#twcitsolutions search results
🔐 4 Facts About the Mother of All Breaches (MOAB) #TWCITsolutions #moab #MotherOfAllBreaches #dataleak #leak #cybernews #cybersecuritycommunity #cybersecurity




5 powerful AI capabilities for contact centres ⬇️ #TWCITsolutions #AI #contactcentre #artificialintelligence #aiinbusiness

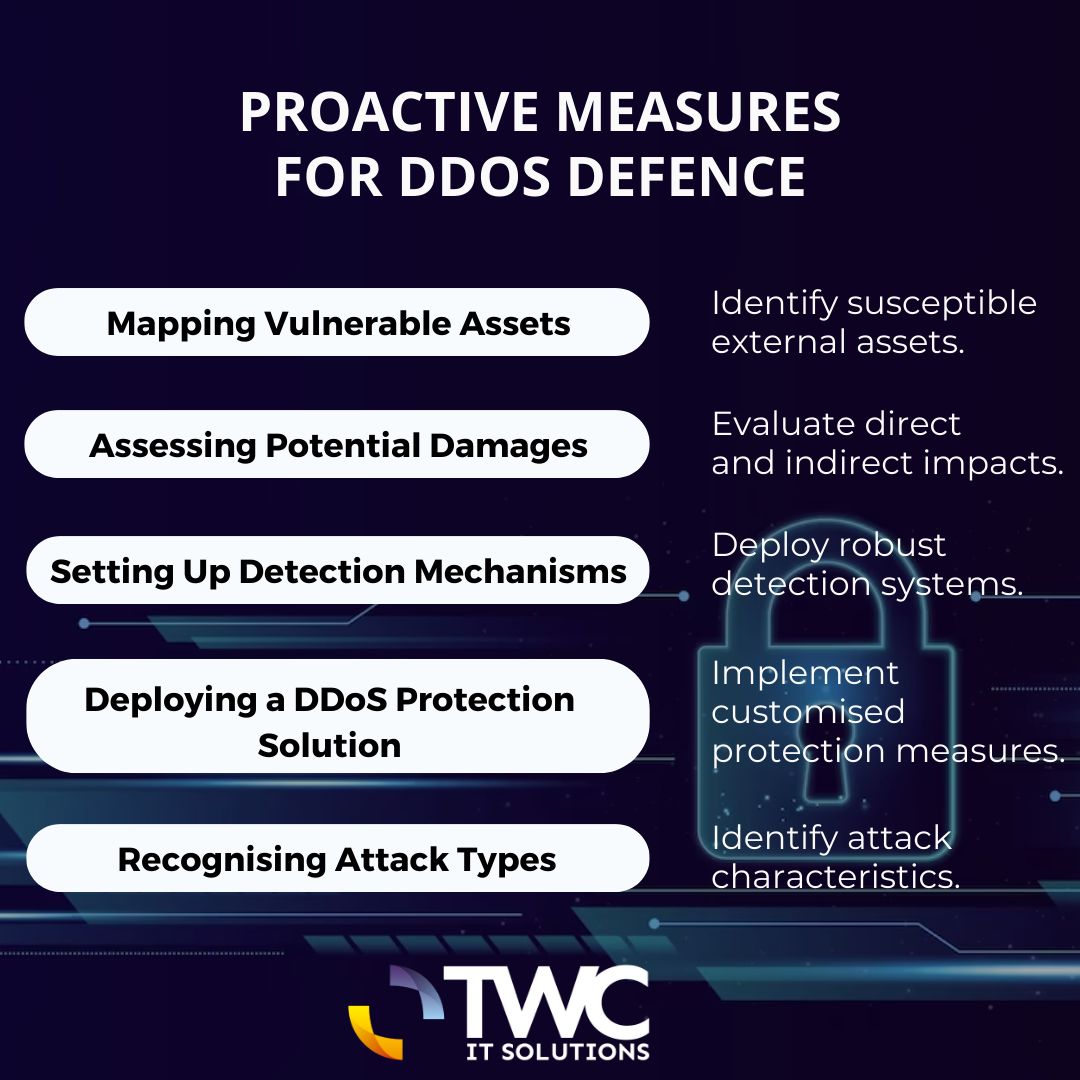
Proactive Measures for DDoS Defence ⬇️ #TWCITsolutions #DDos #DDoSAttack #cyberattack #infosec #cybersecurity #networksecurity #ITSecurity
4 of the Most Common Causes of Data Breaches ⬇️ #TWCITsolutions #databreach #databreaches #software #malware #socialengineering #password #dataprotection #cybersecurity




How Hackers Bypass MFA through Social Engineering ⬇️ #TWCITsolutions #MFA #breach #socialengineering # #cybersecurity #cybersecurityawareness




Critical Threats Targeting Online Retail Businesses ⬇️ (Part 1) #TWCITsolutions #retail #retailbusiness #retailers #pos #supplier #software #eskimming

💡 Implement an account lockout policy for RDP (Remote Desktop Protocol). #TWCITsolutions #cybersecurity #RDP #remotedesktoprotocol #remotework #remote #RDPsecurity #ITsecurity

💡 Always protect your devices with both technical and physical security. #TWCITsolutions #device #devicesecurity #data #digitalsafety #techsecurity #techtips

💡The zero-trust security model verifies every access request to enhance security. #TWCITsolutions #zerotrust #securitymodel #network #cybersecurity

Risk-Based Vulnerability Management (RBVM): Top 6 Benefits ⬇️ Minimise business risks with maximum efficiency. Contact us at 📞 08000 248 900. #TWCITsolutions #riskbasedvulnerabilitymanagement #rbvm #riskbasedvm #cybersecurity #compliance #infosec #ITsupport


💡 Types of cloud provisioning (Advanced, Dynamic & User self-provisioning) offer diverse approaches to managing your cloud resources. #TWCITsolutions #ITsupport #cloud #advancedcloud #dynamiccloud #cloudprovisioning

Valentine's Day is upon us, and cybercriminals are poised to exploit this season of love. ❤️🔒 Here are 4 crucial warnings from cybersecurity experts. #TWCITsolutions #Valentinesday #valentine #cybersecurityexperts




As a CTO, it is crucial for you to adopt essential #dataprivacy strategies to effectively address the prevailing challenges. Discover key Data Privacy Strategies tailored for CTOs in the year 2024. ⬇️ #TWCITsolutions #CTO #dataprivacy #encryption #anonymisation #AI #ML #gdpr




Look who attended the Office Management Show - Emma Chorley and Daniel Connell were on our stand providing insights into our award-winning IT & Cyber Security services. #TWCitsolutions#OfficeManagementShow #BusinessSolutions #theOMS #therecruitmentnetwork #WevegotITcovered

Top 10 Risks for Businesses Using Open Source Software ⬇️ If your business deals with software issues, our special team of engineers can address them remotely or on-site. Call us at 📞 08000 248 900 #TWCitsolutions #software #opensource #sourcecode #business


As we navigate the fast-paced evolution of #cyberthreats, it is imperative that your Endpoint Detection and Response (#EDR) strategy remain both resilient and adaptable. Below are the pivotal features to seek in an EDR for 2024: #TWCITsolutions #endpointprotection




In application control, organisations have two primary options: application allowlisting and application allowlisting. Let's explore both options to help you choose the right one for your organisation. ⬇️ #TWCITsolutions #application #allowlisting #allowlisting #cybersecurity




💡Tip for Multi-Cloud Identity Management! Contact TWC's experts for all your cloud needs! 📞 08000 248 900 📧 [email protected] 🌐 buff.ly/3P15QjZ #TWCITsolutions #multicloud #IAM #SAML #OAuth #cloudcomputing #cloudservices #ITmanagement #ITsupport

💡 Enhance your phishing defence with the SLAM strategy. Reach out to TWC for comprehensive #cybersecurity solutions: 📞 08000 248 900 📧 [email protected] 🌐 buff.ly/40G62IV #TWCITsolutions #ITsupport #SLAM #SLAMmethod #phissing #emailsecurity #onlinesafety

Look who attended the Office Management Show - Emma Chorley and Daniel Connell were on our stand providing insights into our award-winning IT & Cyber Security services. #TWCitsolutions#OfficeManagementShow #BusinessSolutions #theOMS #therecruitmentnetwork #WevegotITcovered

💡 Enhance your phishing defence with the SLAM strategy. Reach out to TWC for comprehensive #cybersecurity solutions: 📞 08000 248 900 📧 [email protected] 🌐 buff.ly/40G62IV #TWCITsolutions #ITsupport #SLAM #SLAMmethod #phissing #emailsecurity #onlinesafety

As we navigate the fast-paced evolution of #cyberthreats, it is imperative that your Endpoint Detection and Response (#EDR) strategy remain both resilient and adaptable. Below are the pivotal features to seek in an EDR for 2024: #TWCITsolutions #endpointprotection




Proactive Measures for DDoS Defence ⬇️ #TWCITsolutions #DDos #DDoSAttack #cyberattack #infosec #cybersecurity #networksecurity #ITSecurity

💡Tip for Multi-Cloud Identity Management! Contact TWC's experts for all your cloud needs! 📞 08000 248 900 📧 [email protected] 🌐 buff.ly/3P15QjZ #TWCITsolutions #multicloud #IAM #SAML #OAuth #cloudcomputing #cloudservices #ITmanagement #ITsupport

CEO's Guide to Cybersecurity Essentials TWC is here to secure your organisation's future through cyber protection. Contact us today 📞 08000 248 900 📧 [email protected] 🌐 buff.ly/40G62IV #TWCITsolutions #CEO #CEOs #securityawareness #riskassessment

How Hackers Bypass MFA through Social Engineering ⬇️ #TWCITsolutions #MFA #breach #socialengineering # #cybersecurity #cybersecurityawareness




💡 Types of cloud provisioning (Advanced, Dynamic & User self-provisioning) offer diverse approaches to managing your cloud resources. #TWCITsolutions #ITsupport #cloud #advancedcloud #dynamiccloud #cloudprovisioning

In application control, organisations have two primary options: application allowlisting and application allowlisting. Let's explore both options to help you choose the right one for your organisation. ⬇️ #TWCITsolutions #application #allowlisting #allowlisting #cybersecurity




Risk-Based Vulnerability Management (RBVM): Top 6 Benefits ⬇️ Minimise business risks with maximum efficiency. Contact us at 📞 08000 248 900. #TWCITsolutions #riskbasedvulnerabilitymanagement #rbvm #riskbasedvm #cybersecurity #compliance #infosec #ITsupport


💡The zero-trust security model verifies every access request to enhance security. #TWCITsolutions #zerotrust #securitymodel #network #cybersecurity

Valentine's Day is upon us, and cybercriminals are poised to exploit this season of love. ❤️🔒 Here are 4 crucial warnings from cybersecurity experts. #TWCITsolutions #Valentinesday #valentine #cybersecurityexperts




5 powerful AI capabilities for contact centres ⬇️ #TWCITsolutions #AI #contactcentre #artificialintelligence #aiinbusiness

💡 Always protect your devices with both technical and physical security. #TWCITsolutions #device #devicesecurity #data #digitalsafety #techsecurity #techtips

4 of the Most Common Causes of Data Breaches ⬇️ #TWCITsolutions #databreach #databreaches #software #malware #socialengineering #password #dataprotection #cybersecurity




Top 10 Risks for Businesses Using Open Source Software ⬇️ If your business deals with software issues, our special team of engineers can address them remotely or on-site. Call us at 📞 08000 248 900 #TWCitsolutions #software #opensource #sourcecode #business


As a CTO, it is crucial for you to adopt essential #dataprivacy strategies to effectively address the prevailing challenges. Discover key Data Privacy Strategies tailored for CTOs in the year 2024. ⬇️ #TWCITsolutions #CTO #dataprivacy #encryption #anonymisation #AI #ML #gdpr




💡 Implement an account lockout policy for RDP (Remote Desktop Protocol). #TWCITsolutions #cybersecurity #RDP #remotedesktoprotocol #remotework #remote #RDPsecurity #ITsecurity

Critical Threats Targeting Online Retail Businesses ⬇️ (Part 1) #TWCITsolutions #retail #retailbusiness #retailers #pos #supplier #software #eskimming

🔐 4 Facts About the Mother of All Breaches (MOAB) #TWCITsolutions #moab #MotherOfAllBreaches #dataleak #leak #cybernews #cybersecuritycommunity #cybersecurity




5 powerful AI capabilities for contact centres ⬇️ #TWCITsolutions #AI #contactcentre #artificialintelligence #aiinbusiness

Proactive Measures for DDoS Defence ⬇️ #TWCITsolutions #DDos #DDoSAttack #cyberattack #infosec #cybersecurity #networksecurity #ITSecurity

4 of the Most Common Causes of Data Breaches ⬇️ #TWCITsolutions #databreach #databreaches #software #malware #socialengineering #password #dataprotection #cybersecurity




How Hackers Bypass MFA through Social Engineering ⬇️ #TWCITsolutions #MFA #breach #socialengineering # #cybersecurity #cybersecurityawareness




🔐 4 Facts About the Mother of All Breaches (MOAB) #TWCITsolutions #moab #MotherOfAllBreaches #dataleak #leak #cybernews #cybersecuritycommunity #cybersecurity




Critical Threats Targeting Online Retail Businesses ⬇️ (Part 1) #TWCITsolutions #retail #retailbusiness #retailers #pos #supplier #software #eskimming

💡 Implement an account lockout policy for RDP (Remote Desktop Protocol). #TWCITsolutions #cybersecurity #RDP #remotedesktoprotocol #remotework #remote #RDPsecurity #ITsecurity

💡 Always protect your devices with both technical and physical security. #TWCITsolutions #device #devicesecurity #data #digitalsafety #techsecurity #techtips

💡The zero-trust security model verifies every access request to enhance security. #TWCITsolutions #zerotrust #securitymodel #network #cybersecurity

💡Tip for Multi-Cloud Identity Management! Contact TWC's experts for all your cloud needs! 📞 08000 248 900 📧 [email protected] 🌐 buff.ly/3P15QjZ #TWCITsolutions #multicloud #IAM #SAML #OAuth #cloudcomputing #cloudservices #ITmanagement #ITsupport

💡 Enhance your phishing defence with the SLAM strategy. Reach out to TWC for comprehensive #cybersecurity solutions: 📞 08000 248 900 📧 [email protected] 🌐 buff.ly/40G62IV #TWCITsolutions #ITsupport #SLAM #SLAMmethod #phissing #emailsecurity #onlinesafety

Risk-Based Vulnerability Management (RBVM): Top 6 Benefits ⬇️ Minimise business risks with maximum efficiency. Contact us at 📞 08000 248 900. #TWCITsolutions #riskbasedvulnerabilitymanagement #rbvm #riskbasedvm #cybersecurity #compliance #infosec #ITsupport


💡 Types of cloud provisioning (Advanced, Dynamic & User self-provisioning) offer diverse approaches to managing your cloud resources. #TWCITsolutions #ITsupport #cloud #advancedcloud #dynamiccloud #cloudprovisioning

CEO's Guide to Cybersecurity Essentials TWC is here to secure your organisation's future through cyber protection. Contact us today 📞 08000 248 900 📧 [email protected] 🌐 buff.ly/40G62IV #TWCITsolutions #CEO #CEOs #securityawareness #riskassessment

Valentine's Day is upon us, and cybercriminals are poised to exploit this season of love. ❤️🔒 Here are 4 crucial warnings from cybersecurity experts. #TWCITsolutions #Valentinesday #valentine #cybersecurityexperts




As a CTO, it is crucial for you to adopt essential #dataprivacy strategies to effectively address the prevailing challenges. Discover key Data Privacy Strategies tailored for CTOs in the year 2024. ⬇️ #TWCITsolutions #CTO #dataprivacy #encryption #anonymisation #AI #ML #gdpr




Look who attended the Office Management Show - Emma Chorley and Daniel Connell were on our stand providing insights into our award-winning IT & Cyber Security services. #TWCitsolutions#OfficeManagementShow #BusinessSolutions #theOMS #therecruitmentnetwork #WevegotITcovered

Top 10 Risks for Businesses Using Open Source Software ⬇️ If your business deals with software issues, our special team of engineers can address them remotely or on-site. Call us at 📞 08000 248 900 #TWCitsolutions #software #opensource #sourcecode #business


As we navigate the fast-paced evolution of #cyberthreats, it is imperative that your Endpoint Detection and Response (#EDR) strategy remain both resilient and adaptable. Below are the pivotal features to seek in an EDR for 2024: #TWCITsolutions #endpointprotection




In application control, organisations have two primary options: application allowlisting and application allowlisting. Let's explore both options to help you choose the right one for your organisation. ⬇️ #TWCITsolutions #application #allowlisting #allowlisting #cybersecurity




Something went wrong.
Something went wrong.
United States Trends
- 1. Lakers 78.1K posts
- 2. #Talus_Labs N/A
- 3. Luka 69.5K posts
- 4. Good Thursday 20K posts
- 5. Wemby 26.9K posts
- 6. Marcus Smart 6,184 posts
- 7. #LakeShow 5,711 posts
- 8. #AmphoreusStamp 7,147 posts
- 9. Blazers 8,857 posts
- 10. Russ 11K posts
- 11. Ayton 16.5K posts
- 12. Will Richard 6,587 posts
- 13. #RipCity N/A
- 14. #dispatch 64.5K posts
- 15. Unplanned 5,703 posts
- 16. Kuminga 3,356 posts
- 17. Podz 2,430 posts
- 18. Nico Harrison 1,994 posts
- 19. Klay 8,528 posts
- 20. Shroud 5,677 posts

