#linuxprivesc zoekresultaten
📢 Check out my latest YouTube video on Linux Privilege Escalation! 🐧💻 Learn essential techniques to elevate your access and master the art of #LinuxPrivEsc. youtu.be/mwmUeb46lxI How wicked are you EFCC spotybet Teni Big Benz Asake Kwara Portable #UCLfinal Sahara El Rufai
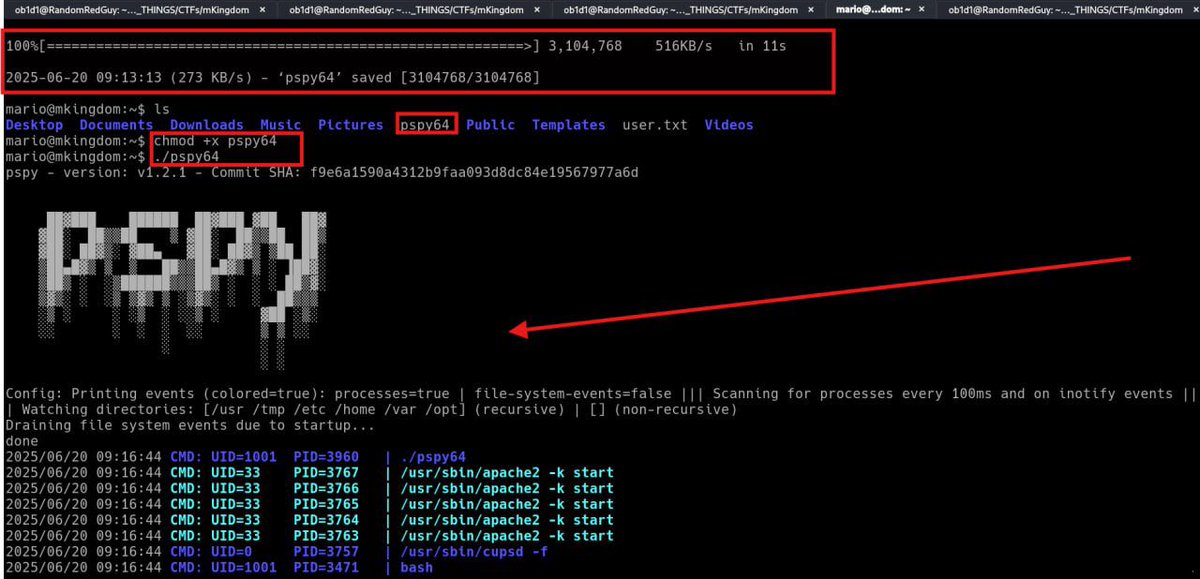
💀 Crushed a CTF room using pspy64 from my Linux privesc tool . Got a shell, watched the system like a hawk, caught a cron, and escalated to root 👑 Flags snatched. Root dance unlocked. #CTF #LinuxPrivEsc #pspy #Rooted #HackThePlanet #PostExploitation #HackerLife #RedTeamMoves
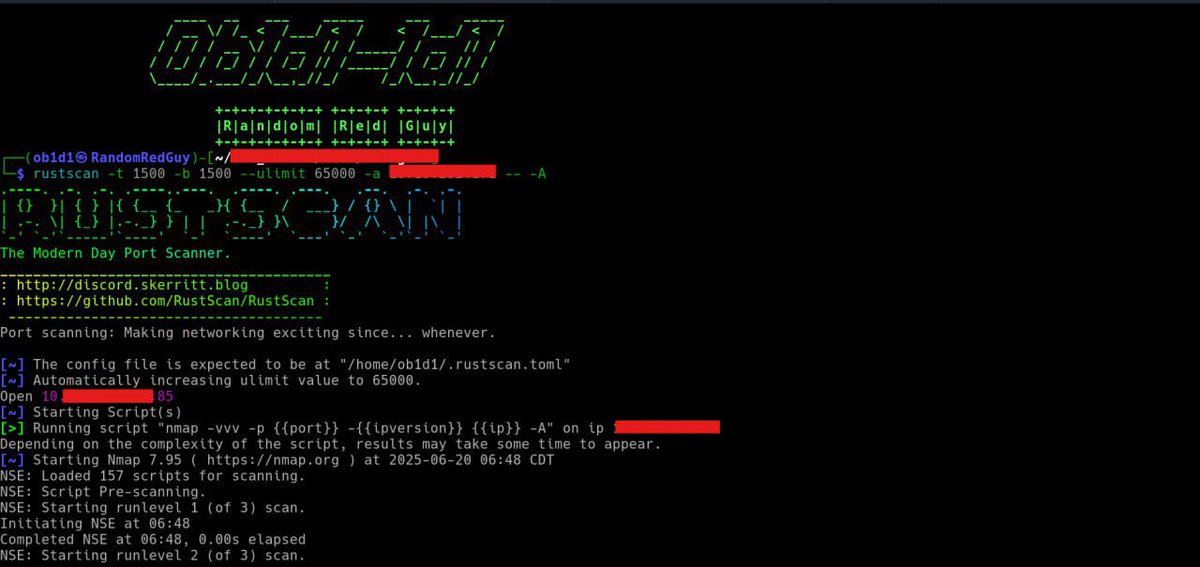
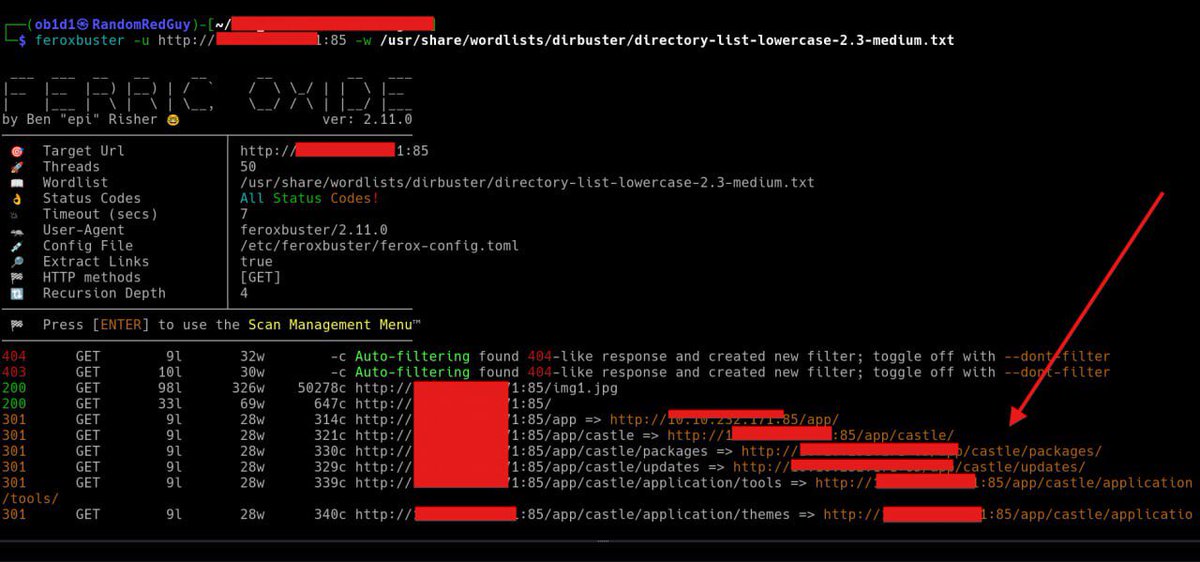
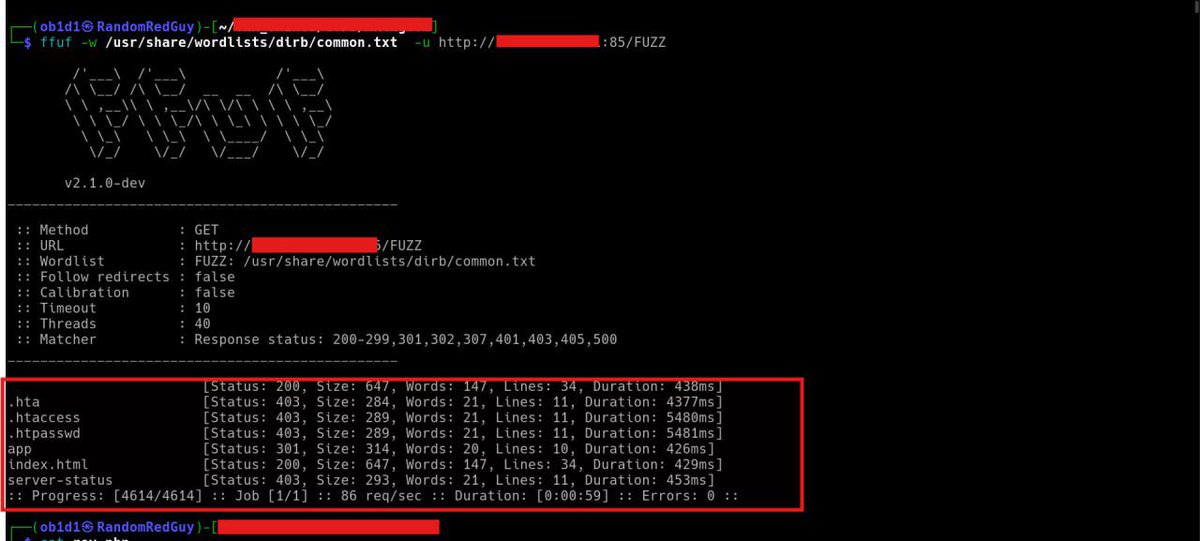
#EthicalHacking #LinuxPrivEsc Proseguiamo e concludiamo la sezione Linux PrivEsc di TryHackMe 👉 youtu.be/LCCG9Yg2mJE

Hack The Box: Shocker #hackthebox #oscp #linuxprivesc #shellshock #sudomisconfiguration #shocker #easy link.medium.com/7lOayIxwm5
After a uncertain break, continuing where i left and this time i will follow the consistency.., #Day1 #7dayaofhacking @RealTryHackMe ⏳ Started with room Linux privilege escalation tryhackme.com/room/linuxpriv… #linuxprivesc #Pentesting #infosec
Hack The Box — Cronos Çözümü #hackthebox #linuxprivesc #oscp #cronos #sqli #rce #crontab #medium link.medium.com/XLtnNsU894
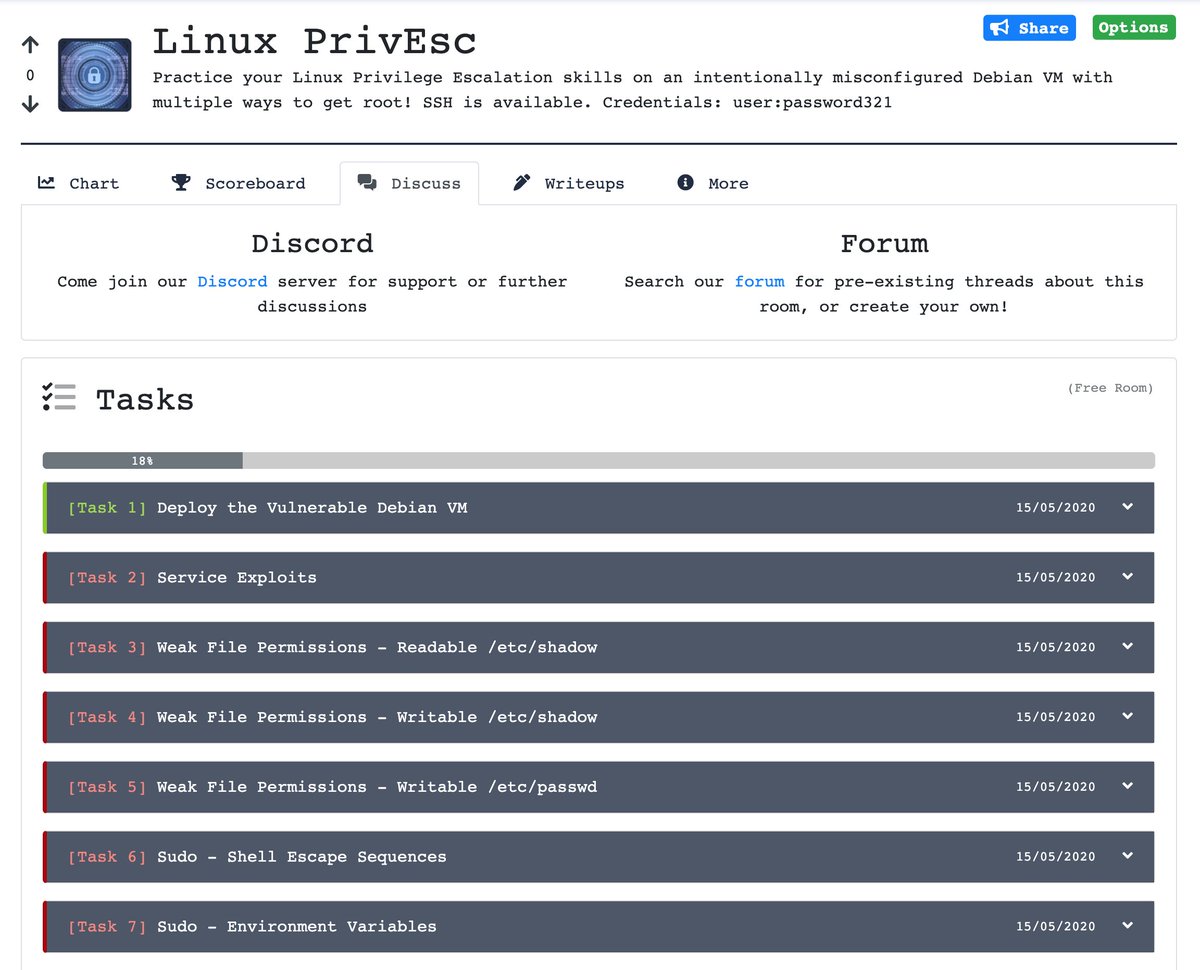
Capstone Challenge on TryHackMe dlvr.it/SZD09w #linuxprivesc #cybersecurity #tryhackme
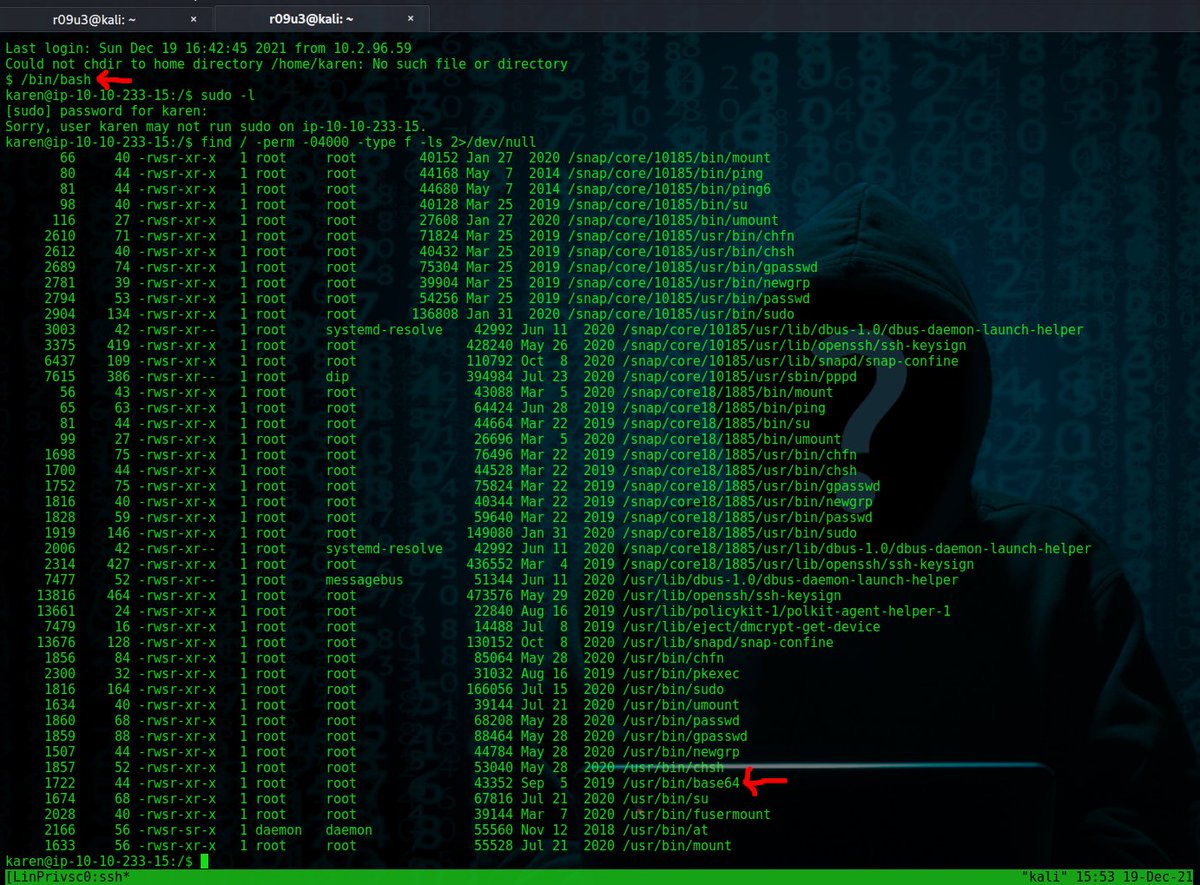
Linux PrivEsc - SUID Path Variable (Relative Path Escalation) dlvr.it/SZbklY #cybersecurity #linuxprivesc #suid
“HA Joker” WriteUp (TryHackMe) dlvr.it/SZZtSX #webpentesting #tryhackme #linuxprivesc
Nothing beats hands-on privilege escalation practice! LazyAdmin on @RealTryHackMe taught me how exposed backups and sloppy scripts can lead to full system compromise. Seeing lazy admin habits turn into real attack paths was a wake-up call. #LinuxPrivEsc #SysAdmin #PenTesting
💀 Crushed a CTF room using pspy64 from my Linux privesc tool . Got a shell, watched the system like a hawk, caught a cron, and escalated to root 👑 Flags snatched. Root dance unlocked. #CTF #LinuxPrivEsc #pspy #Rooted #HackThePlanet #PostExploitation #HackerLife #RedTeamMoves




For LinuxPrivEsc lab, it seems like the simplecopy binary has vulnerability which allows command injection, hence below command changed by user to root without password/authentication /usr/bin/simplecopy filename "; su root" #holidayhack #sans #linuxprivesc
💀 Crushed a CTF room using pspy64 from my Linux privesc tool . Got a shell, watched the system like a hawk, caught a cron, and escalated to root 👑 Flags snatched. Root dance unlocked. #CTF #LinuxPrivEsc #pspy #Rooted #HackThePlanet #PostExploitation #HackerLife #RedTeamMoves




I just published Anonymous: TryHackMe Box Writeup link.medium.com/zrHcs1BKf9 @RealTryHackMe #tryhackme #anonymouswriteup #linuxprivesc tryhackme.com/room/anonymous

#EthicalHacking #LinuxPrivEsc Proseguiamo e concludiamo la sezione Linux PrivEsc di TryHackMe 👉 youtu.be/LCCG9Yg2mJE

Nothing beats hands-on privilege escalation practice! LazyAdmin on @RealTryHackMe taught me how exposed backups and sloppy scripts can lead to full system compromise. Seeing lazy admin habits turn into real attack paths was a wake-up call. #LinuxPrivEsc #SysAdmin #PenTesting

After a uncertain break, continuing where i left and this time i will follow the consistency.., #Day1 #7dayaofhacking @RealTryHackMe ⏳ Started with room Linux privilege escalation tryhackme.com/room/linuxpriv… #linuxprivesc #Pentesting #infosec

Something went wrong.
Something went wrong.
United States Trends
- 1. Cloudflare 23.4K posts
- 2. #heatedrivalry 27.8K posts
- 3. Cowboys 74K posts
- 4. LeBron 111K posts
- 5. Gibbs 20.6K posts
- 6. fnaf 2 27.2K posts
- 7. Pickens 14.8K posts
- 8. scott hunter 5,950 posts
- 9. Lions 92.7K posts
- 10. Warner Bros 24.9K posts
- 11. Paramount 21.1K posts
- 12. #PowerForce N/A
- 13. Happy Farmers 1,192 posts
- 14. Shang Tsung 32.9K posts
- 15. rUSD N/A
- 16. #OnePride 10.7K posts
- 17. Brandon Aubrey 7,477 posts
- 18. Cary 43.3K posts
- 19. Ferguson 11.1K posts
- 20. Scott and Kip 3,385 posts