#toolshell resultados da pesquisa
Blog for ToolShell Disclaimer: The content of this blog is provided for educational and informational purposes only. blog.viettelcybersecurity.com/sharepoint-too… #SharePoint #ToolShell

I started learning #React Native today and I want to quite already :D #JavaScript #toolsHell #tehranjs
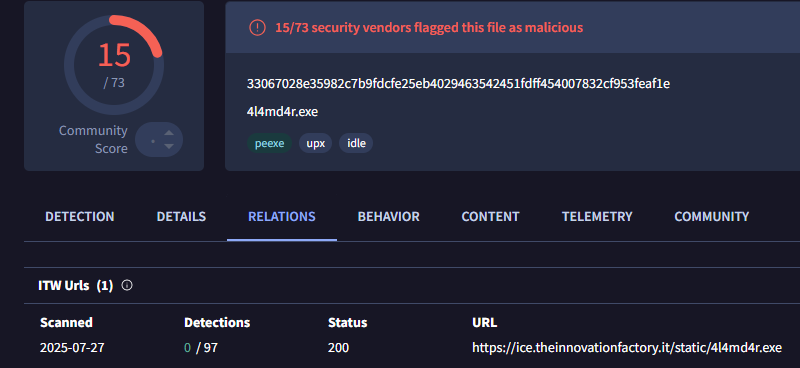
Unit 42 recently identified an unattributed group leveraging the recent #ToolShell exploits to deliver 4L4MD4R #ransomware on July 27th 2025. More info at bit.ly/4l76eL4

Viettel Cyber Security Press Release for Customer alert, Latest research and Recommendations. Blog is comming viettelsecurity.com/microsoft-shar… #SharePoint #ToolShell

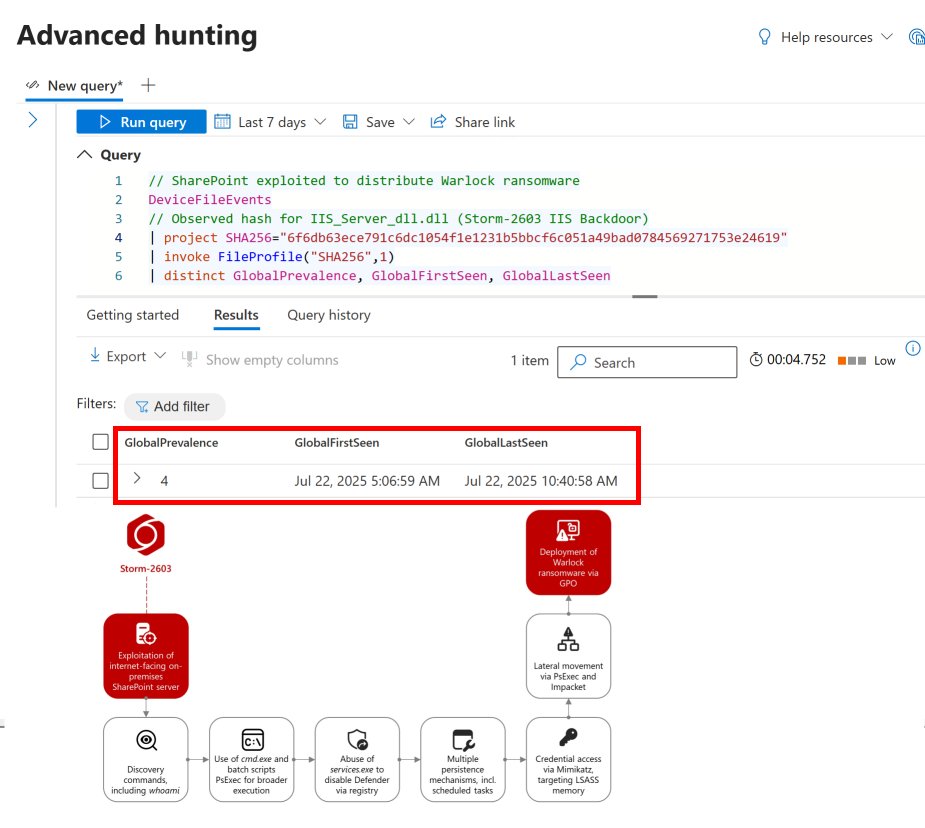
#ToolShell #Warlock 🚨 KQLWizard intel update: Storm-2603 exploited CVE-2025-53770 on 4 internet-facing SharePoint servers on 22 July, deploying Warlock ransomware via ToolShell. Initial access confirmed via observed hash for IIS_Server_dll.dll (Storm-2603 IIS Backdoor).…
"Mimo" Gang used #Sharepoint #ToolShell to deliver "4l4md4r" #ransomware, which is written in Go language and contains religious-style function names. Report: mp.weixin.qq.com/s/h6_ijQAHhq4t…
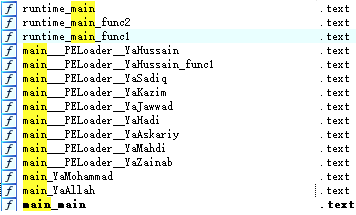
Quck analysis of new #ToolShell payload observed by @leak_ix: Paylaod is a .dll executed in memory. Sha-256: 3461da3a2ddcced4a00f87dcd7650af48f97998a3ac9ca649d7ef3b7332bd997 It collects System Info and the sensitive machine key. Sends back in response. Single Request takeover.

⚠️ New payload in the relation to #ToolShell . Attackers now don't need the static file anymore, leaking keys from memory without leaving the file. This means the existence of a file is not a reliable IoC anymore.
We’ve released a Malware Analysis Report with analysis & detection signatures on files related to Microsoft SharePoint vulnerabilities known as #ToolShell. Review IOCs and detection signatures in our 🆕report 👉 cisa.gov/news-events/an…
Malicious actors are exploiting RCE vulnerability CVE-2025-53770 to compromise on-prem SharePoint servers. See our Alert for info & mitigations on exploitation activity, known as #ToolShell. 👉go.dhs.gov/iZZ

China associated #hackers have leveraged the #ToolShell #vulnerability (CVE-2025-53770) in #Microsoft #SharePoint #cyberattacks targeting government agencies, universities, telecommunication service providers, and finance organisations. #CyberSecurity ift.tt/SM98RkY

Attacker IP addresses Update #toolshell welivesecurity.com/en/eset-resear…

ToolShell Mass Exploitation (CVE-2025-53770) Stealing machine keys to maintain persistent access SharePoint -> The exchange server is the next target research.eye.security/sharepoint-und…

SharePoint脆弱性を悪用する #ToolShell に注意!🇨🇳中国系攻撃グループによる悪用も報告されていますが、#ESET もLuckyMouseに関連するバックドアを検出。ESETの監視結果はブログで掲載→ htps://www.eset.com/jp/blog/welivesecurity/toolshell-an-all-you-can-eat-buffet-for-threat-actors-jp/

CISA Adds One Known Exploited Vulnerability, CVE-2025-53770 “ToolShell,” to Catalog cisa.gov/news-events/al… #Cybersecurity #Sharepoint #toolshell
We added Microsoft SharePoint server remote code execution vulnerability CVE-2025-53770 to our Known Exploited Vulnerabilities Catalog. Visit go.dhs.gov/Z3Q & apply mitigations to protect your org from cyberattacks. #ToolShell

"#Chinese Threat Actors #Exploit #ToolShell #SharePoint Flaw Weeks After #Microsoft's July Patch" thehackernews.com/2025/10/chines… I'm sure "FUCK Microsoft!!!!!!" is what many admin's are saying right now. @Microsoft=💩 #Linux =🐧 #CyberSecurityNews #TechNews #Windows #WindowsServer
🚨 Research update: #ToolShell is back, and it just leveled up. Two new vulnerabilities in Microsoft SharePoint Server, CVE-2025-53770 (RCE) and CVE-2025-53771 (auth bypass), are being actively exploited in the wild. 🔓 Attackers are chaining them to >> • Bypass authentication…

The "no shell" activity cluster was seen exploiting the SharePoint vuln on 17th - one day ahead of others - using no filesystem artifacts. Very cool finding by @TomHegel and friends at @LabsSentinel #toolshell #noshell Link to the blog below ->

Microsoft has issued a security update for SharePoint Subscription Edition which mitigates CVE-2025-53770 and CVE-2025-53771. Defenders should apply the update immediately.🫡 #Cybersecurity #Sharepoint #toolshell microsoft.com/en-us/download…
In light of recent #toolshell events and a DFIR engagement, my colleagues and I put together an article detailing the analysis of post-exploitation activity on affected #Sharepoint servers - specifically, analysis of the "Godzilla" in-memory webshell. kerberpoasting.medium.com/sharepoint-of-…
🔎 ToolShell's original SharePoint RCE (CVE-2025-49704): demoed at Pwn2Own; PoCs on GitHub; observed exploited in the wild since July 7. #Microsoft #ToolShell #SharePoint ➡️ t.me/avleonovcom/16…

🛡️【今日の出来事|ラックが「LAC Security Insight 2025秋」公開】 2025年11月13日、株式会社ラックが最新レポート「LAC Security Insight 第14号 2025秋」を発表 注目は「ToolShell」 セキュリティ担当者必読 #セキュリティ #JSOC #ToolShell #マルウェア #LAC #インシデント対応 #脅威分析
#China-linked hackers exploit patched #ToolShell flaw to breach Middle East Telecom securityaffairs.com/183800/securit… #securityaffairs #hacking @symantec
Chinese-linked hackers exploited the ToolShell SharePoint vulnerability (CVE-2025-53770) shortly after Microsoft’s patch, targeting telecoms in the Middle East and beyond using loaders like Zingdoor and KrustyLoader. #ToolShell #MiddleEast ift.tt/05a8Uyc
China associated #hackers have leveraged the #ToolShell #vulnerability (CVE-2025-53770) in #Microsoft #SharePoint #cyberattacks targeting government agencies, universities, telecommunication service providers, and finance organisations. #CyberSecurity ift.tt/SM98RkY

Warlock ransomware surfaced mid-2025 via exploitation of a Microsoft SharePoint zero-day (CVE-2025-53770), linked to China-backed group Storm-2603 using reused stolen certs and DLL sideloading techniques. #China #ToolShell #LockBit ift.tt/lZ8enaR
Chinese threat groups Linen Typhoon and Violet Typhoon exploit ToolShell vulnerability to breach governments, telecoms, and universities in Africa and South America, deploying Zingdoor, ShadowPad, and ransomware. #Africa #ToolShell #ChineseEspionage ift.tt/krOFM5q
"#Chinese Threat Actors #Exploit #ToolShell #SharePoint Flaw Weeks After #Microsoft's July Patch" thehackernews.com/2025/10/chines… I'm sure "FUCK Microsoft!!!!!!" is what many admin's are saying right now. @Microsoft=💩 #Linux =🐧 #CyberSecurityNews #TechNews #Windows #WindowsServer
Actores de amenazas con vínculos con China explotaron la vulnerabilidad de seguridad de #ToolShell en #MicrosoftSharePoint para atacar a una empresa de telecomunicaciones en Medio Oriente. #2025 #Infosec #BT thehackernews.com/2025/10/chines…
#Warlock #ransomware: Old actor, new tricks? - #ToolShell vuln used in attacks by China-based actor. Read more: security.com/threat-intelli…
#ToolShell Used to Compromise Telecoms Company in Middle East - #ZingDoor and #KrustyLoader also used in attacks that hit victims in a variety of countries and sectors. Read more: security.com/threat-intelli…
#ToolShell Used to Compromise Telecoms Company in Middle East | By @symantec ↘️ security.com/blog-post/tool…
🚨 China-linked actors exploited a patched Microsoft SharePoint ToolShell flaw, breaching telcos & govts worldwide. Details: thehackernews.com/2025/10/chines… #ChineseHackers #SharePoint #ToolShell #CyberAttack #InfoSec
Sharepoint ToolShell attacks targeted orgs across four continents reconbee.com/sharepoint-too… #sharepoint #Toolshell #Vulnerability #china #hackers #hacking
reconbee.com
Sharepoint ToolShell attacks targeted orgs across four continents
Sheathminer/Violet Typhoon—had taken use of ToolShell read more about Sharepoint ToolShell attacks targeted orgs across four continents
#Sharepoint #ToolShell #attacks targeted orgs across four continents scyscan.com/news/sharepoin…
scyscan.com
Sharepoint ToolShell attacks targeted orgs across four continents | ScyScan
Hackers believed to be associated with China have leveraged the ToolShell vulnerability (CVE-2025-53770) in Microsoft SharePoint in attacks targeting governm...
Chinese threat actors exploit the ToolShell vulnerability (CVE-2025-53770) in Microsoft SharePoint, targeting organizations across Middle East, South America, Africa, Europe, and the U.S. using malware like Zingdoor and ShadowPad. #ToolShell #UnitedStates ift.tt/94TGgZL
hendryadrian.com
Sharepoint ToolShell attacks targeted orgs across four continents
Chinese hacker groups are exploiting the ToolShell vulnerability (CVE-2025-53770) in Microsoft SharePoint to target various global organizations through sophisticated side-loading malware techniques....
China-linked hackers exploited SharePoint's ToolShell (CVE-2025-53770) in global attacks on gov, academic, telco, & finance orgs. Read more! bleepingcomputer.com/news/security/… #SharePoint #ToolShell #CyberAttack
🔎 ToolShell's original SharePoint RCE (CVE-2025-49704): demoed at Pwn2Own; PoCs on GitHub; observed exploited in the wild since July 7. #Microsoft #ToolShell #SharePoint ➡️ t.me/avleonovcom/16…

Blog for ToolShell Disclaimer: The content of this blog is provided for educational and informational purposes only. blog.viettelcybersecurity.com/sharepoint-too… #SharePoint #ToolShell

Unit 42 recently identified an unattributed group leveraging the recent #ToolShell exploits to deliver 4L4MD4R #ransomware on July 27th 2025. More info at bit.ly/4l76eL4

Viettel Cyber Security Press Release for Customer alert, Latest research and Recommendations. Blog is comming viettelsecurity.com/microsoft-shar… #SharePoint #ToolShell

I started learning #React Native today and I want to quite already :D #JavaScript #toolsHell #tehranjs

SharePoint脆弱性を悪用する #ToolShell に注意!🇨🇳中国系攻撃グループによる悪用も報告されていますが、#ESET もLuckyMouseに関連するバックドアを検出。ESETの監視結果はブログで掲載→ htps://www.eset.com/jp/blog/welivesecurity/toolshell-an-all-you-can-eat-buffet-for-threat-actors-jp/

Zero-day #ToolShell is being actively exploited in the wild, targeting on-prem #SharePoint servers with unauth RCE. ⚠️ CVEs: CVE-2025-53770 (RCE) + CVE-2025-53771 (Auth Bypass) 🧠 ToolPane.aspx abused for deserialization & webshells 🔐 Attackers steal MachineKeys, go fileless, &…

Une faille #SharePoint a touché l’Agence nucléaire 🇺🇸, exploitée via un zero-day par des hackers d’État 🇨🇳. Microsoft a patché, mais l’alerte est orange : environnements on-prem = risque +. Passez le patch #ToolShell dès maintenant. v/@nextinpact ow.ly/Czus50Wv9M0

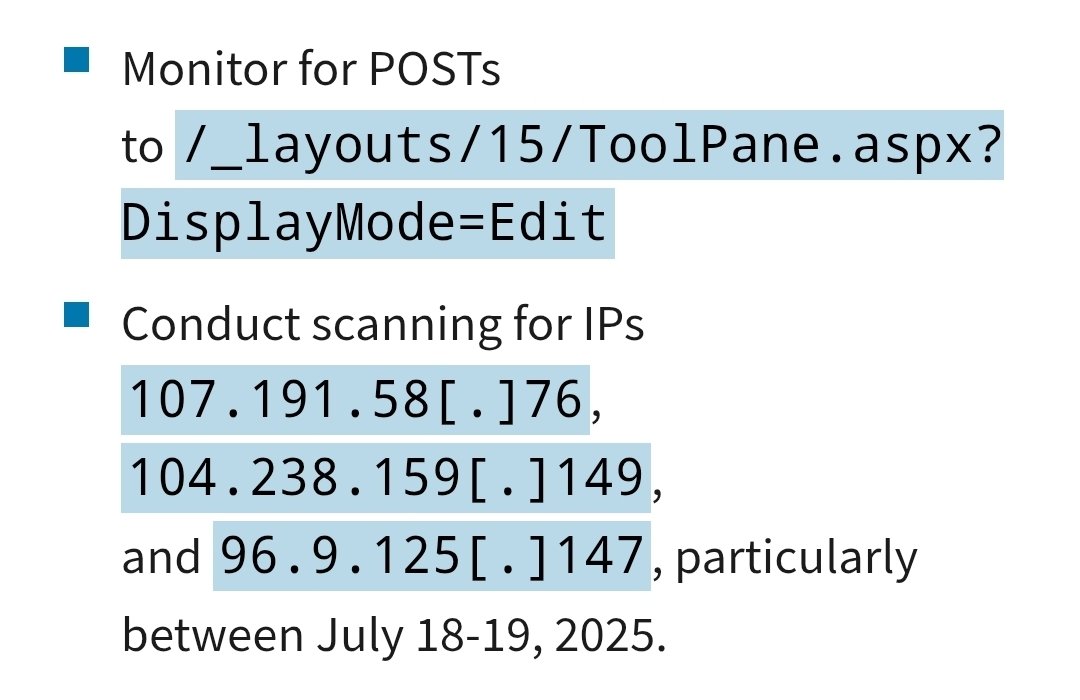
New threat actor possibly behind SharePoint RCE Exploit (CVE-2025-53770) One of the IPs used in the attack, 96.9.125.147, is hosting a WordPress site at dynastyjusticecollective[.]site. The domain was registered on July 18. #Xfensive #SharePoint #ToolShell #ThreatIntel
![raffaele_forte's tweet image. New threat actor possibly behind SharePoint RCE Exploit (CVE-2025-53770)
One of the IPs used in the attack, 96.9.125.147, is hosting a WordPress site at dynastyjusticecollective[.]site.
The domain was registered on July 18.
#Xfensive #SharePoint #ToolShell #ThreatIntel](https://pbs.twimg.com/media/GwYFwPRXsAAWvUP.png)
"Mimo" Gang used #Sharepoint #ToolShell to deliver "4l4md4r" #ransomware, which is written in Go language and contains religious-style function names. Report: mp.weixin.qq.com/s/h6_ijQAHhq4t…


Quck analysis of new #ToolShell payload observed by @leak_ix: Paylaod is a .dll executed in memory. Sha-256: 3461da3a2ddcced4a00f87dcd7650af48f97998a3ac9ca649d7ef3b7332bd997 It collects System Info and the sensitive machine key. Sends back in response. Single Request takeover.

⚠️ New payload in the relation to #ToolShell . Attackers now don't need the static file anymore, leaking keys from memory without leaving the file. This means the existence of a file is not a reliable IoC anymore.
Malicious actors are exploiting RCE vulnerability CVE-2025-53770 to compromise on-prem SharePoint servers. See our Alert for info & mitigations on exploitation activity, known as #ToolShell. 👉go.dhs.gov/iZZ

CISA Adds One Known Exploited Vulnerability, CVE-2025-53770 “ToolShell,” to Catalog cisa.gov/news-events/al… #Cybersecurity #Sharepoint #toolshell

#ToolShell #Warlock 🚨 KQLWizard intel update: Storm-2603 exploited CVE-2025-53770 on 4 internet-facing SharePoint servers on 22 July, deploying Warlock ransomware via ToolShell. Initial access confirmed via observed hash for IIS_Server_dll.dll (Storm-2603 IIS Backdoor).…

Attacker IP addresses Update #toolshell welivesecurity.com/en/eset-resear…

ToolShell Mass Exploitation (CVE-2025-53770) Stealing machine keys to maintain persistent access SharePoint -> The exchange server is the next target research.eye.security/sharepoint-und…

El equipo de #ESETResearch ha estado monitoreando una serie de ataques que explotan las #vulnerabilidades zero-day recientemente descubiertas en Microsoft SharePoint, conocidas como #ToolShell bit.ly/46wma5V vía @ESETLA

🔴 CVE-2025-53770 (CVSS 9.8): Critical SharePoint RCE actively exploited as part of #ToolShell 👀 9,762 hosts online (Censys): hubs.ly/Q03y6BW80 🔎@GreyNoiseIO flagged + Censys scans show RDP TCP/3389 using “alikullab1” untrusted cert #CVE202553770 #SharePoint

Une faille #SharePoint a touché l’Agence nucléaire 🇺🇸, exploitée via un zero-day par des hackers d’État 🇨🇳. Microsoft a patché, mais l’alerte est orange : environnements on-prem = risque +. Passez le patch #ToolShell dès maintenant. v/@nextinpact ow.ly/I56e50Wv5ez

We added Microsoft SharePoint server remote code execution vulnerability CVE-2025-53770 to our Known Exploited Vulnerabilities Catalog. Visit go.dhs.gov/Z3Q & apply mitigations to protect your org from cyberattacks. #ToolShell

🚨 #ToolShell attacks exploiting #SharePoint vulnerabilities have resulted in in sensitive data exfiltration from internet-exposed SharePoint servers – a wake-up call for organizations. Learn more: hubs.ly/Q03ysRBk0

Something went wrong.
Something went wrong.
United States Trends
- 1. Mamdani 187K posts
- 2. Ukraine 560K posts
- 3. Egg Bowl 1,320 posts
- 4. #HMGxBO7Sweeps N/A
- 5. Putin 192K posts
- 6. #KayJewelers N/A
- 7. Adolis Garcia N/A
- 8. DON'T TRADE ON MARGIN N/A
- 9. Geraldo 2,665 posts
- 10. #pilotstwtselfieday 1,154 posts
- 11. #FursuitFriday 14.1K posts
- 12. Anthony Joshua 5,716 posts
- 13. Happy Thanksgiving 3,763 posts
- 14. Start Cade N/A
- 15. Tamera N/A
- 16. Zelensky 124K posts
- 17. Kenyon 2,413 posts
- 18. Shabbat Shalom 6,446 posts
- 19. Keith Carter N/A
- 20. Goodwill 3,411 posts