#packetflow Suchergebnisse
From the moment you click send, your packet goes on a journey! 🚀 #NetworkingBasics #PacketFlow #DataJourney #Cybersecurity #NetworkSecurity #PerisAI #YouBuild #WeGuard

Using #packetflow switches can increase an organization's #cybersecurity by feeding traffic into #IDS, vulnerability scanning platforms and other #security applications providing greater visibility. #datapackets #data #Ad @NETSCOUT #Cybersecurity
🚀Every packet is a note in your network's symphony. So, how are you conducting your masterpiece? Let's hear your strategies. #NetworkVisibility #PacketFlow

Todays lesson in network101: bits in an ordered fashion is better than bits in an non-ordered fashion! #packetflow

Our #PacketFlow system combines both #security and #ServiceAssurance visibility so there is no need to build out independent overlay monitoring #networks. The same hardware and software can be used for both tasks. netscout.link/6015DqDUb #SecurityVisibility

Our #PacketFlow system combines both #security and #ServiceAssurance visibility so there is no need to build out independent overlay monitoring #networks. The same hardware and software can be used for both tasks. netscout.link/6018DOSqn #SecurityVisibility

Ever wondered what happens after you hit “Enter” on a URL? 🤔 1️⃣ ARP → Find MAC address 2️⃣ DNS → Find IP 3️⃣ TCP Handshake → Connect devices 4️⃣ Routing & Switching → Deliver packets ✅ Page loads in ms! 🚀 Learn Networking at AimNxt #Networking #PacketFlow #CyberSecurity #Tech
.@NETSCOUT's #PacketFlow system combines both #security and #ServiceAssurance visibility so there is no need to build out independent overlay monitoring #networks. The same hardware and software can be used for both tasks. #SecurityVisibility bit.ly/2EuuA1e

.@NETSCOUT's #PacketFlow system combines both #security and #ServiceAssurance visibility so there is no need to build out independent overlay monitoring #networks. The same hardware and software can be used for both tasks. #SecurityVisibility bit.ly/2ER96cj

How do network monitoring tools help you to detect and mitigate DDoS attacks? Check out this blog via our partner @Profitap. #networksafety #monitoring #packetflow #packetanalysis #DPI ow.ly/OXlL30jnSas

.@NETSCOUT's #PacketFlow system combines both #security and #ServiceAssurance visibility so there is no need to build out independent overlay monitoring #networks. The same hardware and software can be used for both tasks. #SecurityVisibility bit.ly/2ERh4SP

.@NETSCOUT's #PacketFlow system combines both #security and #ServiceAssurance visibility so there is no need to build out independent overlay monitoring #networks. The same hardware and software can be used for both tasks. #SecurityVisibility bit.ly/2ERlBEP

Packet Buffers: The Unsung Heroes of Networking 🔹 Traffic cops for your network - prevent congestion 🔹 3 types: Ring buffers, Shared memory, Protocol stack 🔹 Critical for routers, switches Read more:fs.com/glossary/packe… #Networking #TechInfrastructure #PacketFlow
#PacketFlow in TCP-IP Networks: what can we learn wrt #intelligent, #automatic #routing of #DIDComm messages in the #Web7 #Global #DIDComm #Network? geeksforgeeks.org/packet-flow-in…
Das Rechenzentrum in der #Echtzeitanalyse von @Cisco - Einblick bis hinunter zu jedem #Packetflow datacenter-insider.de/das-rechenzent…
Doble QoS ahora será posible en V6 | @mkesolutions #mikrotik #qos #packetflow fb.me/zN95PVY0
after a lot of frustrations, this is how I found out what my #VPN issue was. very useful to monitor the #packetflow. bookmark if you work with @Fortinet FW kb.fortinet.com/kb/documentLin…
From the moment you click send, your packet goes on a journey! 🚀 #NetworkingBasics #PacketFlow #DataJourney #Cybersecurity #NetworkSecurity #PerisAI #YouBuild #WeGuard

Ever wondered what happens after you hit “Enter” on a URL? 🤔 1️⃣ ARP → Find MAC address 2️⃣ DNS → Find IP 3️⃣ TCP Handshake → Connect devices 4️⃣ Routing & Switching → Deliver packets ✅ Page loads in ms! 🚀 Learn Networking at AimNxt #Networking #PacketFlow #CyberSecurity #Tech
Packet Buffers: The Unsung Heroes of Networking 🔹 Traffic cops for your network - prevent congestion 🔹 3 types: Ring buffers, Shared memory, Protocol stack 🔹 Critical for routers, switches Read more:fs.com/glossary/packe… #Networking #TechInfrastructure #PacketFlow
Networks use packets to send and receive data. This article explains packet flow, addressing, and how networks prioritize traffic. #Networking #DataFlow #PacketFlow #DataTransmission #TrafficPrioritization slack.engineering/traffic-101-pa…
#PacketFlow in TCP-IP Networks: what can we learn wrt #intelligent, #automatic #routing of #DIDComm messages in the #Web7 #Global #DIDComm #Network? geeksforgeeks.org/packet-flow-in…
Using #packetflow switches can increase an organization's #cybersecurity by feeding traffic into #IDS, vulnerability scanning platforms and other #security applications providing greater visibility. #datapackets #data #Ad @NETSCOUT #Cybersecurity
Todays lesson in network101: bits in an ordered fashion is better than bits in an non-ordered fashion! #packetflow

after a lot of frustrations, this is how I found out what my #VPN issue was. very useful to monitor the #packetflow. bookmark if you work with @Fortinet FW kb.fortinet.com/kb/documentLin…
From the moment you click send, your packet goes on a journey! 🚀 #NetworkingBasics #PacketFlow #DataJourney #Cybersecurity #NetworkSecurity #PerisAI #YouBuild #WeGuard

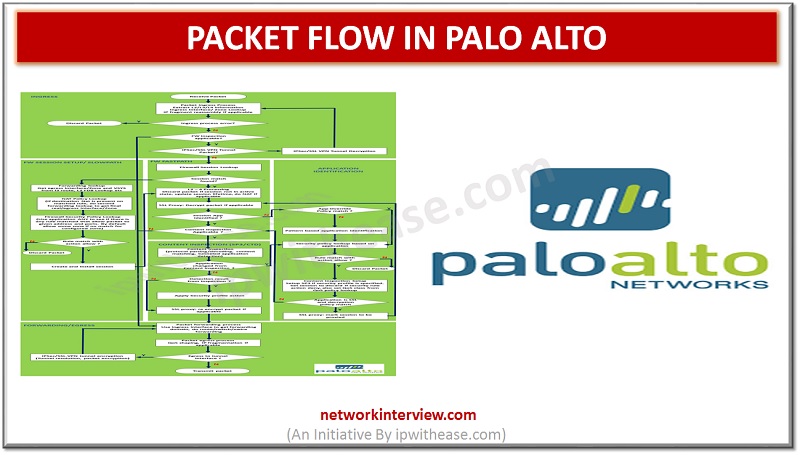
networkinterview.com/packet-flow-in… #packetflow #paloaltonetworks #paloalto #security #netsec #firewall #networksecurity #networkengineer #securityexperts #securityengineer #interviewpreparation #interviewquestions #itjobs #technology #firewalls
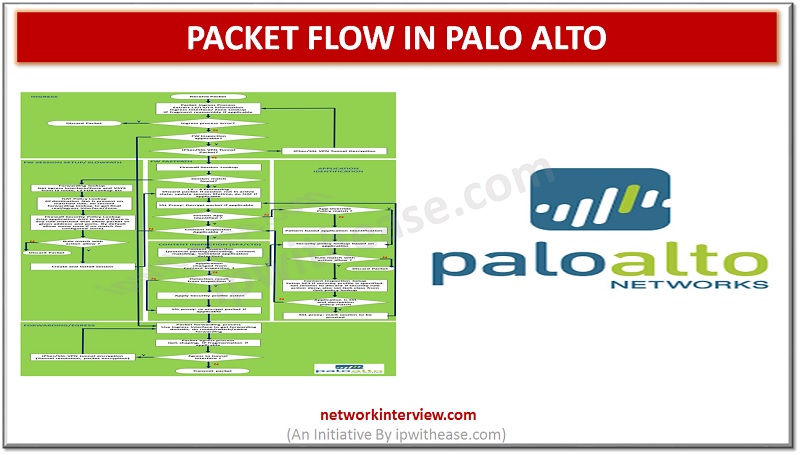
networkinterview.com/packet-flow-in… #packetflow #paloalto #firewall #security #netsec #networksecurity #SecurityEngineer #networkengineer #PCNSE #interviewpreparation #Networkfirewall #paloaltonetworks
Our #PacketFlow system combines both #security and #ServiceAssurance visibility so there is no need to build out independent overlay monitoring #networks. The same hardware and software can be used for both tasks. netscout.link/6015DqDUb #SecurityVisibility

Our #PacketFlow system combines both #security and #ServiceAssurance visibility so there is no need to build out independent overlay monitoring #networks. The same hardware and software can be used for both tasks. netscout.link/6018DOSqn #SecurityVisibility

.@NETSCOUT's #PacketFlow system combines both #security and #ServiceAssurance visibility so there is no need to build out independent overlay monitoring #networks. The same hardware and software can be used for both tasks. #SecurityVisibility bit.ly/2EuuA1e

.@NETSCOUT's #PacketFlow system combines both #security and #ServiceAssurance visibility so there is no need to build out independent overlay monitoring #networks. The same hardware and software can be used for both tasks. #SecurityVisibility bit.ly/2ER96cj

How do network monitoring tools help you to detect and mitigate DDoS attacks? Check out this blog via our partner @Profitap. #networksafety #monitoring #packetflow #packetanalysis #DPI ow.ly/OXlL30jnSas

🚀Every packet is a note in your network's symphony. So, how are you conducting your masterpiece? Let's hear your strategies. #NetworkVisibility #PacketFlow

.@NETSCOUT's #PacketFlow system combines both #security and #ServiceAssurance visibility so there is no need to build out independent overlay monitoring #networks. The same hardware and software can be used for both tasks. #SecurityVisibility bit.ly/2ERh4SP

Todays lesson in network101: bits in an ordered fashion is better than bits in an non-ordered fashion! #packetflow

.@NETSCOUT's #PacketFlow system combines both #security and #ServiceAssurance visibility so there is no need to build out independent overlay monitoring #networks. The same hardware and software can be used for both tasks. #SecurityVisibility bit.ly/2ERlBEP

Something went wrong.
Something went wrong.
United States Trends
- 1. Friendly 61.8K posts
- 2. SNAP 711K posts
- 3. Mac McClung 1,274 posts
- 4. Big Dom 1,878 posts
- 5. James Wiseman N/A
- 6. #JUNGKOOKXCALVINKLEIN 55.2K posts
- 7. Jamaica 114K posts
- 8. #OTGala6 136K posts
- 9. Jessica 27.5K posts
- 10. Riley Gaines 35.7K posts
- 11. Grokipedia 5,836 posts
- 12. Runza N/A
- 13. Sports Equinox 13.7K posts
- 14. Hofer 1,587 posts
- 15. Monday Night Football 7,058 posts
- 16. Mazie 1,383 posts
- 17. MRIs 8,865 posts
- 18. 53 Republicans 4,961 posts
- 19. Roberto Clemente 2,349 posts
- 20. 7 Democrats 5,529 posts