#vulnerabilityexploits 搜尋結果
#VulnerabilityExploits, Not Phishing, Are the Top Cyberattack Vector for Initial Compromise Jai Vijayan lnkd.in/eQMVi_d6
@Verizon DBIR reveals 180% #vulnerabilityexploits increase as initial vector. There's an urgent need for hyperautomated solutions that can address #softwarevulnerabilities. #Hyperautomation in #ITsecurity isn't just a choice; it's becoming a necessity. bit.ly/49X3slT
infosecurity-magazine.com
Vulnerability Exploits Triple as Initial Access Point for Breaches
The growth of software supply chain attacks pushed vulnerability exploits to the third most used initial access method, Verizon found
#NEWSABOUTCYBER #SHAREANDFOLLOWUS The PurpleFox botnet has refreshed its arsenal with new #vulnerabilityexploits and dropped payloads, now also leveraging WebSockets for C2 bidirectional communication. bleepingcomputer.com/news/security/…
@Verizon DBIR reveals 180% #vulnerabilityexploits increase as initial vector. There's an urgent need for hyperautomated solutions that can address #softwarevulnerabilities. #Hyperautomation in #ITsecurity isn't just a choice; it's becoming a necessity. bit.ly/49X3slT
infosecurity-magazine.com
Vulnerability Exploits Triple as Initial Access Point for Breaches
The growth of software supply chain attacks pushed vulnerability exploits to the third most used initial access method, Verizon found
#VulnerabilityExploits, Not Phishing, Are the Top Cyberattack Vector for Initial Compromise Jai Vijayan lnkd.in/eQMVi_d6
Do you want to find more vulnerabilities with recon? 🤑 Open this thread (step-by-step guide)! 🧵 👇

🚨 #phishing report issued 🚨 🌐 Suspected URL: https://arora-labs[.]com/ 🔎 Analysis: urlscan.io/result/0199fb5… 🔒 #InfoSec 🛡️ @Phish_Destroy
![CarlyGriggs13's tweet image. 🚨 #phishing report issued 🚨
🌐 Suspected URL: https://arora-labs[.]com/
🔎 Analysis: urlscan.io/result/0199fb5…
🔒 #InfoSec
🛡️ @Phish_Destroy](https://pbs.twimg.com/media/G3m7KtfWgAAmqby.png)
🚨 #phishing report issued 🚨 🌐 Suspected URL: https://jakt[.]top/ 🔎 Analysis: urlscan.io/result/0199fb5… 🔒 #Crypto 🛡️ @Phish_Destroy
![CarlyGriggs13's tweet image. 🚨 #phishing report issued 🚨
🌐 Suspected URL: https://jakt[.]top/
🔎 Analysis: urlscan.io/result/0199fb5…
🔒 #Crypto
🛡️ @Phish_Destroy](https://pbs.twimg.com/media/G3m5Os_XAAAOzCN.png)
Today I used a technique that’s probably not widely known in the community. In what cases could code like this lead to a vulnerability? ->

Hackers 🔥 This code contains at least 2 serious vulnerabilities. Can you spot them? 😋 What would be your exploit? 🤔
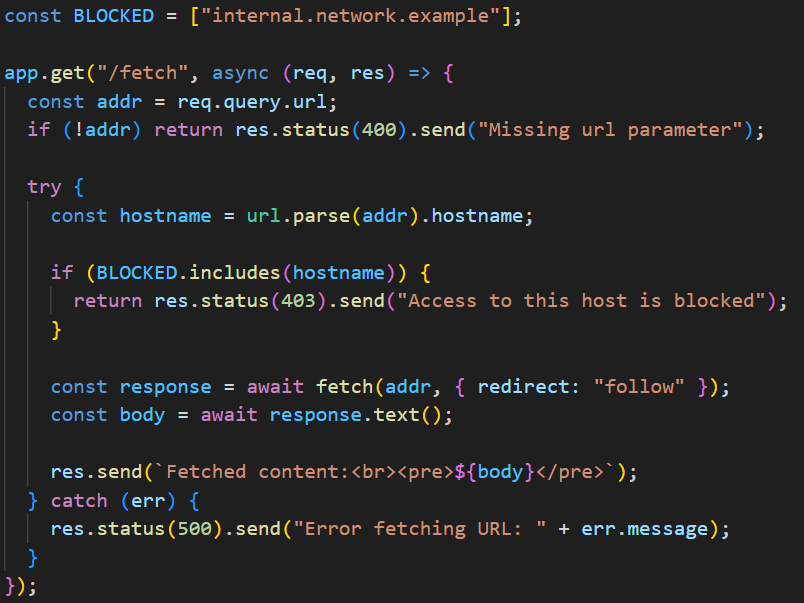
Path Traversal Vulnerability POC: https://redacted/lib///....//....//....//....//....//....//....//....//etc//passwd #bugbountytips #lfi #bugbountywriteups #bugbounty #infosec

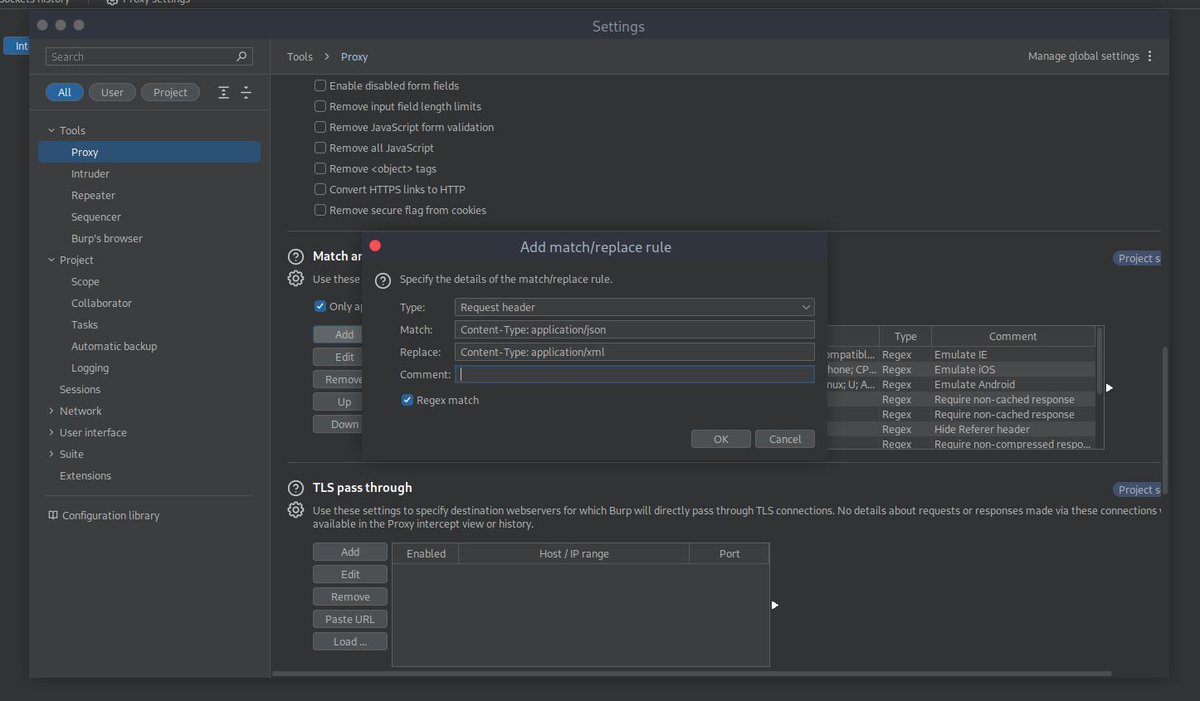
Want to find more vulnerabilities using BurpSuite match & replace rules? 🤑 Open this thread! 🧵 👇
🚨 #phishing report issued 🚨 🌐 Suspected URL: https://betcas[.]us/ 🔎 Analysis: urlscan.io/result/0199fb4… 🔒 #Crypto 🛡️ @Phish_Destroy
![CarlyGriggs13's tweet image. 🚨 #phishing report issued 🚨
🌐 Suspected URL: https://betcas[.]us/
🔎 Analysis: urlscan.io/result/0199fb4…
🔒 #Crypto
🛡️ @Phish_Destroy](https://pbs.twimg.com/media/G3m3VhkXsAAxs5e.png)
🚨 #phishing report issued 🚨 🌐 Suspected URL: https://cyberinvestigations[.]online/ 🔎 Analysis: urlscan.io/result/0199fb5… 🔒 #scam 🛡️ @Phish_Destroy
![CarlyGriggs13's tweet image. 🚨 #phishing report issued 🚨
🌐 Suspected URL: https://cyberinvestigations[.]online/
🔎 Analysis: urlscan.io/result/0199fb5…
🔒 #scam
🛡️ @Phish_Destroy](https://pbs.twimg.com/media/G3m7RFRWcAADbFE.png)
🚨 #phishing report issued 🚨 🌐 Suspected URL: https://voltbet[.]top/ 🔎 Analysis: urlscan.io/result/0199fb5… 🔒 #InfoSec 🛡️ @Phish_Destroy
![CarlyGriggs13's tweet image. 🚨 #phishing report issued 🚨
🌐 Suspected URL: https://voltbet[.]top/
🔎 Analysis: urlscan.io/result/0199fb5…
🔒 #InfoSec
🛡️ @Phish_Destroy](https://pbs.twimg.com/media/G3m62MnXMAAMR5P.png)
A popular NPM package got compromised, attackers updated it to run a post-install script that steals secrets But the script is a *prompt* run by the user's installation of Claude Code. This avoids it being detected by tools that analyze code for malware You just got vibepwned

🚨 #phishing report issued 🚨 🌐 Suspected URL: https://luckyranch[.]us/ 🔎 Analysis: urlscan.io/result/0199fb5… 🔒 #OnlineSafety 🛡️ @Phish_Destroy
![CarlyGriggs13's tweet image. 🚨 #phishing report issued 🚨
🌐 Suspected URL: https://luckyranch[.]us/
🔎 Analysis: urlscan.io/result/0199fb5…
🔒 #OnlineSafety
🛡️ @Phish_Destroy](https://pbs.twimg.com/media/G3m58WsXEAAsmZb.png)
🚨 #phishing report issued 🚨 🌐 Suspected URL: https://gotbet[.]cc/ 🔎 Analysis: urlscan.io/result/0199fb4… 🔒 #phishdestroy 🛡️ @Phish_Destroy
![CarlyGriggs13's tweet image. 🚨 #phishing report issued 🚨
🌐 Suspected URL: https://gotbet[.]cc/
🔎 Analysis: urlscan.io/result/0199fb4…
🔒 #phishdestroy
🛡️ @Phish_Destroy](https://pbs.twimg.com/media/G3m3E0aXUAA1zER.png)
⚡ New Android exploit “Pixnapping” steals 2FA codes via GPU side-channels. — No special permissions — Works across apps (Maps, Authenticator, etc.) — Full 2FA capture in ~30s

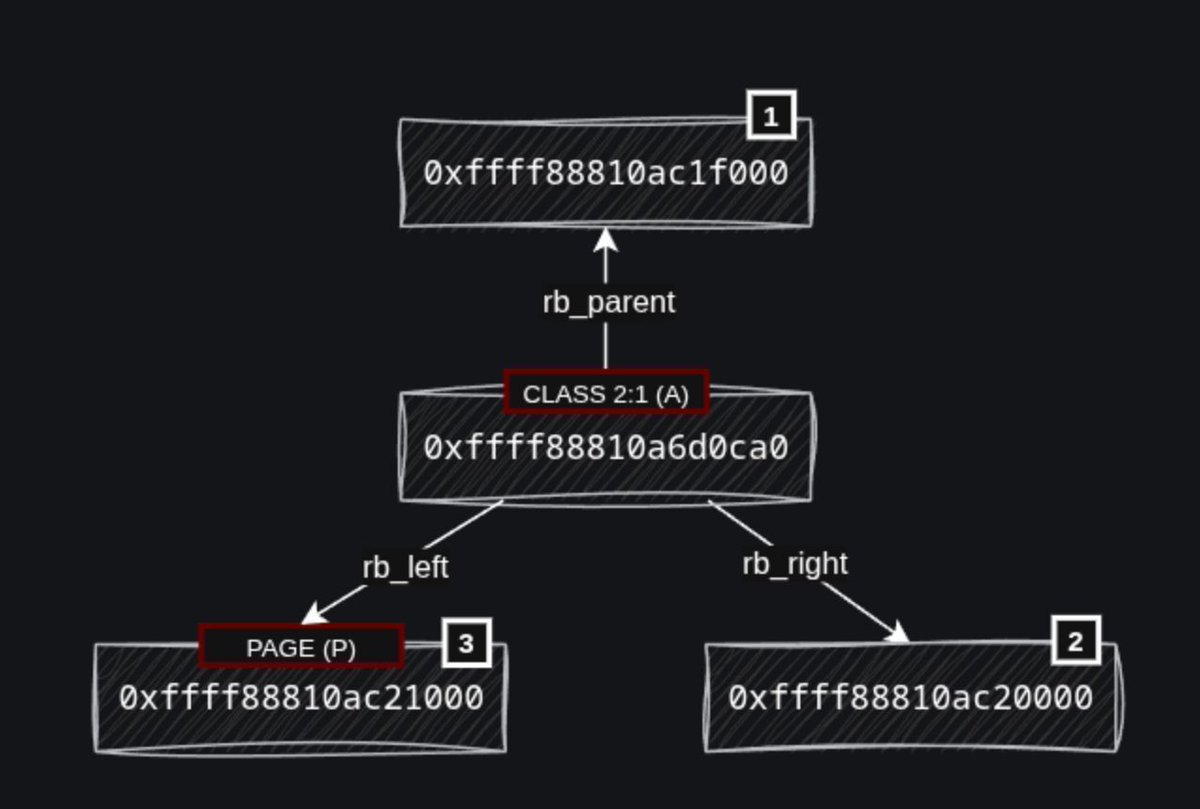
Exploiting a Use-After-Free vulnerability in the Linux network packet schedule (CVE-2025-38001) syst3mfailure.io/rbtree-family-… Credits @cor_ctf #infosec #Linux
Something went wrong.
Something went wrong.
United States Trends
- 1. Stanford 11K posts
- 2. Mike Norvell 1,674 posts
- 3. Florida State 10.2K posts
- 4. #AEWWrestleDream 69.1K posts
- 5. Sabrina 66.6K posts
- 6. SPENCER SMITH N/A
- 7. #byucpl N/A
- 8. Darby 11.5K posts
- 9. Utah 33K posts
- 10. Mizzou 6,285 posts
- 11. Hugh Freeze 3,051 posts
- 12. brendon 5,778 posts
- 13. Lincoln Riley 2,919 posts
- 14. Bama 16.6K posts
- 15. Sperry N/A
- 16. Castellanos 3,771 posts
- 17. Sting 15K posts
- 18. Nobody's Son 3,548 posts
- 19. Pico Prism 4,057 posts
- 20. lorde 5,735 posts



















