#cyberautomation search results
AI Agents are shaping how automation scales in cybersecurity and beyond. #AIAgents #CyberAutomation #PerisAI #Cybersecurity #YouBuild #WeGuard

Security isn’t about adding tools, it’s about aligning them. True resilience comes from orchestration, automation, and focus on what matters: response time, not dashboard count. #CyberAutomation #SecurityOperations #BrahmaFusion #PerisAI #YouBuild #WeGuard

We are extremely thankful for our customers, partners, and team here at Vonahi Security! This has been an absolutely amazing year and we're excited to be part of #cyberautomation. Happy Thanksgiving and have a cyber safe black Friday! #vonahisec #cybersecurity #infosec

For those of you who know me well, you know that I use a lot of business process automation in my own business, as well as with my clients systems to help them solve problems efficiently and consistently. How #CyberAutomation can help you get back time? learn.saferinternetproject.com

Users rave about PinguProxy's automated cybersecurity features, saying effortless geo-targeting & instant IP activation let them focus on development without worrying about proxy management! #proxysecurity #cyberautomation
A processor or any other complex circuitry may be thought of as a building. The chip is not an esoteric realm where wizards work magic. It is a structural form created to contain a transforming #cyberautomation process. It is therefore a place of business.
Putting a fine point on it, there is no process at all without the chip. Today's chips are naked and dumb. They are protected by a thin veneer of software and modular hardware which both offer large attack surfaces. Are we ready for AI and #cyberautomation?
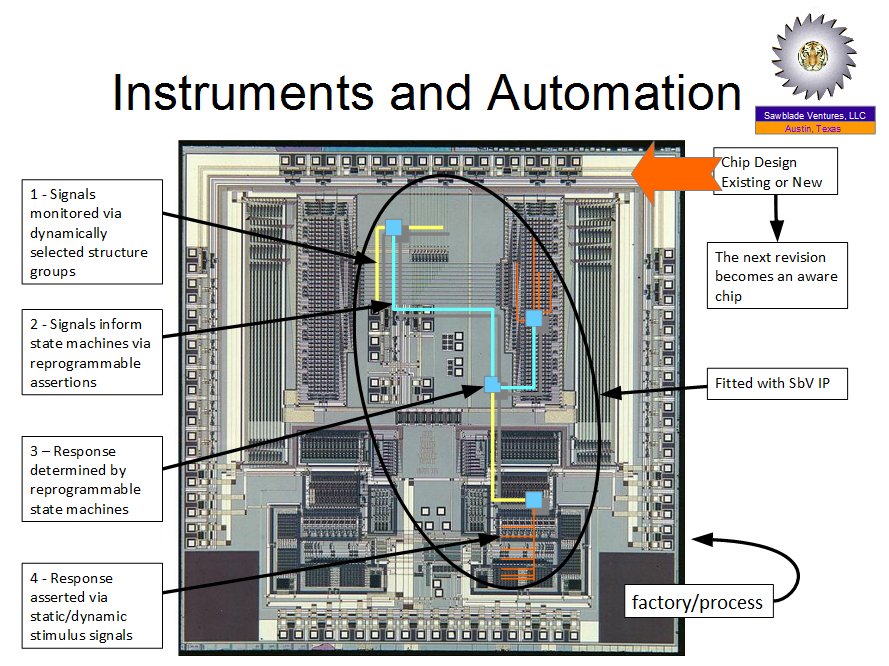
Lightning Talks (Part One): youtube.com/watch?v=l9SgsW… Lightning Talks (Part Two): youtube.com/watch?v=2bKU2s… #CybersecurityAwarenessMonth #cyberautomation #OASIS #securityorchestration #cybersecurity #openstandards

youtube.com
YouTube
Lightning Talks (Part Two): Paul Wormeli and Vaughn Shanks
Automate your cybersecurity tasks like updates and backups. It’s easy, fast, and keeps you protected. 🔒 Boost your defenses today with automation tools! #CyberSecurity #SecureOurWorld #CyberAutomation #DataProtection #ITSecurity#CybersecurityTips #DataSafety #StreamlineSecurity
BFW announces a wholly owned subsidiary m2nxt. automationrobotics.in/bfw-announces-… #smartmanufacturing #cyberautomation #automation #automations #automationsolution #automationsolutions #bharatfritzwerner #digitisation #industrialiot #iot #robotics #robotic #dataanalytics

Automate, protect, and grow. 🚀 iSecureCyber keeps your small business secure from vendor risks with intelligent, automated solutions. #CyberAutomation #BusinessSafety #VendorProtection #CyberSecurityMadeEasy

Automation is reshaping cybersecurity strategies. Automated tools can help detect threats faster and respond more efficiently, reducing the risk of breaches. #CyberAutomation #ThreatResponse #FutureOfSecurity

Parasitic automation can be thought of as a benevolent operation separate and uncoupled to the host operations yet using host transactions as drivers for manipulative efforts as required or desired without host involvement. #CyberAutomation

SIXGEN, a services provider of cybersecurity products and expertise to U.S. national intelligence, defense and critical infrastructure customers and backed by Washington Harbour Partners, has purchased Boldend Inc., #CyberAutomation themiddlemarket.com/latest-news/wh…
Automation is the future of cybersecurity. From threat detection to incident response, automated solutions can reduce human error and speed up response times. #CyberAutomation #RiskAware #StayAhead #CyberResilience

Proactive Cybersecurity – Staying Ahead of Threats with a Preventive Approach bit.ly/45FnPVT #DetectionAsCode #ThreatDetection #CyberAutomation #SecurityOperations #IntelligentSecurity #CyberDefense #TechUnity

Detection as code: Revolutionizing security operations through automated, intelligent threat detection bit.ly/4fxywgv #DetectionAsCode #ThreatDetection #CyberAutomation #SecurityOperations #IntelligentSecurity #CyberDefense #TechUnity

Security isn’t about adding tools, it’s about aligning them. True resilience comes from orchestration, automation, and focus on what matters: response time, not dashboard count. #CyberAutomation #SecurityOperations #BrahmaFusion #PerisAI #YouBuild #WeGuard

AI Agents are shaping how automation scales in cybersecurity and beyond. #AIAgents #CyberAutomation #PerisAI #Cybersecurity #YouBuild #WeGuard

Users rave about PinguProxy's automated cybersecurity features, saying effortless geo-targeting & instant IP activation let them focus on development without worrying about proxy management! #proxysecurity #cyberautomation
Lightning Talks (Part One): youtube.com/watch?v=l9SgsW… Lightning Talks (Part Two): youtube.com/watch?v=2bKU2s… #CybersecurityAwarenessMonth #cyberautomation #OASIS #securityorchestration #cybersecurity #openstandards

youtube.com
YouTube
Lightning Talks (Part Two): Paul Wormeli and Vaughn Shanks
Proactive Cybersecurity – Staying Ahead of Threats with a Preventive Approach bit.ly/45FnPVT #DetectionAsCode #ThreatDetection #CyberAutomation #SecurityOperations #IntelligentSecurity #CyberDefense #TechUnity

Detection as code: Revolutionizing security operations through automated, intelligent threat detection bit.ly/4fxywgv #DetectionAsCode #ThreatDetection #CyberAutomation #SecurityOperations #IntelligentSecurity #CyberDefense #TechUnity

Most businesses don’t need a big IT team. They need a smart MSP with layered protection, monitoring, and automation. You don’t need 10 people. You need one system that works. #SmallBusinessIT #MSPModel #CyberAutomation
AI-powered XDR platforms are reducing threat response time while improving SOC threat detection accuracy. #XDR #CyberAutomation
45% faster response with AI-powered security. Explore how C1’s AI-enhanced framework helps you prevent attacks, detect threats faster, and recover smarter. Download the infographic: hubs.li/Q03y-wX90 #AIinSecurity #CyberAutomation #C1Secure
onec1.com
Transform Your Business, Accelerate Your Security with AI | C1
Explore how C1’s AI-Powered Cyber Security Automation framework accelerates threat detection, response, and recovery—built to protect and scale your business.
Process security event streams in real-time with MQTT/RabbitMQ nodes. n8n enables responsive SecOps automation pipelines. #EventDriven #CyberAutomation #RealtimeProcessing #IoT Build reactive workflows: n8n.partnerlinks.io/id1x55her4mo
Process security event streams in real-time with MQTT/RabbitMQ nodes. n8n enables responsive SecOps automation pipelines. #EventDriven #CyberAutomation #RealtimeProcessing #IoT Build reactive workflows: n8n.partnerlinks.io/id1x55her4mo
SOAR = استجابة تلقائية ذكية Security Orchestration, Automation & Response بدلا من انتظار تدخل الفريق، يقوم النظام بالرد على الهجمات تلقائيًا: - عزل جهاز - تعطيل حساب - رفع تنبيه قائد الذكاء الاصطناعي يبرمج السيناريوهات مسبقا #SOAR #CyberAutomation
Automate, protect, and grow. 🚀 iSecureCyber keeps your small business secure from vendor risks with intelligent, automated solutions. #CyberAutomation #BusinessSafety #VendorProtection #CyberSecurityMadeEasy

Automation is the future of cybersecurity. From threat detection to incident response, automated solutions can reduce human error and speed up response times. #CyberAutomation #RiskAware #StayAhead #CyberResilience

Automate your cybersecurity tasks like updates and backups. It’s easy, fast, and keeps you protected. 🔒 Boost your defenses today with automation tools! #CyberSecurity #SecureOurWorld #CyberAutomation #DataProtection #ITSecurity#CybersecurityTips #DataSafety #StreamlineSecurity
Automation is reshaping cybersecurity strategies. Automated tools can help detect threats faster and respond more efficiently, reducing the risk of breaches. #CyberAutomation #ThreatResponse #FutureOfSecurity

For those of you who know me well, you know that I use a lot of business process automation in my own business, as well as with my clients systems to help them solve problems efficiently and consistently. How #CyberAutomation can help you get back time? learn.saferinternetproject.com

TheMiddleMarket: SIXGEN, a services provider of cybersecurity products and expertise to U.S. national intelligence, defense and critical infrastructure customers and backed by Washington Harbour Partners, has purchased Boldend Inc., #CyberAutomation … ift.tt/UQKS6pH
SIXGEN, a services provider of cybersecurity products and expertise to U.S. national intelligence, defense and critical infrastructure customers and backed by Washington Harbour Partners, has purchased Boldend Inc., #CyberAutomation themiddlemarket.com/latest-news/wh…
🤖 Automation is transforming cybersecurity. What tasks or processes do you automate to streamline your cybersecurity workflow? Share your automation tips! #CyberAutomation #TechInnovation
AI Agents are shaping how automation scales in cybersecurity and beyond. #AIAgents #CyberAutomation #PerisAI #Cybersecurity #YouBuild #WeGuard

Security isn’t about adding tools, it’s about aligning them. True resilience comes from orchestration, automation, and focus on what matters: response time, not dashboard count. #CyberAutomation #SecurityOperations #BrahmaFusion #PerisAI #YouBuild #WeGuard

We are extremely thankful for our customers, partners, and team here at Vonahi Security! This has been an absolutely amazing year and we're excited to be part of #cyberautomation. Happy Thanksgiving and have a cyber safe black Friday! #vonahisec #cybersecurity #infosec

BFW announces a wholly owned subsidiary m2nxt. automationrobotics.in/bfw-announces-… #smartmanufacturing #cyberautomation #automation #automations #automationsolution #automationsolutions #bharatfritzwerner #digitisation #industrialiot #iot #robotics #robotic #dataanalytics

For those of you who know me well, you know that I use a lot of business process automation in my own business, as well as with my clients systems to help them solve problems efficiently and consistently. How #CyberAutomation can help you get back time? learn.saferinternetproject.com

Automation is the future of cybersecurity. From threat detection to incident response, automated solutions can reduce human error and speed up response times. #CyberAutomation #RiskAware #StayAhead #CyberResilience

Automation is reshaping cybersecurity strategies. Automated tools can help detect threats faster and respond more efficiently, reducing the risk of breaches. #CyberAutomation #ThreatResponse #FutureOfSecurity

A processor or any other complex circuitry may be thought of as a building. The chip is not an esoteric realm where wizards work magic. It is a structural form created to contain a transforming #cyberautomation process. It is therefore a place of business.

Putting a fine point on it, there is no process at all without the chip. Today's chips are naked and dumb. They are protected by a thin veneer of software and modular hardware which both offer large attack surfaces. Are we ready for AI and #cyberautomation?

Automate, protect, and grow. 🚀 iSecureCyber keeps your small business secure from vendor risks with intelligent, automated solutions. #CyberAutomation #BusinessSafety #VendorProtection #CyberSecurityMadeEasy

Proactive Cybersecurity – Staying Ahead of Threats with a Preventive Approach bit.ly/45FnPVT #DetectionAsCode #ThreatDetection #CyberAutomation #SecurityOperations #IntelligentSecurity #CyberDefense #TechUnity

This level of #cyberautomation of #security means that important personal #information is #encrypted and protected using the same industry-leading technology that #artificialintelligence uses for banks #PISIQ #AI to read more: pisiq.com/services/auton…

Detection as code: Revolutionizing security operations through automated, intelligent threat detection bit.ly/4fxywgv #DetectionAsCode #ThreatDetection #CyberAutomation #SecurityOperations #IntelligentSecurity #CyberDefense #TechUnity

Parasitic automation can be thought of as a benevolent operation separate and uncoupled to the host operations yet using host transactions as drivers for manipulative efforts as required or desired without host involvement. #CyberAutomation

@VDiSTiE offerings on #CyberAutomation #BusinessIntelligence #ArtificialIntelligence #MachineLearning #InternetOfThings #Robotics #CRM #ERP #HCM find more about us bit.ly/VDiSTiE #facebook bit.ly/fbLink #LinkedIn bit.ly/linkLin #India #Africa #vdistie
Are you a a highly technical Cyber Automation & Integrations Specialist? #Apply today to join this Cyber #SOC. Be part of the solution! #CyberAutomation #CyberContentEngineer ow.ly/7vUb50IHBhs
Find out why the Data Loss Prevention (DLP) Team and end users around the world enthusiastically welcomed the enhancements made during this Cyber Automation project bit.ly/3gbenAf #CyberSecurity #CyberAutomation #DLPanalyst

Something went wrong.
Something went wrong.
United States Trends
- 1. Jimmy Cliff 9,358 posts
- 2. Good Monday 38.7K posts
- 3. #MondayMotivation 9,809 posts
- 4. TOP CALL 4,205 posts
- 5. Victory Monday 2,047 posts
- 6. AI Alert 1,910 posts
- 7. The Harder They Come 1,030 posts
- 8. Market Focus 2,898 posts
- 9. #MondayMood 1,292 posts
- 10. Check Analyze N/A
- 11. Token Signal 2,461 posts
- 12. #MondayVibes 2,608 posts
- 13. Happy Thanksgiving 11K posts
- 14. SAROCHA REBECCA DISNEY AT CTW 752K posts
- 15. DOGE 201K posts
- 16. #centralwOrldXmasXFreenBecky 732K posts
- 17. Monad 134K posts
- 18. Soles 83.8K posts
- 19. $NVO 2,253 posts
- 20. NAMJOON 71.6K posts