#exploitdev 搜尋結果
Bypassing PIE with partial overwrite? 🔥 Instead of guessing full addresses, just overwrite specific bytes to align with predictable offsets. Precision > brute force. A reminder that security evolves, and so must we. 🛡️ #CyberSecurity #ExploitDev #ReverseEngineering


This should be the final set of labs published publicly. That's all folks for now... #RE #Offsec #ExploitDev #SoftwareExploitation exploitation.ashemery.com



Hand-crafted ROP chain 🛠️! Had limited gadgets, so I used an IAT entry for HeapAlloc and calculated the VirtualAllocStub RVA offset. Got creative without ASLR and possibly should've used a read primitive. Details in the gist! #ROP #ExploitDev #osed gist.githubusercontent.com/snowcra5h/a7c1…

Happy New Year 2025! #infosec #CyberSec #ExploitDev #Hacker #Bug #bugbountyhunter #vulnerabilityResearcher #ReverseEngineering #Binex

I’m happy to announce that I passed OSED from @offsectraining 😍😍 I just got the email and man IT FELT SO GOOD #CyberSecurity #exploitdev

It's truly beautiful.🥹Avoiding bad characters, compensating for limited gadgets. It's like crafting a piece of art🎨. Challenges like this make the #OSED so rewarding!💪Got any tricks up your sleeve? Share them with me. Friday is exam day. #ExploitDev #ArtInCode #infosecurity
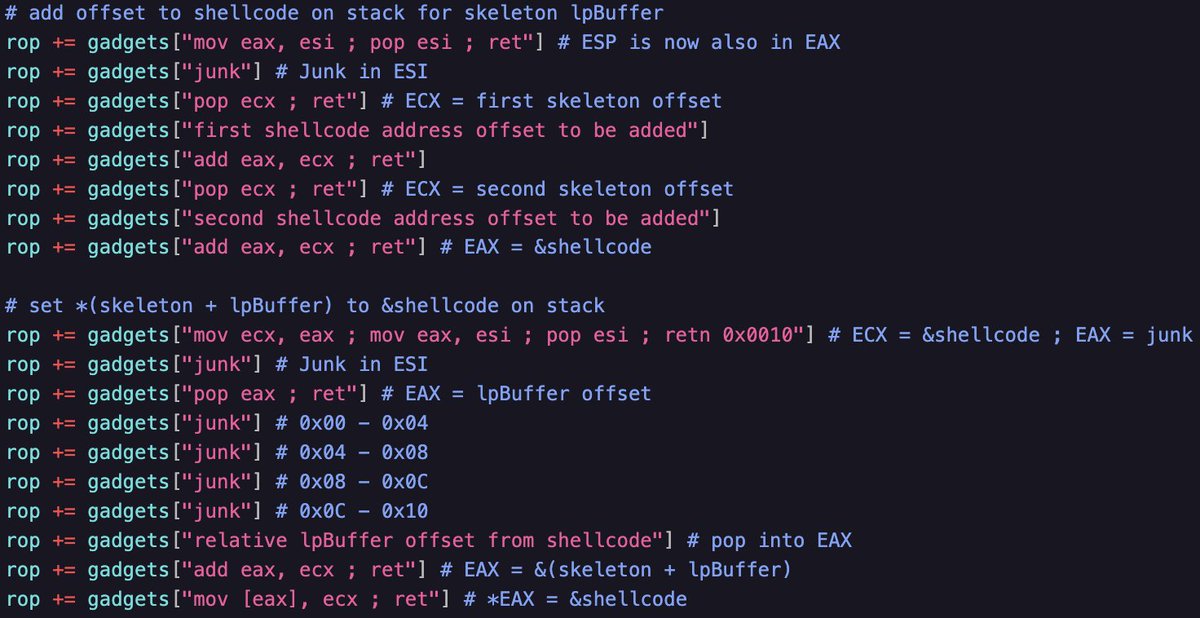
Education is power! corelan-training.com/index.php/trai… #nevergiveup #exploitdev #windows11 #stack #heap @corelanc0d3r

New article alert : ek0msUSB medium.com/@ekoms1/ek0msu… #hacker #greyhat #exploitdev #commandandcontrol #payloads




I really enjoy teaching private classes! Even if you're just a small group (min. 4), willing to travel to Belgium, we can make it happen! I still have some timeslots in November & December. DM if interested @corelanconsult #windows #exploitdev #corelan #nevergiveup

The whole course, labs, videos, etc can be found below. #Cybersecurity #Offsec #ExploitDev #Debugging #Reversing exploitation.ashemery.com

Mastering buffer overflows in Vulnserver is essential for exploit development. WinDBG aids in debugging vulnerabilities by controlling EIP and generating shellcode. A must-learn for secure environments! 🔍⚙️ #ExploitDev #BufferOverflow link: ift.tt/fFk6AGK

Interested in Software Exploitation? This course is for you and will take you from knowing nothing, to understanding how exploits work and how to write them... I hope it will be useful to someone out there! #Offsec #Cybersecurity #ExploitDev #Debugging youtube.com/watch?v=5GGyFb…

Built my own 64-bit ELF packer — something I always wanted to try. XOR encrypts the .text section with a dynamic key and injects a custom stub in new PT_LOAD segment github.com/0x3xploit/entr… #Linux #ELF #Exploitdev #ReverseEngineering #RedTeam #BinaryAnalysis #infosec



ONE more chance this year to take our popular Bootcamp. High-quality materials, real class, real instructor (AND the perfect prep for our heap exploitation class). Seats are selling fast! What are you waiting for? deep-conference.com/predeep-bootca… #corelan#windows11 #exploitdev

🧠 Heap exploits today = brains > brute force. Leaks, UAFs, type confusion—APT-level tactics. Is your defense still stuck in 2015? 👇 What’s your go-to heap hardening move? #CyberSecurity #ExploitDev 👉️ sec.co/blog/modern-he…

All the Assembly and #RE labs have now been shared. I just need to find the reference to the Crackme(s) I used and then it should be 100% complete. #Offsec #ExploitDev #SoftwareExploitation exploitation.ashemery.com

I was driving back home and never thought this last #offsec #ExploitDev #SoftwareExploitation share for 2022 will go this viral. THANKS to all those who Retweeted/Liked/Commented/etc... Wishing you all a great 2023 ...

Uploaded all my Offensive Security & Reverse Engineering (OSRE) course labs (docx) to my repo found below. Most of them have very detailed instructions and should be great to get you started in Software Exploitation. 1/n #Offsec #SoftwareExploitation #RE exploitation.ashemery.com

YES! 🔥 The legendary Corelan (@corelanc0d3r) exploit development training is happening in ROME! 🇮🇹 Absolutely stoked about this opportunity right here in Italy. Time to level up those #ExploitDev skills! 💪 #Corelan #CyberSecurity #InfoSec #Reversing #Rome #Hacking #Cyber

Think kernel bugs are too deep to reach? Think again. 🔥 At #NullconBerlin2025, dive headfirst into a hands-on Linux kernel exploitation with security researcher Andrey Konovalov — no prior kernel knowledge required. Know More: nullcon.net/berlin-2025/tr… #LinuxKernel #ExploitDev

Something went wrong.
Something went wrong.
United States Trends
- 1. $MAYHEM 2,082 posts
- 2. Cherki 21.2K posts
- 3. Villa 190K posts
- 4. #MeAndTheeSeriesEP4 1.85M posts
- 5. namjoon 181K posts
- 6. GAME DAY 32.2K posts
- 7. The EU 478K posts
- 8. Alfredo Díaz 10.6K posts
- 9. #Caturday 3,921 posts
- 10. Arteta 35K posts
- 11. Xavi 11.3K posts
- 12. Championship Saturday 5,403 posts
- 13. Foden 16.2K posts
- 14. BDAY 27.8K posts
- 15. Good Saturday 35.6K posts
- 16. Nueva Esparta 5,170 posts
- 17. #SaturdayVibes 4,291 posts
- 18. Bournemouth 37.1K posts
- 19. Cinnabon 8,297 posts
- 20. #AVLARS 14.4K posts























