#webappsec search results
🚀 Day 2 of 30: 🛠 - Identify Target Subdomains! Start with tools like - Facebook certificate transparency - Google certificate transparency - Findomain - subjack etc. 🔍 These tools save you time by gathering data from multiple sources. #WebAppSec #bugbountytips #bugbounty…

Don't Underestimate HTTP Desync Attacks! HTTP Request Smuggling can lead to cache poisoning, XSS, and more. Make sure you know how to handle such vulnerabilities to keep your applications safe! #CyberSecurity #WebAppSec

Mind the Headers: HTTP Security Headers (X-Frame-Options, X-Content-Type-Options, etc.) are crucial for defending against various attacks. Ensure your web app is fortified! #WebAppSec

Today, I have a great resource reminder - which I have shared before - that I believe will be very useful for those who are improving themselves in the field of Web Application Security❗️🤓 Don't forget to add it to your bookmarks.🌸 Link: media.licdn.com/dms/document/m… #webappsec

According to my VM update this morning @zaproxy 2.16.0 is now available on @kalilinux #DAST #PenTest #WebAppSec #AppSec #RedTeam #PurpleTeam

When going for Blind #XSS attempts, it's better to use a polyglot since we don't know the context of the injection in advance. Just saying. 😎 #WebAppSec #BugBounty #PenTesting

Here's my research about Python dirty Arbitrary File Write to RCE via overwriting shared object files or overwriting bytecode files. Enjoy! siunam321.github.io/research/pytho… #Research #WebAppSec
🛠️ Webinar — Writing Your First Burp Extension 📅 28 Aug 2025 | 🕘 9–10 PM 🎤 Speaker: Marcus (a.k.a benkyou) 🔗 Join: linkedin.com/feed/update/ur… #CyberSecurity #BurpSuite #WebAppSec #CTF #Webinar

⚡ Webinar — Next.js Middleware Bypass & How to Detect It 📅 29 Sept 2025 | 🕘 9–10 PM 🎤 Speaker: @takeptoto 🔗 meet.google.com/tza-umrb-you #CyberSecurity #Nextjs #WebAppSec #CTF #Webinar

Here's my attempted research in PHP class pollution! Although I couldn't escape the object context and pollute other classes, it's still interesting that we can pollute the object's attributes and associative array's keys. siunam321.github.io/research/attem… #Research #WebAppSec
Stay one step ahead of attackers by discovering essential best practices to secure your web applications and protect sensitive data. #CyberSecurity #WebAppSec #OWASP #cybersecurityawareness
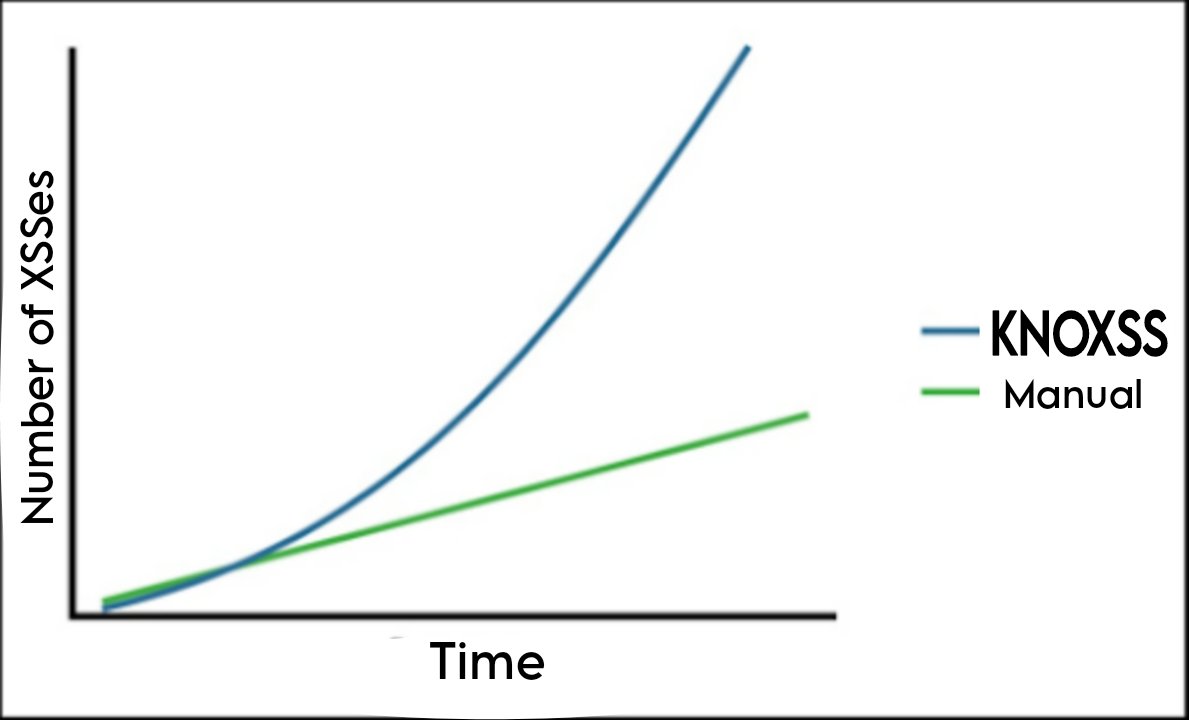
KNOXSS is about productivity! Even if you check manually all the #XSS cases KNOXSS is able to detect, you could not do it 1000s of times in a row. Across a large number of URLs, KNOXSS is able to detect many more XSSes than you can over time. #WebAppSec #BugBounty #PenTesting
Millions of websites at risk! A new vulnerability in ImunifyAV could allow hackers to take control of infected sites. What's being done to protect online security? 🚨 #imunify360 #cybersecurityweaknesses #webappsec #onlinevulnerabilities securityweek.com/imunify360-vul…
I learned how web apps work behind the scenes (from HTML/CSS/JS to servers & databases) and how vulnerabilities like SQL Injection, XSS, & CSRF can expose critical systems. academy.hackthebox.com/achievement/21… #CyberSecurity #OWASP #WebAppSec #CloudSecurity #hackthebox #htbacademy
BypaXSS - The Brute Art of Bypass Slides from the @BugBountyArg @ekoparty 2025 talk #XSS #Bypass #WebAppSec docs.google.com/presentation/d…
هانتر واقعی: صبحانهاش قهوه، ناهارش PoC و عصرش ایمیل بونتیِ تاییدشده 💻☕️📬 #BugBounty #WebAppSec
SessionReaper in Magento hijacks live shopper sessions, stealing carts and credentials. Patch now and enforce secure session IDs. malwarebytes.com/blog/news/2025… #infosec #Magento #WebAppSec
if HttpOnly or secure flags are missing, session theft becomes easier.#WebAppSec🍪
Talking about #SSRF, I just got an idea to add SSRF-based #XSS to @KN0X55 ! It's coming in the update next week most probably. #WebAppSec #BugBounty #PenTesting
You have to be really good manually in order to beat KNOXSS testing 1000's of URLs automatically for every possible #XSS scenario it can detect and prove. 😊 Those XSS scenarios. 👇 knoxss.pro/?page_id=766 #WebAppSec #BugBounty #PenTesting

XSS Without Parentheses location=tagName <JavaScript:"\74Svg\57OnLoad\75\141\154\145\162\164\501\51\76"/ContentEditable/AutoFocus/OnFocus=location=tagName> PoC: x55.is/brutelogic/gym… knoxss.pro - #XSS made easy. Try it now! #WebAppSec #PenTesting #BugBounty

🚀 Day 2 of 30: 🛠 - Identify Target Subdomains! Start with tools like - Facebook certificate transparency - Google certificate transparency - Findomain - subjack etc. 🔍 These tools save you time by gathering data from multiple sources. #WebAppSec #bugbountytips #bugbounty…

Today, I have a great resource reminder - which I have shared before - that I believe will be very useful for those who are improving themselves in the field of Web Application Security❗️🤓 Don't forget to add it to your bookmarks.🌸 Link: media.licdn.com/dms/document/m… #webappsec

🔍 How to crush it in bug hunting and web application pentesting effectively! Uncover vulnerabilities, master recon techniques, and level up your security skills. 🚀 🔗vivekpentest.com/2024/06/Bug%20… #BugBounty #WebAppSec #Pentesting #CyberSecurity #EthicalHacking #InfoSec #bugbounty
According to my VM update this morning @zaproxy 2.16.0 is now available on @kalilinux #DAST #PenTest #WebAppSec #AppSec #RedTeam #PurpleTeam

When going for Blind #XSS attempts, it's better to use a polyglot since we don't know the context of the injection in advance. Just saying. 😎 #WebAppSec #BugBounty #PenTesting

Get serious about #XSS! Sign up or upgrade. knoxss.pro - built for pros. #WebAppSec #BugBounty #Pentesting

Don't miss any of our #XSS tips and tricks, bypasses, memes, promos and coupons. 🤓 Hit the 🔔 in our profile page like below! #WebAppSec #BugBounty #PenTesting
Improve Your #XSS Reports! ✅ Turn your PoC into a remote script call to load a proper attack code with import() ✅ Build a CSRF attack by stealing the anti-CSRF token and then changing some user info like their email address #WebAppSec #BugHunting #Pentesting

Run away from outdated #XSS resources out there. The "src" attribute of "img" doesn't need content to pop with "onerror" but you can use a smart one for a staged payload. Calling a remote script is the best way to report a #XSS vulnerability. #WebAppSec #BugBounty #PenTesting

Mind the Headers: HTTP Security Headers (X-Frame-Options, X-Content-Type-Options, etc.) are crucial for defending against various attacks. Ensure your web app is fortified! #WebAppSec

Don't Underestimate HTTP Desync Attacks! HTTP Request Smuggling can lead to cache poisoning, XSS, and more. Make sure you know how to handle such vulnerabilities to keep your applications safe! #CyberSecurity #WebAppSec

Something went wrong.
Something went wrong.
United States Trends
- 1. Chris Paul 7,803 posts
- 2. Pat Spencer 2,674 posts
- 3. Kerr 5,639 posts
- 4. Podz 3,301 posts
- 5. Jimmy Butler 2,659 posts
- 6. Shai 15.7K posts
- 7. Seth Curry 4,984 posts
- 8. The Clippers 10.6K posts
- 9. Hield 1,590 posts
- 10. Carter Hart 4,121 posts
- 11. #DubNation 1,433 posts
- 12. Lawrence Frank N/A
- 13. #SeanCombsTheReckoning 5,196 posts
- 14. Mark Pope 1,970 posts
- 15. #AreYouSure2 133K posts
- 16. Kuminga 1,498 posts
- 17. Brandy 8,334 posts
- 18. Derek Dixon 1,314 posts
- 19. Elden Campbell N/A
- 20. Connor Bedard 2,459 posts
































