#dockerapi نتائج البحث
#Hacking #DockerAPI #UnixSocket #Vulnerability #CyberCrime #CyberAttack #CyberSecurity Docker for Pentester: Abusing Docker API. hackingarticles.in/docker-for-pen…
I'm trying to learn Docker API. I don't understand the difference between SSH and TLS. HELP #docker #dockerapi #programming #SSH #TLS #API #tech #JS #learning #coding #dockerdaemon #socket #daemon #protection #security
Open terminal windows using Go and Docker SDK stackoverflow.com/questions/7215… #dockerapi #terminal #xfce #go #docker

TOR-Based Cryptojacking Attack Expands Through Misconfigured Docker APIs reconbee.com/tor-based-cryp… #TOR #cryptojackingattack #DockerAPI #cyberattacks #CybersecurityNews #CyberSecurityAwareness
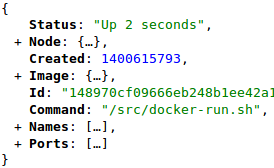
10.🐳 Docker API 📡 The Docker API is like the backstage pass for Docker Engine. It lets apps interact programmatically with Docker. You can use it to manage containers, images, and more, making automation a breeze! 💻🤖 #DockerAPI #Automation
New malware exploits misconfigured Docker APIs to spread and mine Dero cryptocurrency, creating malicious containers that infect other environments through worm-like propagation. Stay alert! 🚨 #DockerAPI #Cryptojacking #Russia ift.tt/e50yVM6
공격 표면에 노출된 도커 컨테이너 인증 없이 컨테이너에 접근 가능한 심각한 보안 이슈blog.criminalip.io/ko/2022/12/30/… #Docker #DockerRegistry #DockerAPI #DockerCompose #DockerSwarm #OSINT
Researchers discovered compromised containers due to an insecure #DockerAPI. The attack led to resource hijacking for #cryptomining and external #NetworkAttacks. #ThreatIntelligence #CyberSecurity securelist.com/dero-miner-inf…
Thanks #DockerBoston for the tshirt and the talk! #dockerapi #ruby!
"The #attacker first checked the availability and version of the #DockerAPI, then proceeds with requests for gRPC/h2c upgrades and #gRPC methods to manipulate Docker functionalities." trendmicro.com/en_us/research…
trendmicro.com
Using gRPC and HTTP/2 for Cryptominer Deployment: An Unconventional Approach
Using gRPC and HTTP/2 for Cryptominer Deployment: An Unconventional Approach
teaching infrastructure to talk #dockerapi #Kubernetes #icp #vic so excited
🚨 Cybercriminals are exploiting #DockerAPI servers to deploy SRBMiner for crypto mining! Protect your systems with strong access controls and monitoring! #Cybersecurity #Cryptojacking
🐳 Did you know? Docker has a robust API, which enables you to automate container management and integrate Docker into your workflow seamlessly. Get hands-free! 🤖🚀🧰 #DockerAPI #Automation
🚨Attackers are exploiting exposed Docker APIs in a fresh campaign. Learn about their latest methods and how you can protect your systems. 🔗 Dive into the details: securitylabs.datadoghq.com/articles/attac… #CyberSecurity #DockerAPI
#dockerapi : docs.docker.com/engine/api/v1.… this tweet is only for myself or for the UX guys from #Docker: this page so hard to navigate I had to bookmark it here 🐬🤣
TOR-Based Cryptojacking Attack Expands Through Misconfigured Docker APIs reconbee.com/tor-based-cryp… #TOR #cryptojackingattack #DockerAPI #cyberattacks #CybersecurityNews #CyberSecurityAwareness
New malware exploits misconfigured Docker APIs to spread and mine Dero cryptocurrency, creating malicious containers that infect other environments through worm-like propagation. Stay alert! 🚨 #DockerAPI #Cryptojacking #Russia ift.tt/e50yVM6
Researchers discovered compromised containers due to an insecure #DockerAPI. The attack led to resource hijacking for #cryptomining and external #NetworkAttacks. #ThreatIntelligence #CyberSecurity securelist.com/dero-miner-inf…
"The #attacker first checked the availability and version of the #DockerAPI, then proceeds with requests for gRPC/h2c upgrades and #gRPC methods to manipulate Docker functionalities." trendmicro.com/en_us/research…
trendmicro.com
Using gRPC and HTTP/2 for Cryptominer Deployment: An Unconventional Approach
Using gRPC and HTTP/2 for Cryptominer Deployment: An Unconventional Approach
🚨 Cybercriminals are exploiting #DockerAPI servers to deploy SRBMiner for crypto mining! Protect your systems with strong access controls and monitoring! #Cybersecurity #Cryptojacking
Cybercriminals Exploiting Docker API Servers for SRBMiner Crypto Mining Attacks reconbee.com/cybercriminals… #cybercriminals #DockerAPI #Docker #SRBMiner #cryptominingattacks #cryptomining #CryptoNews #cryptomarket
New Malware Targets Exposed Docker APIs for Cryptocurrency Mining reconbee.com/new-malware-ta… #malware #DockerAPI #cryptocurrencymining #cryptocurrency #cybersecurity #cybersecuritynews #cyberattack
🚨Attackers are exploiting exposed Docker APIs in a fresh campaign. Learn about their latest methods and how you can protect your systems. 🔗 Dive into the details: securitylabs.datadoghq.com/articles/attac… #CyberSecurity #DockerAPI
🐳 Did you know? Docker has a robust API, which enables you to automate container management and integrate Docker into your workflow seamlessly. Get hands-free! 🤖🚀🧰 #DockerAPI #Automation
10.🐳 Docker API 📡 The Docker API is like the backstage pass for Docker Engine. It lets apps interact programmatically with Docker. You can use it to manage containers, images, and more, making automation a breeze! 💻🤖 #DockerAPI #Automation
Docker container exposed to the attack surface! Serious security issue which malicious actors can access without authentication blog.criminalip.io/2022/12/30/doc… #Docker #DockerRegistry #DockerAPI #DockerCompose #DockerSwarm #OSINT
攻撃対象領域に漏えいされたドッカ―コンテナ、 認証なしでコンテナにアクセスできる深刻なセキュリティ問題 blog.criminalip.io/ja/2022/12/30/… #Docker #DockerRegistry #DockerAPI #DockerCompose #DockerSwarm #OSINT
공격 표면에 노출된 도커 컨테이너 인증 없이 컨테이너에 접근 가능한 심각한 보안 이슈blog.criminalip.io/ko/2022/12/30/… #Docker #DockerRegistry #DockerAPI #DockerCompose #DockerSwarm #OSINT
Open terminal windows using Go and Docker SDK stackoverflow.com/questions/7215… #dockerapi #terminal #xfce #go #docker

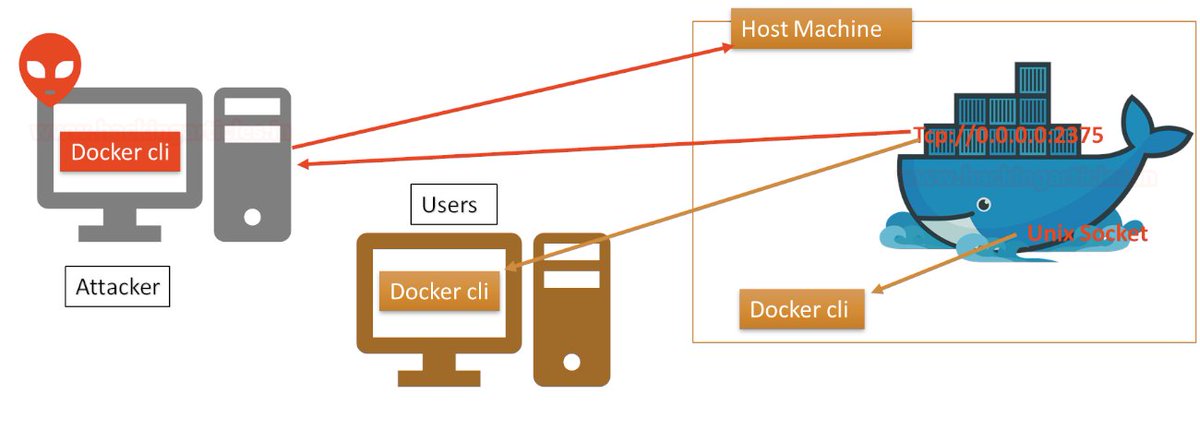
The Danger of Having an Exposed Docker API Port #dockerapi 🎬 youtu.be/6wGDS17YQo0
TeamTNT Botnet Updated to Steal Docker and AWS Credentials techdator.net/teamtnt-botnet… Hacking News #AWS #DockerAPI #LoginCredentials #TeamTNT
Open terminal windows using Go and Docker SDK stackoverflow.com/questions/7215… #dockerapi #terminal #xfce #go #docker

#Hacking #DockerAPI #UnixSocket #Vulnerability #CyberCrime #CyberAttack #CyberSecurity Docker for Pentester: Abusing Docker API. hackingarticles.in/docker-for-pen…

Something went wrong.
Something went wrong.
United States Trends
- 1. Wentz 14.3K posts
- 2. Vikings 40.6K posts
- 3. Chargers 46.3K posts
- 4. Pacers 17.9K posts
- 5. Herbert 14.1K posts
- 6. $UNI 3,136 posts
- 7. #Skol 4,549 posts
- 8. Brosmer 2,307 posts
- 9. Shai 14.3K posts
- 10. Quentin Johnston 1,542 posts
- 11. Chet 12.6K posts
- 12. Ajay Mitchell 1,227 posts
- 13. #TNFonPrime 2,039 posts
- 14. Mathurin 3,756 posts
- 15. Siakam 4,260 posts
- 16. #911onABC 13.1K posts
- 17. #criticalrolespoilers 2,692 posts
- 18. Double OT 12.7K posts
- 19. Vidal 8,966 posts
- 20. Justin Jefferson 3,277 posts