You might like
1. Dev exposed .env in a mp4; was only able to partially use the secrets. 2. In 2FA flow, correct OTP request was validated by server, blocking manual entry via frontend. By directly browsing the URL from correct OTP response made successful login into the account. #BugBounty



Who are buying iphone in bigbillon days on emi #Flipkart #Amazon #BigBillionDays #bigboss
I'm 24 hours into my first bug bounty program, but seeing the source code in scope and devs fixing bugs publicly(pushing in github) makes me feel discouraged—should I keep going toward my 100-hour goal, or change the target, source code review seems overwhelming
10 hacking tools I've developed over the years 👇

This 👇
I just hacked multiple @lovable_dev 'top launched' sites Wait—what? In less time than it took me to finish my lunch (47 mins), I extracted from live production apps: 💰Personal debt amounts 🏠Home Addresses 🗝️API keys (admin access) 🔥Spicy Prompts Screenshots in thread…
Use fast and simple Google Dorks during recon. They can 𝐫𝐞𝐯𝐞𝐚𝐥 𝐬𝐞𝐧𝐬𝐢𝐭𝐢𝐯𝐞 𝐢𝐧𝐟𝐨 𝐥𝐢𝐤𝐞 .𝐞𝐧𝐯 𝐟𝐢𝐥𝐞𝐬, 𝐃𝐁 𝐝𝐮𝐦𝐩𝐬, 𝐜𝐨𝐧𝐟𝐢𝐠 𝐟𝐢𝐥𝐞𝐬, 𝐚𝐧𝐝 𝐛𝐚𝐜𝐤𝐮𝐩𝐬. Follow me 👉🏼 DarkShadow 😁 #bugbountytip #recon #infosec #dork


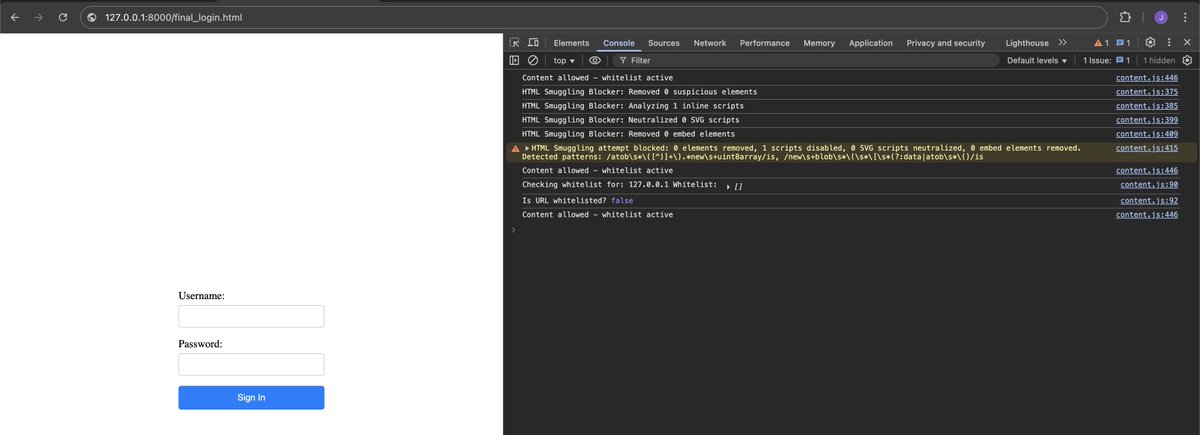
Great research here this technique leverages Rust’s capabilities to compile to WASM for HTML smuggling (lrqa.com/en/cyber-labs/…) - Next Level Smuggling with WebAssembly. However, my extension "SmuggleShield" prevents such crafted file by default. #infosec #redteam #blueteam
Top-25 Github Cybersec Projects Credit @xmodulo #infosec #cybersecurity #cybersecuritytips #microsoft #redteam #informationsecurity #CyberSec #microsoft #offensivesecurity #infosecurity #cyberattacks #security #oscp #cybersecurityawareness #bugbounty #bugbountytips

Awesome Wordlists A curated list of wordlists for bruteforcing and fuzzing. github.com/n0kovo/awesome… #infosec #bugbounty #pentesting t.me/hackgit/8096
💡 Quick tip! When testing WordPress targets, always make sure to check for exposed backup files! These are sometimes saved in the web root path of the server and accessible to anyone! 🤠 Here's a list of common file names to look for! 👇

⚠️ Giveaway ⚠️ Want to learn modern reconnaissance and hacking skills? Join The Bug Hunter's Methodology Cohort 5! October 2nd, 3rd, 4th - jhaddix.gumroad.com/l/kihwd Like and retweet this post for a chance to win a free seat! Five winners will be announced on Sept 1st!
Aws pentesting Testing checklist by @wtf_brut #bugbounty #bugbountytips

Challenge solutions and source code from this year's @DownUnderCTF 🔥 github.com/DownUnderCTF/C…
United States Trends
- 1. #Worlds2025 38.1K posts
- 2. #TalusLabs N/A
- 3. Raindotgg 1,944 posts
- 4. Doran 15.9K posts
- 5. #T1WIN 25.6K posts
- 6. Sam Houston 1,520 posts
- 7. Boots 29.1K posts
- 8. Oregon State 4,805 posts
- 9. Lubin 5,651 posts
- 10. Faker 30.9K posts
- 11. #GoAvsGo 1,572 posts
- 12. Louisville 14.4K posts
- 13. Keria 9,484 posts
- 14. #T1fighting 3,284 posts
- 15. Batum N/A
- 16. UCLA 7,828 posts
- 17. Miller Moss 1,237 posts
- 18. Emmett Johnson 2,533 posts
- 19. Oilers 5,197 posts
- 20. Hyan 1,351 posts
You might like
-
 d4rk_c0r3
d4rk_c0r3
@d4rk_c0r3 -
 Eslam Monex 🕵️🧑💻
Eslam Monex 🕵️🧑💻
@eslam_monex -
 bl@ck9rnC3
bl@ck9rnC3
@bla3k9rnc3 -
 Aditya Rusmana
Aditya Rusmana
@justbecomfy4 -
 Crypto Yoda 😈😎
Crypto Yoda 😈😎
@Kingsblanc -
 Eduardo José Guerrero Romero
Eduardo José Guerrero Romero
@4b3rf0rth -
 Hacker1VIP
Hacker1VIP
@Hacker1V -
 BlackHydra
BlackHydra
@blackhydra443 -
 graceful glimmer
graceful glimmer
@perlyglow -
 nefta camarco perez
nefta camarco perez
@neftacamarcoper -
 H0ffen
H0ffen
@colorwils0n -
 Ronin
Ronin
@_Ronin_0_ -
 Usman Ali
Usman Ali
@ual1cyb -
 Connor
Connor
@ceoofdankmemes -
 Mr_Pc
Mr_Pc
@MrPc69257431
Something went wrong.
Something went wrong.