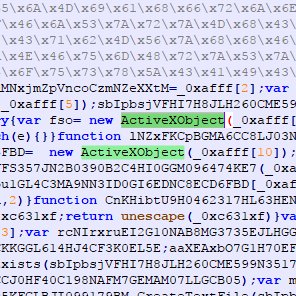
𝔫𝔲𝔪𝔟 𝔣𝔯𝔞𝔫𝔨
@malware_gawk
Malware Researcher, Creator of things and tech hoarder
You might like
#Ransomware: the crime that pays. 💸 With attacks on critical infrastructure and mega breaches hitting the headlines almost weekly, ransomware is holding the #cybersecurity spotlight at the moment. Tune in to this special episode of #CyberHumanity: hubs.ly/H0QLq6f0
player.captivate.fm
39: The Crime That Pays: Ransomware Special
Going to be taking a technical dive into the malware associated with Nobelium, if you want to play along: Free Labs: hubs.ly/H0QgsGK0 Walkthrough Webinar: hubs.ly/H0QgsC80

Proud to have been a part of the @immersivelabs journey so far and can not wait to see what this year brings with $75 Million in investment. 🚀techcrunch.com/2021/06/13/cyb…
techcrunch.com
Cybersecurity training platform Immersive Labs closes $75M Series C led by Insight Partners |...
Immersive Labs, a platform which teaches cybersecurity skills to corporate employees by using real, up-to-date threat intelligence in a “gamified” way,
I just tipped @KevTheHermit using the Brave Browser. Check it out at brave.com/tips. #TipWithBrave
Did not realise @msftsecurity had an API to query Patch Tuesday releases, really easy to write a python script to show some interesting stats in #PatchTuesday updates

..- .-. --. . -. - -....- .. ... .- -. -.-- --- -. . -.. --- .. -. --. .- -. -.-- - .... .. -. --. --- -. - .... . .---- ..--- -....- .---- ...-- - .... -. --- ...- . -- -... . .-. - .... .. ... -.-- . .- .-. ..--.. -....- -- . ... ... .- --. . . -. -.. ...
Verifying myself: I am gazlockwood on Keybase.io. n2aarFJhWjwi10XL93_jxmQNSM_Zt7RurtFs / keybase.io/gazlockwood/si…
ICYMI (and how could you?), #Hafnium has been exploiting four zero-day vulnerabilities in Microsoft Exchange. In our latest blog, we get hands-on Hafnium – and give you the chance to do the same with FREE labs in Community Mode! hubs.ly/H0Jk7bN0
Having a fun "early morning" with friends @LucidUnicorn_ @malware_gawk @Bambooj0e exploiting the new #saltstack #CVE CVE-2021-25281 this is why I love working @immersivelabs


CVE-2020-0796 - a "wormable" SMBv3 vulnerability. Great... 😂
Cutter v1.8.3 has just been released! With significantly better performance and stability 🚀 We introduce major improvements to our analysis speed, a better UI and fixed bugs that were reported by you - keep 'em coming! Download and release notes @ github.com/radareorg/cutt…
We are excited to introduce one of your most requested features! Cutter, the radare2 GUI, now supports Graph Overview to easily navigate in big graphs and quickly spot flow patterns. A big thanks for @Vane11ope that made this happen! ❤️
Posted hash and torrent sets 338 through 352 with over 163GB of zipped #malware samples. Users login for links.
Malware, Malware Everywhere!!! .. 🤨🤨 I gonna have a very fun sunday!! .. 🤓🤓



#powershell #fun 2 Use $ExecutionContext.InvokeCommand.#PreCommandLookupAction or #CommandNotFoundAction to manipulate the executed commands or run arbitrary code E.g. override CommandNotFoundAction to launch a process when a command is not found and its name starts with #wtf
Just posted another article on macro based malware (Lazarus APT Group). This one injects function addresses like VirtualAlloc into shellcode within the VBA Macro. I describe a short an easy way to get to the actual shellcode. cyberfox.blog/macro-malware-…

United States Trends
- 1. Rodgers 14K posts
- 2. Steelers 31.7K posts
- 3. Chargers 20.1K posts
- 4. #RHOP 5,880 posts
- 5. Herbert 8,888 posts
- 6. #HereWeGo 4,438 posts
- 7. Schumer 178K posts
- 8. Tim Kaine 8,214 posts
- 9. #ITWelcomeToDerry 2,615 posts
- 10. Cade Cunningham 3,786 posts
- 11. Jaylen Warren 1,341 posts
- 12. #90DayFianceHappilyEverAfter 1,741 posts
- 13. Rams 29K posts
- 14. Durbin 12K posts
- 15. Jassi 1,495 posts
- 16. Drummond 2,598 posts
- 17. Resign 84.2K posts
- 18. #snfonnbc N/A
- 19. Commanders 143K posts
- 20. Boswell 1,464 posts
Something went wrong.
Something went wrong.