#toolshell 搜尋結果
We’ve released a Malware Analysis Report with analysis & detection signatures on files related to Microsoft SharePoint vulnerabilities known as #ToolShell. Review IOCs and detection signatures in our 🆕report 👉 cisa.gov/news-events/an…
Blog for ToolShell Disclaimer: The content of this blog is provided for educational and informational purposes only. blog.viettelcybersecurity.com/sharepoint-too… #SharePoint #ToolShell

I started learning #React Native today and I want to quite already :D #JavaScript #toolsHell #tehranjs
Viettel Cyber Security Press Release for Customer alert, Latest research and Recommendations. Blog is comming viettelsecurity.com/microsoft-shar… #SharePoint #ToolShell

🚨 WARNING: Cloud migration isn’t optional! Researchers uncovered #ToolShell, a vulnerability chain giving attackers full control of on-prem #SharePoint. Start with an intranet audit & content inventory to keep your SharePoint secure. Learn more 🔗 2tl.co/4mnsO3D

CISA Adds One Known Exploited Vulnerability, CVE-2025-53770 “ToolShell,” to Catalog cisa.gov/news-events/al… #Cybersecurity #Sharepoint #toolshell
Quck analysis of new #ToolShell payload observed by @leak_ix: Paylaod is a .dll executed in memory. Sha-256: 3461da3a2ddcced4a00f87dcd7650af48f97998a3ac9ca649d7ef3b7332bd997 It collects System Info and the sensitive machine key. Sends back in response. Single Request takeover.

⚠️ New payload in the relation to #ToolShell . Attackers now don't need the static file anymore, leaking keys from memory without leaving the file. This means the existence of a file is not a reliable IoC anymore.
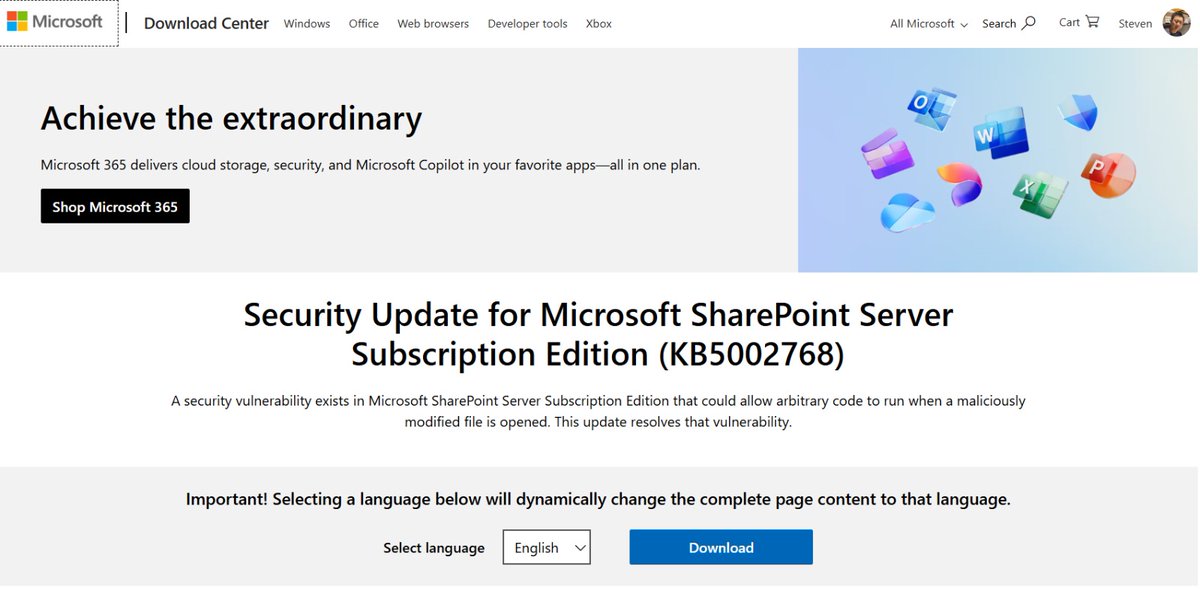
Microsoft has issued a security update for SharePoint Subscription Edition which mitigates CVE-2025-53770 and CVE-2025-53771. Defenders should apply the update immediately.🫡 #Cybersecurity #Sharepoint #toolshell microsoft.com/en-us/download…
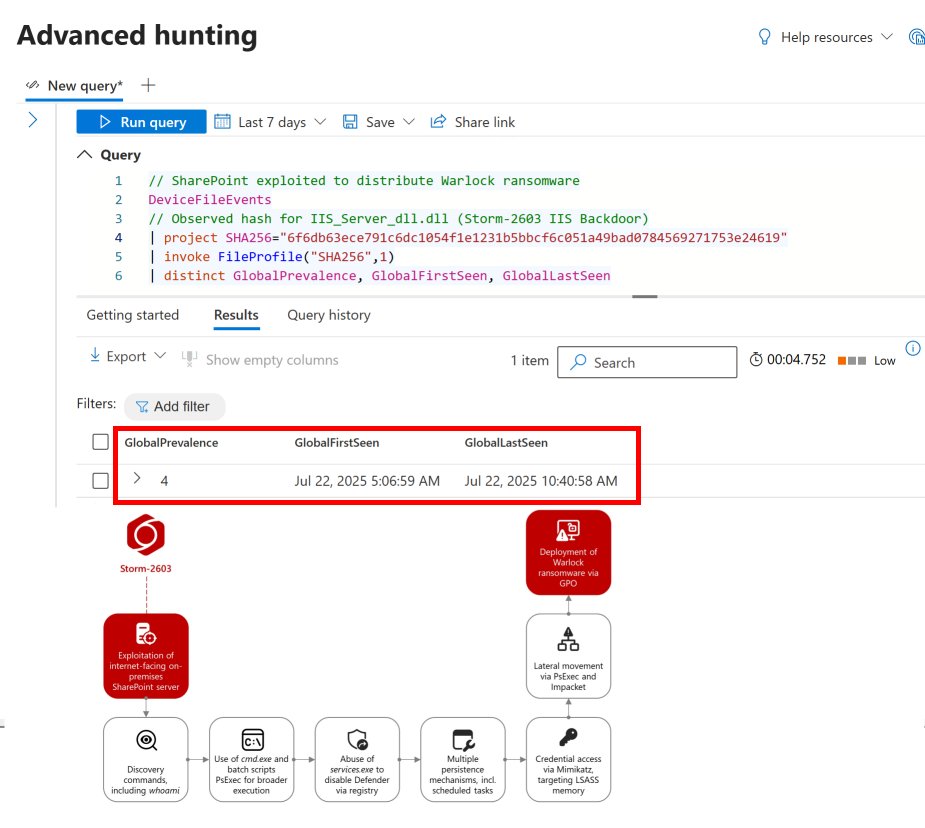
#ToolShell #Warlock 🚨 KQLWizard intel update: Storm-2603 exploited CVE-2025-53770 on 4 internet-facing SharePoint servers on 22 July, deploying Warlock ransomware via ToolShell. Initial access confirmed via observed hash for IIS_Server_dll.dll (Storm-2603 IIS Backdoor).…
The "no shell" activity cluster was seen exploiting the SharePoint vuln on 17th - one day ahead of others - using no filesystem artifacts. Very cool finding by @TomHegel and friends at @LabsSentinel #toolshell #noshell Link to the blog below ->

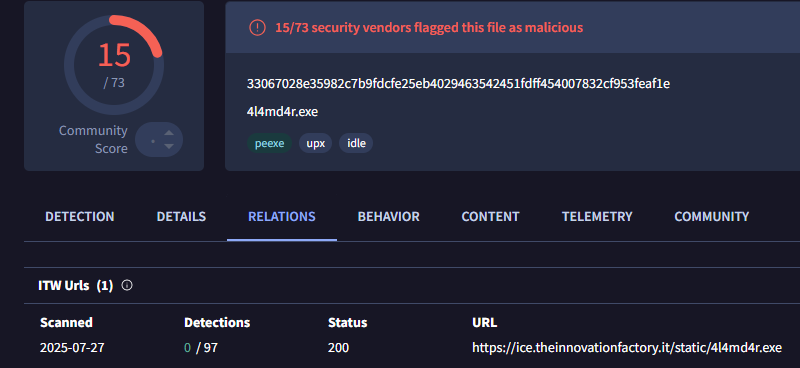
Unit 42 recently identified an unattributed group leveraging the recent #ToolShell exploits to deliver 4L4MD4R #ransomware on July 27th 2025. More info at bit.ly/4l76eL4

Malicious actors are exploiting RCE vulnerability CVE-2025-53770 to compromise on-prem SharePoint servers. See our Alert for info & mitigations on exploitation activity, known as #ToolShell. 👉go.dhs.gov/iZZ

Une faille #SharePoint a touché l’Agence nucléaire 🇺🇸, exploitée via un zero-day par des hackers d’État 🇨🇳. Microsoft a patché, mais l’alerte est orange : environnements on-prem = risque +. Passez le patch #ToolShell dès maintenant. v/@nextinpact ow.ly/Czus50Wv9M0

🔴 CVE-2025-53770 (CVSS 9.8): Critical SharePoint RCE actively exploited as part of #ToolShell 👀 9,762 hosts online (Censys): hubs.ly/Q03y6BW80 🔎@GreyNoiseIO flagged + Censys scans show RDP TCP/3389 using “alikullab1” untrusted cert #CVE202553770 #SharePoint

In light of recent #toolshell events and a DFIR engagement, my colleagues and I put together an article detailing the analysis of post-exploitation activity on affected #Sharepoint servers - specifically, analysis of the "Godzilla" in-memory webshell. kerberpoasting.medium.com/sharepoint-of-…
We added Microsoft SharePoint server remote code execution vulnerability CVE-2025-53770 to our Known Exploited Vulnerabilities Catalog. Visit go.dhs.gov/Z3Q & apply mitigations to protect your org from cyberattacks. #ToolShell

"Mimo" Gang used #Sharepoint #ToolShell to deliver "4l4md4r" #ransomware, which is written in Go language and contains religious-style function names. Report: mp.weixin.qq.com/s/h6_ijQAHhq4t…
Why #ToolShell is a wake-up call for IT leaders: ⚠️ Zero-Trust bypass = attackers don’t need credentials ⚠️ Wider attack surface = low-effort entry points ⚠️ Ransomware risk = data & reputation on the line Don’t wait for a breach. Act now 👇 #SharePoint #M365
Attackers exploited #SharePoint #ToolShell flaws to hit 145+ orgs, incl. US agencies. The campaign persisted even after patches with stealth tactics. @saeed4bbasi of @Qualys says that when patching isn’t possible, use advanced remediation. Via @isms_online sprou.tt/1IYZTYWWaxL
🚨 WARNING: Cloud migration isn’t optional! Researchers uncovered #ToolShell, a vulnerability chain giving attackers full control of on-prem #SharePoint. Start with an intranet audit & content inventory to keep your SharePoint secure. Learn more 🔗 2tl.co/4mnsO3D

Storm-2603 milks ToolShell: CISA flags SharpyShell; Warlock hitting unpatched SharePoint. Rotate machine keys & patch now. 🔓🐼 Read: blog.alphahunt.io/storm-2603-hyb… #AlphaHunt #CyberSecurity #ToolShell
#ToolShell gives hackers full control with no passwords needed. Cloud migration isn’t optional. Start with an #intranet audit & content inventory. Learn more 🔗 2tl.co/4mnsO3D #SharePoint #CloudMigration

Why #ToolShell is a wake-up call for IT leaders: ⚠️ Zero-Trust bypass = attackers don’t need credentials ⚠️ Wider attack surface = low-effort entry points ⚠️ Ransomware risk = data & reputation on the line Don’t wait for a breach. Act now 👇 #SharePoint #M365
カナダ下院が Microsoft 製品の脆弱性(Kerberos 特権昇格、ToolShell)を悪用された攻撃を受けた可能性。ゼロデイ脆弱性はPatch Tuesdayで修正も、SharePoint は依然未防御状態。#MicrosoftExploit #ToolShell gbhackers.com/hackers-exploi…
The Ruđer Bošković Institute in Croatia was hit by a ransomware attack exploiting SharePoint ToolShell vulnerabilities. Data restoration and forensic analysis are underway, with no ransom paid. #ToolShell #RansomwareAttack #Croatia ift.tt/1tHAfX6
Croatian research institute confirms ransomware attack via ToolShell vulnerabilities - helpnetsecurity.com/2025/08/13/cro… - #Ransomware #SharePoint #ToolShell #Europe #Croatia #CybersecurityNews #InfosecNews #ITsec #Cybersecurity

⚠️ Active #ToolShell SharePoint Exploits Detected. Anomali Threat Research breaks down the flaw, IoCs, and defense steps to stop attackers in their tracks. 📖 Read now: bit.ly/4mcyJsf

Hello world, check out my first blog at @InsideStairwell on the #ToolShell #SharePoint vulnerability! 🤓 🔎 📈 👩🏽💻 🦋 Includes: 2 undocumented ASPX webshell variants + a YARA rule to detect ASPX webshells: stairwell.com/resources/tool… #threatintel #threathunting #malwareanalysis
Did you miss this on Monday? Last week we helped several organisations address #SharePoint vulnerabilities. But what are the key messages we can learn from #ToolShell for protecting your systems? Read more here: jcsc.je/advice-and-gui… #JerseyCI #patching #cybersecurity

CISA Releases Malware Analysis Report for Microsoft SharePoint Vulnerabilities | Linn Freedman, Data Privacy + Cybersecurity Insider dataprivacyandsecurityinsider.com/2025/08/cisa-r… #CISA #malware #ToolShell
📢 Los expertos de Kaspersky Global Research and Analysis Team (GReAT) han realizado un análisis detallado de #ToolShell, un conjunto de vulnerabilidades en #Microsoft #SharePoint que los atacantes están explotando activamente. 🔍 Las fallas de ToolShell se originan en una…

#ThreatProtection #ProjectAK47 malware links threat actor to #ToolShell activity, read more about Symantec's coverage: broadcom.com/support/securi…
CISA issues an urgent warning about "ToolShell," a sophisticated exploit chain targeting SharePoint servers with multiple vulnerabilities to install webshells and steal crypto keys. #CISAAlert #ToolShell #SharePoint #ZeroDay #Cybersecurity securityonline.info/cisa-warns-of-…
We’ve released a Malware Analysis Report with analysis & detection signatures on files related to Microsoft SharePoint vulnerabilities known as #ToolShell. Review IOCs and detection signatures in our 🆕report 👉 cisa.gov/news-events/an…
Ransomware attacks have been seen exploiting the ToolShell vulnerability chain in SharePoint. Find out what you can do to protect your environment today. 🚨 hubs.ly/Q03ztX2Q0 #Ransomware #ToolShell #Cybersecurity
SharePoint Servers on Fire: ToolShell Hack Breaks 400+ Networks A chain of zero-days dubbed “ToolShell” is being used in mass attacks across SharePoint servers globally, with up to 400 systems compromised and new ransomware variants spreading. #ToolShell #SharePointZeroDay…
Summer 2025 saw a surge in cyberattacks targeting healthcare, retail, and geopolitical sectors. Ransomware groups like Interlock, Rhysida, and Qilin exploited vulnerabilities, causing data leaks and disruptions. #DataBreach #US #ToolShell ift.tt/RvgTNO2
Blog for ToolShell Disclaimer: The content of this blog is provided for educational and informational purposes only. blog.viettelcybersecurity.com/sharepoint-too… #SharePoint #ToolShell

Viettel Cyber Security Press Release for Customer alert, Latest research and Recommendations. Blog is comming viettelsecurity.com/microsoft-shar… #SharePoint #ToolShell

#ToolShell gives hackers full control with no passwords needed. Cloud migration isn’t optional. Start with an #intranet audit & content inventory. Learn more 🔗 2tl.co/4mnsO3D #SharePoint #CloudMigration

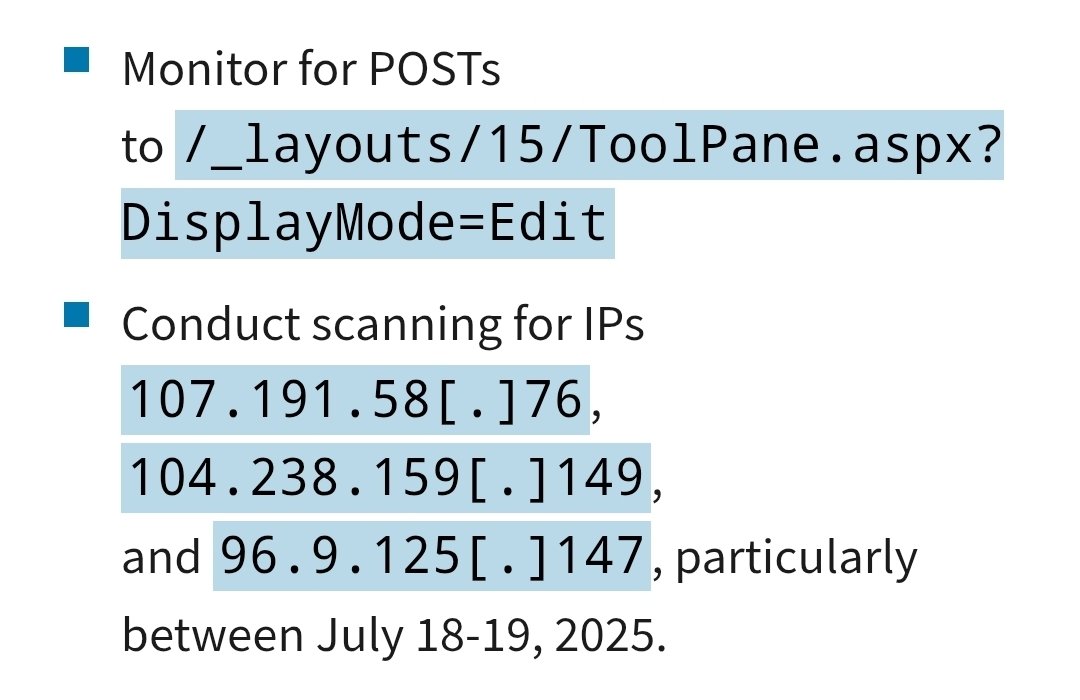
Zero-day #ToolShell is being actively exploited in the wild, targeting on-prem #SharePoint servers with unauth RCE. ⚠️ CVEs: CVE-2025-53770 (RCE) + CVE-2025-53771 (Auth Bypass) 🧠 ToolPane.aspx abused for deserialization & webshells 🔐 Attackers steal MachineKeys, go fileless, &…

Quck analysis of new #ToolShell payload observed by @leak_ix: Paylaod is a .dll executed in memory. Sha-256: 3461da3a2ddcced4a00f87dcd7650af48f97998a3ac9ca649d7ef3b7332bd997 It collects System Info and the sensitive machine key. Sends back in response. Single Request takeover.

⚠️ New payload in the relation to #ToolShell . Attackers now don't need the static file anymore, leaking keys from memory without leaving the file. This means the existence of a file is not a reliable IoC anymore.
SharePoint脆弱性を悪用する #ToolShell に注意!🇨🇳中国系攻撃グループによる悪用も報告されていますが、#ESET もLuckyMouseに関連するバックドアを検出。ESETの監視結果はブログで掲載→ htps://www.eset.com/jp/blog/welivesecurity/toolshell-an-all-you-can-eat-buffet-for-threat-actors-jp/

CISA Adds One Known Exploited Vulnerability, CVE-2025-53770 “ToolShell,” to Catalog cisa.gov/news-events/al… #Cybersecurity #Sharepoint #toolshell

Une faille #SharePoint a touché l’Agence nucléaire 🇺🇸, exploitée via un zero-day par des hackers d’État 🇨🇳. Microsoft a patché, mais l’alerte est orange : environnements on-prem = risque +. Passez le patch #ToolShell dès maintenant. v/@nextinpact ow.ly/Czus50Wv9M0

Malicious actors are exploiting RCE vulnerability CVE-2025-53770 to compromise on-prem SharePoint servers. See our Alert for info & mitigations on exploitation activity, known as #ToolShell. 👉go.dhs.gov/iZZ

🚨 WARNING: Cloud migration isn’t optional! Researchers uncovered #ToolShell, a vulnerability chain giving attackers full control of on-prem #SharePoint. Start with an intranet audit & content inventory to keep your SharePoint secure. Learn more 🔗 2tl.co/4mnsO3D

I started learning #React Native today and I want to quite already :D #JavaScript #toolsHell #tehranjs

Unit 42 recently identified an unattributed group leveraging the recent #ToolShell exploits to deliver 4L4MD4R #ransomware on July 27th 2025. More info at bit.ly/4l76eL4

Update: See newly added info to our #ToolShell Alert. We’ve included info on ransomware deployment, new webshells involved in exploitation, & detection guidance 👉 go.dhs.gov/i4J

Update: As we continue to monitor the scope & impact of #ToolShell, we’ll update our related Alert with new info. Today, we’ve added info on new CVEs & additional mitigations on exploitation activity. 👉 go.dhs.gov/i4J

🔴 CVE-2025-53770 (CVSS 9.8): Critical SharePoint RCE actively exploited as part of #ToolShell 👀 9,762 hosts online (Censys): hubs.ly/Q03y6BW80 🔎@GreyNoiseIO flagged + Censys scans show RDP TCP/3389 using “alikullab1” untrusted cert #CVE202553770 #SharePoint

We added Microsoft SharePoint server remote code execution vulnerability CVE-2025-53770 to our Known Exploited Vulnerabilities Catalog. Visit go.dhs.gov/Z3Q & apply mitigations to protect your org from cyberattacks. #ToolShell

Microsoft has issued a security update for SharePoint Subscription Edition which mitigates CVE-2025-53770 and CVE-2025-53771. Defenders should apply the update immediately.🫡 #Cybersecurity #Sharepoint #toolshell microsoft.com/en-us/download…

🚨 Research update: #ToolShell is back, and it just leveled up. Two new vulnerabilities in Microsoft SharePoint Server, CVE-2025-53770 (RCE) and CVE-2025-53771 (auth bypass), are being actively exploited in the wild. 🔓 Attackers are chaining them to >> • Bypass authentication…

Something went wrong.
Something went wrong.
United States Trends
- 1. Branch 38.4K posts
- 2. Red Cross 59.2K posts
- 3. Chiefs 113K posts
- 4. #njkopw 11.1K posts
- 5. Knesset 20.2K posts
- 6. Lions 90.6K posts
- 7. Exceeded 5,981 posts
- 8. Binance DEX 5,216 posts
- 9. Rod Wave 1,755 posts
- 10. Mahomes 35.1K posts
- 11. Air Force One 60.4K posts
- 12. #LaGranjaVIP 84.6K posts
- 13. Use GiveRep N/A
- 14. Eitan Mor 19.4K posts
- 15. #LoveCabin 1,411 posts
- 16. Ziv Berman 22.9K posts
- 17. Alon Ohel 20.1K posts
- 18. Tel Aviv 62.8K posts
- 19. #TNABoundForGlory 61K posts
- 20. Matan Angrest 18K posts