#malwareevasion search results
Our PhD student @mrigaki won the first place in the category of "Informatics and Cybernetics" at the POSTER 2022 (26th International Student Conference on Electrical Engineering) with her poster "Stealing and Evading Malware Classifiers"! Congratulations!🥇#MalwareEvasion

Understanding Antivirus Evasion Through Code Obfuscation 🧠🛡️🧩 #CyberSecurity #Obfuscation #MalwareEvasion #EDRBypass #RedTeamEducation #InfoSec #EducationOnly #SecurityAwareness



As #cybersecurity controls improve, #malwareevasion techniques are getting more innovative. #AgentTesla, a prolific strain of #spyware, has a unique infection chain that is long & complex. Read our new #blog for further insight: hubs.ly/H0xkM4_0 #malware #deeplearning

Malware delivery in 2025 is all about deception—SVG invoices, image-embedded payloads, and LOTL tools bypass defenses. Old formats, new threats. 🖼️📦 #MalwareEvasion #Deception buff.ly/CgMw2Ap
ARMO highlights a vulnerability in Linux's io_uring that malware can exploit to evade detection. The "curing" tool demonstrates this threat, while Sysdig and Falco strengthen defense measures. 🛡️🐧 #LinuxSecurity #MalwareEvasion #USA link: ift.tt/ihB7eko

Expel uncovered a phishing attack using Cache Smuggling to deliver malware. The technique uses a fake Fortinet lure and PowerShell to execute a payload staged in the browser's cache, bypassing network detection. #CacheSmuggling #ClickFix #MalwareEvasion securityonline.info/zero-download-…
3/11 Bypassing antivirus? Malware now uses encryption services to avoid detection, raising the bar for security measures. #MalwareEvasion #CyberThreats 🔑
5/11 GodLoader's stealth includes sandbox evasion and manipulating @Microsoft Defender settings. It's time to enhance your security measures. #MalwareEvasion 🕵️♂️
1/11 New malware technique uses Windows UI Automation to bypass EDR tools! Learn how attackers exploit this for stealth attacks. 🕵️♂️💻 #CyberSecurity #MalwareEvasion
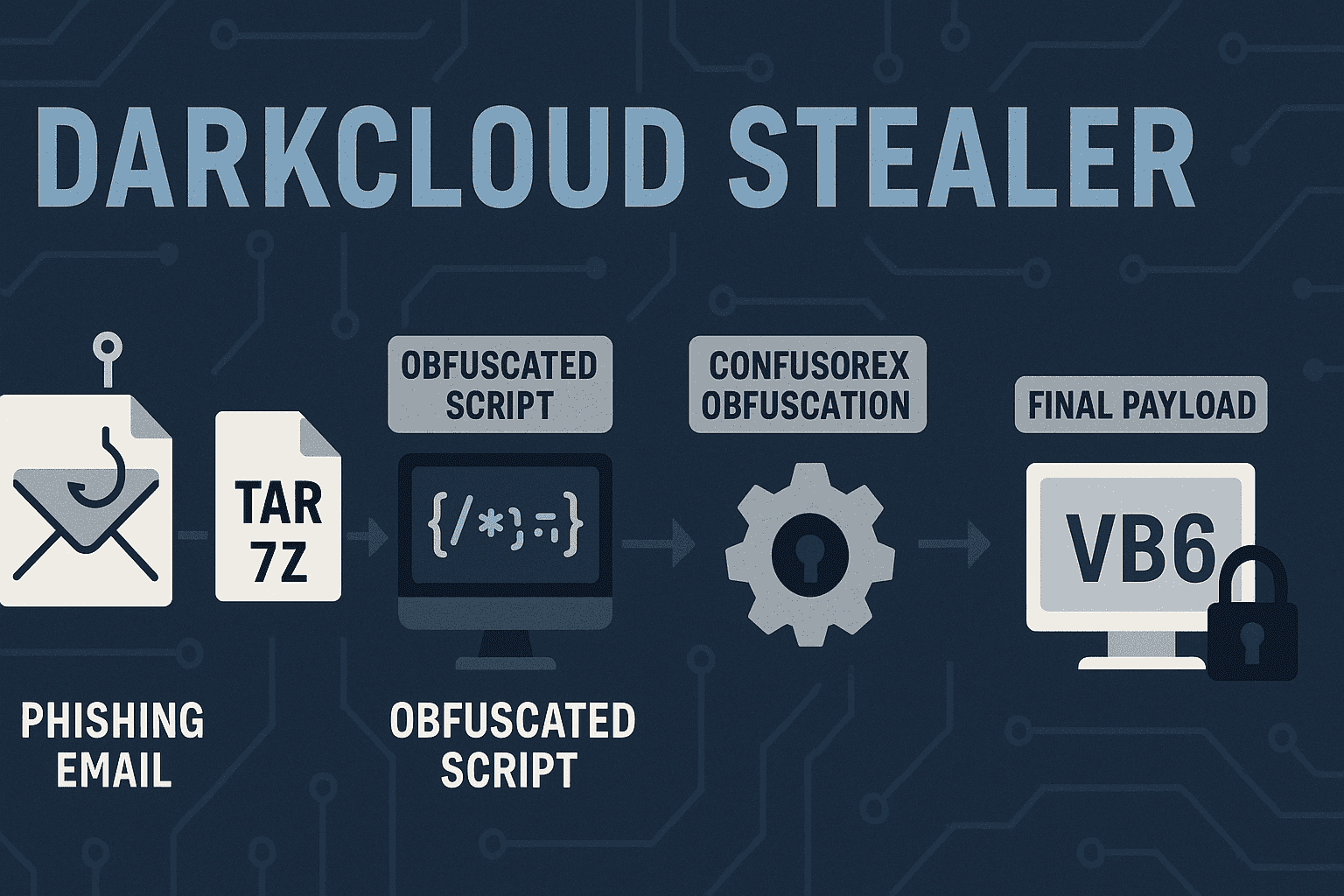
Unit 42 uncovers DarkCloud Stealer's new evasion tactics, including heavily obfuscated JavaScript/WSF loaders and a final VB6 payload that injects into RegAsm.exe to bypass detection #DarkCloudStealer #MalwareEvasion #Obfuscation #Cybersecurity #VB6Malware securityonline.info/darkcloud-stea…
The evolution of malware: From traditional file-based attacks to memory-resident threats and living-off-the-land techniques, attackers are constantly adapting. #malwareevasion #threatdetection
AI-powered malware like PromptLock and PromptSteal use large language models to autonomously adapt and evade detection, fueling a new wave of sophisticated cyber threats. #AIThreats #MalwareEvasion #TechInnovation ift.tt/Ki7oGCV
ThreatLabz reveals the evolution of Raspberry Robin malware, now featuring stronger encryption, complex obfuscation, and a new privilege escalation exploit to bypass detection. #RaspberryRobin #MalwareEvasion #Cybersecurity #LPE #Roshtyak securityonline.info/the-evolution-…
securityonline.info
The Evolution of Evasion: Raspberry Robin Malware Upgrades with New Encryption & UAC Bypass Exploit
ThreatLabz reveals the evolution of Raspberry Robin malware, now featuring stronger encryption, complex obfuscation, and a new privilege escalation exploit to bypass detection.
Use diversified sandbox environments Simulate realistic user behavior during analysis Employ memory analysis to catch dormant payloads #MalwareEvasion #SandboxDetection #ThreatAnalysis #SOCAnalyst #CyberThreats
UNC5518 uses ClickFix fake CAPTCHA pages on compromised sites to drop CORNFLAKE.V3 backdoors (Node.js/PHP), enabling persistence, Active Directory recon, Kerberoasting, and lateral movement via WINDYTWIST.SEA #UNC5518 #WindowsAttack #MalwareEvasion ift.tt/ZOzMmKd
Russian APT COLDRIVER replaces LOSTKEYS with NOROBOT, YESROBOT, and MAYBEROBOT targeting NGOs, policy advisors, and dissidents. Uses ClickFix CAPTCHA lure and shifts to PowerShell backdoors for stealth. #COLDRIVER #MalwareEvasion #Russia ift.tt/vBhoRsZ
HTTP Malware Analysis Evasion HTTP Malware Analysis Evasion In this article published securityzap.com/http-malware-a… #httpbypass #malwareevasion
AI-powered malware like PromptLock and PromptSteal use large language models to autonomously adapt and evade detection, fueling a new wave of sophisticated cyber threats. #AIThreats #MalwareEvasion #TechInnovation ift.tt/Ki7oGCV
Russian APT COLDRIVER replaces LOSTKEYS with NOROBOT, YESROBOT, and MAYBEROBOT targeting NGOs, policy advisors, and dissidents. Uses ClickFix CAPTCHA lure and shifts to PowerShell backdoors for stealth. #COLDRIVER #MalwareEvasion #Russia ift.tt/vBhoRsZ
Malware delivery in 2025 is all about deception—SVG invoices, image-embedded payloads, and LOTL tools bypass defenses. Old formats, new threats. 🖼️📦 #MalwareEvasion #Deception buff.ly/CgMw2Ap
UNC5518 uses ClickFix fake CAPTCHA pages on compromised sites to drop CORNFLAKE.V3 backdoors (Node.js/PHP), enabling persistence, Active Directory recon, Kerberoasting, and lateral movement via WINDYTWIST.SEA #UNC5518 #WindowsAttack #MalwareEvasion ift.tt/ZOzMmKd
Unit 42 uncovers DarkCloud Stealer's new evasion tactics, including heavily obfuscated JavaScript/WSF loaders and a final VB6 payload that injects into RegAsm.exe to bypass detection #DarkCloudStealer #MalwareEvasion #Obfuscation #Cybersecurity #VB6Malware securityonline.info/darkcloud-stea…
ThreatLabz reveals the evolution of Raspberry Robin malware, now featuring stronger encryption, complex obfuscation, and a new privilege escalation exploit to bypass detection. #RaspberryRobin #MalwareEvasion #Cybersecurity #LPE #Roshtyak securityonline.info/the-evolution-…
securityonline.info
The Evolution of Evasion: Raspberry Robin Malware Upgrades with New Encryption & UAC Bypass Exploit
ThreatLabz reveals the evolution of Raspberry Robin malware, now featuring stronger encryption, complex obfuscation, and a new privilege escalation exploit to bypass detection.
Use diversified sandbox environments Simulate realistic user behavior during analysis Employ memory analysis to catch dormant payloads #MalwareEvasion #SandboxDetection #ThreatAnalysis #SOCAnalyst #CyberThreats
Understanding Antivirus Evasion Through Code Obfuscation 🧠🛡️🧩 #CyberSecurity #Obfuscation #MalwareEvasion #EDRBypass #RedTeamEducation #InfoSec #EducationOnly #SecurityAwareness




ARMO highlights a vulnerability in Linux's io_uring that malware can exploit to evade detection. The "curing" tool demonstrates this threat, while Sysdig and Falco strengthen defense measures. 🛡️🐧 #LinuxSecurity #MalwareEvasion #USA link: ift.tt/ihB7eko

1/11 New malware technique uses Windows UI Automation to bypass EDR tools! Learn how attackers exploit this for stealth attacks. 🕵️♂️💻 #CyberSecurity #MalwareEvasion
5/11 GodLoader's stealth includes sandbox evasion and manipulating @Microsoft Defender settings. It's time to enhance your security measures. #MalwareEvasion 🕵️♂️
Understanding Antivirus Evasion Through Code Obfuscation 🧠🛡️🧩 #CyberSecurity #Obfuscation #MalwareEvasion #EDRBypass #RedTeamEducation #InfoSec #EducationOnly #SecurityAwareness




Our PhD student @mrigaki won the first place in the category of "Informatics and Cybernetics" at the POSTER 2022 (26th International Student Conference on Electrical Engineering) with her poster "Stealing and Evading Malware Classifiers"! Congratulations!🥇#MalwareEvasion

As #cybersecurity controls improve, #malwareevasion techniques are getting more innovative. #AgentTesla, a prolific strain of #spyware, has a unique infection chain that is long & complex. Read our new #blog for further insight: hubs.ly/H0xkM4_0 #malware #deeplearning

ARMO highlights a vulnerability in Linux's io_uring that malware can exploit to evade detection. The "curing" tool demonstrates this threat, while Sysdig and Falco strengthen defense measures. 🛡️🐧 #LinuxSecurity #MalwareEvasion #USA link: ift.tt/ihB7eko

Something went wrong.
Something went wrong.
United States Trends
- 1. Cowboys 87.9K posts
- 2. Eagles 126K posts
- 3. Rams 21.9K posts
- 4. #BaddiesUSA 19.2K posts
- 5. Stafford 9,682 posts
- 6. Bucs 9,569 posts
- 7. Baker 17.3K posts
- 8. Scotty 6,154 posts
- 9. #RHOP 7,617 posts
- 10. Pickens 27.7K posts
- 11. Raiders 54.4K posts
- 12. Stacey 28.4K posts
- 13. Browns 99.9K posts
- 14. Todd Bowles 1,123 posts
- 15. Davante Adams 2,220 posts
- 16. Nimmo 18.7K posts
- 17. Shedeur 114K posts
- 18. #ITWelcomeToDerry 6,022 posts
- 19. Ceedee 16.5K posts
- 20. Teddy Bridgewater N/A