K7 Computing
@k7computing
K7 Computing is a world leader in providing high quality #cybersecurity solutions for consumers and businesses. Buy Now: http://bit.ly/3PEQqzY #k7antivirus
قد يعجبك
Our gold award win confirms that K7’s customers are protected by the best in the world! Your computing experience will never be marred by a cyber attack or a device that slows down due to cyber security. #goldaward #gold #antivirus #cybersecurity #worldleader @AV_Comparatives

The Log4j vulnerability has been well known for several years, but we still find organisations running vulnerable versions! Swipe through for mitigation measures, and learn more about how K7 VAPT can help you strengthen enterprise cybersecurity at k7computing.com/in/business-us…




#Cybersecurity isn't a one-time solution; it's an ongoing journey. From vulnerability assessments to penetration testing, our latest blog explores how tailored strategies can protect your business from evolving threats. blog.k7computing.com/cybersecurity-…




A new campaign is hijacking WhatsApp Web sessions to spread malware to a victim's contacts. It's a threat that leverages trust to bypass your defenses. labs.k7computing.com/index.php/braz… #CyberSecurity #Malware #InfoSec #ThreatIntel #WhatsApp #K7Labs #K7Security #ThreatLandscape

Attackers are getting smarter, using signed Microsoft binaries to hide their tracks. Our latest analysis reveals how a hidden Python fragment injects into cvtres.exe to evade detection. Get the full technical breakdown here labs.k7computing.com/index.php/mask… #CyberSecurity #MalwareAnalysis

Today we celebrate the men who contribute to stronger homes, teams, and communities. Warm wishes from K7 Security on International Men’s Day. #internationalmensday2025



K7 Computing’s Samir Mody will speak at the panel discussion on maintaining impartiality in cybersecurity testing and fostering trust in testing at AVAR 2025 on 5 December 2025 – events.aavar.org/cybersecurity-…

K7 Computing’s Baran Kumar S will analyse the SpyMax Android Remote Access Trojan’s architecture and obfuscation mechanism, and discuss the use of LLMs for Android malware analysis, at AVAR 2025 on 5 December 2025 – events.aavar.org/cybersecurity-…

K7 Computing’s Suresh Reddy Lomada will speak on the Tiny FUD backdoor that targets macOS devices, and analyse its DYLD injection technique, at AVAR 2025 on 5 December 2025 – events.aavar.org/cybersecurity-…

K7 Computing’s Anurag Shandilya, Arnab Mandal, and Satyam yadav will speak on NTLM relay techniques and provide best practices to defend against such attacks at AVAR 2025 on 4 December – events.aavar.org/cybersecurity-… AVAR Asia

K7 Security is proud to sponsor the 28th AVAR Annual Conference! The event features AI training for cybersecurity leaders, 2 days of knowledge sessions and panel discussions, plus social events for industry networking. Register now for AVAR 2025: events.aavar.org/cybersecurity-…

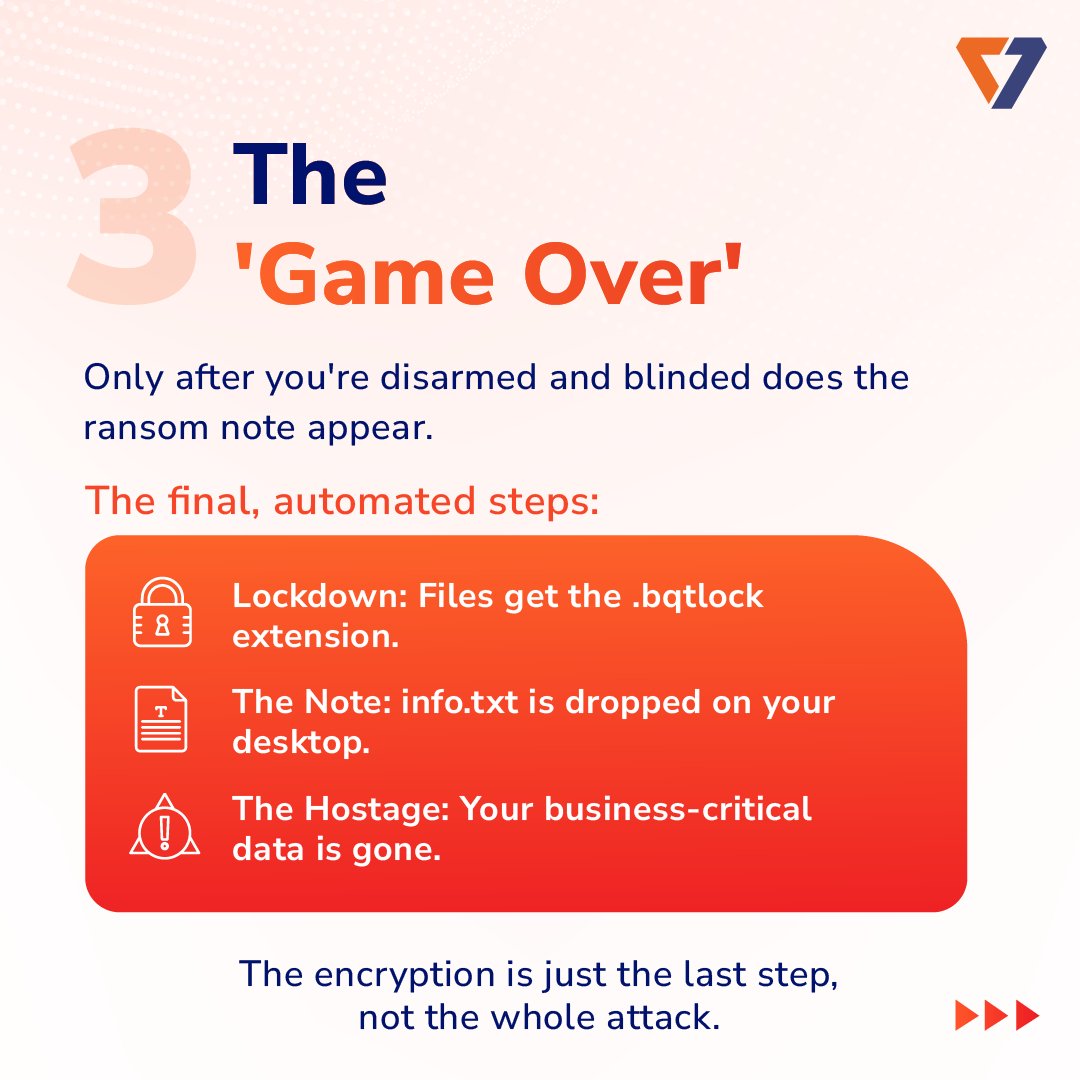
Stop focusing on the ransom note. The real attack is surgical. Swipe to see how BQTLock disarms your databases before locking a single file. Get the intelligence you need to actually stay safe. Download K7 Q2-2025_26 Threat Report now. rebrand.ly/K7_CTM_Q2_2025… #ThreatReport



Ransomware groups have created new versions of ransomware that cannot be detected by conventional endpoint security. Stay ahead of threat actors and their evolving tactics with K7 Endpoint Security – Graphene. Try it in your organisation – k7computing.com/in/business-us…

Rathna K, Senior Product Manager at K7 Security, will be speaking at the webinar on Staying Safe in the Age of AI-Driven Cyber Attacks organised by the Nehru Science Centre, Mumbai, on 22 October 2025 at 11.30 AM. Register for the webinar at tinyurl.com/CybersecurityA…

May your Deepavali shine bright with happiness, success, and security. K7 wishes you a Safe and Happy Deepavali!

United States الاتجاهات
- 1. Penn State 19.8K posts
- 2. #twitchrecap 12.9K posts
- 3. #TADCFriend 1,715 posts
- 4. Paul Dano 1,378 posts
- 5. Pat Kraft 2,325 posts
- 6. Romero 23.4K posts
- 7. Slay 20.3K posts
- 8. Zion 9,941 posts
- 9. Tarantino 8,150 posts
- 10. #LightningStrikes N/A
- 11. #GivingTuesday 32.2K posts
- 12. Fulham 45.9K posts
- 13. Bernie 25.5K posts
- 14. Somali 174K posts
- 15. Larry 63.7K posts
- 16. Franklin 68.6K posts
- 17. Sabrina Carpenter 44.2K posts
- 18. Sleepy Don 6,290 posts
- 19. Trump Accounts 31.2K posts
- 20. Terry Smith 1,025 posts
قد يعجبك
-
 Anees Merchant
Anees Merchant
@aneesmerchant -
 Adlice
Adlice
@AdliceSoftware -
 AVAR Asia
AVAR Asia
@avar_asia -
 null Ahmedabad (n|u Ahmedabad)
null Ahmedabad (n|u Ahmedabad)
@NullAhm -
 AV-Comparatives
AV-Comparatives
@AV_Comparatives -
 Emsisoft
Emsisoft
@emsisoft -
 Anna Gát 🧭
Anna Gát 🧭
@TheAnnaGat -
 Amr Thabet
Amr Thabet
@Amr_Thabet -
 Brian E. Thomas
Brian E. Thomas
@DivergentCIO -
 eScan AV
eScan AV
@escan_tweet -
 MRG Effitas
MRG Effitas
@mrgeffitas -
 thecyberlama
thecyberlama
@thecyberlama -
 Brian A. Marschhauser
Brian A. Marschhauser
@marsch_madness
Something went wrong.
Something went wrong.