Mohammed Tanveer
@threatpointer
Foodie, backpacker, newbie blogger & Security Engineer @Microsoft~ Opinions expressed are personal!
You might like
Wonderful meeting @spantzel and diving deep into GPU security — from architecture nuances to AI model execution risks. Exciting times ahead for security! 🔐⚡ #GPU #SecurityResearch #AI #BlueHatAsia @MSFTBlueHat @msftsecresponse

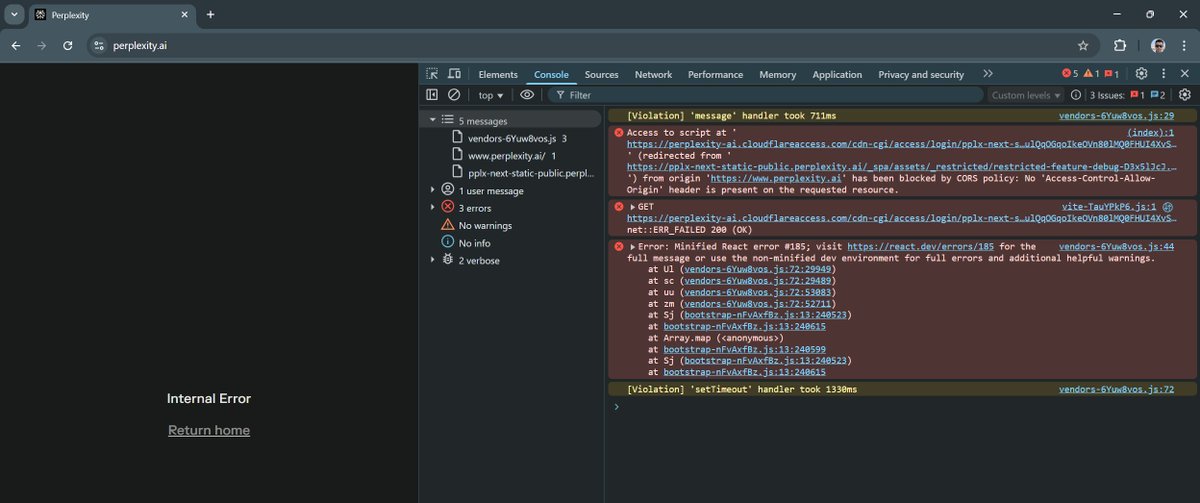
Hey @perplexity_ai seeing two issues on Chrome Access to script at pplx-next-static-public.perplexity.ai redirected to perplexity-ai.cloudflareaccess.com … CORS issue + Minified React error #185 (max depth exceeded) Looks like a restricted asset redirect via Cloudflare Access + retry loop in React.
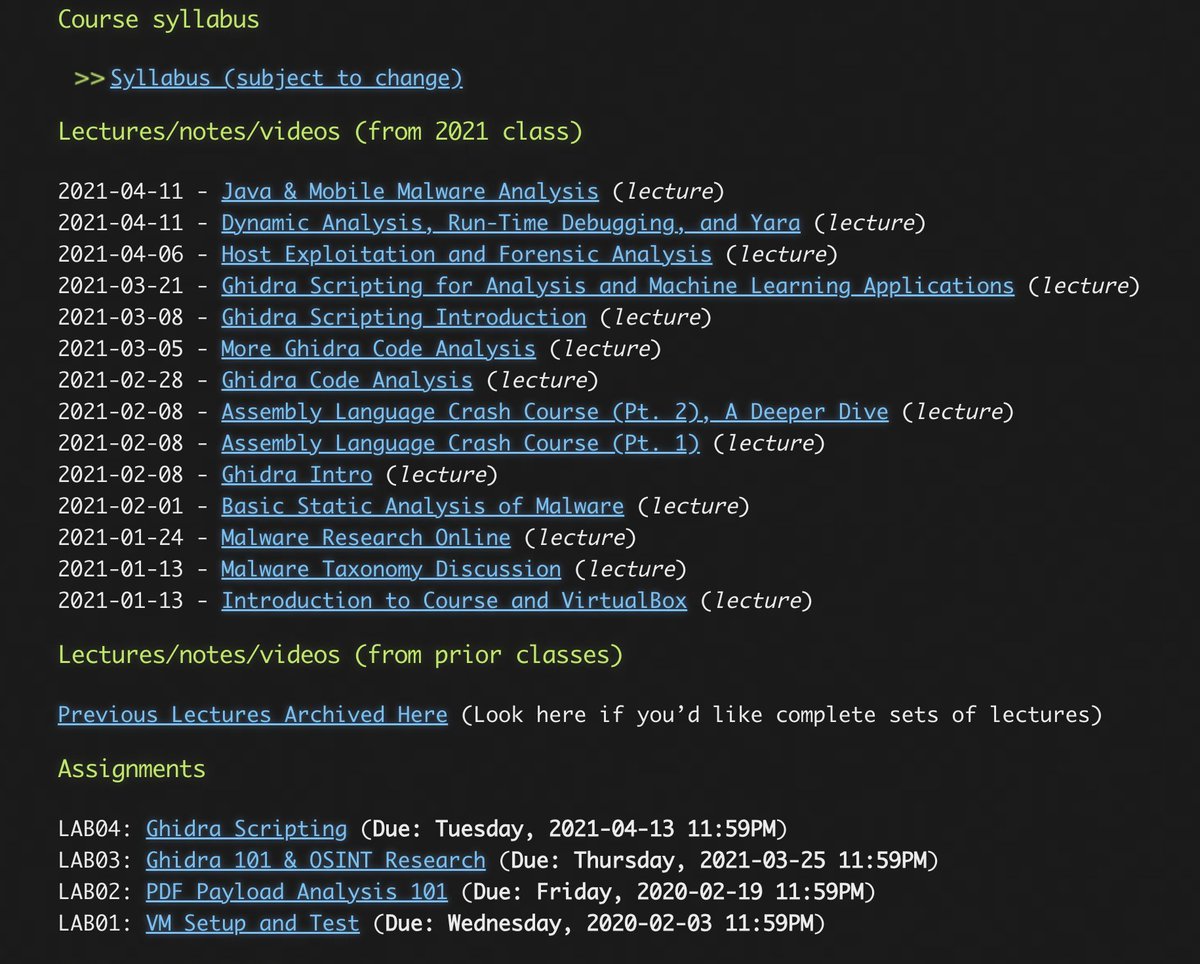
Free Malware Analysis Course, covers malware concepts, malware analysis, and black-box reverse engineering techniques class.malware.re
CVE-2025-55680 cldflt.sys EoP exploited in TyphoonPWN 2025 A direct bypass of @tiraniddo 's bug from 2020 (project-zero.issues.chromium.org/issues/42451188) unpatched for 5 years
I just published Deconstructing CVE-2025–10585: Deep Dive into Chrome’s Latest V8 Zero-Day! medium.com/p/deconstructi… #infosec #browser #zerodayattack
“The largest supply chain compromise in npm, Inc. history just happened, packages with a total of 2 billion weekly downloads just got turned malicious” LinkedIn Post linkedin.com/posts/advocate… More info on hacker news news.ycombinator.com/item?id=451696…


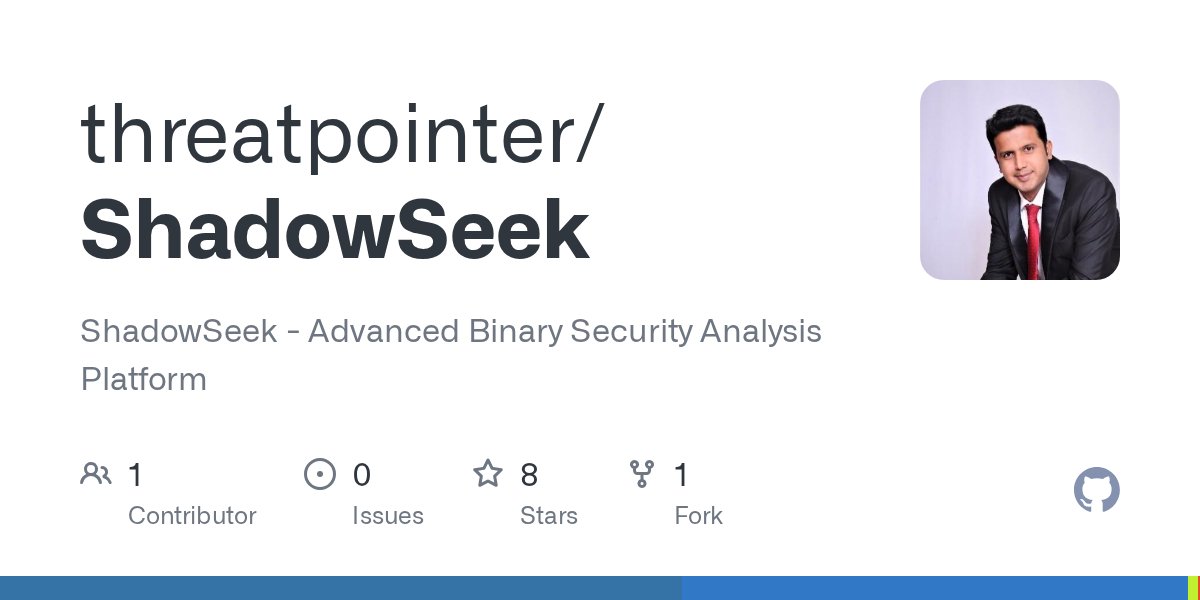
🚀 Just launched ShadowSeek at Black Hat Arsenal 2025! This new AI-powered binary security analysis platform is set to change how we find vulnerabilities in closed-source code. Try here: github.com/threatpointer/… #BinaryAnalysis #ReverseEngineering #LLM #Ghidra #SecurityResearch
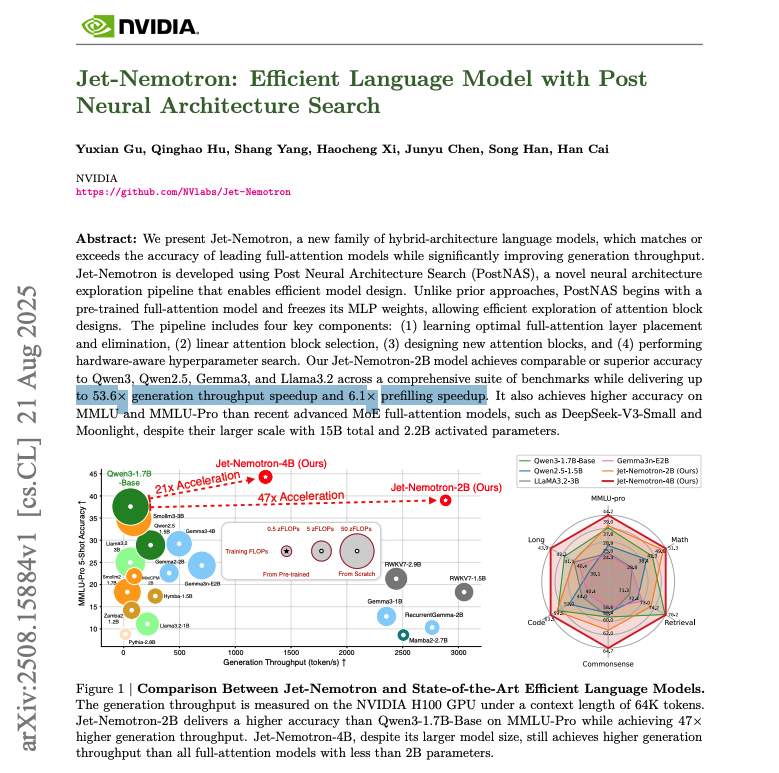
NVIDIA research just made LLMs 53x faster. 🤯 Imagine slashing your AI inference budget by 98%. This breakthrough doesn't require training a new model from scratch; it upgrades your existing ones for hyper-speed while matching or beating SOTA accuracy. Here's how it works:…
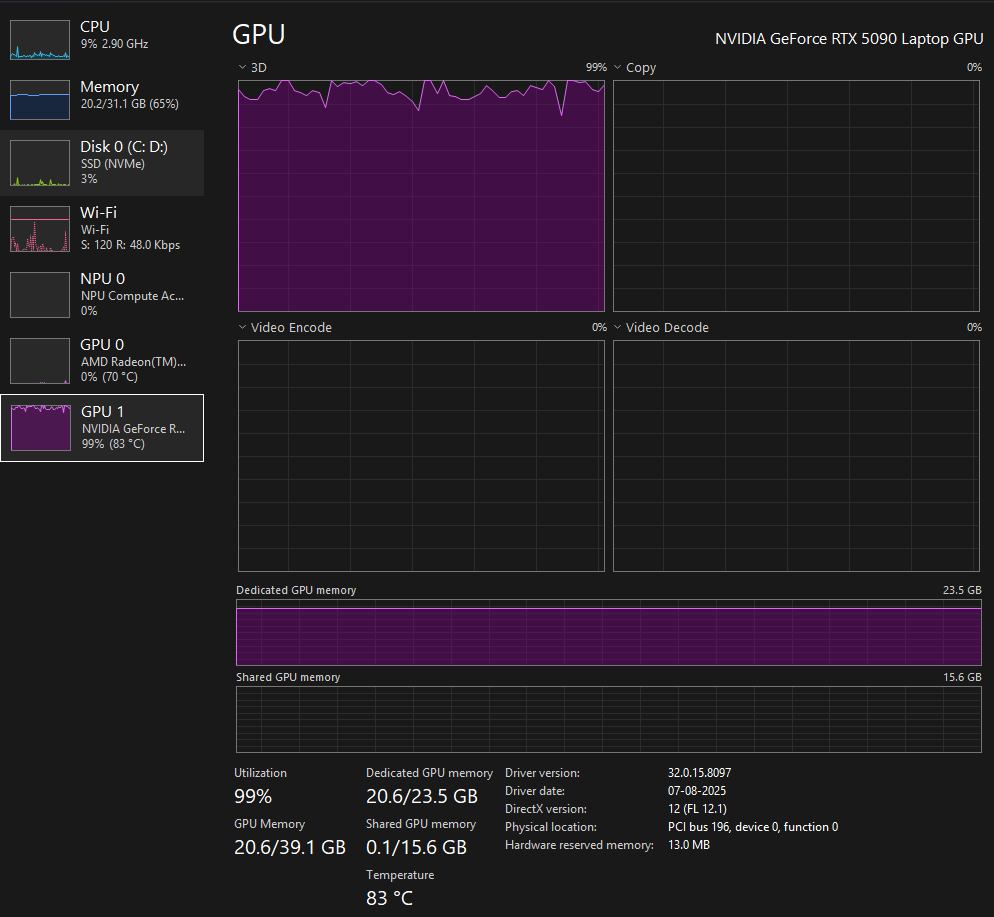
I am sure I need a better cooling system in place for the ML workloads but supper excited to be extacting every ounce of my GPU!
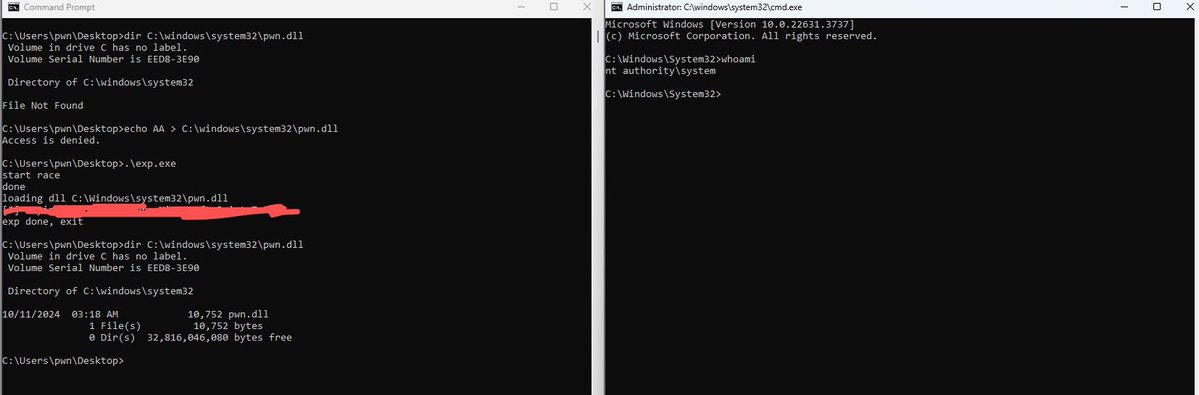
Read “Leveraging .INI Files for Code Execution on Windows: Techniques Used by Malware and Adversaries“ on Medium: medium.com/@threatpointer…
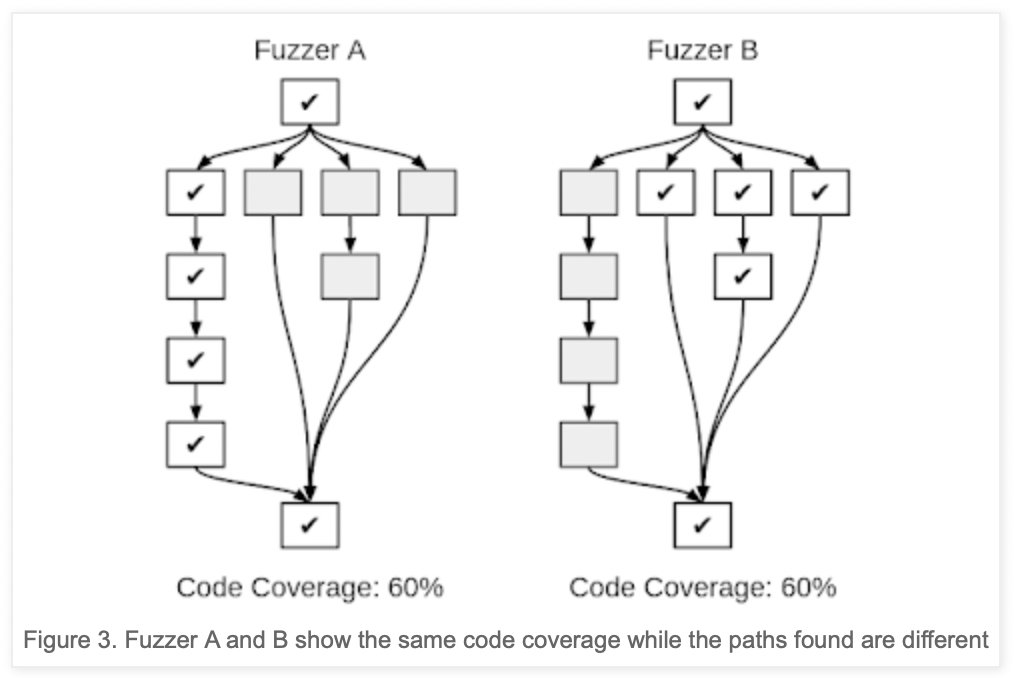
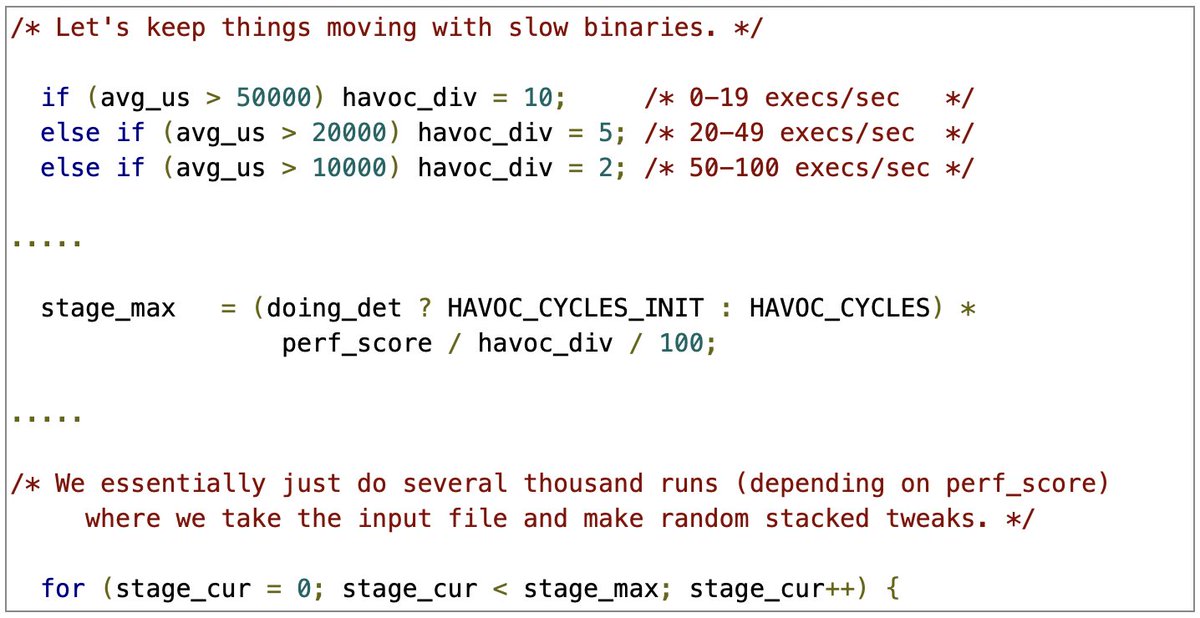
Series on fuzzing open source software using fuzzuf by @RicercaSec ricercasecurity.blogspot.com/2023/07/fuzzin… ricercasecurity.blogspot.com/2023/07/fuzzin… ricercasecurity.blogspot.com/2023/07/fuzzin… ricercasecurity.blogspot.com/2023/07/fuzzin… #fuzzing #cybersecurity


Just published my latest blog on MCP & Security! Check it out and let me know your thoughts. 🚀🔒 medium.com/@threatpointer… #CyberSecurity #MCP #infosec #AI
SignToolEx - code sign things with expired (leaked) certificates without adjusting system clock using Microsoft Detours. github.com/hackerhouse-op…

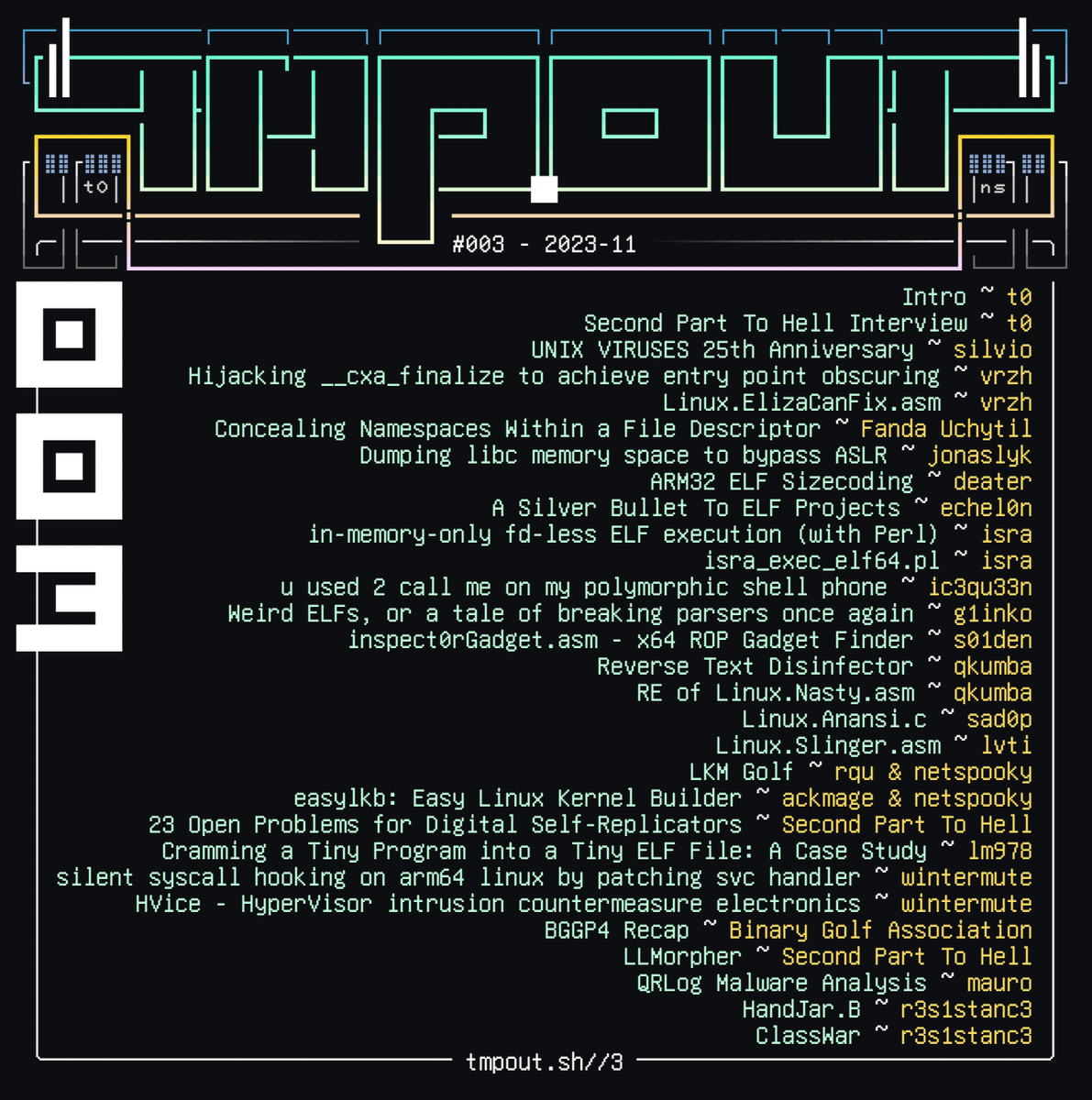
tmpout vol3 - article a day #14 "rain king - silent syscall hooking on arm64 linux via patching svc handler" wintermute shows us an interesting way of hooking syscalls that isn't commonly detected! read here: tmpout.sh/3/23.html

Hey Hackers, Here's the EDR and AV Bypass Content Thread! 🧵 👇 #infosec #Hacking #Pentesting #redteam
So far I've written 559 pages to help the security community: 1. exploitreversing.com/2021/12/03/mal… 2. exploitreversing.com/2022/02/03/mal… 3. exploitreversing.com/2022/05/05/mal… 4. exploitreversing.com/2022/05/12/mal… 5. exploitreversing.com/2022/09/14/mal… 6. exploitreversing.com/2022/11/24/mal… 7. exploitreversing.com/2023/01/05/mal… 8. exploitreversing.com/2023/04/11/exp…
🚨🚨🚨 Whatever you were thinking about CVE-2023-20198 (#Cisco IOS EX) it's 100x worst. We used @TalosSecurity IOC check and found ~30k implants. That's 30k devices infected (routers, switches, VPNs), under the control of threat actors. That's excluding rebooted devices.

Poor man's guide to de-obfuscating VMProtect's : Discovery: youtube.com/watch?v=ZhQUbj…… (1/3) Resolution: youtube.com/watch?v=uxOVbG…… (2/3) Import Recontruction: youtube.com/watch?v=GvWSa6…… (3/3)
United States Trends
- 1. #BaddiesUSA 58.1K posts
- 2. Rams 29K posts
- 3. #LAShortnSweet 19.9K posts
- 4. Scotty 9,575 posts
- 5. Cowboys 99.8K posts
- 6. Chip Kelly 8,479 posts
- 7. Eagles 140K posts
- 8. Stafford 14.8K posts
- 9. Raiders 66.9K posts
- 10. #TROLLBOY 1,933 posts
- 11. #ITWelcomeToDerry 14.9K posts
- 12. Baker 20.7K posts
- 13. Bucs 12.2K posts
- 14. #RHOP 11.7K posts
- 15. Stacey 25.3K posts
- 16. sabrina 58.5K posts
- 17. Vin Diesel 1,167 posts
- 18. Ahna 6,912 posts
- 19. Teddy Bridgewater 1,221 posts
- 20. billie 18.3K posts
Something went wrong.
Something went wrong.