You might like
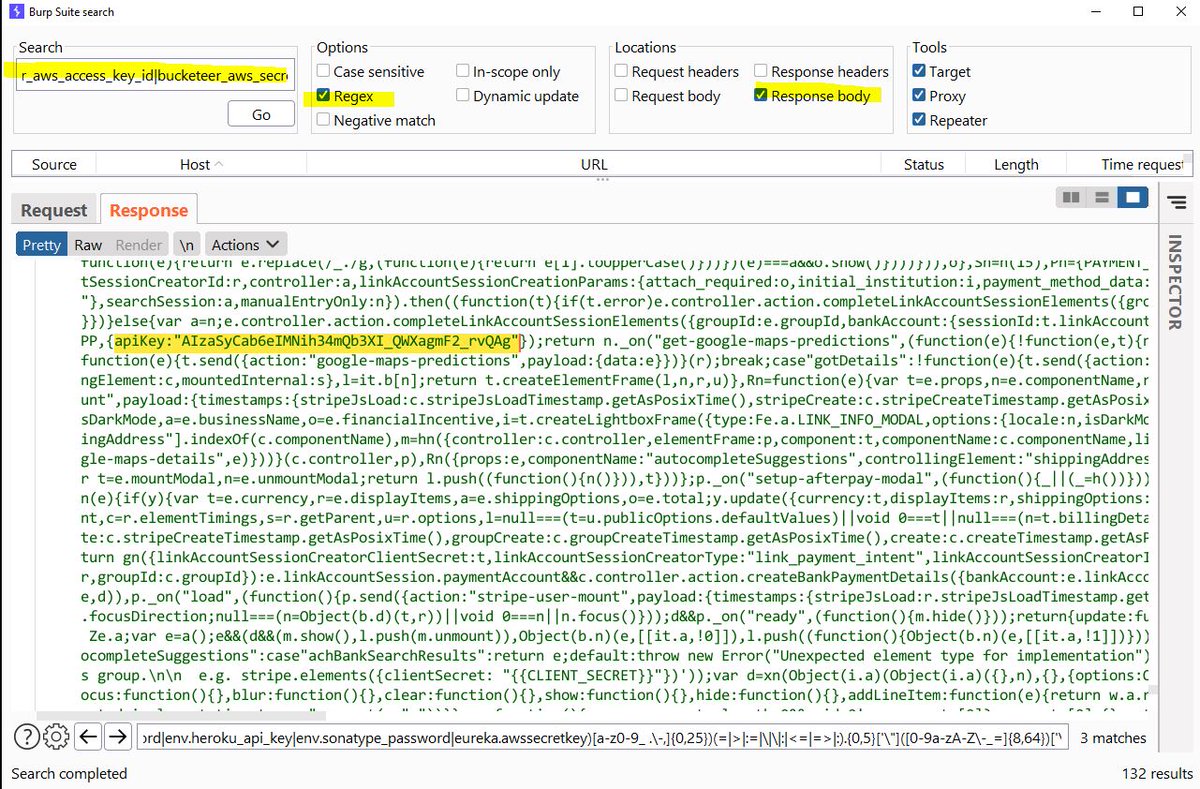
Search for all leaked keys/secrets using one regex! regex: gist.github.com/h4x0r-dz/be69c… #BugBounty #bugbountytip
CloudRip Fast Cloudflare bypass scanner Find real server IPs behind Cloudflare by scanning subdomains. Multi-threaded for speed, skips Cloudflare-owned IPs, supports custom or built-in wordlists, and exports results. Built-in rate limiting to avoid getting blocked REPO ⤵️

🚀 sandmap Nmap on steroids. Simple CLI with the ability to run pure Nmap engine, 31 modules with 459 scan profiles. github.com/trimstray/sand…
Arctic Wolf Labs reports that the China-linked threat actor UNC6384 targeted European diplomatic entities in Hungary and Belgium during September and October 2025, exploiting ZDI-CAN-25373 and deploying PlugX RAT malware. arcticwolf.com/resources/blog…

These three extensions will definitely help and save you time during your bug hunting process: Fake Filler, Code Formatter: js, css, json
Becoming a Security Researcher with @4osp3l as my mentor — Day 22 - I haven’t been feeling, but I still managed to read the web hacking recon from Vivkie’s bug bounty book and practiced on a real platform. I also went through a Medium posts to see how other hunters do recon


⚠️⚠️ CVE-2025-12463 — critical unauthenticated SQLi (CVSS 9.8) in Geutebruck G-Cam E-Series 🎯1.9k+ Results are found on the en.fofa.info nearly year. 🔗FOFA Link: en.fofa.info/result?qbase64… FOFA Query: app="GEUTEBRUCK" 🔖Refer: blog.blacklanternsecurity.com/p/cve-2025-124… #OSINT #FOFA…

GitHub - rix4uni/originiphunter: A powerful Go tool for finding origin IPs of domains by querying multiple security APIs and validating results with built-in HTTP client. github.com/rix4uni/origin…
A smarter web fuzzing tool that combines local LLM models and ffuf to optimize directory and file discovery github.com/Invicti-Securi…

Hell nahh..Check this out all🔥you will enjoy it <33 Full Admin pannel access via this simple methodology..
🚩 Master the Art of CTFs: The Ultimate Cybersecurity Cheatsheet 💻⚡ Capture The Flag (CTF) challenges are one of the fastest ways to build real, hands-on hacking skills and this cheatsheet is designed to take you from beginner to expert

GitHub - rix4uni/emailextractor: High-speed Go email scraper that crawls sites and internal links concurrently to collect email addresses for reconnaissance, research, or sales intelligence. github.com/rix4uni/emaile…
New research blog: We identified a stealthy multi-stage campaign, Operation #SkyCloak, targeting Russian & Belarusian military personnel Attack uses PowerShell infection with #Tor obfs4 bridges to expose RDP, SMB, SSH for persistent remote access #APT #OpenSSH #Malware #NetFlow

This Google Dork Exposes Internal Test Environments 🔥 inurl:test | inurl:env | inurl:dev | inurl:staging | inurl:sandbox | inurl:debug | inurl:temp | inurl:internal | inurl:demo site:example[.]com #BugBounty #BugBountyTips #CyberSecurity #Pentesting #EthicalHacking #Hacking
![Yass1nMohamed's tweet image. This Google Dork Exposes Internal Test Environments 🔥
inurl:test | inurl:env | inurl:dev | inurl:staging | inurl:sandbox | inurl:debug | inurl:temp | inurl:internal | inurl:demo site:example[.]com
#BugBounty #BugBountyTips #CyberSecurity #Pentesting #EthicalHacking #Hacking](https://pbs.twimg.com/media/G4iM8jOWkAAPfQN.jpg)
Web Application Penetration Testing Checklist👾 Credits: @e11i0t_4lders0n 🔗alike-lantern-72d.notion.site/Web-Applicatio…

GitHub - Matrix-Community-ORG/SSHCracker: A powerful (SSH Cracker) and efficient SSH connection testing tool written in Go. Features include multi-threaded testing, real-time progress monitoring, Discord webhook integration, and a robust license system. github.com/Matrix-Communi…
🚨 CVE-2023-2437 - critical 🚨 UserPro <= 5.1.1 - Authentication Bypass > The UserPro plugin for WordPress through 5.1.1 allows authentication bypass via the u... 👾 cloud.projectdiscovery.io/library/CVE-20… @pdnuclei #NucleiTemplates #cve
⚠️⚠️ CVE-2025-10932: High 8.2/10 Vulnerability in MOVEit Transfer AS2 module (by Progress Software) — allows unauthorized data exposure or manipulation 🎯2.4k+ Results are found on the en.fofa.info nearly year. 🔗FOFA Link: en.fofa.info/result?qbase64… FOFA Query:…

United States Trends
- 1. Grammy 443K posts
- 2. Vesia 3,359 posts
- 3. #FliffCashFriday 2,518 posts
- 4. Dizzy 11.1K posts
- 5. #drwfirstgoal N/A
- 6. James Watson 12.5K posts
- 7. Georgetown 2,290 posts
- 8. Capitol Police 15.7K posts
- 9. Thank a Republican 1,075 posts
- 10. Collar 14.4K posts
- 11. Dylan Edwards N/A
- 12. Myles Rice N/A
- 13. Silver Slugger 10.8K posts
- 14. NBA Cup 5,521 posts
- 15. Kansas 23.1K posts
- 16. Darryl Strawberry 1,836 posts
- 17. Chase 85.7K posts
- 18. Filibuster 376K posts
- 19. MANELYK EN COMPLICES 17K posts
- 20. Laporta 14.8K posts
You might like
-
 Munna✨
Munna✨
@mr0x1_ -
 Aman Singh !!🇮🇳!!
Aman Singh !!🇮🇳!!
@hackeriron1 -
 Ritik Chaddha(pwn_box)
Ritik Chaddha(pwn_box)
@RitikChaddha -
 Uncle Adisa
Uncle Adisa
@pwn5t4r -
 0xWizard
0xWizard
@noob_labs -
 Maniesh.Neupane
Maniesh.Neupane
@pwn4arn -
 BlackHydra
BlackHydra
@blackhydra443 -
 Alex Farias
Alex Farias
@alexfariasec -
 bl@ck9rnC3
bl@ck9rnC3
@bla3k9rnc3 -
 Logan
Logan
@LoganWerewolf -
 om_prakash
om_prakash
@om_pakash_ -
 Dreams of Tragedy
Dreams of Tragedy
@DreamsofTragedy -
 Anouar Youcef
Anouar Youcef
@EthicalhackerC -
 Andreu Band
Andreu Band
@andrii_band -
 Ronin
Ronin
@_Ronin_0_
Something went wrong.
Something went wrong.



































































































































