#vulnerabilityexploits результаты поиска
#VulnerabilityExploits, Not Phishing, Are the Top Cyberattack Vector for Initial Compromise Jai Vijayan lnkd.in/eQMVi_d6
@Verizon DBIR reveals 180% #vulnerabilityexploits increase as initial vector. There's an urgent need for hyperautomated solutions that can address #softwarevulnerabilities. #Hyperautomation in #ITsecurity isn't just a choice; it's becoming a necessity. bit.ly/49X3slT
infosecurity-magazine.com
Vulnerability Exploits Triple as Initial Access Point for Breaches
The growth of software supply chain attacks pushed vulnerability exploits to the third most used initial access method, Verizon found
#NEWSABOUTCYBER #SHAREANDFOLLOWUS The PurpleFox botnet has refreshed its arsenal with new #vulnerabilityexploits and dropped payloads, now also leveraging WebSockets for C2 bidirectional communication. bleepingcomputer.com/news/security/…
@Verizon DBIR reveals 180% #vulnerabilityexploits increase as initial vector. There's an urgent need for hyperautomated solutions that can address #softwarevulnerabilities. #Hyperautomation in #ITsecurity isn't just a choice; it's becoming a necessity. bit.ly/49X3slT
infosecurity-magazine.com
Vulnerability Exploits Triple as Initial Access Point for Breaches
The growth of software supply chain attacks pushed vulnerability exploits to the third most used initial access method, Verizon found
#VulnerabilityExploits, Not Phishing, Are the Top Cyberattack Vector for Initial Compromise Jai Vijayan lnkd.in/eQMVi_d6
Container Security 🐳 Scan container images for vulnerabilities during builds. 🐳 Use secure base images from trusted registries. 🐳 Avoid running containers with root privileges. 🐳 Monitor runtime containers for drift. 🐳 Apply least privilege access. Container Security! 🔐…

Today I used a technique that’s probably not widely known in the community. In what cases could code like this lead to a vulnerability? ->

Do you want to find more vulnerabilities with recon? 🤑 Open this thread (step-by-step guide)! 🧵 👇

Hackers 🔥 This code contains at least 2 serious vulnerabilities. Can you spot them? 😋 What would be your exploit? 🤔
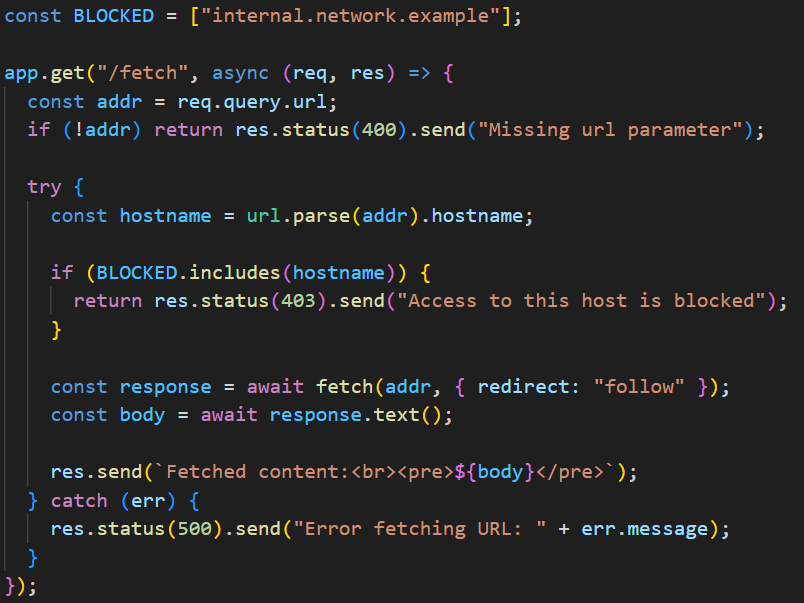
Vulnerability checklist: 📓⚔️ This repository contains a lot of web and API vulnerability checklist, a lot of vulnerability ideas, and tips from twitter - github.com/Az0x7/vulnerab… #infosec #cybersec #bugbountytips
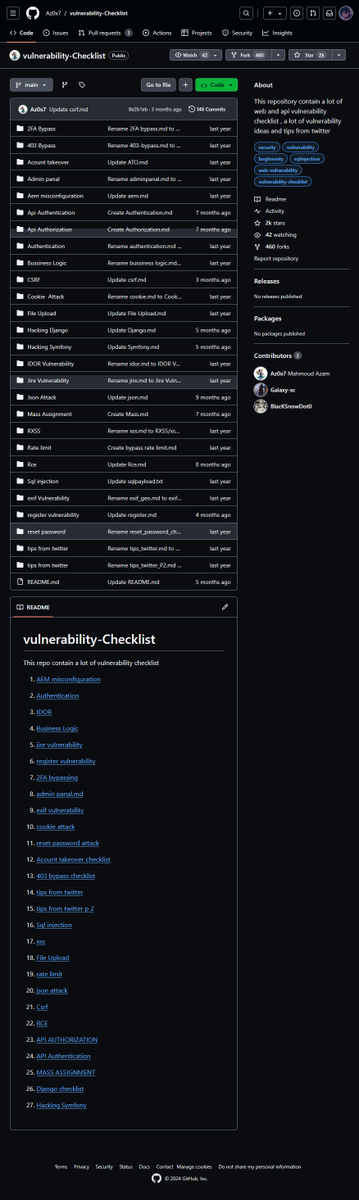
Want to find more vulnerabilities using BurpSuite match & replace rules? 🤑 Open this thread! 🧵 👇
These two accounts are sending suspicious links in DMs: @Nah804 @lady_freyaCC Lots of accounts have been hacked recently after people clicked on the links. NEVER CLICK ON ANY LINKS SENT VIA DMS.
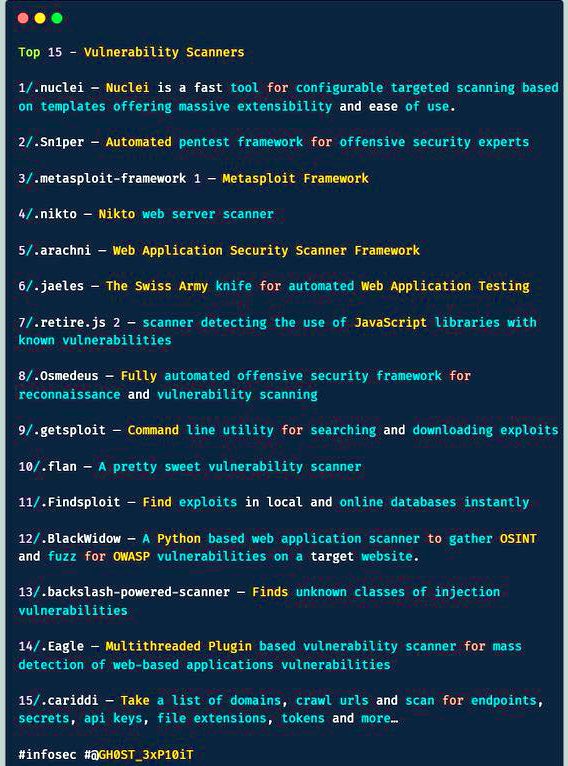
Top 10 Exploited Vulnerabilities #infosec #cybersecurity #pentesting #redteam #informationsecurity #CyberSec #networking #networksecurity #infosecurity #cyberattacks #security #linux #cybersecurityawareness #bugbounty #bugbountytips

We analyzed the vulnerability CVE-2019-0708 and can confirm that it is exploitable. We have therefore developed detection strategies for attempts to exploit it and would now like to share those with trusted industry parties. Please contact: [email protected]
How to find authentication bypass vulnerabilities. Focus. Added headers. #bugbountytips #infosecurity #CyberSec

Path Traversal Vulnerability POC: https://redacted/lib///....//....//....//....//....//....//....//....//etc//passwd #bugbountytips #lfi #bugbountywriteups #bugbounty #infosec

🚨Reset Password Vulnerabilities Testing Method🚨 📥Download PDF scarlet-ianthe-20.tiiny.site . . #bugbounty #bugbountytips #penetrationtesting #password



Something went wrong.
Something went wrong.
United States Trends
- 1. Broncos 42.7K posts
- 2. Giants 57.7K posts
- 3. Colts 27.7K posts
- 4. Packers 29.1K posts
- 5. Cowboys 25.6K posts
- 6. Lattimore 4,747 posts
- 7. Chargers 27.8K posts
- 8. Sean Payton 4,428 posts
- 9. Bo Nix 4,760 posts
- 10. Nate Hobbs 1,373 posts
- 11. Herbert 12.1K posts
- 12. Pickens 10K posts
- 13. #RaiseHail 5,742 posts
- 14. Joe Whitt 1,655 posts
- 15. Jayden Daniels 4,593 posts
- 16. Jaxson Dart 6,828 posts
- 17. Brandon Aubrey 2,429 posts
- 18. Jonathan Taylor 3,893 posts
- 19. Raiders 67K posts
- 20. Mariota 1,265 posts