#encryptionkeys résultats de recherche
Moving out? 👍 Sending all with couriers? 👍 Just take #EncryptionKeys with you. cc @NETGEAR @Dell #Cybersecurity #SOP #DigitalResiliency #DLP

QKD quantum security for conference calls #QuantumKeyDistribution #Authentication #EncryptionKeys #OpticalFibre tinyurl.com/y6n7o3zb

New attack recovers RSA encryption keys from EM Waves within seconds: buff.ly/2LgW4GD #CyberSecurity #Security #encryptionkeys #CyberAttack #hackers

Looking to generate, store and manage #encryptionkeys by leveraging APIs around the globe? This @451Research shows Equinix #SmartKey and help: eqix.it/2KM1Q7S

Businesses can generate, store and manage #encryptionkeys by leveraging APIs around the globe. @451Research shows how with #Equinix SmartKey: eqix.it/2KM1Q7S

#LoRaWAN #EncryptionKeys Easy to Crack, Jeopardizing Security of #IoT Networks: buff.ly/2O8ScMq via @threatpost #informedsecurity

Explore the world of encryption keys in our latest blog post. hubs.li/Q01XbHDX0 #DataSecurity #EncryptionKeys

🔒 Discover how #AWSKMS provides a secure solution for storing and managing #EncryptionKeys Explore how this powerful tool can protect your data across AWS services with our free cheat sheet! 📄 👉 digitalcloud.training/aws-kms
The requirement for #storingdata and providing #encryptionkeys - via @informationage bit.ly/3qpKnbc #WANAcceleration #WANOptimisation #Innovation #AI #MachineLearning #OnlineCrime
With #encryptionkeys, #data can be unlocked, but #WAN Optimisation tools cannot cope with encrypted #data. bit.ly/3qpKnbc #WANAcceleration #WANOptimisation #Innovation #AI #MachineLearning #DataPrivacy #BigData

#Microsoftsdesign choices when it comes to the #management of BitLocker #encryptionkeys have been questioned online. This month, a Twitter and StackOverflow debate has been taking place over how BitLocker encryption keys are stored before users sign in with a Microsoft account.

Researchers Find New Fast-Acting #SideChannel #Vulnerability ubm.io/2Msz9Oj #encryptionkeys, #mobilesec

Here’s the good news for #GoogleCloud Platform users— @fortanix External Key Manager for #GCP is live now and is helping businesses in Europe and around the world create, store and manage #encryptionkeys outside of the public cloud in a seamless manner. hubs.li/Q01kl0Td0

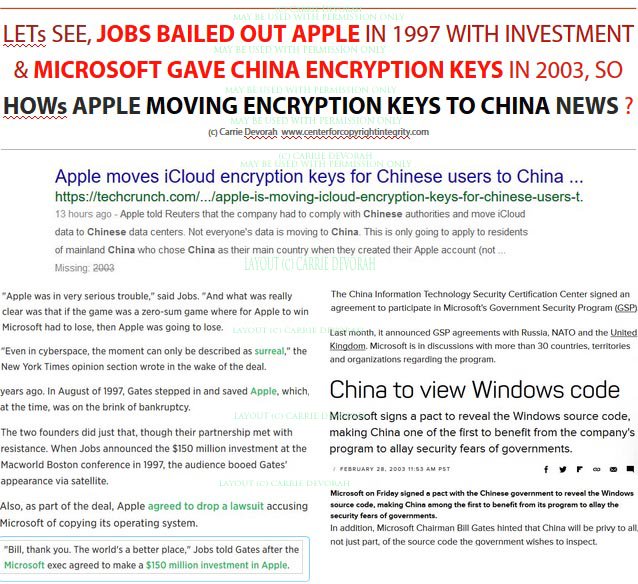
About CHINA & ENCRYPTION KEYS? Old News.... 2003 centerforcopyrightintegrity.com #apple #encryptionkeys #apple #microsoft #china
Affine Cipher Encryption Technique Using Residue Number System 🔐 Read more at: mdpi.com/2410-387X/9/2/… #AffineCiphers #CaesarCipher #EncryptionKeys

Listen to @Barclays Troels Oerting as he discusses their deployment of @Venafi to enable discovery and management of #encryptionkeys and certificates @john_pescatore | sans.org/u/IiM

Businesses can generate, store and manage #encryptionkeys by leveraging APIs around the globe. @451Research shows how with the Equinix SmartKey: ow.ly/5iNM30kFThI

What if we told you that you could eliminate multiple #attackvectors, get back control of #encryptionkeys, and protect data collected, transmitted, and stored, whether that be a private location or #publiccloud?cyphre.com/cyphrelink/

Understanding VPN Handshake: How Secure Connections Are Made bit.ly/4ooqtWL #VPNHandshake #SecureConnection #EncryptionKeys #TechnicalVPN #NetworkSecurity #CryptographyBasics #TechEducation #ConnectionProcess

ضياع مفتاح التشفير الخاص بانتخابات هيئة IACR يؤدي لفقدان بيانات الانتخابات بالكامل وبالتالي اعادة الانتخابات .IACR هي اكبر هيئة متخصصة في أبحاث التشفير #cryptography #encryptionkeys #CyberSecurityAwareness #Cipher #تشفير #الامن_السيبراني
IACR Nullifies Election Because of Lost Decryption Key schneier.com/blog/archives/…
schneier.com
IACR Nullifies Election Because of Lost Decryption Key - Schneier on Security
The International Association of Cryptologic Research—the academic cryptography association that’s been putting conferences like Crypto (back when “crypto” meant “cryptography”) and Eurocrypt since...
نظام تشفير بدون إدارة قوية للمفاتيح key management هيكون عديم الفائدة #cryptography #encryption #encryptionkeys #CyberSecurity

By managing your own encryption keys, you ensure that only authorized individuals and systems can access and decrypt your data. #EncryptionKeys #DataStorage #CloudSecurity

Best Unbreakable Security: End-to-End Encryption. Why e2ee? pastace.com/best-unbreakab… #Computers #encryptionkeys
pastace.com
Best Unbreakable Security: End-to-End Encryption. Why e2ee?
E2EE, or End-to-End Encryption, refers to the process where data is encrypted at the end host. learn how it works as best unbreakable security.
Moving out? 👍 Sending all with couriers? 👍 Just take #EncryptionKeys with you. cc @NETGEAR @Dell #Cybersecurity #SOP #DigitalResiliency #DLP

#Encryption at arm's length means that raw values and #encryptionkeys are never exposed to the #Salesforce environment. You retain custody and control of data and keys. Learn more: stratokey.com/casb/salesforc…
Affine Cipher Encryption Technique Using Residue Number System 🔐 Read more at: mdpi.com/2410-387X/9/2/… #AffineCiphers #CaesarCipher #EncryptionKeys

Want to know the key to ultimate data security? Discover why Dr. Richard Alston believes full disk encryption is crucial for servers and network-attached storage. #DataSecurity #EncryptionKeys storagetech.news/securing-centr…
🔒 Discover how #AWSKMS provides a secure solution for storing and managing #EncryptionKeys Explore how this powerful tool can protect your data across AWS services with our free cheat sheet! 📄 👉 digitalcloud.training/aws-kms

These people, they seem to use the backdoor for most everything they are involved in. 😏 #Backdoor #EncryptionKeys #SourceCode #COTS #Quorum #EAC #CTCL #ElectionInterference #TickTock #TrumpWon
BREAKING: Arizona’s Democratic Secretary of State, Adrian Fontes, has revealed that the “coding error” allowing voters to receive ballots without providing proof of U.S. citizenship actually included 218,000 voters, not just 98,000 as initially announced.
DeKalb GOP v. Raffensperger #EncryptionKeys youtube.com/watch?v=iXn6mk…
With four new features, video meetings on Zoom should have fewer network problems and new solutions for data management were introduced. dlvr.it/TDj9Qx #Applications #compliance #encryptionkeys - Follow for more
techzine.eu
Zoom improves network stability with new enterprise features
Zoom has made four new features available to enterprise customers. The products should address the complex needs of enterprises and simultaneously serve
5/15 In the background, E2EE relies on cryptographic keys. When you send a message, it's encrypted using a key that only the recipient's device has. Without the matching decryption key, the message remains scrambled and unreadable. #EncryptionKeys #Cryptography
Hardcoded encryption keys in Java apps pose a serious security risk. Source code exposure can lead to key compromise, making key rotation difficult. #EncryptionKeys #SecurityRisk #JavaApps"
#Telegram: Great tool indeed. But a design problem: it shouldn't have copies of #EncryptionKeys anywhere. It should be a "no knowledge" tool (we can't possibly know"). Similar tools are (#Signal, #Threema, #Element). #FreePavel #Telegram
نظام تشفير بدون إدارة قوية للمفاتيح key management هيكون عديم الفائدة #cryptography #encryption #encryptionkeys #CyberSecurity

New OpenSSH bug could leak #encryptionkeys to attackers. Learn more about this threat: symc.ly/1VlhMbI

SIM card #encryptionkeys stolen by NSA & GCHQ now your cellphone communications can be listened to : get GoldLocked

QKD quantum security for conference calls #QuantumKeyDistribution #Authentication #EncryptionKeys #OpticalFibre tinyurl.com/y6n7o3zb

Looking to generate, store and manage #encryptionkeys by leveraging APIs around the globe? This @451Research shows Equinix #SmartKey and help: eqix.it/2KM1Q7S

Businesses can generate, store and manage #encryptionkeys by leveraging APIs around the globe. @451Research shows how with #Equinix SmartKey: eqix.it/2KM1Q7S

New attack recovers RSA encryption keys from EM Waves within seconds: buff.ly/2LgW4GD #CyberSecurity #Security #encryptionkeys #CyberAttack #hackers

ONLY 14% of Businesses control all of their own Encryption Keys in the Cloud in 2023. Deploy Cloud Security Solutions with SNS ! Contact SNS: [email protected] | snsin.com | 9789092637 #CloudSecurity #EncryptionKeys #DataProtection #CyberSecuritySolutions #SNS

Listen to @Barclays Troels Oerting as he discusses their deployment of @Venafi to enable discovery and management of #encryptionkeys and certificates @john_pescatore | sans.org/u/IiM

Moving out? 👍 Sending all with couriers? 👍 Just take #EncryptionKeys with you. cc @NETGEAR @Dell #Cybersecurity #SOP #DigitalResiliency #DLP

Researchers Find New Fast-Acting #SideChannel #Vulnerability ubm.io/2Msz9Oj #encryptionkeys, #mobilesec

Here’s the good news for #GoogleCloud Platform users— @fortanix External Key Manager for #GCP is live now and is helping businesses in Europe and around the world create, store and manage #encryptionkeys outside of the public cloud in a seamless manner. hubs.li/Q01kl0Td0

The requirement for #storingdata and providing #encryptionkeys - via @informationage bit.ly/3qpKnbc #WANAcceleration #WANOptimisation #Innovation #AI #MachineLearning #OnlineCrime

🔒 Discover how #AWSKMS provides a secure solution for storing and managing #EncryptionKeys Explore how this powerful tool can protect your data across AWS services with our free cheat sheet! 📄 👉 digitalcloud.training/aws-kms

Something went wrong.
Something went wrong.
United States Trends
- 1. Cowboys 73.8K posts
- 2. #heatedrivalry 25.8K posts
- 3. LeBron 108K posts
- 4. Gibbs 20.4K posts
- 5. Pickens 14.6K posts
- 6. Lions 91.8K posts
- 7. scott hunter 5,474 posts
- 8. fnaf 2 26.5K posts
- 9. Paramount 20.4K posts
- 10. Warner Bros 22.1K posts
- 11. Shang Tsung 30.6K posts
- 12. #OnePride 10.6K posts
- 13. Brandon Aubrey 7,418 posts
- 14. Ferguson 11K posts
- 15. #PowerForce N/A
- 16. Eberflus 2,686 posts
- 17. CeeDee 10.6K posts
- 18. #criticalrolespoilers 2,105 posts
- 19. Cary 40.1K posts
- 20. Goff 8,752 posts














































