#cyberdeception نتائج البحث
🍯Great slides from Brent Muir (@Mandiant) about how to deploy #CyberDeception strategies on #ICS and #OT environments. lnkd.in/gk_gGi9b #DEFCON33 #cybersecurity

Welcome, Jennifer Lee, to our team as the North America Channel Sales Director. We are excited about the channel sales leadership Jennifer brings to Acalvio and look forward to her contributions to the next stage of our journey. Welcome, Jennifer! #CyberDeception #ChannelLeader

Happy #cyberdeceptionday! Adversaries are gaining in speed and stealth, as highlighted by the recent CrowdStrike Global Threat Report 2024. Read this blog on why deception technology is a necessary countermeasure to detect threats early and stop breaches. #CyberDeception

At Secure Point Solutions, we use Cyber Deception to identify threats quickly and accurately. Interested in learning more about how we can protect your business? Visit our website at securepointsolutions.com. #CyberDeception #CyberSecurity
ICS Deception Sketchbook: Craft decoys, identity beacons, and misinformation layers to mislead adversaries. #ICSDefense #CyberDeception #OTSecurity treadstone71.com/ics-deception-…
Turn deception into strategy. Build ICS defense blueprints with Treadstone 71. #CyberDeception #ICS #IndustrialCybersecurity treadstone71.com/ics-deception-…
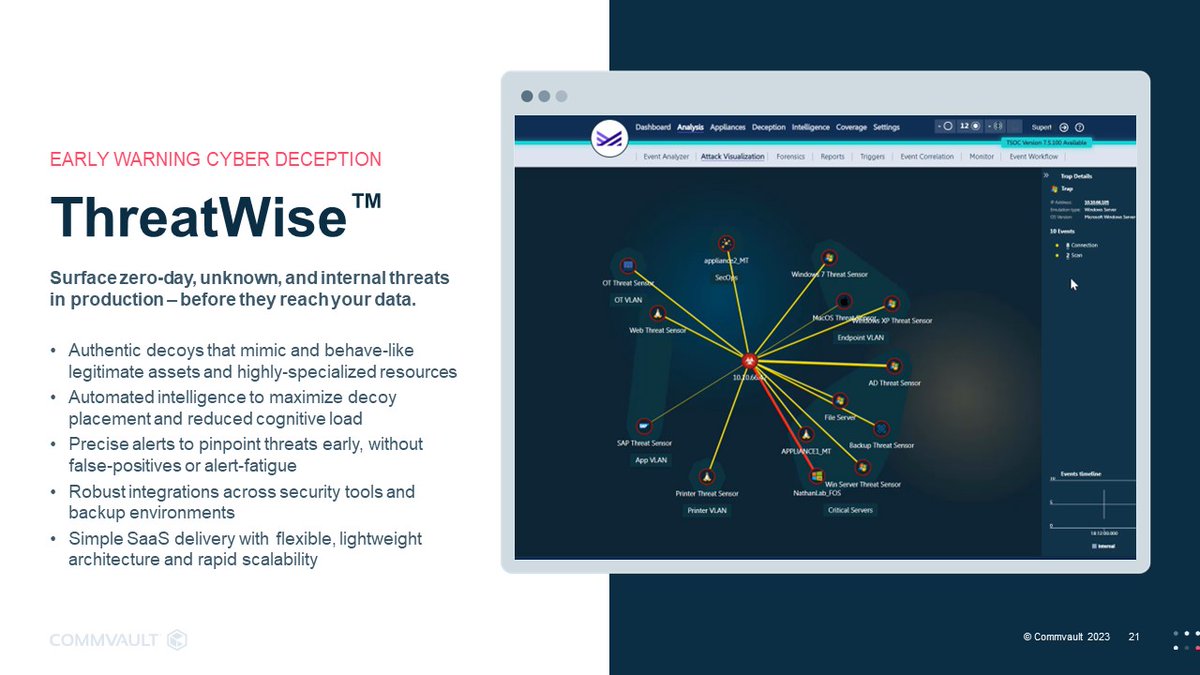
Commvault is the only data protection vendor with in-depth threat monitoring, early warning, and #cyberdeception for production and backup environments. Its new security portfolio is redefining #dataprotection. Read more at New Digital Age: ow.ly/3WMF104LxmK

Can you trust what you see?🕵️♀️ Check out the first in a series of posts on how attackers manipulate their GitHub Profiles to Deceive You. #CyberDeception #GitHub #softwaresupplychainsecurity medium.com/checkmarx-secu…
NCSC collects evidence on #cyberdeception ukauthority.com/articles/ncsc-… @UKAuthority @NCSC #CyberSecurity

Don't miss the webinar tomorrow (July 30) - The Rise Of Insider Threats: Strategies For Cyber Defense. Register now buff.ly/4bxBGgB 👉 Insider threats continue to rise with the increased adoption of cloud services and remote work. #InsiderThreat #CyberDeception

This Thursday, Cyber Deception will be the topic of the new episode of Scaling Cyber. Tune in here: youtu.be/gMnmv7TJE-I Or subscribe in scalingcyber.substack.com #cyberdeception #cybersecuritypodcast

youtube.com
YouTube
Cyber Deception: a must-have tool for defenders | Cybersecurity...
Attending RSA Conference? Meet our founders and cyber deception experts!!! buff.ly/4bbkTAb Our experts are available to demo and discuss use cases of deception technology to protect identities, endpoint and network. #CyberDeception #IdentityProtection

How do you detect a cyber attacker who looks like a legitimate user? Say hello to #CyberDeception, a powerful strategy that flips the script on attackers by creating high-fidelity detection opportunities they can't resist. More below ⬇️

LLMベースのハニーポット登場。Shell/API応答やシステム出力をAI生成し、攻撃者やAIエージェントを誘導。複雑手口の露出やセッション要約も自動化。リアル環境模倣でTTP探索強化。#LLMHoneypot #CyberDeception gbhackers.com/llm-honeypots-…
Webinar on July 30: The Rise Of Insider Threats: Strategies For Cyber Defense buff.ly/4bxBGgB 👉 Insider threats are rising with the increased adoption of cloud services and remote work making it easier for insiders to gain access to sensitive data. #CyberDeception

Join us at The Honeynet Project Workshop 2024 in Copenhagen, Denmark this week. denmark2024.honeynet.org Our co-founder Raj Gopalakrishna will be delivering a keynote “Navigating the Evolving Threat Landscape: Identity Attacks and the Role of Deception Technology” #CyberDeception

Will you be at the RSA Conference 2024 at Moscone Center in San Francisco May 6-9? buff.ly/4bbkTAb Our experts will be available to demo and discuss use cases of deception technology to protect identities, endpoint and network. #CyberDeception #IdentityProtection

Manager, IT Security and Risk Management in the Government Industry gives ShadowPlex Advanced Threat Defense 5/5 Rating in Gartner Peer Insights™ Security Solutions. Read the full review here: gtnr.io/t7fG6ptrC #gartnerpeerinsights #CyberDeception

88% of CISOs and IT Managers believe that threat hunting is rapidly becoming essential. Download our whitepaper to find out how adding #cyberdeception to your security plans can keep your security team a step ahead of adversaries ➡️ eu1.hubs.ly/H04KrDK0

ICS Deception Sketchbook: Craft decoys, identity beacons, and misinformation layers to mislead adversaries. #ICSDefense #CyberDeception #OTSecurity treadstone71.com/ics-deception-…
This Thursday, Cyber Deception will be the topic of the new episode of Scaling Cyber. Tune in here: youtu.be/gMnmv7TJE-I Or subscribe in scalingcyber.substack.com #cyberdeception #cybersecuritypodcast

youtube.com
YouTube
Cyber Deception: a must-have tool for defenders | Cybersecurity...
[SAVE THE DATE] Es la temporada para burlar a los atacantes: Lo que Kevin McCallister de "Mi Pobre Angelito" puede enseñarnos sobre el engaño cibernético. acalvio.com/resources/webi… 🍯MITRE Engage + @AcalvioTech team! #cybersecurity #cyberdeception
Turn deception into strategy. Build ICS defense blueprints with Treadstone 71. #CyberDeception #ICS #IndustrialCybersecurity treadstone71.com/ics-deception-…
TODAY AT 1 PM ET! Leveraging Your Home Field Advantage To Stop Ransomware webinar by Health-ISAC Navigator, @AcalvioTech. portal.h-isac.org/s/community-ev…. #CyberDeception #AIPoweredDeception #Preemptive #Cybersecurity #HoneyToken

Leveraging Your Home Field Advantage To Stop Ransomware webinar by Health-ISAC Navigator, @AcalvioTech on Wednesday, October 29th at 1 PM ET. portal.h-isac.org/s/community-ev…. #CyberDeception #AIPoweredDeception #Preemptive #Cybersecurity #HoneyToken

Leveraging Your Home Field Advantage To Stop Ransomware webinar by Health-ISAC Navigator, @AcalvioTech on Wednesday, October 29th at 1 PM ET. portal.h-isac.org/s/community-ev…. #CyberDeception #AIPoweredDeception #Preemptive #Cybersecurity #HoneyToken

Leveraging Your Home Field Advantage To Stop Ransomware webinar by Health-ISAC Navigator, @AcalvioTech on Wednesday, October 29th at 1 PM ET. portal.h-isac.org/s/community-ev…. #CyberDeception #AIPoweredDeception #Preemptive #Cybersecurity #HoneyToken

🍯Great slides from Brent Muir (@Mandiant) about how to deploy #CyberDeception strategies on #ICS and #OT environments. lnkd.in/gk_gGi9b #DEFCON33 #cybersecurity

#HoneypotSecurity #CyberDeception #ThreatIntelligence #InfosecEducation #ADTECH247 #CyberForensics #BlueTeamOps #DigitalResilience #CyberAwareness #Honeynet facebook.com/share/p/17NmTY…
As cyber threats grow more sophisticated, organizations must adapt to stay ahead. Combining cutting-edge technologies like #AI, hyper-automation, and #cyberdeception lead the way to smarter strategies for resilience and defense. Read more ⬇️ ms.spr.ly/6019s9kaB
LLMベースのハニーポット登場。Shell/API応答やシステム出力をAI生成し、攻撃者やAIエージェントを誘導。複雑手口の露出やセッション要約も自動化。リアル環境模倣でTTP探索強化。#LLMHoneypot #CyberDeception gbhackers.com/llm-honeypots-…
💻⚠️Quantum-powered adversaries are rewriting cyber warfare—using AI to launch invisible, adaptive, and deeply deceptive attacks. The future of cybersecurity is no longer reactive. Stay informed. #Cybersecurity #QuantumAI #CyberDeception #TheCyberLens thecyberlens.com/p/quantum-enab…
thecyberlens.com
Quantum Enabled Adversaries Fueling the Rise of AI Cyber Deception
Behind the Code: How Quantum Power and Artificial Intelligence Are Changing the Rules of Cyber Warfare—Faster Than You Think
Helps detect lateral movement and early compromise. Example: A fake RDP credential stored in memory. If accessed, an alert is triggered — revealing an attacker’s presence early. #CyberDeception #SOCAnalyst #BlueTeam #IncidentDetection #ThreatDetection #Breadcrumbs #InfoSec
🍯Up the Garden Path: Applying #CyberDeception to the Attack Lifecycle | @SLEUTHCON 2025 youtu.be/vEHg9hRyJ9c #cybersecurity #activedefense

youtube.com
YouTube
Up the Garden Path: Applying Cyber Deception to the Attack Lifecycle...
TODAY AT 11 AM ET! Securing Medical Devices In Healthcare: An Expert’s View webinar by Health-ISAC Navigator, @AcalvioTech. portal.h-isac.org/s/community-ev… #CyberDeception #AIPoweredDeception #ActiveDefense #HoneyToken #MedTech

Named to lure attackers (e.g., “passwords.xlsx”) SOC teams use this as a tripwire for stealthy intrusions. #HoneyFiles #CyberDeception #InsiderThreats #SOCTrap #FileMonitoring #scorpion_drogon
Triggers alerts without risking real data SOC teams use decoys as canaries in the cyber coal mine. #DecoyAccounts #CyberDeception #SOCDetection #LateralMovementTrap #HoneynetStrategy #scorpion_drogon
Securing Medical Devices In Healthcare: An Expert’s View webinar by Health-ISAC Navigator, @AcalvioTech on Wednesday, July 9th at 11 AM ET. portal.h-isac.org/s/community-ev… #CyberDeception #AIPoweredDeception #ActiveDefense #HoneyToken #MedTech

Scales deception across hybrid and cloud environments Increases attacker dwell time and detection rates SOC teams use it to turn the network into an early-warning battlefield. #DeceptionMesh #CyberDeception #AdvancedDefense #ThreatDetection #SOCStrategy #scorpion_drogon
🍯Great slides from Brent Muir (@Mandiant) about how to deploy #CyberDeception strategies on #ICS and #OT environments. lnkd.in/gk_gGi9b #DEFCON33 #cybersecurity

Welcome, Jennifer Lee, to our team as the North America Channel Sales Director. We are excited about the channel sales leadership Jennifer brings to Acalvio and look forward to her contributions to the next stage of our journey. Welcome, Jennifer! #CyberDeception #ChannelLeader

Cyber deception empowers organizations by misleading attackers, wasting their time and prompting errors. Proactive confusion enhances security measures and traps intruders. 🛡️💻 #CyberDeception #USA #InfosecTech link: ift.tt/zeKWwB6

Happy #cyberdeceptionday! Adversaries are gaining in speed and stealth, as highlighted by the recent CrowdStrike Global Threat Report 2024. Read this blog on why deception technology is a necessary countermeasure to detect threats early and stop breaches. #CyberDeception

We wish you a wonderful holiday season! Thanks to our customers, partners, investors, employees and the cybersecurity community for the continued support. #happyholidays #activedefense #cyberdeception #cybersecurity #AIPoweredDeception

Don't miss the webinar tomorrow (July 30) - The Rise Of Insider Threats: Strategies For Cyber Defense. Register now buff.ly/4bxBGgB 👉 Insider threats continue to rise with the increased adoption of cloud services and remote work. #InsiderThreat #CyberDeception

Attending RSA Conference? Meet our founders and cyber deception experts!!! buff.ly/4bbkTAb Our experts are available to demo and discuss use cases of deception technology to protect identities, endpoint and network. #CyberDeception #IdentityProtection

Quote of the Day! #PHISING #cyberdeception #cyberworld #ttb #ttbinternetsecurity #quoteoftheday #dailyquotes #updates #cybersecurity #cybersansar

NCSC collects evidence on #cyberdeception ukauthority.com/articles/ncsc-… @UKAuthority @NCSC #CyberSecurity

#DKY that Commvault is the only #dataprotection vendor with #cyberdeception technology that can detect threats in both production and backup environments. Find out more commvault.com/platform/produ…
If you’ll be at #WEST2025, January 28-30, be sure to stop by our booth in Carahsoft’s partner pavilion to explore our AI-powered Cyber Deception solutions transforming the defense and maritime industry. carah.io/AFCEAWEST_2025 #CyberDeception #AdvancedThreatDefense…

Announcing our partnership with Google to deliver Active Defense to protect customers from advanced threats buff.ly/463Bun4 The join solution will help @googlecloud customers detect and respond to the latest advanced threats with precision and speed. #CyberDeception

Will you be at the RSA Conference 2024 at Moscone Center in San Francisco May 6-9? buff.ly/4bbkTAb Our experts will be available to demo and discuss use cases of deception technology to protect identities, endpoint and network. #CyberDeception #IdentityProtection

Cutting-Edge Deception Strategy: The Role of Deception Technology in the Evolving Threat Landscape - A joint session with our customer Paramount on Cutting-Edge Deception Strategy at Fal.Con 2024 buff.ly/4eaG46S #FalCon2024 #CyberDeception #IdentityProtection…

Securing Medical Devices In Healthcare: An Expert’s View webinar by Health-ISAC Navigator, @AcalvioTech on Wednesday, July 9th at 11 AM ET. portal.h-isac.org/s/community-ev… #CyberDeception #AIPoweredDeception #ActiveDefense #HoneyToken #MedTech

Cyber Deception Market Size, Share & Growth Report, 2034 🔰 𝐃𝐨𝐰𝐧𝐥𝐨𝐚𝐝 𝐩𝐝𝐟 𝐁𝐫𝐨𝐜𝐡𝐮𝐫𝐞: marketresearchfuture.com/reports/cyber-… #CyberDeception #Cyber #Tech4All

Webinar on July 30: The Rise Of Insider Threats: Strategies For Cyber Defense buff.ly/4bxBGgB 👉 Insider threats are rising with the increased adoption of cloud services and remote work making it easier for insiders to gain access to sensitive data. #CyberDeception

Join us at The Honeynet Project Workshop 2024 in Copenhagen, Denmark this week. denmark2024.honeynet.org Our co-founder Raj Gopalakrishna will be delivering a keynote “Navigating the Evolving Threat Landscape: Identity Attacks and the Role of Deception Technology” #CyberDeception

#TBT The Brick Wall of Identity Security: Five Parts for A Rock-Solid Defense by @AcalvioTech. cyberdefensemagazine.com/the-brick-wall… #cyberdeception #ITDR #infosec #cybersecurity #RSAC2025

Had a great time connecting with CISOs and industry experts at the #SINCCISO25 event in Austin. @sahawkx did a great job discussing how threat actors are weaponizing #AI and the significance of Preemptive Defense with #CyberDeception to safeguard against these evolving threats

Something went wrong.
Something went wrong.
United States Trends
- 1. Thanksgiving 2M posts
- 2. Packers 37.5K posts
- 3. Jack White 2,946 posts
- 4. #GBvsDET 2,892 posts
- 5. Thankful 398K posts
- 6. #GoPackGo 5,813 posts
- 7. Wicks 4,137 posts
- 8. Jordan Love 5,450 posts
- 9. Goff 6,013 posts
- 10. Jameson Williams 1,577 posts
- 11. #OnePride 5,474 posts
- 12. Jamo 3,191 posts
- 13. Turkey 262K posts
- 14. Amon Ra 2,271 posts
- 15. Seven Nation Army N/A
- 16. Tom Kennedy N/A
- 17. LaFleur 2,080 posts
- 18. Branch 23.4K posts
- 19. Ray J 2,940 posts
- 20. David Montgomery N/A


























