 @xealistt @heathcliff_eth

Paperclip and Apis Productions Case Study - Paperclip Data Management & Security paperclip.com/resource/apis-… #DataSecurity #Encryption #Fintech #CyberSecurity
Let's Encrypt to reduce SSL/TLS certificate validity from 90 to 45 days by 2028, enhancing internet security. thedailytechfeed.com/lets-encrypt-t… #Security #Encryption #Certificates #SSL #TLS #Internet #Technology #Privacy #Innovation #Compliance #Web #Trust #Safety #Digital #Protection…

winbuzzer.com/2025/12/04/pro… Proton Sheets Launches as an Encrypted Google Sheets Alternative Protected Against AI Data Scraping #Privacy #Encryption #Proton #AI #DataSecurity #CloudStorage #Cybersecurity #Productivity #DataSovereignty #Spreadsheets

Is there a plan for @Arattai to bring #EndToEnd #Encryption for group chats too? @Zoho @ZohoCares @SVembu

Europe is one step closer to scanning private messages. Critics call it “voluntary mass surveillance” and a “disaster waiting to happen.” Supporters say it protects children. The fight over privacy isn’t slowing down. #ChatControl #Privacy #Encryption #CyberSecurity #EU…

Cyber resilience begins with advanced #encryption. Remove critical data from the threat-plane. Cyber resilience is a business imperative: skills and strategy must evolve techradar.com/pro/cyber-resi… #Resilience #Data #CyberSec #Breach
PL/ENG 🇵🇱 Szyfrowanie end-to-end to dziś standard. 🔐 Z ITwithB wprowadzisz E2EE bez utraty wygody pracy. 🚀 🇬🇧 End-to-end encryption today is a standard. 🔐 With ITwithB, you deploy E2EE without sacrificing usability. 🚀 #E2EE #Encryption #ITwithB


Proton launches encrypted spreadsheet tool Proton Sheets #Proton #sheets #encryption cyberinsider.com/proton-launche…
The Power of Encryption "Your data, truly yours. With Zama Protocol, unlock the power of confidential computing, ensuring your sensitive information remains encrypted even during complex computations. The future of privacy is here. 🔒 #Encryption #Cybersecurity #DataProtection

When sharing files this season like proposals, spreadsheets, ID documents, or internal reports, ensure they are encrypted. Benefits: 🔹 Prevents unauthorized access 🔹 Protects data during transfer 🔹 Maintains confidentiality even if intercepted. #DataSecurity #Encryption

Your data, truly yours. With Zama Protocol, unlock the power of confidential computing, ensuring your sensitive information remains encrypted even during complex computations. The future of privacy is here.🔒 #Encryption #Cybersecurity #DataProtection @zama #ZamaCreatorProgram

Stop trusting defaults! 🔒 Learn the 5 essential steps for Cloud Storage Security Read more here: privarase.com/post/how-to-us… #CloudStorageSecurity #CloudSecurity #Encryption #MFA #DataProtection

While #quantumcomputing threatens to break today’s #encryption, #QKD offers a promising #defence, allowing detection of any attempt to intervene in the #encrypted exchange: Shravishtha Ajaykumar or-f.org/35315
World’s first open-source P2P post-quantum E2E encrypted distributed messenger is coming. No servers. No control. No compromise. Just pure privacy. Stay tuned. The quantum-safe era of communication is about to begin. ⚡ #PostQuantum #Encryption #P2P #OpenSource #Cpunk

That is where it began! Asymmetric cryptography = two keys, one truth. Public key locks 🔒, private key unlocks 🔓. It’s how trust travels safely through the chaos of the internet. #Blockchain #Encryption #CyberSecurity

Gmic @SeismicSys fam 🎨 Hope the community doing fine 💕 Here’s the most fav Three Leaders of seismic encryption Family 💫 Hope they will like this what i draw. @NoxxW3 @BharatWormie @snow_blis @revvETH #seismic #seismicleaders #encryption

🇷🇺 Russia wants China's Great Firewall After Tuta Mail, it's now also blocking #Signal & #WhatsApp to stop its citizens from using #encryption Together with @torproject, @fightfortheftr and others we are standing up to say: Stop! ✊ Everyone deserves #privacy. Read our open…

What is SHA-256, and how does it secure the digital world? 🔐 This powerful hashing algorithm keeps data safe & tamper-proof — from blockchain to everyday encryption. 💻 Learn how it works 👇 👉 101blockchains.com/sha-256-algori… #CyberSecurity #Blockchain #Encryption #SHA256 #Tech

Your data, truly yours. With Zama Protocol, unlock the power of confidential computing, ensuring your sensitive information remains encrypted even during complex computations. The future of privacy is here.🔒 #Encryption #Cybersecurity #DataProtection @zama #ZamaCreatorProgram

🖥️ When #QuantumComputers become commercially available, what was considered best-in-class #encryption will be easily cracked. Even now, threat actors are actively stealing encrypted data from organizations with the intention to break into it with quantum computers in coming…

Europe is one step closer to scanning private messages. Critics call it “voluntary mass surveillance” and a “disaster waiting to happen.” Supporters say it protects children. The fight over privacy isn’t slowing down. #ChatControl #Privacy #Encryption #CyberSecurity #EU…

Rocky holds the key, Seismic holds the future.Magnitude is the key 🔐🪨 Created with love ❤️ hope it resonates #Encryption #Seismic @SeismicSys @NoxxW3 @xealistt

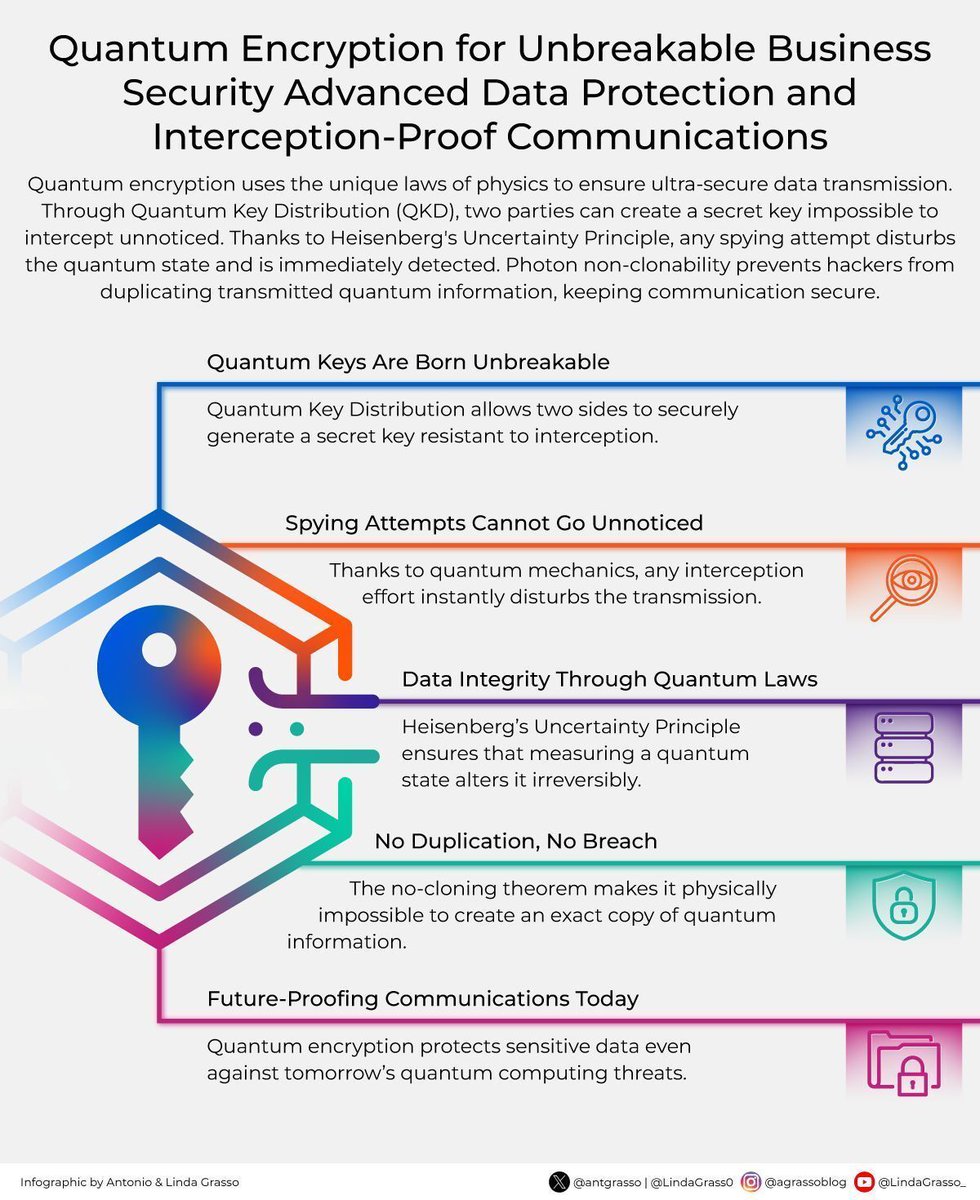
Quantum #Encryption for Unbreakable #Business Security by @antgrasso #CyberSecurity #Infosec #IT #Technology cc: @bernardmarr @marcusborba @JimMarous
Making arts for @SeismicSys with Rocky is always fun 🤩 Here’s another art with Rocky …… evyerytime it turns out more interesting 😁👀 #seismic #rocky #encryption Magnitude is the key 🔑 @NoxxW3 @xealistt @heathcliff_eth

Keys stay on your device. Zero-knowledge by design. No tracking or profiling. IDZ = private cloud + encrypted chat. idz.com #privacy #encryption

EU may force providers to scan all messages - even encrypted ones. As demand for real privacy grows, #STRTalk offers decentralized, full-privacy chats with no central point to scan or sell. Take back your communication: strtalk.net #Encryption

Something went wrong.
Something went wrong.
United States Trends
- 1. Comet 27.6K posts
- 2. Oviedo 5,158 posts
- 3. Fame 56.8K posts
- 4. Matt Campbell 1,791 posts
- 5. Amon Ra 1,194 posts
- 6. TPUSA 87.9K posts
- 7. The Password 3,521 posts
- 8. #MissVenezuela2025 1,516 posts
- 9. Letitia James 17.1K posts
- 10. The Supreme Court 34.2K posts
- 11. SCOTUS 14.8K posts
- 12. Teslaa 2,123 posts
- 13. Amorim 55.5K posts
- 14. fnaf 2 17.9K posts
- 15. Jarry N/A
- 16. ARSB N/A
- 17. Spaghetti 11.2K posts
- 18. #TakoTori1stConcert 1,016 posts
- 19. Jhostynxon Garcia 1,508 posts
- 20. #LightningStrikes N/A