#thickclient arama sonuçları
Thick Client Penetration Testing hackingarticles.in/thick-client-p… hackingarticles.in/thick-client-p… hackingarticles.in/thick-client-p… hackingarticles.in/thick-client-p… hackingarticles.in/thick-client-p… #infosec #thickclient #pentesting #cybersecurity



Thick Client Pentest Lab Setup: DVTA Thick client applications are not new and have been around for many years and can be still easily found within a variety of organizations. hackingarticles.in/thick-client-p… #infosec #thickclient #pentest #hacking
After lockdown 1st hands on session in null Bangalore Null puliya on “Getting familiar with Windows Desktop App Security Assessment Tools” by Kartik Lalan @null0x00 #thickclient #pentesting #windows #securtity



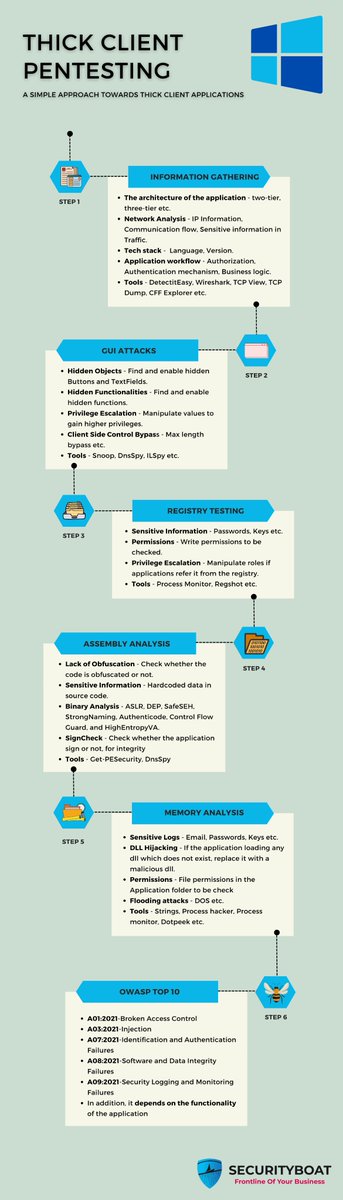
Are you struggling to get started in thick client pentest? 🤔 We have designed a roadmap for you. 🤩 Check it out and start learning! workbook.securityboat.in/mindmaps/thick… #securityboat #bugbounty #thickclient #pentest
Why #ThickClient #ApplicationSecurity Is Important? #CyberSecurity #PenetrationTesting #VAPT #Network Traffic analyser #Memoryanalysis #static analysis #Ghidra #ThickClientTestingTools | cyberatacks@Briskinfosec Technology and Consulting Pvt Ltd bit.ly/2yeXfpv
Are you using #thickclient applications like SAP but your Identity providers only integrate to web-based applications? Know more: bit.ly/2UosCDv #SAP #SSO #CompactIdentity

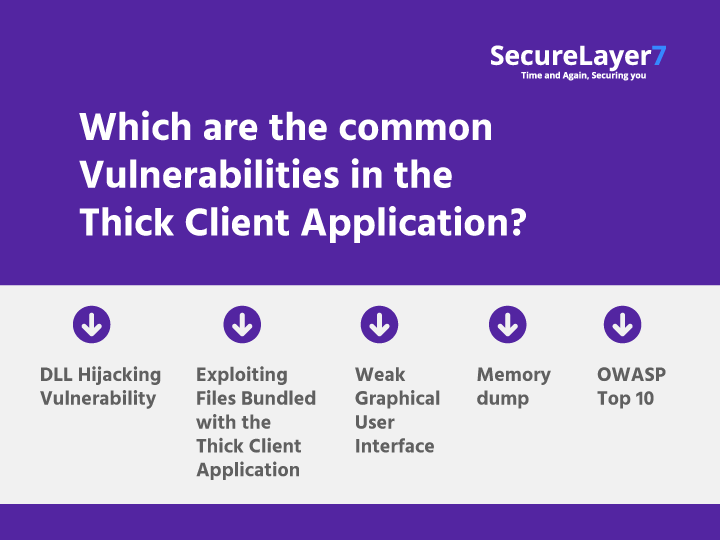
Which are the common Vulnerabilities in the Thick Client Application? DLL Hijacking Vulnerability Exploiting Files Bundled with the Thick Client Application Weak Graphical User Interface Memory dump OWASP Top 10 Visit : bit.ly/389D6jQ #Vulnerabilities #ThickClient
The attacker's payloads have the ability to interfere with and influence insecure communication to the server. use the SecureLayer7 service to find security weaknesses before addressing thick client problems. Visit: bit.ly/389D6jQ #thickclienttesting #thickclient

Thin Clients vs Thick Clients: The end user experience can be quite different depending on the decisions that are made in selecting and creating a company’s virtual desktop infrastructure. clearcube.com/posts/thin-cli… #thinclient #thickclient #smallformfactor #cybersecurity #lowcost

Trying to figure out healthy line between "baked in the template" and "deployed by cm" when it comes to c.d. Good fun. #devops #thickclient
IT teams sometimes have to manage thousands of employee devices. The terms #ThinClient and #ThickClient refer to those individual computers. But what exactly are they and how do they compare ? Discover the answer to this and more here: epos.link/FVYyfl #EPOS

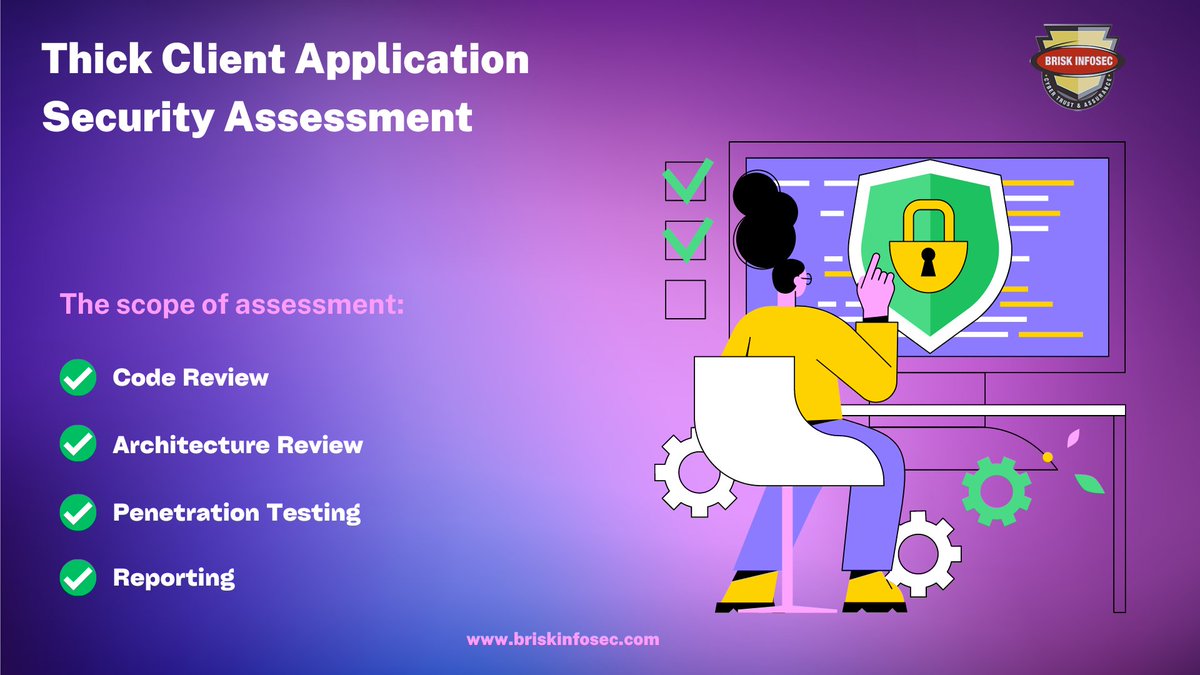
#ThickClient applications often process and store sensitive data, making them a prime target for #cybercriminals. A comprehensive #securityassessment can #help you strengthen your #application's defenses and safeguard your critical #data. briskinfosec.com/services/thick… #SecurityAudit
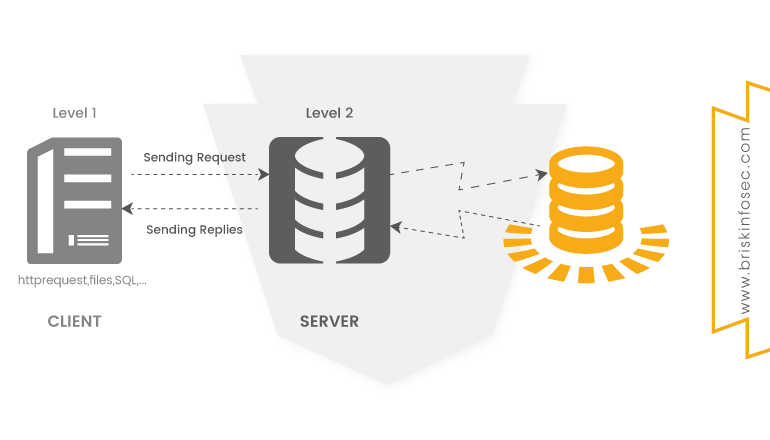
Thick client penetration testing encompasses both client- and server-side processing and frequently makes use of proprietary communication protocols. Visit: bit.ly/389D6jQ #thickclient #thickclientpenetrationtesting #thickclienttesting

Thick Client Application Security identifies every details to abuse or find attack surfaces in the application so that your business is never going to be at risk. Visit:bit.ly/389D6jQ #thickclient #thickclientpenetration #penetrationtesting

Whether you're concerned about Intellectual property risk, operational stress and costs, or regulatory compliance, our service will save your business time and money. Visit:bit.ly/389D6jQ #thickclient #thickclientpenetrationtesting #thickclientpentest

Discover the critical vulnerabilities in thick client application. Thick client pentesting involves both local & server-side processing and often uses proprietary protocols for communication bit.ly/389D6jQ #thickclientapplication #thickclient #thickclientvulnerabilities

Thin and thick client devices - do you know the difference? If you're curious to learn, find out here: fal.cn/3sgs1 #EPOS #ThinClient #ThickClient

My first blogpost about Thick Client Penetration Testing Methodology cyberark.com/threat-researc… #pentest #thickclient #owasp #bugbountytips
Don’t know if you need thick or thin infrastructure? 🤔 We’ve got you covered! 👏 Read our blog to understand both IT infrastructures. 👇 bit.ly/3NjdPrK #ThinClient #ThickClient #Infrastructure

Legacy apps = Security nightmares? Patch the holes with Thick Client Pen Testing! ️ Stops data breaches, exposes weak logins & identifies hidden flaws. Don't wait for a disaster! Click here: darkrelay.com/challenge-page… #thickclient #pentesting #cybersecurity #infosec #darkrelay
Legacy apps = Security nightmares? Patch the holes with Thick Client Pen Testing! ️ Stops data breaches, exposes weak logins & identifies hidden flaws. Don't wait for a disaster! Click here: darkrelay.com/challenge-page… #thickclient #pentesting #cybersecurity #infosec #darkrelay

Don’t know if you need thick or thin infrastructure? 🤔 We’ve got you covered! 👏 Read our blog to understand both IT infrastructures. 👇 bit.ly/3NjdPrK #ThinClient #ThickClient #Infrastructure

#ThickClient applications often process and store sensitive data, making them a prime target for #cybercriminals. A comprehensive #securityassessment can #help you strengthen your #application's defenses and safeguard your critical #data. briskinfosec.com/services/thick… #SecurityAudit

Are you struggling to get started in thick client pentest? 🤔 We have designed a roadmap for you. 🤩 Check it out and start learning! workbook.securityboat.in/mindmaps/thick… #securityboat #bugbounty #thickclient #pentest

After lockdown 1st hands on session in null Bangalore Null puliya on “Getting familiar with Windows Desktop App Security Assessment Tools” by Kartik Lalan @null0x00 #thickclient #pentesting #windows #securtity



Thick client penetration testing encompasses both client- and server-side processing and frequently makes use of proprietary communication protocols. Visit: bit.ly/389D6jQ #thickclient #thickclientpenetrationtesting #thickclienttesting

Thin and thick client devices - do you know the difference? If you're curious to learn, find out here: fal.cn/3sgs1 #EPOS #ThinClient #ThickClient

Thick Client Penetration Testing hackingarticles.in/thick-client-p… hackingarticles.in/thick-client-p… hackingarticles.in/thick-client-p… hackingarticles.in/thick-client-p… hackingarticles.in/thick-client-p… #infosec #thickclient #pentesting #cybersecurity




Thick Client Pentest Lab Setup: DVTA Thick client applications are not new and have been around for many years and can be still easily found within a variety of organizations. hackingarticles.in/thick-client-p… #infosec #thickclient #pentest #hacking

Are you struggling to get started in thick client pentest? 🤔 We have designed a roadmap for you. 🤩 Check it out and start learning! workbook.securityboat.in/mindmaps/thick… #securityboat #bugbounty #thickclient #pentest

After lockdown 1st hands on session in null Bangalore Null puliya on “Getting familiar with Windows Desktop App Security Assessment Tools” by Kartik Lalan @null0x00 #thickclient #pentesting #windows #securtity



Thin Clients vs Thick Clients: The end user experience can be quite different depending on the decisions that are made in selecting and creating a company’s virtual desktop infrastructure. clearcube.com/posts/thin-cli… #thinclient #thickclient #smallformfactor #cybersecurity #lowcost

Discover the critical vulnerabilities in thick client application. Thick client pentesting involves both local & server-side processing and often uses proprietary protocols for communication bit.ly/389D6jQ #thickclientapplication #thickclient #thickclientvulnerabilities

Are you using #thickclient applications like SAP but your Identity providers only integrate to web-based applications? Know more: bit.ly/2UosCDv #SAP #SSO #CompactIdentity

Why #ThickClient #ApplicationSecurity Is Important? #CyberSecurity #PenetrationTesting #VAPT #Network Traffic analyser #Memoryanalysis #static analysis #Ghidra #ThickClientTestingTools | cyberatacks@Briskinfosec Technology and Consulting Pvt Ltd bit.ly/2yeXfpv

Which are the common Vulnerabilities in the Thick Client Application? DLL Hijacking Vulnerability Exploiting Files Bundled with the Thick Client Application Weak Graphical User Interface Memory dump OWASP Top 10 Visit : bit.ly/389D6jQ #Vulnerabilities #ThickClient

The attacker's payloads have the ability to interfere with and influence insecure communication to the server. use the SecureLayer7 service to find security weaknesses before addressing thick client problems. Visit: bit.ly/389D6jQ #thickclienttesting #thickclient

Thick client penetration testing encompasses both client- and server-side processing and frequently makes use of proprietary communication protocols. Visit: bit.ly/389D6jQ #thickclient #thickclientpenetrationtesting #thickclienttesting

Thick Client Application Security identifies every details to abuse or find attack surfaces in the application so that your business is never going to be at risk. Visit:bit.ly/389D6jQ #thickclient #thickclientpenetration #penetrationtesting

Whether you're concerned about Intellectual property risk, operational stress and costs, or regulatory compliance, our service will save your business time and money. Visit:bit.ly/389D6jQ #thickclient #thickclientpenetrationtesting #thickclientpentest

IT teams sometimes have to manage thousands of employee devices. The terms #ThinClient and #ThickClient refer to those individual computers. But what exactly are they and how do they compare ? Discover the answer to this and more here: epos.link/FVYyfl #EPOS

#ThickClient applications often process and store sensitive data, making them a prime target for #cybercriminals. A comprehensive #securityassessment can #help you strengthen your #application's defenses and safeguard your critical #data. briskinfosec.com/services/thick… #SecurityAudit

Thin and thick client devices - do you know the difference? If you're curious to learn, find out here: fal.cn/3sgs1 #EPOS #ThinClient #ThickClient

Don’t know if you need thick or thin infrastructure? 🤔 We’ve got you covered! 👏 Read our blog to understand both IT infrastructures. 👇 bit.ly/3NjdPrK #ThinClient #ThickClient #Infrastructure

Legacy apps = Security nightmares? Patch the holes with Thick Client Pen Testing! ️ Stops data breaches, exposes weak logins & identifies hidden flaws. Don't wait for a disaster! Click here: darkrelay.com/challenge-page… #thickclient #pentesting #cybersecurity #infosec #darkrelay

Difference between thin client and thick client bit.ly/2XD9DfV The basic difference between both terms is that the thin client uses a remote computer for processing an application. #Whatisclient #thinclient #thickclient
💻 Is your thick client app secure? 🔍 At #AuditifySecurity we specialize in #ThickClient Penetration Testing — uncovering hidden vulnerabilities before attackers do ✅ Reverse Engineering ✅ Traffic Interception ✅ Real-world Exploits auditifysecurity.com #CyberSecurity

Something went wrong.
Something went wrong.
United States Trends
- 1. Thanksgiving 372K posts
- 2. Fani Willis 9,854 posts
- 3. Golesh 1,761 posts
- 4. Trumplican 2,552 posts
- 5. Hong Kong 15.4K posts
- 6. Stranger Things 156K posts
- 7. #TejRan 4,112 posts
- 8. Elijah Moore N/A
- 9. Riker N/A
- 10. Khabib 5,778 posts
- 11. Pete Skandalakis N/A
- 12. Ruth 13.9K posts
- 13. Tom Hardy N/A
- 14. #wednesdaymotivation 6,546 posts
- 15. Nuns 10.2K posts
- 16. #Wednesdayvibe 3,485 posts
- 17. Karoline Leavitt 28.1K posts
- 18. Ribs 11.6K posts
- 19. NextNRG Inc N/A
- 20. #WednesdayWisdom 1,173 posts















