#systemcompromise search results
How to Respond to a System Compromise: Expert Tips and Strategies #SystemCompromise #CybersecurityTips #DataSecurity #ITSecurity #SystemSafety #InformationSecurity #NetworkProtection #DataBreachResponse #CyberThreats #DigitalSafety
What to do when your system is compromised? #systemcompromise #cybersecurity #tipstorecover @GoI_MeitY @Cyberdost @IndianCERT @MeitY_NICSI @mygovindia @Rajeev_GoI #Beaware #Besecure

Hackers exploited CVE-2025-12480 in Gladinet’s Triofox, bypassing authentication via spoofed localhost to gain SYSTEM privileges, create admin accounts, and deploy remote access tools using the antivirus feature. #RemoteAccess #SystemCompromise ift.tt/KkCySGv
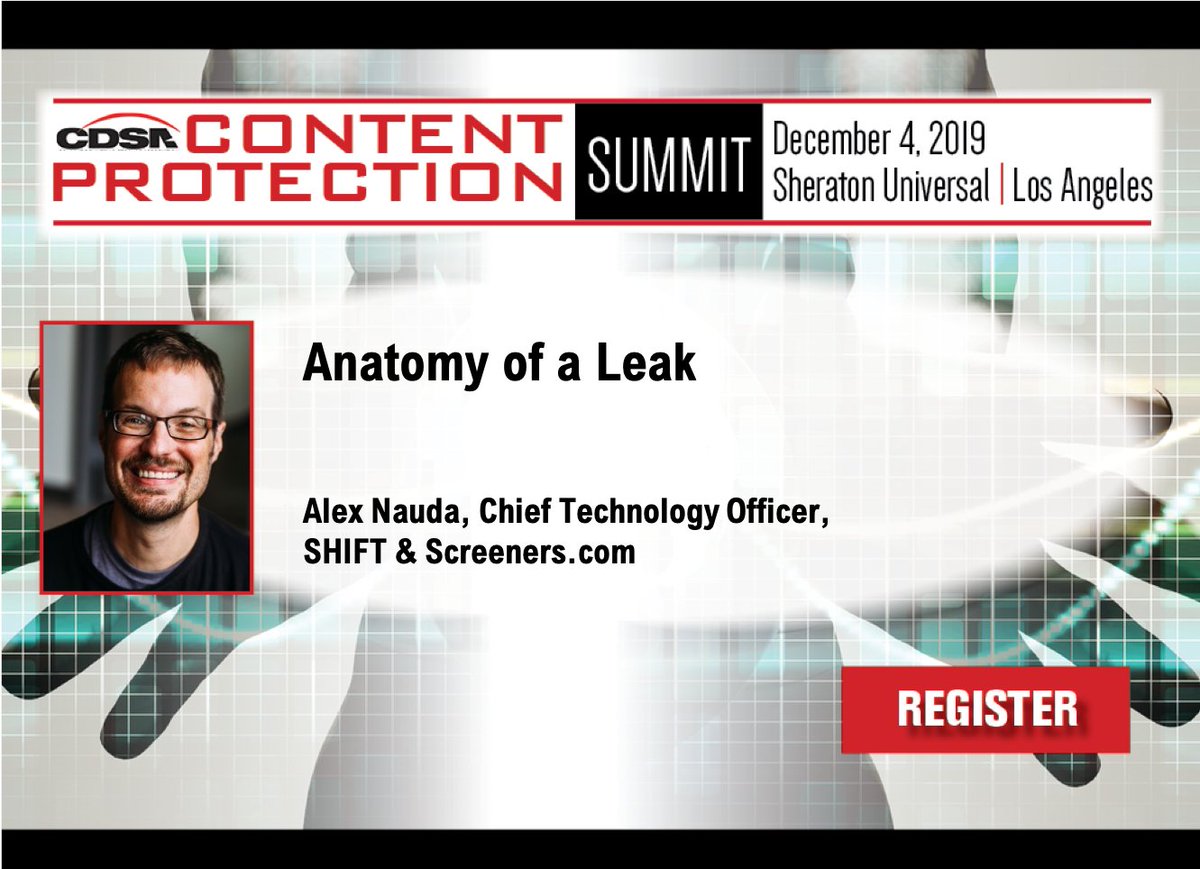
This session is conveying the importance of studying the #Anatomy of a #Leak moderated by Alex Nauda, Chief Technology Officer, @madewithSHIFT with Christian Kennel, Vice President, Media Operations and Digital Product, @warnerbros #SystemCompromise #NatureAndImplications

Improper input validation or insecure deserialization allows an attacker to execute arbitrary commands remotely. Exploitation can lead to unauthorized access, data theft, system compromise, and persistent control over vulnerable servers. #DataTheft #SystemCompromise 💻
- Execute Malicious Code: An attacker might be able to run arbitrary code on the server, potentially leading to a complete system compromise. #Malware #SystemCompromise
Best practices for working with a new computer dlvr.it/SB76gh #systemcompromise
Decrypting possibly compromised Veracrypt hard drive dlvr.it/S2547t #encryption #diskencryption #systemcompromise
Differences between compromised shared hosting and dedicated/virtual hosting dlvr.it/S7NsHd #systemcompromise #sharedhosting
Why am I seeing this in /var/log? dlvr.it/Sg1FJm #logging #systemcompromise #indicatorofcompromise
File with list of logins and passwords dlvr.it/S92QJp #passwords #windows #systemcompromise
Server protection measures from authorities dlvr.it/SgZjV3 #hardware #forensics #systemcompromise
Server protection measures from authorities dlvr.it/S9JQkC #hardware #forensics #systemcompromise
Security Risks Of Letting Users Send Pings On System dlvr.it/S5SzS9 #permissions #systemcompromise #userinterface
How can I get & keep an unauthorized user out of my network? dlvr.it/ScZgRp #malware #identity #systemcompromise
How do you find an attacker if he immediately cleans after himself? dlvr.it/RvvW9t #forensics #logging #systemcompromise
How can this "Jim Browning" YouTuber have access to all these scammers' PCs? dlvr.it/RtFv9D #windows #remotedesktop #systemcompromise
Friend's Instagram account repeatedly hacked despite changing all information and enabling 2FA dlvr.it/SY69mR #attacks #accountsecurity #systemcompromise
Hackers exploited CVE-2025-12480 in Gladinet’s Triofox, bypassing authentication via spoofed localhost to gain SYSTEM privileges, create admin accounts, and deploy remote access tools using the antivirus feature. #RemoteAccess #SystemCompromise ift.tt/KkCySGv
Improper input validation or insecure deserialization allows an attacker to execute arbitrary commands remotely. Exploitation can lead to unauthorized access, data theft, system compromise, and persistent control over vulnerable servers. #DataTheft #SystemCompromise 💻
Critical vulnerabilities discovered in Zyxel Firewalls could compromise entire systems. Stay secure with the latest firmware update. #vulnerabilities #permissions #systemcompromise redoracle.com/News/Critical-…
- Execute Malicious Code: An attacker might be able to run arbitrary code on the server, potentially leading to a complete system compromise. #Malware #SystemCompromise
How to Respond to a System Compromise: Expert Tips and Strategies #SystemCompromise #CybersecurityTips #DataSecurity #ITSecurity #SystemSafety #InformationSecurity #NetworkProtection #DataBreachResponse #CyberThreats #DigitalSafety
Server protection measures from authorities dlvr.it/SgZjV3 #hardware #forensics #systemcompromise
Why am I seeing this in /var/log? dlvr.it/Sg1FJm #logging #systemcompromise #indicatorofcompromise
Friend's Instagram account repeatedly hacked despite changing all information and enabling 2FA dlvr.it/SdKGH9 #attacks #accountsecurity #systemcompromise
How can I get & keep an unauthorized user out of my network? dlvr.it/ScZgRp #malware #identity #systemcompromise
Friend's Instagram account repeatedly hacked despite changing all information and enabling 2FA dlvr.it/SY69mR #attacks #accountsecurity #systemcompromise
Why am I seeing this in /var/log? dlvr.it/SXR2vS #logging #systemcompromise #indicatorofcompromise
What to do when your system is compromised? #systemcompromise #cybersecurity #tipstorecover @GoI_MeitY @Cyberdost @IndianCERT @MeitY_NICSI @mygovindia @Rajeev_GoI #Beaware #Besecure

Server protection measures from authorities dlvr.it/S9JQkC #hardware #forensics #systemcompromise
File with list of logins and passwords dlvr.it/S92QJp #passwords #windows #systemcompromise
Differences between compromised shared hosting and dedicated/virtual hosting dlvr.it/S7NsHd #systemcompromise #sharedhosting
Why am I seeing this in /var/log? dlvr.it/S35nxl #logging #systemcompromise #indicatorofcompromise
What to do when your system is compromised? #systemcompromise #cybersecurity #tipstorecover @GoI_MeitY @Cyberdost @IndianCERT @MeitY_NICSI @mygovindia @Rajeev_GoI #Beaware #Besecure

This session is conveying the importance of studying the #Anatomy of a #Leak moderated by Alex Nauda, Chief Technology Officer, @madewithSHIFT with Christian Kennel, Vice President, Media Operations and Digital Product, @warnerbros #SystemCompromise #NatureAndImplications


Something went wrong.
Something went wrong.
United States Trends
- 1. Sonny Gray 7,132 posts
- 2. Dick Fitts N/A
- 3. Red Sox 7,004 posts
- 4. Rush Hour 4 7,230 posts
- 5. Godzilla 20.1K posts
- 6. National Treasure 5,197 posts
- 7. Raising Arizona N/A
- 8. Gone in 60 1,892 posts
- 9. Clarke 6,306 posts
- 10. Happy Thanksgiving 20.7K posts
- 11. 50 Cent 3,905 posts
- 12. #yummymeets N/A
- 13. Lord of War 1,373 posts
- 14. Giolito N/A
- 15. NextNRG Inc N/A
- 16. #GMMTV2026 4.22M posts
- 17. Thankful 49.3K posts
- 18. Brett Ratner 2,373 posts
- 19. Chelsea 304K posts
- 20. Academic All-District N/A









