#securityresearch search results
#MobileSecurity #SecurityResearch Bypassing Android System Library Integrity Checks! Learn how to defeat checks that flag your Frida hooks. We dive deep into system libraries memory modification techniques. Don't let integrity checks stop your research. youtu.be/8FZYmsDUj-c

youtube.com
YouTube
Bypass Integrity Checks for Android System Libraries
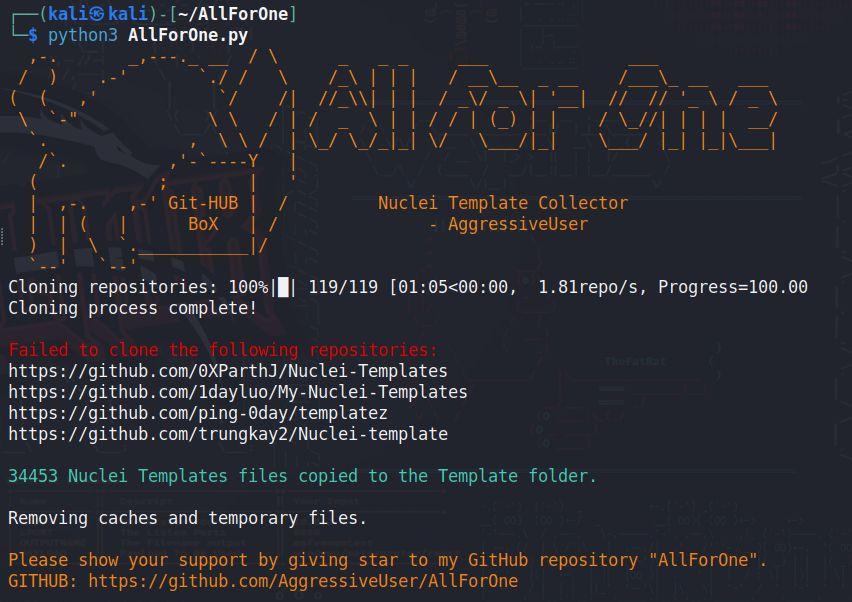
⚡AllForOne allows bug bounty hunters and security researchers to collect all Nuclei YAML templates from various public repositories. 🚨github.com/AggressiveUser… ✅Join Telegram For More - t.me/brutsecurity/1… #BugBounty #SecurityResearch #NucleiTemplates #AllForOne…
Ranked #73 on @Microsoft MVR 2025 leaderboard 🎉 Huge thanks to MSRC & the community — swag level: 💯🚀 #SecurityResearch #MSRC #BugBounty


🌐 Two months ago, we uncovered APT Sidewinder’s use of Netlify and Pages[.]dev hosting platforms to deploy phishing portals that impersonated government and defense agencies throughout South Asia. ⬇️ hunt.io/blog/apt-sidew… #MalwareAnalysis #SecurityResearch
Major breaches consistently expose cloud password manager failures. Local alternatives provide measurable advantages without corporate dependency. See the full video: youtu.be/uMDHPK-xyAA #DataBreach #InfoSec #SecurityResearch
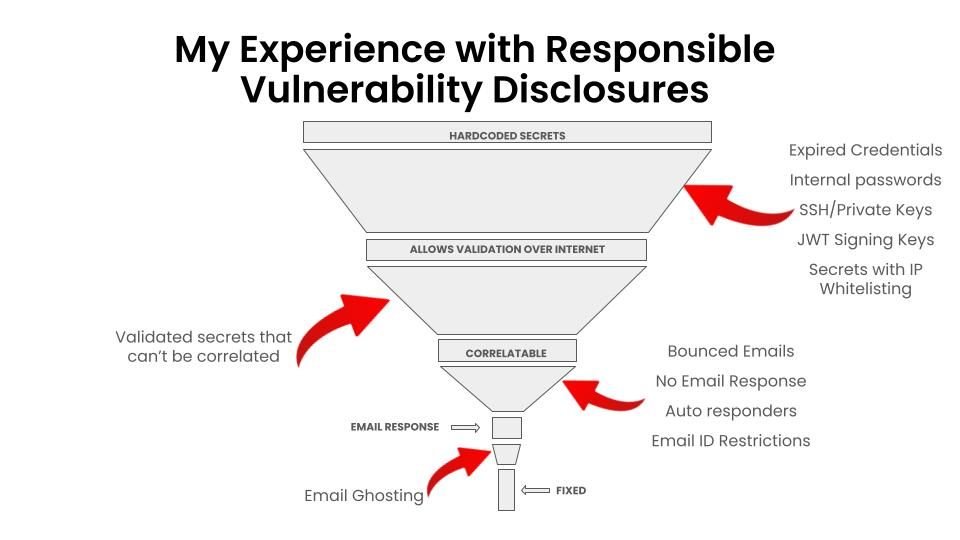
You can hack the planet alone. But 𝐲𝐨𝐮 𝐜𝐚𝐧'𝐭 𝐝𝐞𝐟𝐞𝐧𝐝 𝐭𝐡𝐞 𝐩𝐥𝐚𝐧𝐞𝐭 𝐚𝐥𝐨𝐧𝐞. #VDP #BugBounty #SecurityResearch #Secrets
can-i-take-over-xyz by @EdOverflow Explore subdomain takeover vulnerabilities & learn how to identify potential security issues. A helpful resource for security researchers! #SubdomainTakeover #SecurityResearch #BugBountyPrograms

🚨 The 1st issue of the #ARMADILLO project newsletter is out now. Discover our project’s vision, objectives, innovative solutions, pilot activities & latest news. Read now👉 armadillo-project.eu/ARMADILLO_NEWS… #HorizonEU #SecurityResearch
🔎 Advanced Google Search Techniques for Security Discovery Quick reference for defensive search operators to find publicly exposed assets, leaked configs, and accidental data exposures — use only for authorized research and remediation. #InfoSec #OSINT #SecurityResearch

🔍 Specialized Security Research Operating Systems: Tools for Professional Assessment 🛡️ 💻 🔧 Hashtags:🔖 #SecurityResearch #CyberSecurity #InfoSec #SecurityTools #ProfessionalTesting #NetworkAnalysis #SecurityEngineering #EthicalHacking #SecurityAssessment #DigitalForensics




#HaxStroke #CyberAttack #SecurityResearch Military Networks presents 🗄 CyberRecog 🗄 Search Login and Password only by the URL. the CyberRecog system make fast search on big database to return your data. This all for free! ~HaxStroke cyberecog.militarynetworks.eu
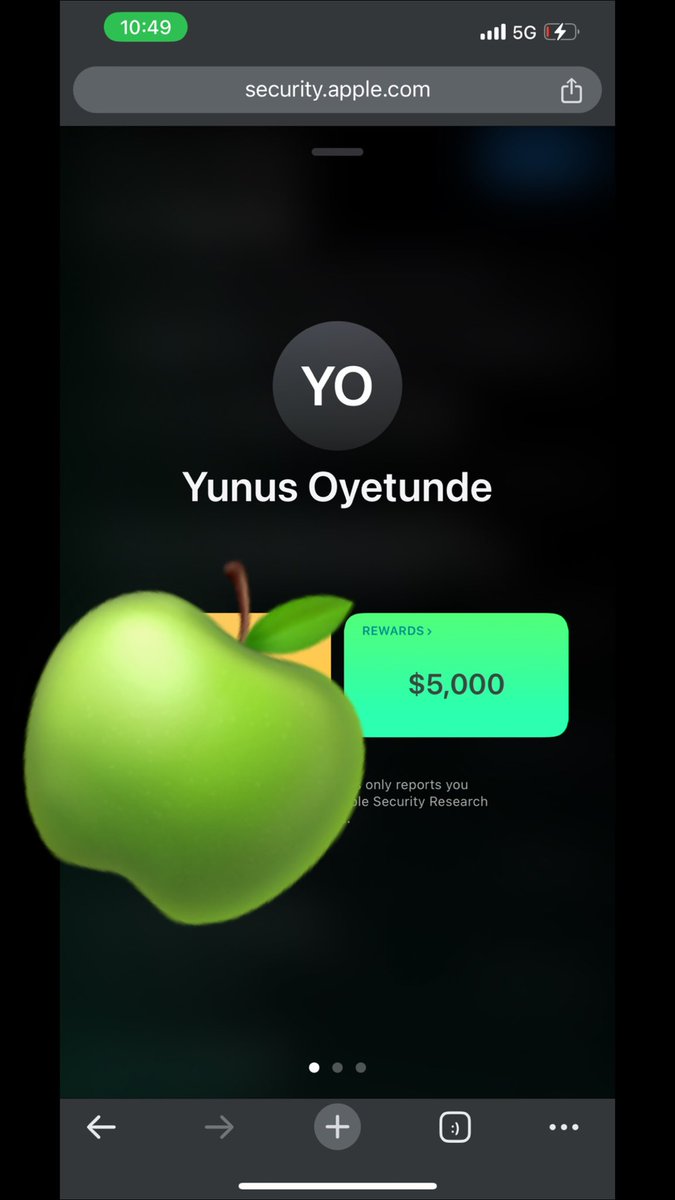
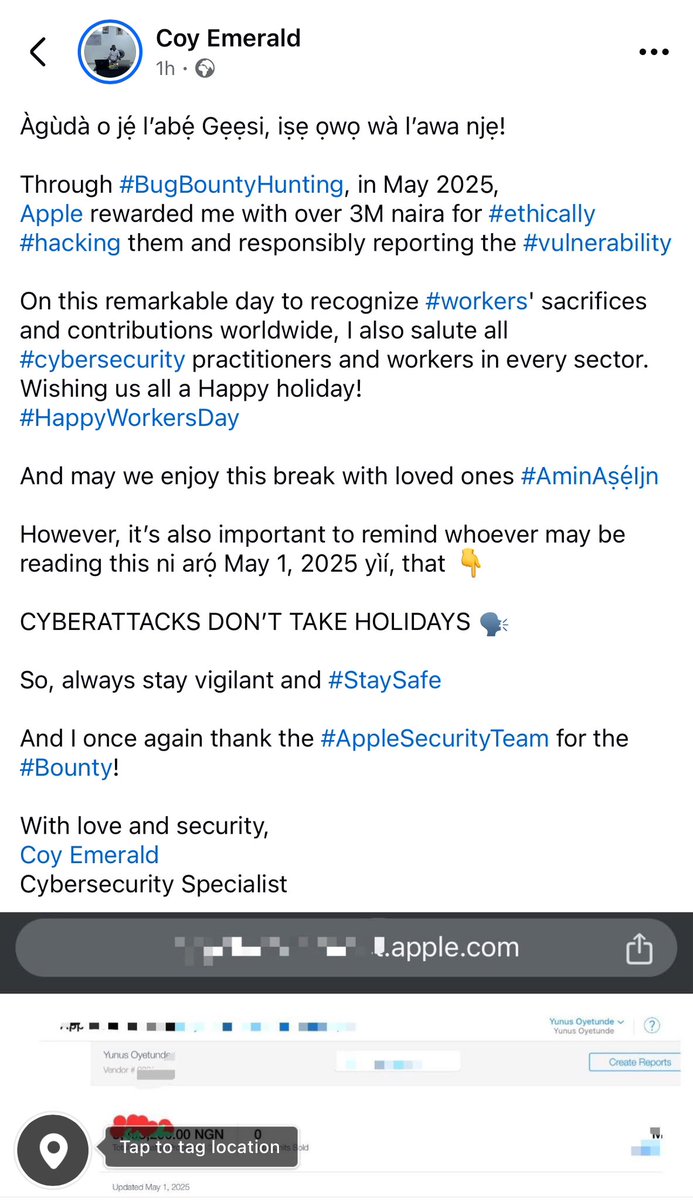
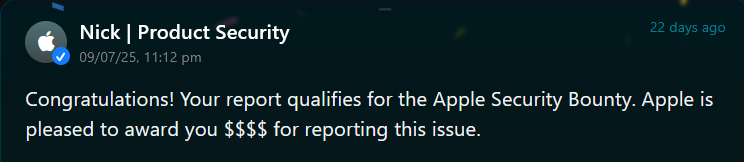
Just randomly checked my Apple Security portal and realized I was awarded a bounty—$$$$ for reporting a security issue! Didn’t even notice the email from 3 weeks ago. #bugbounty #infosec #securityresearch
🚀 Two months ago, we uncovered the operation behind the malware loader known as #TinyLoader, which was found distributing crypto-theft tools across a global infrastructure. hunt.io/blog/tinyloade… #MalwareAnalysis #SecurityResearch
New research on security issues in vibe-coded web apps! Read the blog: okt.to/e58C63 #VibeCoding #AICodeSecurity #SecurityResearch
🙏🔐 Agradecimiento recibido del Banco de España 🇪🇸✨ linkedin.com/posts/manuel-m… #Ciberseguridad #EthicalHacking #SecurityResearch #InfoSec #SeguridadFinanciera #CyberResilience #DigitalTrust

Today, we shift gears at #H16102 with Community Day! From knowledge-sharing to a special panel featuring @salesforce, HackerOne, and a top researcher—this is where relationships grow and innovation thrives. #LiveHackingEvents #SecurityResearch #Cybersecurity




Windows Admin-To-Kernel Elevation of Privilege (CVE-2024-21338) In our latest blog post, @biscoitomesmo details CVE-2024-21338 🔗 Read the full article here: hakaisecurity.io/cve-2024-21338… #WindowsVulnerability #SecurityResearch #PrivilegeEscalation #WindowsSecurity #CyberSecurity



#MobileSecurity #SecurityResearch Bypassing Android System Library Integrity Checks! Learn how to defeat checks that flag your Frida hooks. We dive deep into system libraries memory modification techniques. Don't let integrity checks stop your research. youtu.be/8FZYmsDUj-c

youtube.com
YouTube
Bypass Integrity Checks for Android System Libraries
@grok you understand we SRs live on bugs right? we do bugs for a living, man! 🤣🤣 #web3security #securityresearch #whitehat #bugbounty
🔒🔍 Exciting news from Meta! Introducing WhatsApp Research Proxy to enhance security research and tackle potential threats. Stay ahead of the game! 🚀💻 #WhatsApp #SecurityResearch #BugBounty #StateActors 🛡️🔎 Source: thehackernews.com/2025/11/meta-e…
Navigating crypto taxes for 2025? 📊 Tools are key, but what's the *real* security risk in connecting your wallets? Stay vigilant! #CryptoTax #SecurityResearch 🔒 What's your biggest concern with these tools?
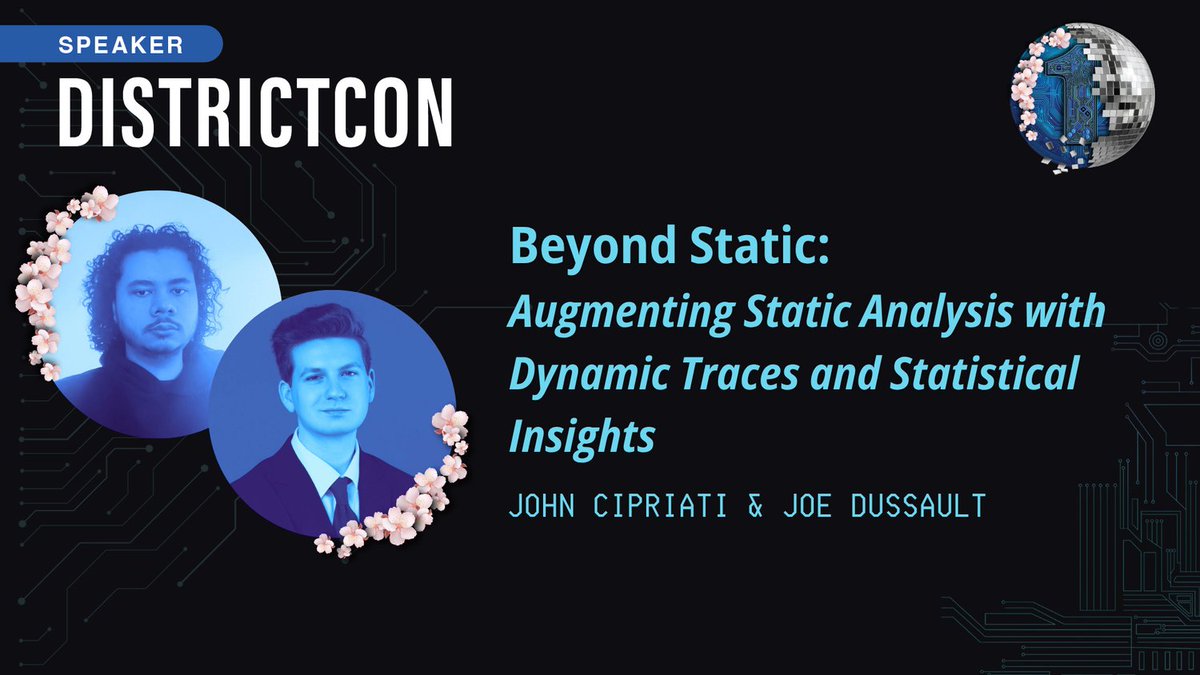
We’re proud to announce that not one – but two – of our team’s submissions were accepted to @DistrictCon! If you’re attending, stop by the Zetier table to meet us, talk #securityresearch, and hear more about the roles we’re actively hiring for as we continue to grow. #InfoSec

This was my first real RE project. I'm sure I made mistakes. If you're experienced in reverse engineering or security research, I'd love your feedback on my methodology. What should I tackle next to improve my skills? #InfoSec #CyberSecurity #SecurityResearch
⚡AllForOne allows bug bounty hunters and security researchers to collect all Nuclei YAML templates from various public repositories. 🚨github.com/AggressiveUser… ✅Join Telegram For More - t.me/brutsecurity/1… #BugBounty #SecurityResearch #NucleiTemplates #AllForOne…

I'll provide additional details soon. Meanwhile, check out real-time DJI DroneID decoding with ANTSDR in this brief video. #securityresearch #sdr #djimini3pro youtube.com/shorts/1xshKGH…

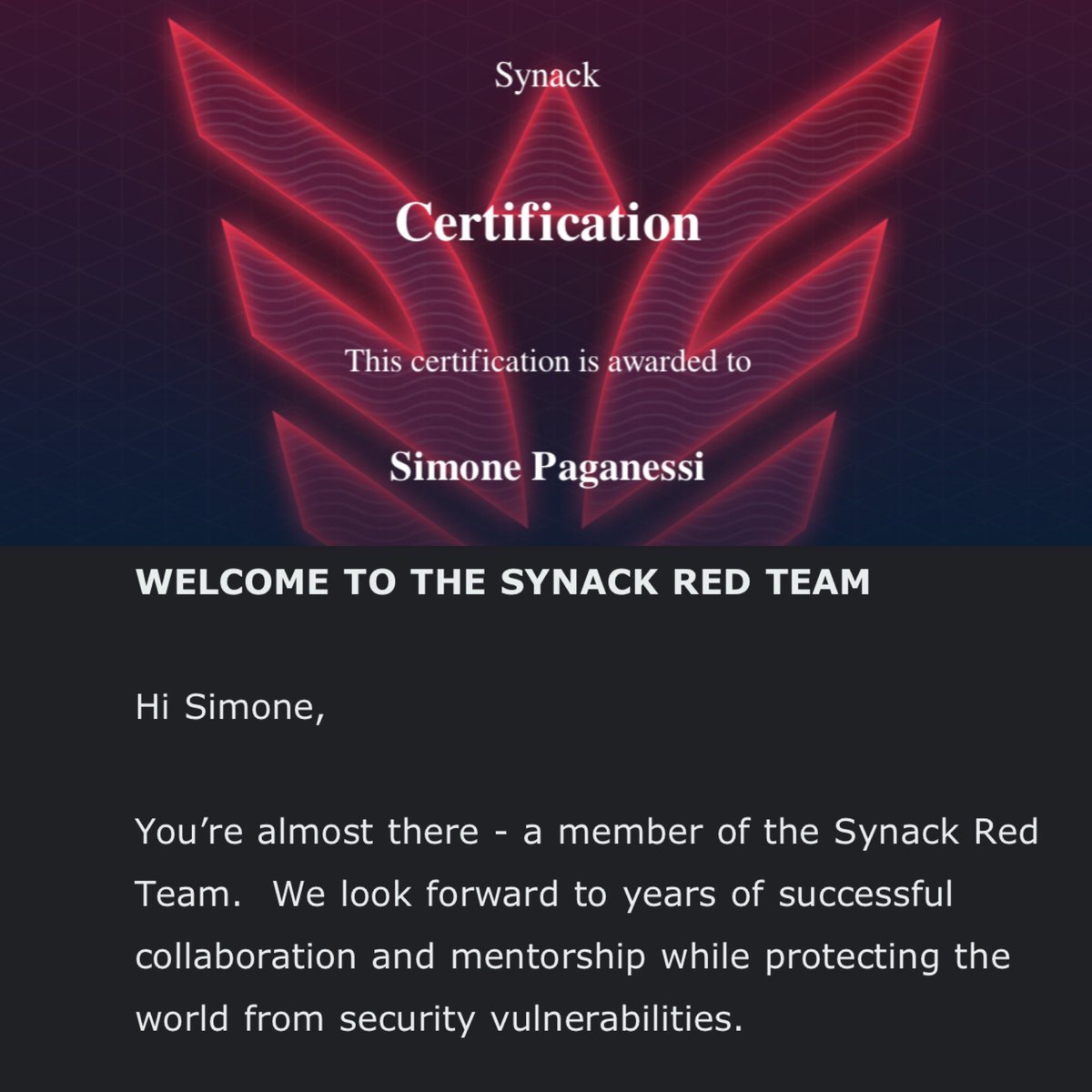
After several months of assessments and interviews I’ve just accomplished one of my all time goal, becoming a Synack Red Team member. Thanks @SynackRedTeam #cybersecurity #bugbounty #securityresearch #synack #redteam
Ranked #73 on @Microsoft MVR 2025 leaderboard 🎉 Huge thanks to MSRC & the community — swag level: 💯🚀 #SecurityResearch #MSRC #BugBounty


Very excited to release PANIX, a highly flexible Linux persistence tool for security research and detection engineering. Test your security posture and learn about Linux persistence. github.com/Aegrah/PANIX #DetectionEngineering #SecurityResearch #Persistence #Linux #Security


📡Time is running out for you to inspire the whole industry with your #securityresearch! ⚠️Call for Papers ends tonight 11:59 PM IST➡️ bit.ly/42FR5b5 #NullconGoa2023 #CFP #Infosec #Conference

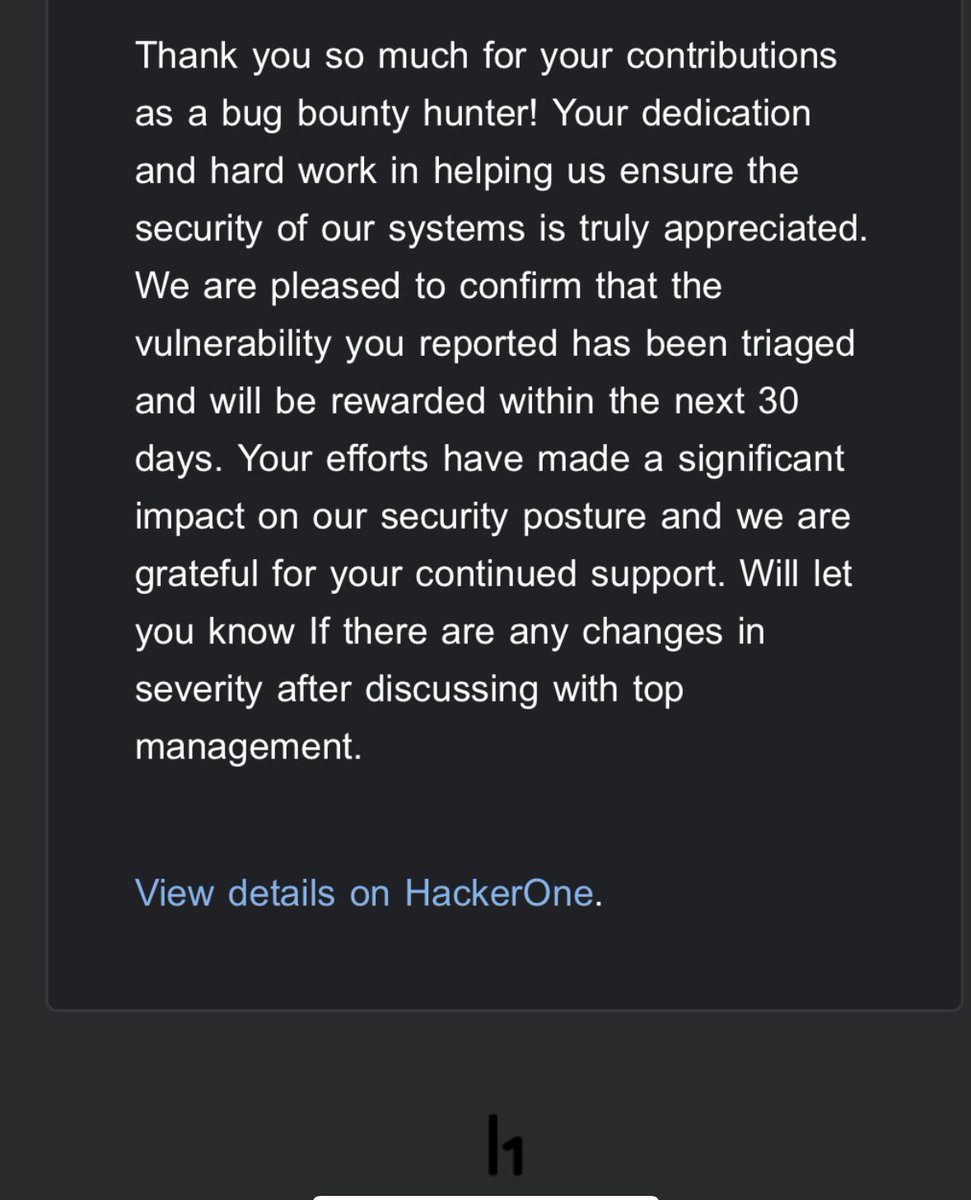
This feedback always helps to improve and is much appreciated. This vulnerability I marked has a big impact on the loss of PII of clinical patients. @Hacker0x01 #bugbounty #cybersecurity #securityresearch
🌐 Shodan Search Techniques: Comprehensive Guide for Security Researchers 🔍 🖥️ 🛡️ #Shodan #SecurityResearch #CyberSecurity #NetworkSecurity #InfoSec #SecurityTesting #EthicalHacking #ITSecurity #ThreatIntelligence #SecurityAssessment

You can hack the planet alone. But 𝐲𝐨𝐮 𝐜𝐚𝐧'𝐭 𝐝𝐞𝐟𝐞𝐧𝐝 𝐭𝐡𝐞 𝐩𝐥𝐚𝐧𝐞𝐭 𝐚𝐥𝐨𝐧𝐞. #VDP #BugBounty #SecurityResearch #Secrets

None to P1 on @Bugcrowd 🍀✨❤️ #BugHunting, #InfoSec, #SecurityResearch, #PenetrationTesting, #VulnerabilityManagement.

can-i-take-over-xyz by @EdOverflow Explore subdomain takeover vulnerabilities & learn how to identify potential security issues. A helpful resource for security researchers! #SubdomainTakeover #SecurityResearch #BugBountyPrograms

🔍 Essential Recon-ng Modules for Professional Security Research 🛡️ 🌐 🧩 #Reconng #SecurityResearch #OSINT #CyberSecurity #InfoSec #ReconTools #SecurityAssessment #ThreatIntelligence #DigitalFootprint #EthicalHacking



🔍 Specialized Security Research Operating Systems: Tools for Professional Assessment 🛡️ 💻 🔧 Hashtags:🔖 #SecurityResearch #CyberSecurity #InfoSec #SecurityTools #ProfessionalTesting #NetworkAnalysis #SecurityEngineering #EthicalHacking #SecurityAssessment #DigitalForensics




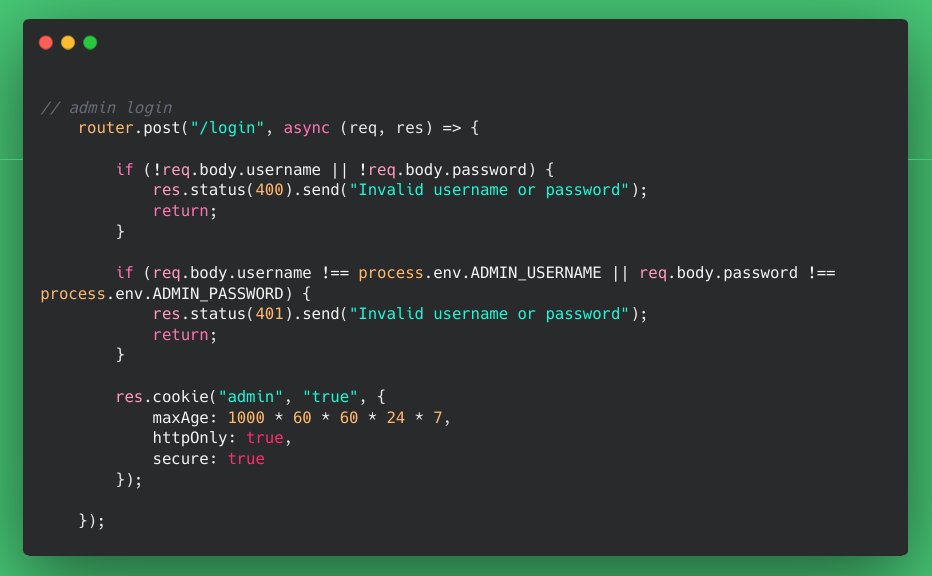
What could possibly go wrong, if this code is actually implemented in a software solution you pentest? Correct answers only. 😌 #SecurityResearch #CyberSecurity
#HaxStroke #CyberAttack #SecurityResearch Military Networks presents 🗄 CyberRecog 🗄 Search Login and Password only by the URL. the CyberRecog system make fast search on big database to return your data. This all for free! ~HaxStroke cyberecog.militarynetworks.eu

Something went wrong.
Something went wrong.
United States Trends
- 1. #StrangerThings5 98.7K posts
- 2. Thanksgiving 612K posts
- 3. Afghan 229K posts
- 4. National Guard 593K posts
- 5. Gonzaga 7,112 posts
- 6. holly 42.8K posts
- 7. #AEWDynamite 20.3K posts
- 8. robin 59.1K posts
- 9. Michigan 74.1K posts
- 10. dustin 85.8K posts
- 11. #Survivor49 2,825 posts
- 12. Rahmanullah Lakanwal 87.3K posts
- 13. Tini 6,548 posts
- 14. Erica 11.3K posts
- 15. #GoAvsGo 1,192 posts
- 16. Kevin Knight 2,500 posts
- 17. Bill Kristol 7,088 posts
- 18. Cease 29.1K posts
- 19. Dusty May N/A
- 20. Doris Burke N/A