CodeBitch
@CodeBitch1
CodeBitch
Intel Processor Trace may be a useful utility to determine if backdoor code is consuming too many CPU cycles.
Reverse engineering and vulnerability analysis of DJI drones' firmware. A two-parts blog series by @nozominetworks Firmware Analysis: nozominetworks.com/blog/dji-mavic… Vulnerability Analysis: nozominetworks.com/blog/dji-mavic… Particularly interesting is the chain of weak Wi-Fi password cracking…



apk-obfucation-detection - Detect code obfuscation through text classification in the detection process #MobileSecurity #AndroidSecurity github.com/liansecurityOS…
Create videos within ChatGPT 🪄 Try our VideoMaker on the GPT Store >> ChatGPT Plus required ✨
Accidentally compressed 50,000+ malware samples with the password 'infecyed'.

Looks very interesting, definitely going to give it a try!
vscode-container-wasm: An Extension of VSCode on Browser for Running Containers Within Your Browser at FOSDEM2024! By @TokunagaKohei github.com/ktock/vscode-c… github.com/ktock/containe…


16 courses on @pluralsight down and the next one in progress.. this time the focus will be on #assembly basics! For now, check out what is already there 👇 ☑️ pluralsight.com/authors/josh-s… These courses can help jump start your learning in malware analysis!

Analysis of the Huawei Security Hypervisor Worth a reading! Credits @the_impalabs Hypervisor analysis: blog.impalabs.com/2212_huawei-se… OOB vuln: blog.impalabs.com/2212_advisory_… #huawei #infosec




✝️The Holy Trinity of Game Hacking✝️ ✅Cheat Engine ☑️ReClass . NET ✅IDA Pro Learn how we use them together to find and reverse engineer the TraceLine Function 👉youtu.be/hZQzJkzmPG4

If you have failed the "OTHER CHECKS" for the League of Legends Vanguard checks, you can download github.com/rcmaehl/WhyNot… to determine which Windows security features you have disabled. You can easily fix them as a visual aid, and once you are done, you should be ready for the…


Windows game anti-cheating systems internals: in depth analysis of Vanguard's guarded regions Excellent blog post by @Xyrem256 reversing.info/posts/guardedr… #anticheat #infosec


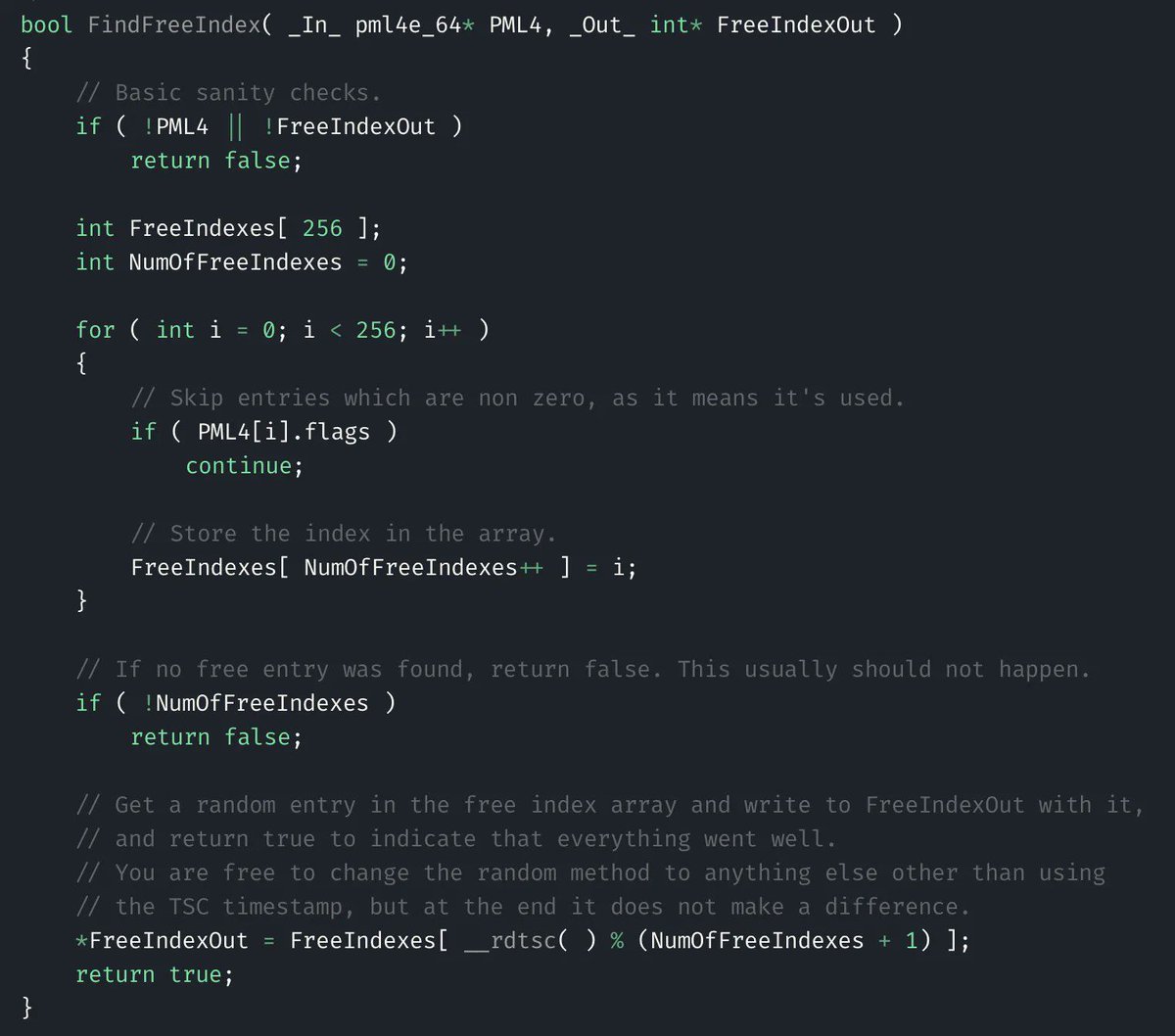
Quick preview of my ETW write-up that I did on the 'Microsoft-Windows-DotNETRuntime' Provider. Here I'm showing how certain EDR vendors are using this telemetry to build detections when .NET assemblies are reflective loaded from byte arrays.

Understanding Windows x64 Assembly sonictk.github.io/asm_tutorial/

I did two write-ups about ETW. The first one will cover how to capture an ETW trace and covers a case-study using the WinInet provider to analyze Cobalt Strike. The second one covers how EDR are using the DotNetRuntime ETW. 1. github.com/DebugPrivilege… 2. github.com/DebugPrivilege…
More Praise for "Getting Started Becoming a Master Hacker" Chosen as One of the Top 5 Cybersecurity Books of All Time AND the Top 100 Malware Books of All Time! amzn.to/3Quq4UM

Delighted to share the #STRT blog on the #Darkgate malware variant that uses DLL side loading with the Windbg, an Autoit Loader, and Splunk analytics to detect (TTPs) extracted during R.E. I hope it helps! 😊 #splunk #int3 #malware #blueteam splunk.com/en_us/blog/sec…



Understanding Dirty Pagetable - m0leCon Finals 2023 CTF Writeup ptr-yudai.hatenablog.com/entry/2023/12/… #pentesting #cybersecurity #Infosec




🍯 Galah An LLM-powered web honeypot that uses #OpenAI to respond to arbitrary HTTP requests GET /login.php → Returns HTML/PHP + login form GET /.aws/credentials → Returns fake creds ➡️ Mimics lots of software with 1 prompt By @0x4d31 #infosec github.com/0x4D31/galah
RE tip of the day: Apart from parsing PEB to find its ProcessHeap structure, whose fields reveal the presence of the debugger, malware can use GetProcessHeap or RtlGetProcessHeaps APIs that return a pointer to ProcessHeap. #infosec #cybersecurity #malware #reverseengineering
Introduction to user space Linux rootkits with C code examples Credits @h0mbre_ buff.ly/33TK3jM #linux #rootkit




United States Xu hướng
- 1. #RaiseHail 2,319 posts
- 2. Good Sunday 80.2K posts
- 3. #PhinsUp 2,153 posts
- 4. Matt Gay N/A
- 5. Jacob Martin N/A
- 6. #AskFFT N/A
- 7. #sundayvibes 6,095 posts
- 8. Mariota 1,107 posts
- 9. #Dolphins N/A
- 10. Chris Rodriguez N/A
- 11. Spain 72.5K posts
- 12. Kenneth Grant N/A
- 13. CRod N/A
- 14. Blessed Sunday 22.6K posts
- 15. Kliff N/A
- 16. Who Dey 8,080 posts
- 17. Sunday Funday 2,918 posts
- 18. Full PPR N/A
- 19. Portugal 60K posts
- 20. Madrid 148K posts
Something went wrong.
Something went wrong.