#vulnerabilityexploits arama sonuçları
#VulnerabilityExploits, Not Phishing, Are the Top Cyberattack Vector for Initial Compromise Jai Vijayan lnkd.in/eQMVi_d6
@Verizon DBIR reveals 180% #vulnerabilityexploits increase as initial vector. There's an urgent need for hyperautomated solutions that can address #softwarevulnerabilities. #Hyperautomation in #ITsecurity isn't just a choice; it's becoming a necessity. bit.ly/49X3slT
#NEWSABOUTCYBER #SHAREANDFOLLOWUS The PurpleFox botnet has refreshed its arsenal with new #vulnerabilityexploits and dropped payloads, now also leveraging WebSockets for C2 bidirectional communication. bleepingcomputer.com/news/security/…
@Verizon DBIR reveals 180% #vulnerabilityexploits increase as initial vector. There's an urgent need for hyperautomated solutions that can address #softwarevulnerabilities. #Hyperautomation in #ITsecurity isn't just a choice; it's becoming a necessity. bit.ly/49X3slT
#VulnerabilityExploits, Not Phishing, Are the Top Cyberattack Vector for Initial Compromise Jai Vijayan lnkd.in/eQMVi_d6
vidde.pro/e/sm8ttuqek67w vidde.pro/e/fw9t3h4qxmxo vidde.pro/e/xevz1lxcbf1v vidde.pro/e/gi3oqvi3k8gz spesial.warnet.pro t.me/big_vvip

Do you want to find more vulnerabilities with recon? 🤑 Open this thread (step-by-step guide)! 🧵 👇

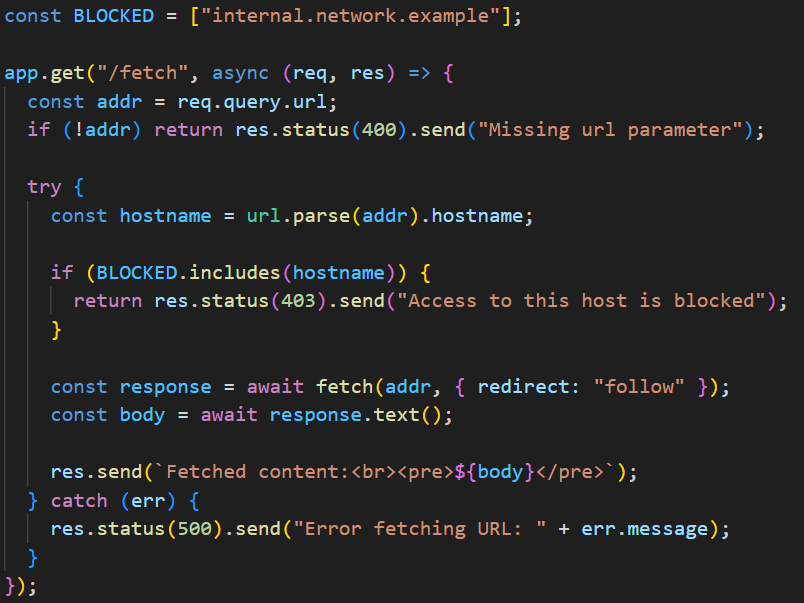
Hackers 🔥 This code contains at least 2 serious vulnerabilities. Can you spot them? 😋 What would be your exploit? 🤔
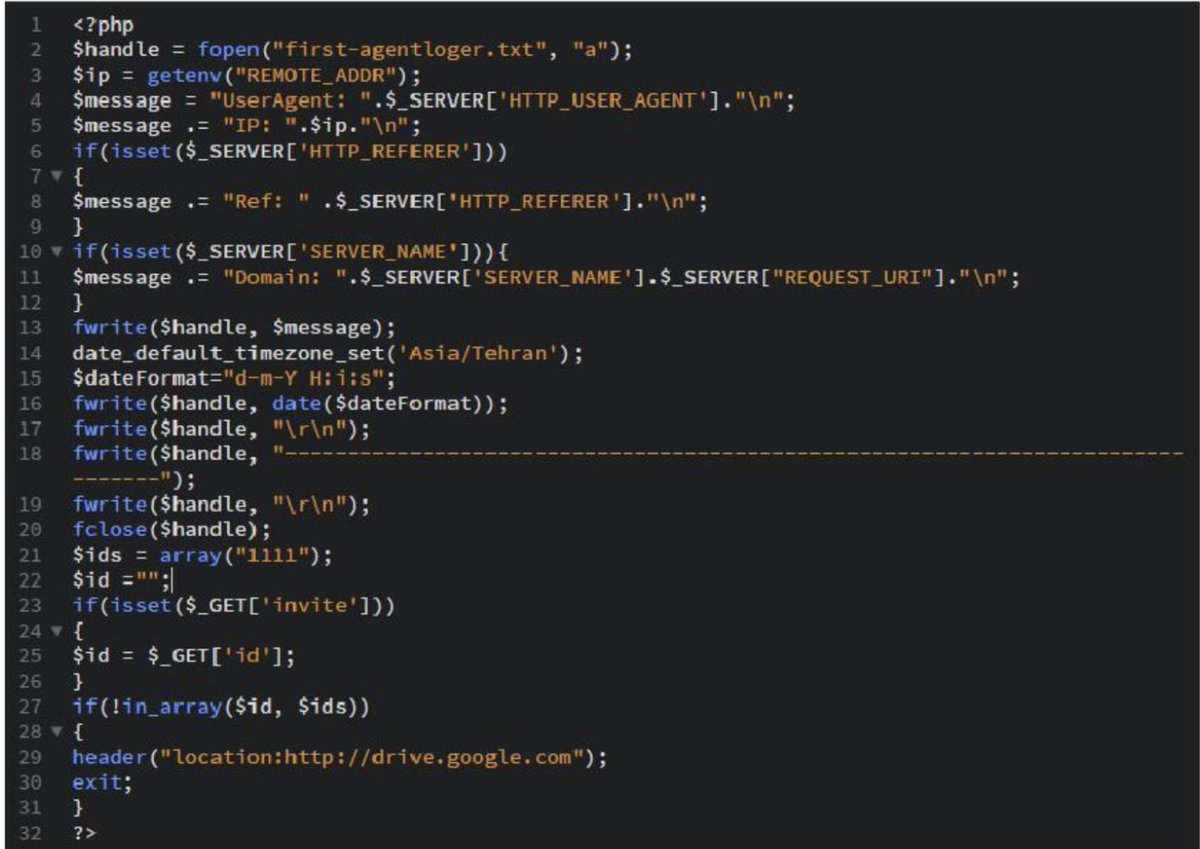
Path Traversal Vulnerability POC: https://redacted/lib///....//....//....//....//....//....//....//....//etc//passwd #bugbountytips #lfi #bugbountywriteups #bugbounty #infosec

Digging up old path traversal vulnerabilities? 🕵️♂️ I built this scanner for CVE-2022-37122 to help you find these classic bugs on your authorized targets: Github Tool: github.com/bughuntar/CVE-… #Cybersecurity #VulnerabilityScanner #BugBounty #bugbountytips #professor #the…

Top 10 Exploited Vulnerabilities #infosec #cybersecurity #pentesting #redteam #informationsecurity #CyberSec #networking #networksecurity #infosecurity #cyberattacks #security #linux #cybersecurityawareness #bugbounty #bugbountytips

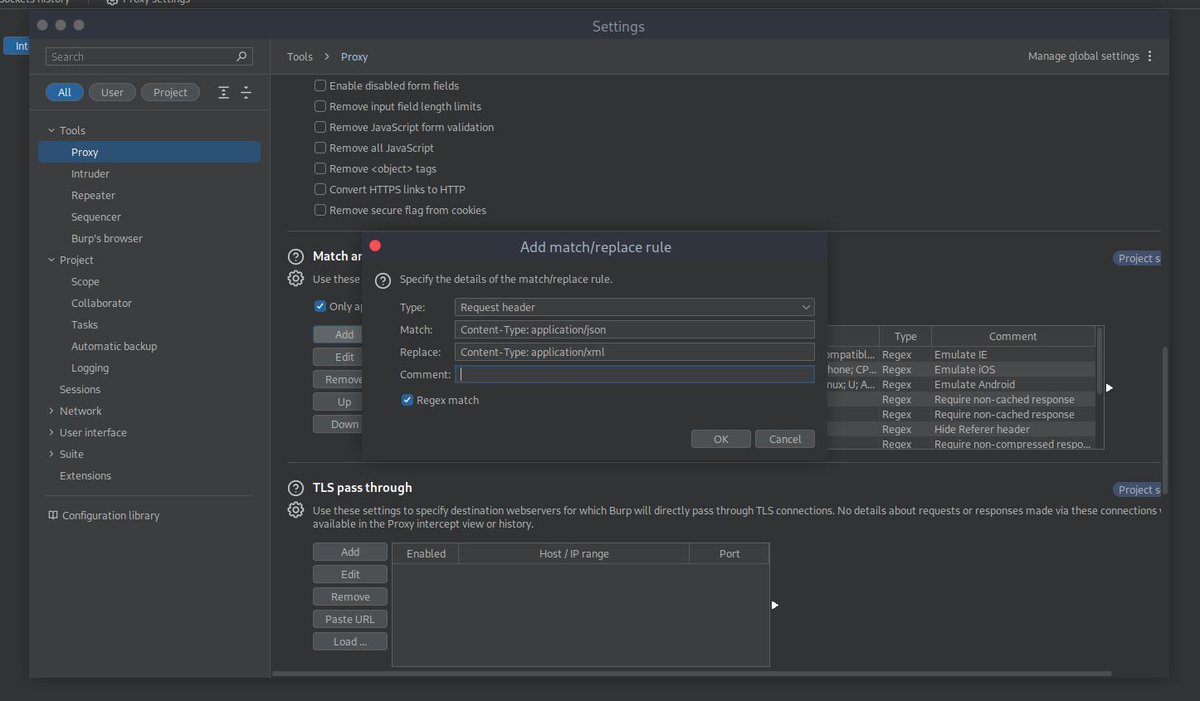
Want to find more vulnerabilities using BurpSuite match & replace rules? 🤑 Open this thread! 🧵 👇
New XINTRA course‼️ Advanced IIS Post Exploitation, Detection & Evasion Modern APT groups are actively weaponizing ToolShell and fileless IIS tradecraft to compromise Exchange, SharePoint, ASP workloads. If your detection and response capabilities lag exposure, this course…


Lenovo CVE-2025-8061: PoC for popping a system shell against the LnvMSRIO.sys driver GitHub: github.com/symeonp/Lenovo…


Hackers just turned GitHub into their command center. When police take down their servers, the malware just… reboots itself from GitHub. The twist? It hides configs inside images using steganography. This isn’t a glitch — it’s resilience by design. Read how it works →…

‼️ Iranian nation-state APT CharmingKitten exposed on GitHub: Episode 3! - BellaCiao malware samples - Google Drive phishing guides - Malware usage guides - Malware specification sheets & MORE!
⚠️#INCIBEaviso | Múltiples vulnerabilidades en EPMM y MDM de #Ivanti incibe.es/incibe-cert/al… #AvisosDeSeguridad #TI

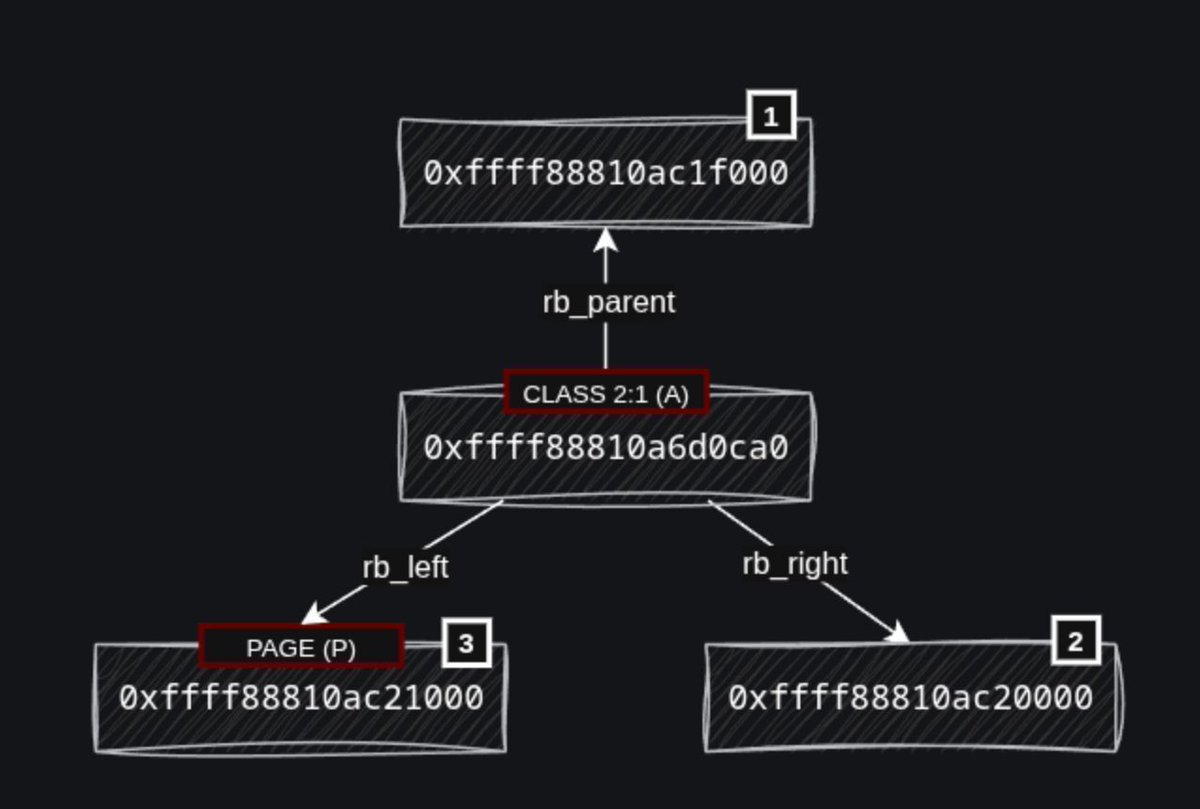
Exploiting a Use-After-Free vulnerability in the Linux network packet schedule (CVE-2025-38001) syst3mfailure.io/rbtree-family-… Credits @cor_ctf #infosec #Linux
New #Pixnapping #Android #Flaw Lets #Rogue_Apps #Steal #2FA Codes Without Permissions ift.tt/7ncB4Cz

A popular NPM package got compromised, attackers updated it to run a post-install script that steals secrets But the script is a *prompt* run by the user's installation of Claude Code. This avoids it being detected by tools that analyze code for malware You just got vibepwned

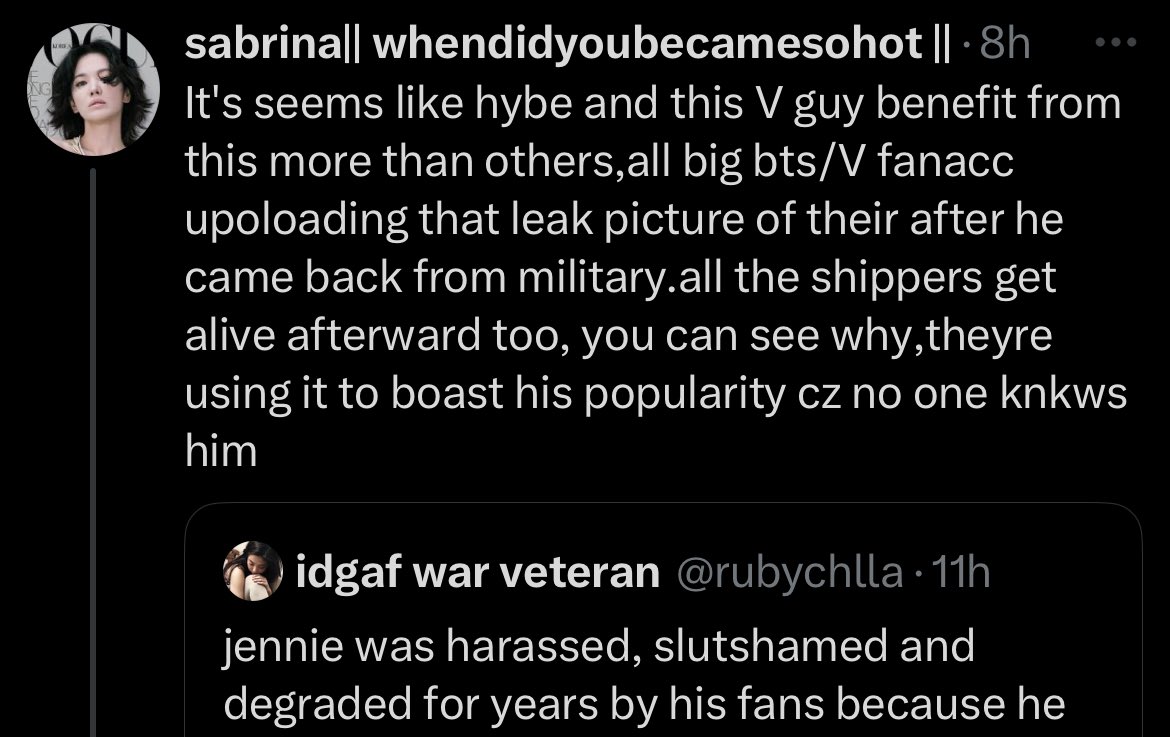
🚨 keep reporting these obsessed antis defaming 🐯 with lies do hate, th, harm (codes incitement) multiple times on all accounts x.com/rubychlla x.com/sabrinamenchild (+ CSE)
🚨Reset Password Vulnerabilities Testing Method🚨 📥Download PDF scarlet-ianthe-20.tiiny.site . . #bugbounty #bugbountytips #penetrationtesting #password



Something went wrong.
Something went wrong.
United States Trends
- 1. #Worlds2025 49.8K posts
- 2. And the Word 76.4K posts
- 3. #100T N/A
- 4. Yamamoto 50.3K posts
- 5. #DWTS 45.6K posts
- 6. halsey 9,726 posts
- 7. Young Republicans 82.3K posts
- 8. #MOST_WANTED_IN_CHICAGO 1,636 posts
- 9. Kreider 1,398 posts
- 10. Jared Butler N/A
- 11. #FlyTogether 3,079 posts
- 12. Tami 4,762 posts
- 13. Lucia 62.2K posts
- 14. George Floyd 35.9K posts
- 15. Vishnu 9,177 posts
- 16. Politico 321K posts
- 17. Will Richard 2,614 posts
- 18. The Dodgers 50.3K posts
- 19. Vivian 30.5K posts
- 20. Totodile 4,338 posts




























