#dbatloader search results
🚨 New #phishing campaign uses #DBatLoader to drop #Remcos RAT. The infection relies on #UAC bypass with mock directories, obfuscated .cmd scripts, Windows #LOLBAS techniques, and advanced persistence techniques. At the time of analysis, the samples had not yet been submitted to…

Recent variants of #DBatLoader #malware allocate large semi-random regions of memory before dropping the payload, which can be problematic for sandboxes. It calculates the memory allocation size using QueryPerformanceCounter and GetTickCount which act as a seed for a random size.


📄#DBatLoader Old vs New 👉Old Dll uses APIs from Wininet.dll to download encrypted payload from decrypted url. 👉New Dll uses COM object to download encrypted payload from decrypted url.



Dropping a #Yara rule for a new variant of #DBatLoader/#ModiLoader in the wild: github.com/d4rksystem/Yar… #100DaysOfYara

ISC Diary: @malware_traffic saw #GuLoader or #ModiLoader/#DBatLoader style traffic for #RemcosRAT i5c.us/d29990

#dbatloader spread via mail "New Purchase Order" url > .pdf.img > .exe 🔗p://www.islamicbankbd.]org/document/PurchaseOrder52435374.pdf 🔥p://ecmtibbiclhazlar.]com/cyxjElXJ/205_Chilrcjtcqn Now stager and C2 seems disabled and redirect to RickRoll
![Tac_Mangusta's tweet image. #dbatloader spread via mail "New Purchase Order"
url > .pdf.img > .exe
🔗p://www.islamicbankbd.]org/document/PurchaseOrder52435374.pdf
🔥p://ecmtibbiclhazlar.]com/cyxjElXJ/205_Chilrcjtcqn
Now stager and C2 seems disabled and redirect to RickRoll](https://pbs.twimg.com/media/Fx9ybF9XoAIfg4e.png)
![Tac_Mangusta's tweet image. #dbatloader spread via mail "New Purchase Order"
url > .pdf.img > .exe
🔗p://www.islamicbankbd.]org/document/PurchaseOrder52435374.pdf
🔥p://ecmtibbiclhazlar.]com/cyxjElXJ/205_Chilrcjtcqn
Now stager and C2 seems disabled and redirect to RickRoll](https://pbs.twimg.com/media/Fx9zDK2XwAEpjGq.jpg)
And this one uploaded by TeamDreier (Thx) #DBatLoader -> #Remcos RAT bazaar.abuse.ch/sample/115bfc9… 240320920_240320920192580_PDF.cmd:68:-----BEGIN X509 CRL----- 240320920_240320920192580_PDF.cmd:52230:-----END X509 CRL----- joesandbox.com/analysis/14129…


32ba1ee78874a80a23a0d09427d52af6 05ef4ca659965c1d3faa58077b0f9943 #FormBook #ModiLoader #DBatLoader


[4/4] drop url: 176.65.144[.23/ff/kkinng.txt sha256: 954b611a8e8163b42691ec83d4ff0077ef6f80505a434d03e04c9ae19494ea13 bazaar.abuse.ch/browse/tag/176…
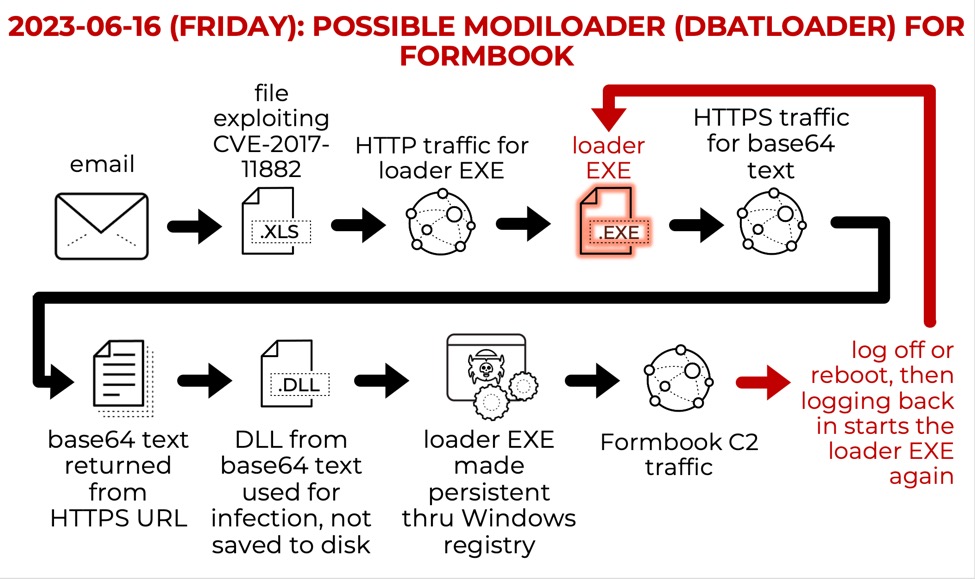
2025-01-10 (Fri): We still find malicious Office docs in the wild exploiting CVE-2017-0199, often using #steganography to avoid detection. One such chain recently led to #DBatLoader/#GuLoader-style malware for #AgentTesla with FTP data exfil. More info at: bit.ly/40ewwT0




#DBatLoader used for many #rat🐀 С2: IP, ports below in comment Final payload from blog.talosintelligence.com/new-banking-tr… (fresh #CarnavalHeist/#AllaSenha) reminds DBatLoader, script here -> github.com/executemalware… (outdated, e.g. no port 6281) tria.ge/231107-vt8bmsc… joesandbox.com/analysis/13473…


And even more recent #DBatLoader samples, all with base64 encoded PE in BAT/CMD file 1) bazaar.abuse.ch/sample/dd1dfdb… 2) bazaar.abuse.ch/sample/3119184… 3) bazaar.abuse.ch/sample/df8a1a2… 4) bazaar.abuse.ch/sample/1874359… 5) bazaar.abuse.ch/sample/b257d62…

Jep, #DBatLoader and #Remcos RAT C2: severdops[.]ddns[.]net Has been used since 2021 😮 for many different RATs and stealers I would guess this could be #DESKTOPgroup 🤔
![c_APT_ure's tweet image. Jep, #DBatLoader and #Remcos RAT
C2: severdops[.]ddns[.]net
Has been used since 2021 😮
for many different RATs and stealers
I would guess this could be #DESKTOPgroup 🤔](https://pbs.twimg.com/media/GRLYW-SWYAE6lGJ.png)
![c_APT_ure's tweet image. Jep, #DBatLoader and #Remcos RAT
C2: severdops[.]ddns[.]net
Has been used since 2021 😮
for many different RATs and stealers
I would guess this could be #DESKTOPgroup 🤔](https://pbs.twimg.com/media/GRLYYSMWMAAe7D4.png)
"PAGAMENTO FATTURA PRO-FORMA 394" spread #DbatLoader #RemcosRat Samples👇 bazaar.abuse.ch/browse/tag/198… AnyRun👇 app.any.run/tasks/7c7fbeb0… ⛔️C2 198.23.227[.]212:32583 BotnetYavakosa
![JAMESWT_WT's tweet image. "PAGAMENTO FATTURA PRO-FORMA 394"
spread #DbatLoader #RemcosRat
Samples👇
bazaar.abuse.ch/browse/tag/198…
AnyRun👇
app.any.run/tasks/7c7fbeb0…
⛔️C2
198.23.227[.]212:32583
BotnetYavakosa](https://pbs.twimg.com/media/GrfRrTOXgAA5O3e.jpg)
![JAMESWT_WT's tweet image. "PAGAMENTO FATTURA PRO-FORMA 394"
spread #DbatLoader #RemcosRat
Samples👇
bazaar.abuse.ch/browse/tag/198…
AnyRun👇
app.any.run/tasks/7c7fbeb0…
⛔️C2
198.23.227[.]212:32583
BotnetYavakosa](https://pbs.twimg.com/media/GrfRsM6XwAAlRJJ.jpg)
![JAMESWT_WT's tweet image. "PAGAMENTO FATTURA PRO-FORMA 394"
spread #DbatLoader #RemcosRat
Samples👇
bazaar.abuse.ch/browse/tag/198…
AnyRun👇
app.any.run/tasks/7c7fbeb0…
⛔️C2
198.23.227[.]212:32583
BotnetYavakosa](https://pbs.twimg.com/media/GrfRvWIXgAAAxRd.jpg)
A @pmmkowalczyk jak nie ze swojego konta, to na naszej stronie. Zerknijcie na analizę nowego #njrat, tym razem z #DBATLoader. cert.orange.pl/aktualnosci/re…

Threat actor turns a Cabinet (CAB) file into the Loader. It dropped #ModiLoader (aka #DBatLoader) and ultimately deployed Agent Tesla. NEOMS_EOI_FORM.cmd (yep this is CAB file) SHA256: a631e4304cf932de1129cc660fd648125226cfee4059321b4e2048c38b2f9357 Rules & IOCs in🧵 #malware

Update in #Malware Trends Tracker: #DBatLoader 🔍 This #loader uses Discord and OneDrive to host malicious payloads and drops different #malware, including #Remcos and #Formbook. Keep up with its latest samples and #IOCs👉 any.run/malware-trends…
In the recent campaign, hackers are sending phishing emails containing malicious files. These files then download and install malware from WordPress websites. Read more ⬇️ #whalebone #zerodaythreatprevention #DBatLoader #securityfirst #whaleboneshorts

#DBatLoader, aka #ModiLoader & #NatsoLoader, is being used in several #phishing campaigns to target manufacturing companies and various businesses in Europe. #CyberSecurity #infosec #cybercrime buff.ly/40QJSUw

DBatLoader, a Delphi-compiled Windows x86 malware, uses heavy obfuscation, import hiding, and anti-analysis to maintain stealthy surveillance, registry edits, screenshot capture, and possible keylogging in enterprise environments. #DBatLoader #DelphiMalw… ift.tt/yFGwHSV
32ba1ee78874a80a23a0d09427d52af6 05ef4ca659965c1d3faa58077b0f9943 #FormBook #ModiLoader #DBatLoader


[4/4] drop url: 176.65.144[.23/ff/kkinng.txt sha256: 954b611a8e8163b42691ec83d4ff0077ef6f80505a434d03e04c9ae19494ea13 bazaar.abuse.ch/browse/tag/176…
🎣 Look out for this new #phishing campaign #DBatLoader deploys #Remcos by abusing .pif (Program Information Files) to evade detection and execute the final payload See analysis of the full attack chain 👇 any.run/cybersecurity-…
🔒⚠️ New DBatLoader campaign observed!👀 Drops Remcos RAT onto unsuspecting users' computers for data theft👾🔓. Stay vigilant and protect your digital fortress!💻🔐 #CyberSecurity #MalwareAlert #DBatLoader #Remcos 🚫🕵️♂️👨💻 any.run/cybersecurity-… #anyrunptk
"PAGAMENTO FATTURA PRO-FORMA 394" spread #DbatLoader #RemcosRat Samples👇 bazaar.abuse.ch/browse/tag/198… AnyRun👇 app.any.run/tasks/7c7fbeb0… ⛔️C2 198.23.227[.]212:32583 BotnetYavakosa
![JAMESWT_WT's tweet image. "PAGAMENTO FATTURA PRO-FORMA 394"
spread #DbatLoader #RemcosRat
Samples👇
bazaar.abuse.ch/browse/tag/198…
AnyRun👇
app.any.run/tasks/7c7fbeb0…
⛔️C2
198.23.227[.]212:32583
BotnetYavakosa](https://pbs.twimg.com/media/GrfRrTOXgAA5O3e.jpg)
![JAMESWT_WT's tweet image. "PAGAMENTO FATTURA PRO-FORMA 394"
spread #DbatLoader #RemcosRat
Samples👇
bazaar.abuse.ch/browse/tag/198…
AnyRun👇
app.any.run/tasks/7c7fbeb0…
⛔️C2
198.23.227[.]212:32583
BotnetYavakosa](https://pbs.twimg.com/media/GrfRsM6XwAAlRJJ.jpg)
![JAMESWT_WT's tweet image. "PAGAMENTO FATTURA PRO-FORMA 394"
spread #DbatLoader #RemcosRat
Samples👇
bazaar.abuse.ch/browse/tag/198…
AnyRun👇
app.any.run/tasks/7c7fbeb0…
⛔️C2
198.23.227[.]212:32583
BotnetYavakosa](https://pbs.twimg.com/media/GrfRvWIXgAAAxRd.jpg)
⚠️ A #phishing campaign targeting Turkish users is distributing #DBatLoader via fake transaction record emails. Stay cautious on executing script extensions from phishing emails and keep security products up to date to prevent attacks. 🔗 Read more: asec.ahnlab.com/en/88025/ #TI

🚨 New #phishing campaign uses #DBatLoader to drop #Remcos RAT. The infection relies on #UAC bypass with mock directories, obfuscated .cmd scripts, Windows #LOLBAS techniques, and advanced persistence techniques. At the time of analysis, the samples had not yet been submitted to…

See our March release notes for ACCE ciphertechsolutions.com/acce-release-n… #Prysmax #AutocRAT #DBatLoader #Onimai
2025-01-10 (Fri): We still find malicious Office docs in the wild exploiting CVE-2017-0199, often using #steganography to avoid detection. One such chain recently led to #DBatLoader/#GuLoader-style malware for #AgentTesla with FTP data exfil. More info at: bit.ly/40ewwT0




Threat actor turns a Cabinet (CAB) file into the Loader. It dropped #ModiLoader (aka #DBatLoader) and ultimately deployed Agent Tesla. NEOMS_EOI_FORM.cmd (yep this is CAB file) SHA256: a631e4304cf932de1129cc660fd648125226cfee4059321b4e2048c38b2f9357 Rules & IOCs in🧵 #malware

"instead, in all nine campaigns, #attackers used #ModiLoader (aka #DBatLoader) as the preferred delivery tool of choice. The final payload to be delivered and launched on the compromised machines varied" welivesecurity.com/en/eset-resear…
Jep, #DBatLoader and #Remcos RAT C2: severdops[.]ddns[.]net Has been used since 2021 😮 for many different RATs and stealers I would guess this could be #DESKTOPgroup 🤔
![c_APT_ure's tweet image. Jep, #DBatLoader and #Remcos RAT
C2: severdops[.]ddns[.]net
Has been used since 2021 😮
for many different RATs and stealers
I would guess this could be #DESKTOPgroup 🤔](https://pbs.twimg.com/media/GRLYW-SWYAE6lGJ.png)
![c_APT_ure's tweet image. Jep, #DBatLoader and #Remcos RAT
C2: severdops[.]ddns[.]net
Has been used since 2021 😮
for many different RATs and stealers
I would guess this could be #DESKTOPgroup 🤔](https://pbs.twimg.com/media/GRLYYSMWMAAe7D4.png)
#DBatLoader malware has resurfaced with enhanced evasion techniques, utilizing a sophisticated distribution mechanism that leverages command files (CMD) to bypass security measures securityonline.info/dbatloader-a-m…
securityonline.info
DBatLoader: A Malware Distribution via CMD Files
DBatLoader is being actively distributed via phishing emails, with the malware now packaged in compressed CMD files
#DBatLoader used for many #rat🐀 С2: IP, ports below in comment Final payload from blog.talosintelligence.com/new-banking-tr… (fresh #CarnavalHeist/#AllaSenha) reminds DBatLoader, script here -> github.com/executemalware… (outdated, e.g. no port 6281) tria.ge/231107-vt8bmsc… joesandbox.com/analysis/13473…


#opendir #DBatLoader #XWorm #RemcosRAT 144.126.134.25:5000 144.126.134.25:8080 #AS40021 @ContaboCom climb-items-macedonia-hometown.trycloudflare[.]com climb-items-macedonia-hometown.trycloudflare[.]com:8080 Full list: paste.ee/r/wD2MX/0
![NDA0E's tweet image. #opendir #DBatLoader #XWorm #RemcosRAT
144.126.134.25:5000
144.126.134.25:8080 #AS40021 @ContaboCom
climb-items-macedonia-hometown.trycloudflare[.]com
climb-items-macedonia-hometown.trycloudflare[.]com:8080
Full list: paste.ee/r/wD2MX/0](https://pbs.twimg.com/media/GNsi5dzWAAAT8wH.png)
![NDA0E's tweet image. #opendir #DBatLoader #XWorm #RemcosRAT
144.126.134.25:5000
144.126.134.25:8080 #AS40021 @ContaboCom
climb-items-macedonia-hometown.trycloudflare[.]com
climb-items-macedonia-hometown.trycloudflare[.]com:8080
Full list: paste.ee/r/wD2MX/0](https://pbs.twimg.com/media/GNsi6G4X0AAuMRx.png)
![NDA0E's tweet image. #opendir #DBatLoader #XWorm #RemcosRAT
144.126.134.25:5000
144.126.134.25:8080 #AS40021 @ContaboCom
climb-items-macedonia-hometown.trycloudflare[.]com
climb-items-macedonia-hometown.trycloudflare[.]com:8080
Full list: paste.ee/r/wD2MX/0](https://pbs.twimg.com/media/GNsi6q6W4AA5w20.png)
![NDA0E's tweet image. #opendir #DBatLoader #XWorm #RemcosRAT
144.126.134.25:5000
144.126.134.25:8080 #AS40021 @ContaboCom
climb-items-macedonia-hometown.trycloudflare[.]com
climb-items-macedonia-hometown.trycloudflare[.]com:8080
Full list: paste.ee/r/wD2MX/0](https://pbs.twimg.com/media/GNsi7QlXQAAuesu.png)
🚨#Opendir #Malware http://103.198.26[.173/360/HJC.exe #dbatloader HJC.exe➡️MD5:2cc30d206669699e58870623365fef82 Dropped file ⬇️ 🔥#Remcos #Malware 🛜@anyrun_app Sandbox analysis: app.any.run/tasks/d9438bb9…
app.any.run
Analysis 42ac8e7e9df9877af1382f5626fd74e63210d307f6d577cd5b387ffd0c9520bd.exe (MD5: 2CC30D2066696...
Interactive malware hunting service. Live testing of most type of threats in any environments. No installation and no waiting necessary.
dropped by #DBatLoader 📦 sample shared on @abuse_ch bazaar.abuse.ch/sample/7cbe8b9…
✍️🇻🇳My quick note about techniques employed by the threat actor in the phishing email to distribute #WarZoneRAT via #DBatLoader. kienmanowar.wordpress.com/2024/04/09/qui…
kienmanowar.wordpress.com
[QuickNote] Phishing email distributes WarZone RAT via DBatLoader
I. Execution Flow Summary: Below is an illustrated and summarized way of how WarZone RAT sample infects the victim system via DBatLoader:
And even more recent #DBatLoader samples, all with base64 encoded PE in BAT/CMD file 1) bazaar.abuse.ch/sample/dd1dfdb… 2) bazaar.abuse.ch/sample/3119184… 3) bazaar.abuse.ch/sample/df8a1a2… 4) bazaar.abuse.ch/sample/1874359… 5) bazaar.abuse.ch/sample/b257d62…

A couple more related samples added here 🧵 2⃣ #DBatLoader -> #Remcos RAT
More similar samples (containing those "X509 CRL" tags) encoded payload here? (in between) TT copy_00285.bat:89:-----BEGIN X509 CRL----- TT copy_00285.bat:48752:-----END X509 CRL----- 1/n bazaar.abuse.ch/sample/4076e46…
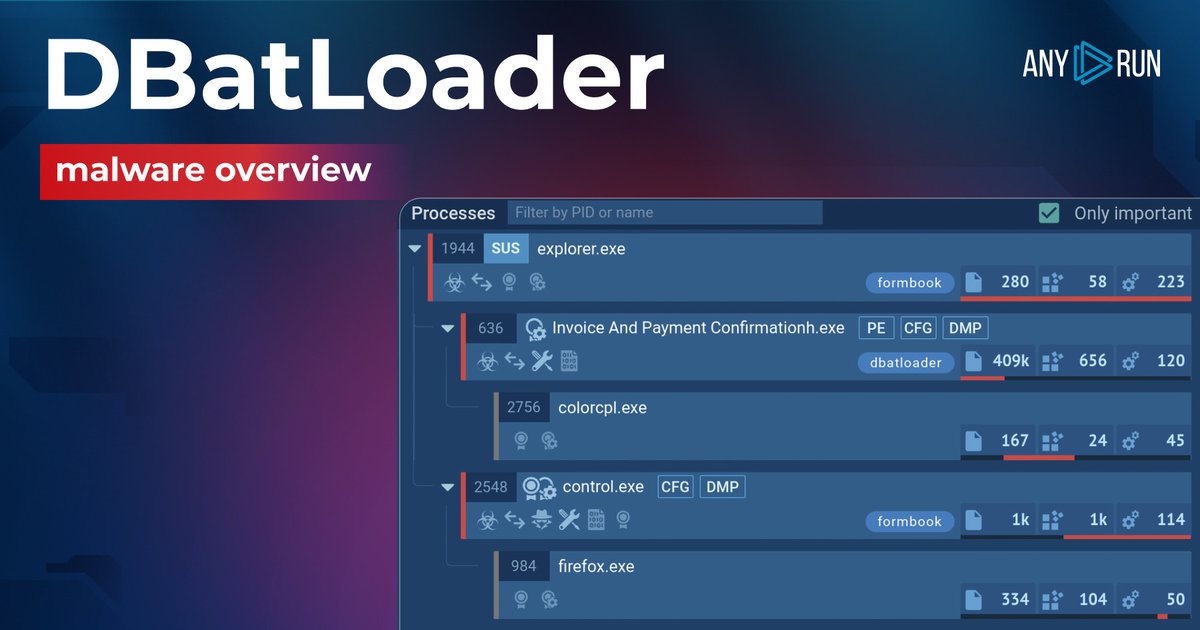
#Redline malware flow Malspam -> zip -> .img -> .lnk -> powershell -> mshta -> powershell -> download exe -> encrypted onedrive file download -> decrypt on fly ( #Dbatloader ) -> theft I am seeing that whenever encrypted onedrive file is downloaded, user agent is "lVali" (1/2)


ISC Diary: @malware_traffic saw #GuLoader or #ModiLoader/#DBatLoader style traffic for #RemcosRAT i5c.us/d29990

🚨 New #phishing campaign uses #DBatLoader to drop #Remcos RAT. The infection relies on #UAC bypass with mock directories, obfuscated .cmd scripts, Windows #LOLBAS techniques, and advanced persistence techniques. At the time of analysis, the samples had not yet been submitted to…

Dropping a #Yara rule for a new variant of #DBatLoader/#ModiLoader in the wild: github.com/d4rksystem/Yar… #100DaysOfYara

Recent variants of #DBatLoader #malware allocate large semi-random regions of memory before dropping the payload, which can be problematic for sandboxes. It calculates the memory allocation size using QueryPerformanceCounter and GetTickCount which act as a seed for a random size.


"Re: CR-FEDEX_TN-270036844357_DT-_CD-20220301_CT-0833" r00 archive -> exe -> #AvemariaRAT / #warzoneRAT uses #DBatLoader sender is impersonates to @FedEx VT Confidence: 13/69 Full IOC here: github.com/0xToxin/Malwar…

👁🗨👄👁🗨 We are live! Join us! Today, #dbatloader (#delphi) let’s reverse engineer in bat country!! #OALABS 🦇 twitch.tv/oalabslive

#Modiloader / #Dbatloader The .z archive leads to exe, which uses lVali UserAgent to download encrypted file from Onedrive ( so MS doesn't take it down ). Post decryption its injected in legit MS process like sndvol to do the C2 comms on 42020 port. bazaar.abuse.ch/sample/4473b5d…

Was bored so collected some additional #IoC. This time for #SystemBC from 2020-2023. Fewer than #DBatLoader collected last Wednesday, however due to its #ransomware ties probably way more important. Here you go: raw.githubusercontent.com/Gi7w0rm/Malwar…


#DBatLoader used for many #rat🐀 С2: IP, ports below in comment Final payload from blog.talosintelligence.com/new-banking-tr… (fresh #CarnavalHeist/#AllaSenha) reminds DBatLoader, script here -> github.com/executemalware… (outdated, e.g. no port 6281) tria.ge/231107-vt8bmsc… joesandbox.com/analysis/13473…


🫣 we are live! Join us as we build a simple #botnet tracker for #dbatloader #OALABS twitch.tv/oalabslive

This week's main focus was on collecting indicators for #DBatLoader. Using some self-made scripts I collected 1621 URLs used between 2020-2023 to download the final payload stage. 23 of those were still online at the time of scanning. All indicators were shared via known channels


2025-01-10 (Fri): We still find malicious Office docs in the wild exploiting CVE-2017-0199, often using #steganography to avoid detection. One such chain recently led to #DBatLoader/#GuLoader-style malware for #AgentTesla with FTP data exfil. More info at: bit.ly/40ewwT0




New #AveMaria stealer / #WarzoneRAT via #DBatLoader URL: urlhaus.abuse.ch/url/1845038/ #UACMe Samples on Bazaar: LZH: bazaar.abuse.ch/sample/86fdfd4… EXE: bazaar.abuse.ch/sample/6072185… C2: pentester01[.]duckdns[.]org:60977 (69.16.216[.]42) #malware
![c_APT_ure's tweet image. New #AveMaria stealer / #WarzoneRAT via
#DBatLoader
URL: urlhaus.abuse.ch/url/1845038/
#UACMe
Samples on Bazaar:
LZH: bazaar.abuse.ch/sample/86fdfd4…
EXE: bazaar.abuse.ch/sample/6072185…
C2: pentester01[.]duckdns[.]org:60977 (69.16.216[.]42)
#malware](https://pbs.twimg.com/media/FFnOPBCXwAwoPdq.png)
📄#DBatLoader Old vs New 👉Old Dll uses APIs from Wininet.dll to download encrypted payload from decrypted url. 👉New Dll uses COM object to download encrypted payload from decrypted url.



#DBatLoader #RemcosRAT Envision Digital.exe e52cf82f435602239c33092829fcf8f1 DBat /mkdvesti.com/F437E4455F6689E610resi25412545d3437E44F6689E61025874515/Wiupbuvvpxknaamhtjrsejoreaxeszq Remcos d94721da651457b288e89a4d0da22453 C2 micenaxus,com:2404


#dbatloader spread via mail "New Purchase Order" url > .pdf.img > .exe 🔗p://www.islamicbankbd.]org/document/PurchaseOrder52435374.pdf 🔥p://ecmtibbiclhazlar.]com/cyxjElXJ/205_Chilrcjtcqn Now stager and C2 seems disabled and redirect to RickRoll
![Tac_Mangusta's tweet image. #dbatloader spread via mail "New Purchase Order"
url > .pdf.img > .exe
🔗p://www.islamicbankbd.]org/document/PurchaseOrder52435374.pdf
🔥p://ecmtibbiclhazlar.]com/cyxjElXJ/205_Chilrcjtcqn
Now stager and C2 seems disabled and redirect to RickRoll](https://pbs.twimg.com/media/Fx9ybF9XoAIfg4e.png)
![Tac_Mangusta's tweet image. #dbatloader spread via mail "New Purchase Order"
url > .pdf.img > .exe
🔗p://www.islamicbankbd.]org/document/PurchaseOrder52435374.pdf
🔥p://ecmtibbiclhazlar.]com/cyxjElXJ/205_Chilrcjtcqn
Now stager and C2 seems disabled and redirect to RickRoll](https://pbs.twimg.com/media/Fx9zDK2XwAEpjGq.jpg)
"RE: [EXTERNAL] RE: RE: Plaćanje stanja" zip -> exe -> #DbatLoader -> #Remcos targets croatian audience. VT confidence: 20/71 Full IOC here: github.com/0xToxin/Malwar…
![0xToxin's tweet image. "RE: [EXTERNAL] RE: RE: Plaćanje stanja"
zip -> exe -> #DbatLoader -> #Remcos
targets croatian audience.
VT confidence: 20/71
Full IOC here: github.com/0xToxin/Malwar…](https://pbs.twimg.com/media/FZIspU1WIAAmar_.png)
Something went wrong.
Something went wrong.
United States Trends
- 1. Bama 14.7K posts
- 2. Oklahoma 23.1K posts
- 3. Ty Simpson 3,404 posts
- 4. #UFC322 27.8K posts
- 5. Iowa 18K posts
- 6. South Carolina 32.7K posts
- 7. Mateer 2,921 posts
- 8. #EubankBenn2 29.4K posts
- 9. #RollTide 2,884 posts
- 10. Brent Venables N/A
- 11. Ryan Williams 1,657 posts
- 12. Arbuckle 1,001 posts
- 13. Georgia Tech 2,501 posts
- 14. Heisman 10K posts
- 15. Talty 1,375 posts
- 16. Susurkaev 2,549 posts
- 17. #USMNT 1,176 posts
- 18. Texas A&M 32.4K posts
- 19. DeBoer 1,045 posts
- 20. Beamer 9,367 posts