Quang Vo
@mr_r3bot
OutputDebugString(L"Till no more bug") . Tweets are my own
You might like
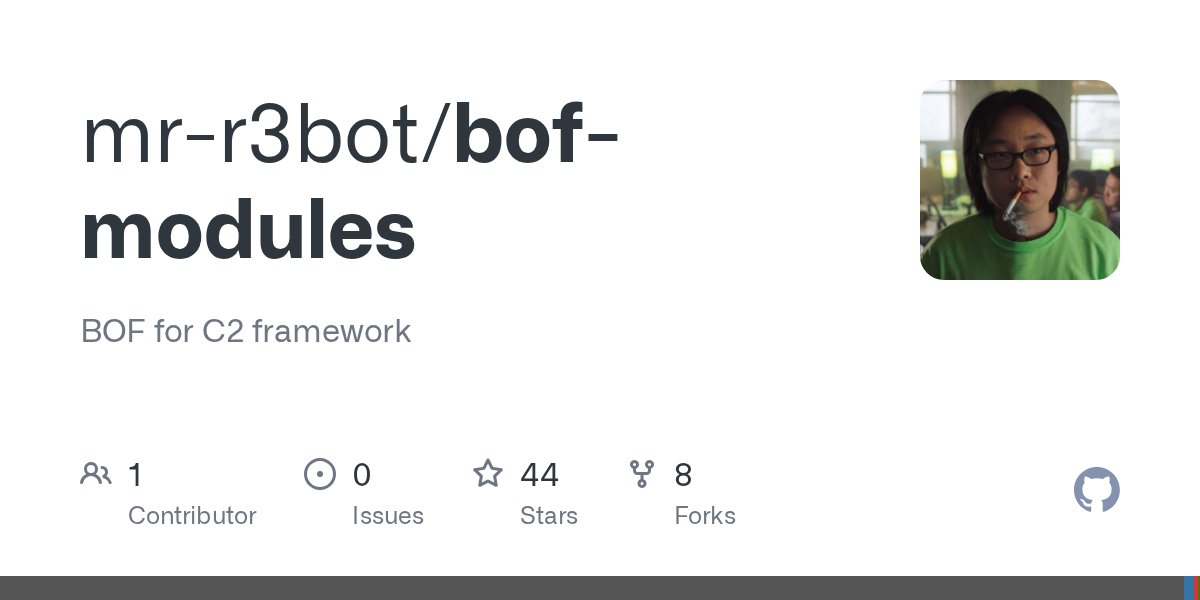
Inspired by @tijme talks about COM and UAC bypass , I have ported his POC code for exploiting COM object to bypass UAC and eventually elevated permission to BOF file and integrate it to Havoc client modules Any feedbacks are welcome. github.com/mr-r3bot/bof-m…
As a follow up to my last post, here is part II of driver reverse engineering 101, this time about dynamic analysis. We unpack a VMProtected kernel driver and restore its IAT with some emulation. Enjoy:) eversinc33.com/posts/driver-r…
I with my colleagues from @GroupIB_TI and @GroupIB_DFIR uncover how #UNC2891 is blending stealthy malware, physical infiltration, and money #mule ops to pull off high-impact bank attacks in Southeast Asia. 📌 Key findings: • Undetected access since 2017 • Rootkits, log…


#Lazarus carry out hands-on-keyboard activities for at least six consecutive hours, using compromised WordPress sites with vulnerable plugins as part of their attack infrastructure.#DreamJob orangecyberdefense.com/global/blog/ce…

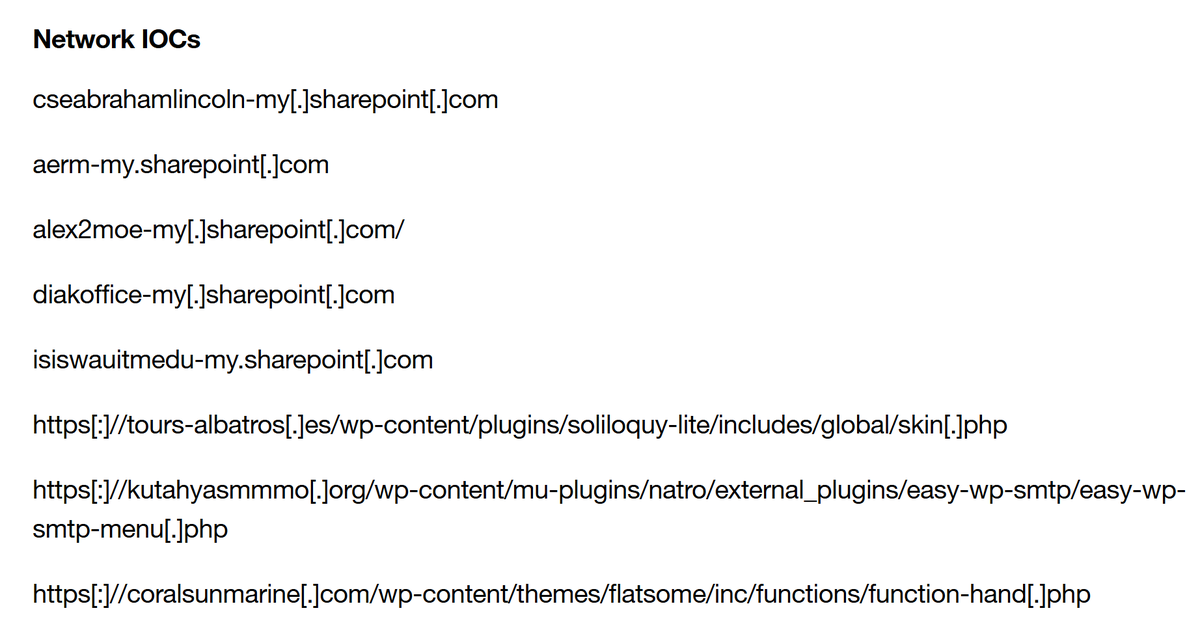
#Lazarus Operation DreamJob targets the UAV sector DroneEXEHijackingLoader.dll /ScoringMathTea RAT welivesecurity.com/en/eset-resear…

Writeup of new PDF malware converter: blog.lukeacha.com/2025/11/primep… Persistence, remote code execution, browser hijack, obfuscation, and more. #YAPA #EvilAI @SquiblydooBlog @MalasadaTech808 @x3ph1 @SecurityAura
ESET researchers have discovered a network implant used by the China-aligned PlushDaemon APT group to perform adversary-in-the-middle attacks | welivesecurity.com/en/eset-resear… @ESET
Autumn Dragon: China-nexus APT Group Targets South East Asia In this report, we describe how we tracked for several months a sustained espionage campaign against the government, media, and news sectors in several countries surrounding the South China Sea: cyberarmor.tech/blog/autumn-dr…
A bit late but here are the slides for the talk I gave at London Beacon25 conference, on UDRLs: rwxstoned.github.io/2025-11-19-bea…
Researchers from the Israel National Digital Agency have uncovered an ongoing espionage campaign conducted by Iranian threat actors tracked as SpearSpecter (APT42, Mint Sandstorm, Educated Manticore, CharmingCypress). govextra.gov.il/national-digit…

🐈 Cat’s Got Your Files: Lynx Ransomware 🎉New report out by @Friffnz, Daniel Casenove & @MittenSec!🎉 Attackers used stolen creds to access RDP, quickly pivoted to a DC with a second compromised admin, created impersonation accounts, mapped the environment, and more.

#Lazarus ScoringMathTea is a RAT (Remote Access Trojan) in C++, developed and operated by Lazarus, which provides operators with all the necessary capabilities that a good RAT can offer, including remote command execution, loading and execution of plugins in memory, among other…

📣 Everything defenders need to know about UNC1549: a deep dive analysis of suspected Iran-nexus espionage targeting the aerospace, aviation, and defense industries in the Middle East. Dive into the details: bit.ly/3LLpzFF

Malware development tricks, by @cocomelonckz 46 Windows keylogger cocomelonc.github.io/malware/2025/0… 47 Windows clipboard hijacking cocomelonc.github.io/malware/2025/0… 48 leveraging Office macros cocomelonc.github.io/malware/2025/0… 49 abusing Azure DevOps REST API for covert data channels cocomelonc.github.io/malware/2025/0…
#APT28 OneDrive.exe Sideloading + SSPICLI.dll + tmp7E9C.dll + sspicli.dll + testtemp.ini (VBA Macro backdoor) = Outlook Macro splunk.com/en_us/blog/sec…


Attention malware analysts 💻 Our latest blog post delves into Time Travel Debugging (TTD). We introduce the basics of WinDbg and TTD to help you start incorporating TTD into your analysis. 📄: bit.ly/441J3vS

#ElasticSecurityLabs uncovers #RONINGLOADER, a multi-stage loader utilizing signed drivers, PPL abuse, CI Policies, and other evasion techniques to deliver #DragonBreath's gh0st RAT variant. Check it out at ela.st/roningloader

United States Trends
- 1. Jameis 34.6K posts
- 2. Gibbs 11.1K posts
- 3. Giants 72.4K posts
- 4. Chiefs 60.5K posts
- 5. Colts 28K posts
- 6. Lions 50.2K posts
- 7. JJ McCarthy 6,080 posts
- 8. Steelers 45.8K posts
- 9. Bears 60.2K posts
- 10. Vikings 28.2K posts
- 11. Mahomes 15.7K posts
- 12. Ravens 23.2K posts
- 13. Bengals 20.3K posts
- 14. Tomlin 5,794 posts
- 15. Tony Romo 3,002 posts
- 16. Campbell 16.4K posts
- 17. #OnePride 3,702 posts
- 18. Shane Bowen 1,429 posts
- 19. #GoPackGo 4,958 posts
- 20. Mason Rudolph 5,615 posts
You might like
-
 Bien 🇻🇳
Bien 🇻🇳
@bienpnn -
 frycos
frycos
@frycos -
 jkana101
jkana101
@jkana101 -
 Tuan Anh Nguyen⚡️ 🇻🇳
Tuan Anh Nguyen⚡️ 🇻🇳
@haxor31337 -
 VCSLab
VCSLab
@vcslab -
 Đào Trọng Nghĩa
Đào Trọng Nghĩa
@nghiadt1098 -
 Thach Nguyen Hoang 🇻🇳
Thach Nguyen Hoang 🇻🇳
@hi_im_d4rkn3ss -
 Piotr Bazydło
Piotr Bazydło
@chudyPB -
 Icare
Icare
@Icare1337 -
 Công Thành Nguyễn
Công Thành Nguyễn
@ExLuck99 -
 Pew
Pew
@TheGrandPew -
 Akai 🇻🇳
Akai 🇻🇳
@KMA_Akai -
 PHYR3WALL 🇺🇲
PHYR3WALL 🇺🇲
@phyr3wall -
 gIA Bui
gIA Bui
@yabeow -
 Max Yaremchuk
Max Yaremchuk
@0xw2w
Something went wrong.
Something went wrong.