#selfdefendingdata search results
Pretty good read... but a lot of anxiety is to be avoided with #selfDefendingData. #YourDataAsAnAI
Surviving a #LockBit #ransomware attack Hear from @UHSPedu's Zachary Lewis as he walks you through the timeline of events, from the alert to the aftermath, and offers invaluable tips to boost your readiness to survive ransomware: #ransomware: okt.to/oHV4gc
Exactly why "assume breach" controls are necessary. It's assumed the network has been breached, but an additional layer of defense at the data layer is still able to thwart data attack payload completion. #YourDataAsAnAI #NOTaBackup #SelfDefendingData #AI youtube.com/watch?v=9jd1y-…

youtube.com
YouTube
Watch Resiliate data defend itself in Grafana
Resiliate was designed to thwart data attack payload execution attempts for SMBs or laggard verticals, no matter how porous or non-existent network defenses are... Resiliate assumes network breaches, but still protects critical data. #YourDataAsAnAI #SelfDefendingData
If you think you can win negotiating with a ransomware operator over a ransom payment, you're doing it wrong! #PreventionOverRecovery #SelfDefendingData #NOTaBackup #YourDataAsAnAI #AI #ImmutableData #DataIntegrityControls #DLP #Resiliate
Have your "assume breach" control" yet? This control serves as a failsafe-last line of defense. It assumes your network has been breached, and protects the critical data in a unique zero-trust zone. You don't have to find out you're a victim of a zero-day. #SelfDefendingData
The #MOVEit vulnerability continues to impact a growing number of victim organizations. Find out how this widespread #cyberattack is causing concern and raising questions about #DataSsecurity. #DataBreach #ransomware #cybersecurity #CL0P hubs.li/Q01Wp9B40
Increasing costs to ransomware operators should be secondary to disrupting payloads/revenues. Thwart ransomware payload execution attempts & there is no ROI for the cost to perform an attack. Turn zero days into zero paydays! #SelfDefendingData #DLP youtube.com/watch?v=9jd1y-…

youtube.com
YouTube
Watch Resiliate data defend itself in Grafana
Has always been a possible risk but now potentially growing... Again, a non-issue with #SelfDefendingData because if they can't get your data, how can they extort you or screw things up trying to? #UpYourRansomwareGame
What happens if you're targeted by a #ransomware operator that doesn't have the same discipline and rigour as the top-tier groups? buff.ly/3xxQr4P #CyberCrime

Knowing the history or polymorphic malware, is this a surprise? Hence the need for threat-agnostic controls that prevent any threat from completing data attack payload execution attempts.... #SelfDefendingData #YourDataAsAnAI
We analysed the leaked #LockBit 3.0 builder and, inside our testing environment, we were able to quickly create a "targeted #ransomware" sample with it. We found that it's alarming simple for attackers to craft customized, targeted ransomware. More ⇒ kas.pr/ab1o

Consider also .... if you can disrupt data attack payload execution attempts so the kill chain is broken - at scale .... then you disrupt the revenue stream. #SelfDefendingData #NOTaBackup #ImmutableData #DenyPayloads #PreventionOverRecovery
The White House said that it wants agencies across the U.S. government to prioritize disruption campaigns that are “so sustained, coordinated, and targeted that they render ransomware no longer profitable.” @TheRecord_Media #ransomware therecord.media/white-house-cy…
Even more important is knowing that all attack roads lead to the attack target - the data layer, because one can now add a new layer of defensive controls that wait for attackers in the network to attempt to execute their payloads. #YourDataAsAnAttackAwareAI #SelfDefendingData
Another effort to "Talk ourselves secure". Nothing here for overwhelmed SMBs really. The preferred way to prevent ransomware payments is new prevention tech that prevents data loss/exfiltration & disrupts the criminal revenue stream. #UpYourRansomwareGame #SelfDefendingData
More standard "Talk yourself secure". Preparedness doesn't mean much for under-resourced and overwhelmed SMBs. Disrupting ransomware operators needs to take the form of disrupting their revenue streams, including halting exfiltration for double extortion. #SelfDefendingData
New @DecipherSec video with @MeganStifel and @tgrossman_ of @IST_org on the new Ransomware Task Force report and the many challenges that remain in disrupting this ecosystem. youtu.be/PHKFHY2YfS0?si…
youtube.com
YouTube
Ransomware Task Force: We Need to Disrupt Operations at Scale
As it turns out, the porous defenses that can't deny the initial attacker effort, can't stop any others as well... Who knew? #ThreePeat #WhyBeAVictim #SelfDefendingData #YourDataAsAnAI #DenyPayloadCompletion #UpYourRansomwareGame
Almost Three-quarters of Ransomware Victims Hit Multiple Times hipaajournal.com/three-quarters… #healthcare #cybersecurity #ransomware
hipaajournal.com
Almost Three-quarters of Ransomware Victims Hit Multiple Times
A recent study conducted by the cybersecurity firm Semperis has revealed that companies are often targeted by ransomware groups multiple times, with Semperis reports that 74% of companies that...
Well, yes! #YourDataAsAnAI #AI #SelfDefendingData #DenyPayloads #NOTaBackup #ImmutableData #DataIntegrity
AI-vs-AI is the next front in the fight against #phishing. Companies can leverage AI-driven tools to detect malicious activity & stay ahead of cybercriminals. #cybersecurity #infosec #cyberattacks briefly.co/anchor/Informa…
Not incorrect, but this status quo reliance can literally take months and cost millions.... Time to innovate with preventative solutions. ##SelfDefendingData #YourDataAsAnAI #NotABackup
Stabilizing networks after a #ransomware attack: -Response: Contain ransomware -Assessing: Identify affected systems -Remove malware: Clean or reinstall systems -Recover from backups -Enhance security: Update, patch, monitor and train -Test systems -Inform stakeholders, #patelco
Attacking leaders is like cutting the head of a muliple headed snake. They just grow another. To kill the snake, one must disrupt the revenue stream and business model. #SelfDefendingData #YourDataAsAnAI #NOTaBackup #UpYourRansomwareGame #DenyPayloads
What happens to #ransomware groups after takedown? Cybercriminals form new groups and devise new extortion tactics. Even as law enforcement closes in on adversaries, proactive #cybersecurity remains your greatest defense.
Better know how to reduce blast radius and thwart data attack payload execution..... #YourDataAsAnAI #ImmutableData #SelfDefendingData #DataIntegrityControls #DLP
Ransomware: recovering from the inevitable via @Veeam technative.io/ransomware-rec…
What's your defence against zero-days? You need an "Assume breach" control that can still prevent the attack from completing. In our case, it's #AI empowered #SelfDefendingData that transforms the attack target-the data layer, into a self-aware #AI able to thwart payloads.
Inside the breach of Barracuda's email security gateway products via an 0-day: a Chinese hacking team was behind it: bit.ly/42Iotxd #email #China
If you're not starting with data-centric resilience, you're doing it the hard way... #YourDataAsAnAI #SelfDefendingData #UpYourRansomwareGame #NotABackup
Defenders need to get innovating with an additional layer of "assume breach" controls" at the attack target-the data layer! #Resiliate #YourDataAsAnAI #SelfdefendingData #ImmutableData #NOTaBackup #DenyPayloads
As it turns out, the porous defenses that can't deny the initial attacker effort, can't stop any others as well... Who knew? #ThreePeat #WhyBeAVictim #SelfDefendingData #YourDataAsAnAI #DenyPayloadCompletion #UpYourRansomwareGame
Almost Three-quarters of Ransomware Victims Hit Multiple Times hipaajournal.com/three-quarters… #healthcare #cybersecurity #ransomware
hipaajournal.com
Almost Three-quarters of Ransomware Victims Hit Multiple Times
A recent study conducted by the cybersecurity firm Semperis has revealed that companies are often targeted by ransomware groups multiple times, with Semperis reports that 74% of companies that...
Resiliate was designed to thwart data attack payload execution attempts for SMBs or laggard verticals, no matter how porous or non-existent network defenses are... Resiliate assumes network breaches, but still protects critical data. #YourDataAsAnAI #SelfDefendingData
Pretty good read... but a lot of anxiety is to be avoided with #selfDefendingData. #YourDataAsAnAI
Surviving a #LockBit #ransomware attack Hear from @UHSPedu's Zachary Lewis as he walks you through the timeline of events, from the alert to the aftermath, and offers invaluable tips to boost your readiness to survive ransomware: #ransomware: okt.to/oHV4gc
Attacking leaders is like cutting the head of a muliple headed snake. They just grow another. To kill the snake, one must disrupt the revenue stream and business model. #SelfDefendingData #YourDataAsAnAI #NOTaBackup #UpYourRansomwareGame #DenyPayloads
What happens to #ransomware groups after takedown? Cybercriminals form new groups and devise new extortion tactics. Even as law enforcement closes in on adversaries, proactive #cybersecurity remains your greatest defense.
Exactly why "assume breach" controls are necessary. It's assumed the network has been breached, but an additional layer of defense at the data layer is still able to thwart data attack payload completion. #YourDataAsAnAI #NOTaBackup #SelfDefendingData #AI youtube.com/watch?v=9jd1y-…

youtube.com
YouTube
Watch Resiliate data defend itself in Grafana
Not incorrect, but this status quo reliance can literally take months and cost millions.... Time to innovate with preventative solutions. ##SelfDefendingData #YourDataAsAnAI #NotABackup
Stabilizing networks after a #ransomware attack: -Response: Contain ransomware -Assessing: Identify affected systems -Remove malware: Clean or reinstall systems -Recover from backups -Enhance security: Update, patch, monitor and train -Test systems -Inform stakeholders, #patelco
If you're not starting with data-centric resilience, you're doing it the hard way... #YourDataAsAnAI #SelfDefendingData #UpYourRansomwareGame #NotABackup
The business model is too attractive. Fight it by: 1) Making it harder to collect ransomware payments; 2) Deny data attack payload execution attempts so that criminal operators are unable to extort data owners & demand ransoms - prevention over recovery. #SelfDefendingData #AI
Even more important is knowing that all attack roads lead to the attack target - the data layer, because one can now add a new layer of defensive controls that wait for attackers in the network to attempt to execute their payloads. #YourDataAsAnAttackAwareAI #SelfDefendingData
Increasing costs to ransomware operators should be secondary to disrupting payloads/revenues. Thwart ransomware payload execution attempts & there is no ROI for the cost to perform an attack. Turn zero days into zero paydays! #SelfDefendingData #DLP youtube.com/watch?v=9jd1y-…

youtube.com
YouTube
Watch Resiliate data defend itself in Grafana
More standard "Talk yourself secure". Preparedness doesn't mean much for under-resourced and overwhelmed SMBs. Disrupting ransomware operators needs to take the form of disrupting their revenue streams, including halting exfiltration for double extortion. #SelfDefendingData
New @DecipherSec video with @MeganStifel and @tgrossman_ of @IST_org on the new Ransomware Task Force report and the many challenges that remain in disrupting this ecosystem. youtu.be/PHKFHY2YfS0?si…
youtube.com
YouTube
Ransomware Task Force: We Need to Disrupt Operations at Scale
Knowing the history or polymorphic malware, is this a surprise? Hence the need for threat-agnostic controls that prevent any threat from completing data attack payload execution attempts.... #SelfDefendingData #YourDataAsAnAI
We analysed the leaked #LockBit 3.0 builder and, inside our testing environment, we were able to quickly create a "targeted #ransomware" sample with it. We found that it's alarming simple for attackers to craft customized, targeted ransomware. More ⇒ kas.pr/ab1o

Another effort to "Talk ourselves secure". Nothing here for overwhelmed SMBs really. The preferred way to prevent ransomware payments is new prevention tech that prevents data loss/exfiltration & disrupts the criminal revenue stream. #UpYourRansomwareGame #SelfDefendingData
Has always been a possible risk but now potentially growing... Again, a non-issue with #SelfDefendingData because if they can't get your data, how can they extort you or screw things up trying to? #UpYourRansomwareGame
What happens if you're targeted by a #ransomware operator that doesn't have the same discipline and rigour as the top-tier groups? buff.ly/3xxQr4P #CyberCrime

If data owners can't contain blast radius and attack damage, this is what is going to keep happening. Hence the need for data-centric resilience. #YourDataAsAnAI #SelfDefendingData #AI
It's all about the data. If attackers can't steal data, change it or remove data owner access, can they extort anyone? #SelfDefendingData #YourDataAsAnAI #UpYourRansomwareGame
CL0P's Ransomware Rampage - Security Measures for 2024 thehackernews.com/2024/04/cl0ps-… #Infosec #Security #Cybersecurity #CeptBiro #CL0P #Ransomware #Rampage #SecurityMeasures
thehackernews.com
CL0P's Ransomware Rampage - Security Measures for 2024
CL0P ransomware emerges as a major player in the cybercrime world! From "bed bug" beginnings to a global threat, this group's aggressive tactics are r
You do know that the goal is to have the last laugh on Ransomware operators by thwarting their attack payload execution attempts, right? #YourDataAsAnAI #AttackAwareData #SelfDefendingData #DenyPayloads #BreakTheKillChain
Hold on to your hats! There’s a new type of #cyberattack shaking up the #cybersecurity landscape and inducing chuckles along the way. Learn more about the new #CyberThreat that takes a lighthearted approach to extortion. purefla.sh/4aFx5Jb #data #DataStorage #ransomware
blog.purestorage.com
Randomware Shakes Up the Ransomware Game
A new type of cyberattack is shaking up the cybersecurity landscape. Learn more about Randomware and how it’s changing the ransomware game.
Mostly common sense approach but pretty good read. Like many pieces, no mention of exfiltration at all, which is a major piece of the Rware puzzle. Even the fastest recovery won't be fast as prevention that thwarts data attack payload execution attempts! #SelfDefendingData #AI
The threat of ransomware looms large over organizations, regardless of their size or industry. These malicious attacks wreak havoc on businesses, causing significant financial losses, reputation damage,… thefastmode.com/expert-opinion…
thefastmode.com
Mitigating Cyber Liability with Smarter Ransomware Recovery
The threat of ransomware looms large over organizations, regardless of their size or industry. These malicious attacks wreak havoc on businesses,
The same Resiliate cyber defenses for thwarting data attack payload execution attempts at the data in storage level, can be used to protect backups as well. A reminder that backups don't stop or return exfiltrated data either. #YourDataAsAnAI #SelfDefendingData #DLP
Data Backups Targeted in 94% of Ransomware Attacks #Backups are highly recommended for disaster recovery, but organizations cannot depend on them as the primary means of recovering from #ransomware #attacks... ransomwareattacks.halcyon.ai/news/data-back… #cybersecurity #infosec #seecurity

Decent discussion that recognizes need to innovate but still heavy on trying to ID and eject network intruders. Why not innovate in area that breaks killchain for those network intruders in new ways? #SelfDefendingData #YourDataAsAnAI #AI
Join @TrendMicro experts Jon Clay, VP of Threat Intelligence, and Greg Young, VP of Cybersecurity, as they discuss the current state of #cybersecurity. Learn about trends of threat actors, optimism around #AI, and the continuance of #ransomware attacks. bit.ly/3IUtETp

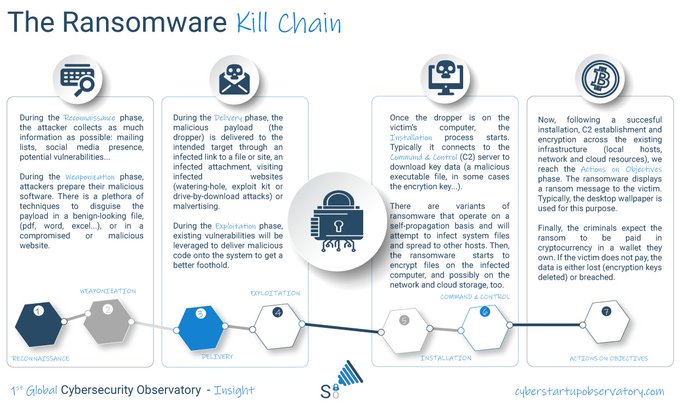
Do you know about the #Ransomware kill chain? #BreachesHappen #SelfDefendingData stops attacks at the end stages of the chain.
Something went wrong.
Something went wrong.
United States Trends
- 1. Haney 11.1K posts
- 2. #AEWFullGear 12.8K posts
- 3. Georgia Tech 4,135 posts
- 4. #RiyadhSeason 15.4K posts
- 5. Darby 3,797 posts
- 6. Utah 19.4K posts
- 7. Mason 39.6K posts
- 8. Syracuse 8,915 posts
- 9. #TheRingIV 6,371 posts
- 10. Kansas State 4,153 posts
- 11. Okada 10.1K posts
- 12. Bam Rodriguez 3,451 posts
- 13. Lincoln Riley 1,854 posts
- 14. #AEWTailgateBrawl 3,182 posts
- 15. #Boxing 6,470 posts
- 16. Oregon 29.2K posts
- 17. Utes 1,635 posts
- 18. Avery Johnson N/A
- 19. Arch Manning 4,421 posts
- 20. Ethan Davis N/A





















