#networkattacks risultati di ricerca
#CyberSecurity #NetworkAttacks! #BigData #Analytics #DataScience #AI #MachineLearning #IoT #IIoT #PyTorch #Python #RStats #TensorFlow #Java #JavaScript #ReactJS #GoLang #CloudComputing #Serverless #DataScientist #Linux #Programming #Coding #100DaysofCode geni.us/CyberSecurityN…
ARP SPOOFING ATTACKS! | IPCisco . Please Retweet.:) . #network #networksecurity #networkattacks #cisco

🚨 Understanding #NetworkAttacks is crucial for cybersecurity! Here are some common types: DDoS- Overwhelming a network with traffic. Man-in-the-Middle - Intercepting communication between two parties. Stay informed & protect your network! 🔒💻 #CyberSecurity #InfoSec
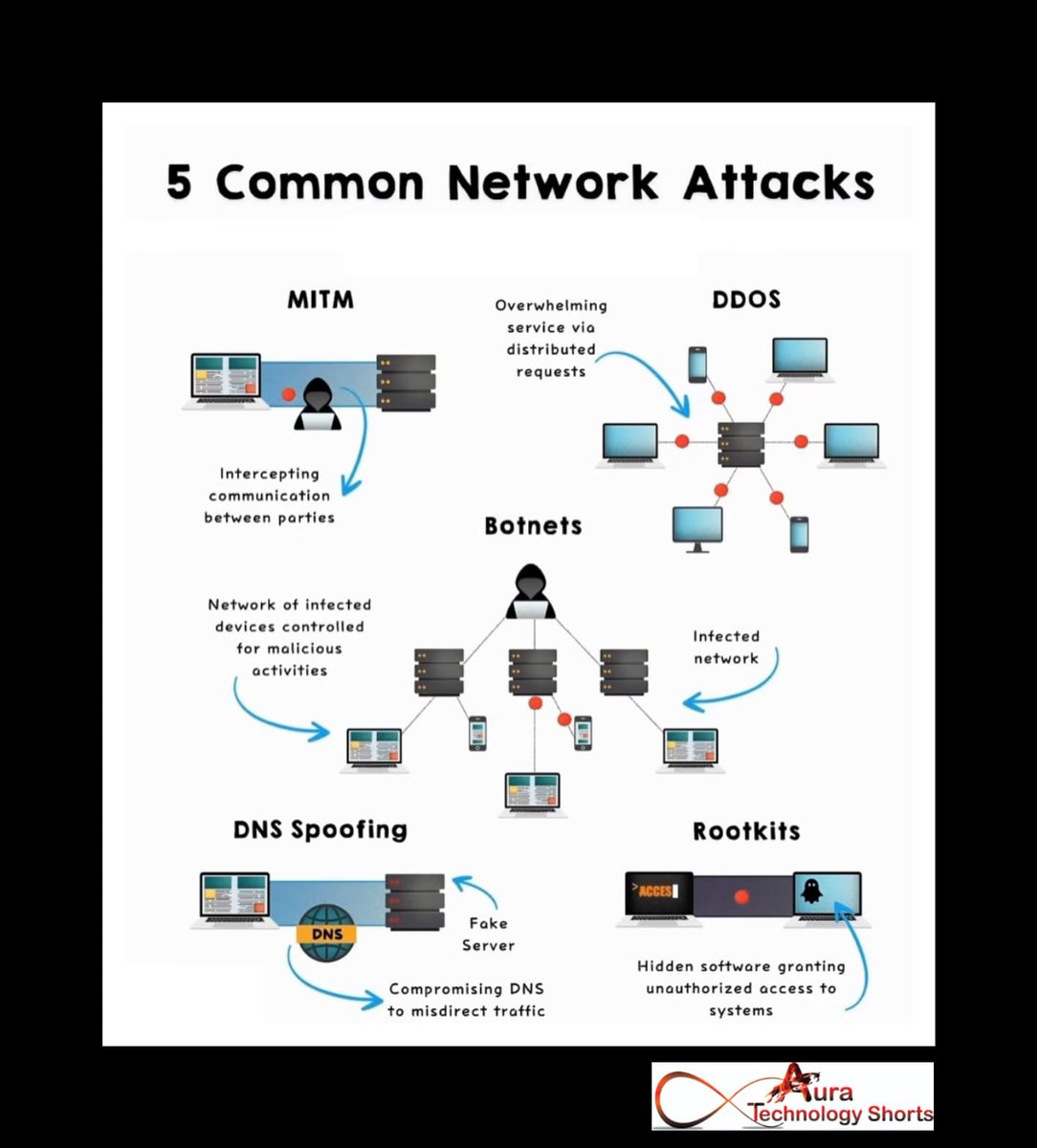
5 common network attacks ............... #NetworkSecurity #CyberSecurity #NetworkAttacks #CyberThreats #Hacking #DataBreach #Phishing #Malware #Ransomware #DenialOfService #ManInTheMiddle #SQLInjection #SocialEngineering #ThreatDefense #WebSecurity #ITSecurity #SecurityAwareness
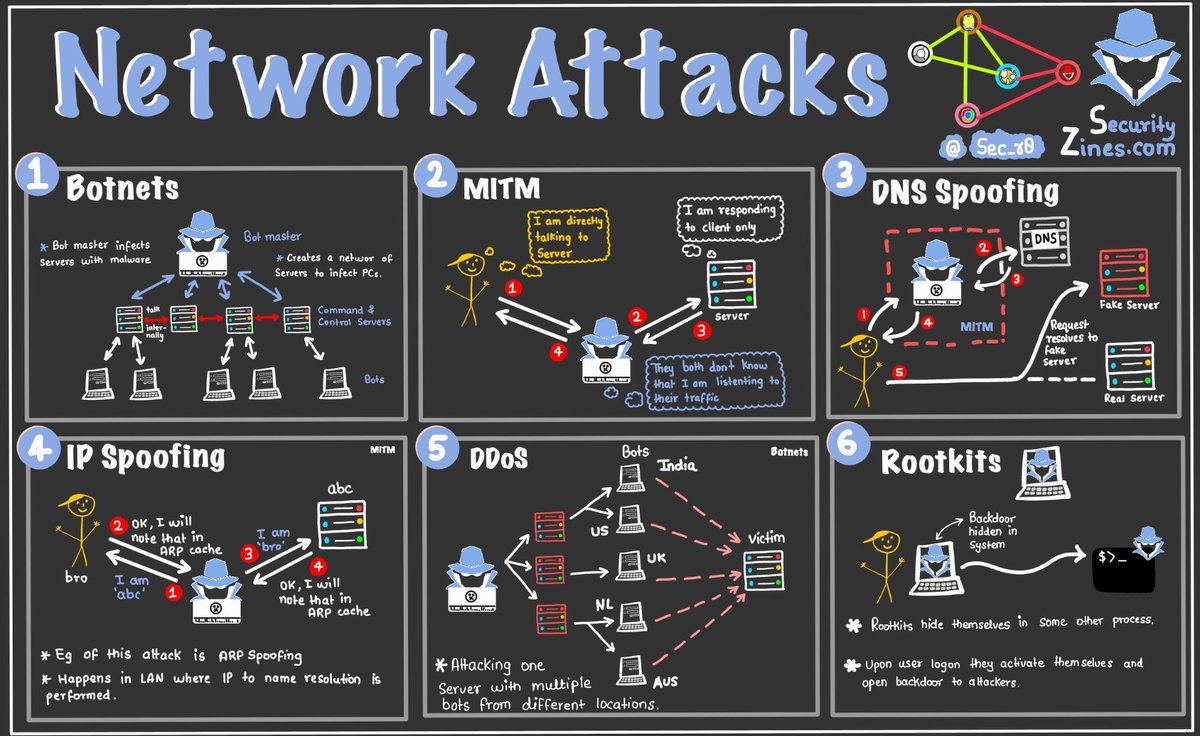
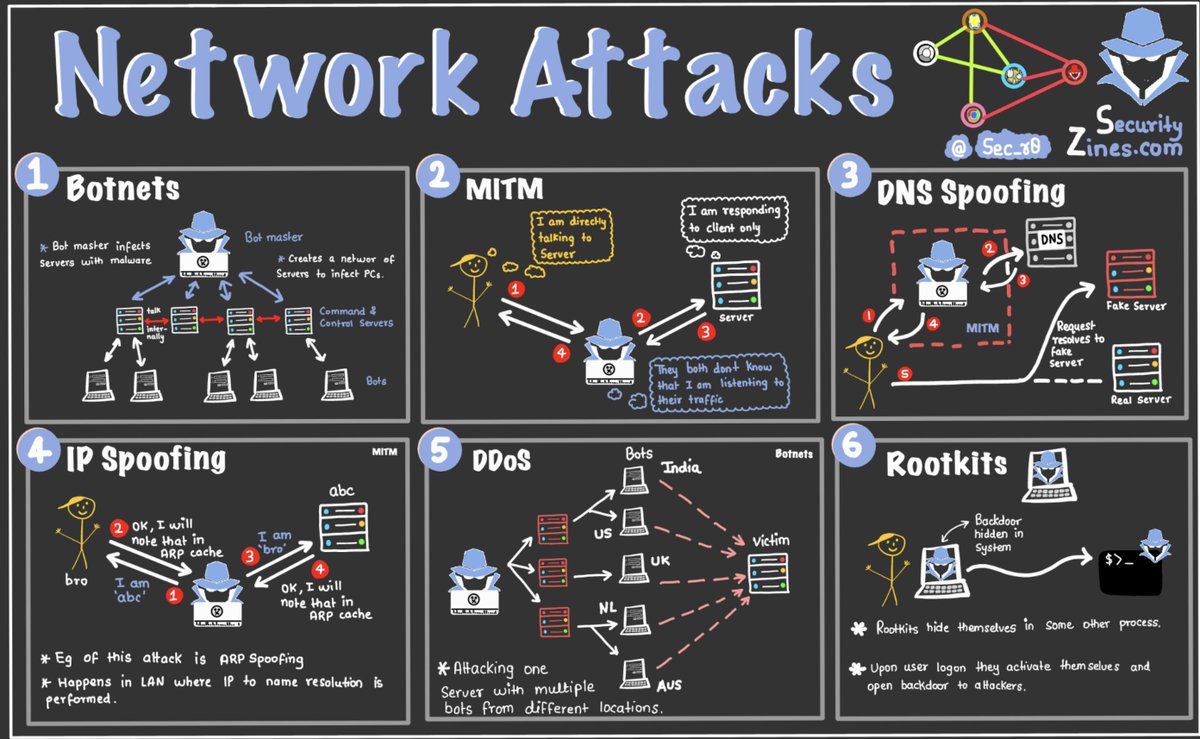
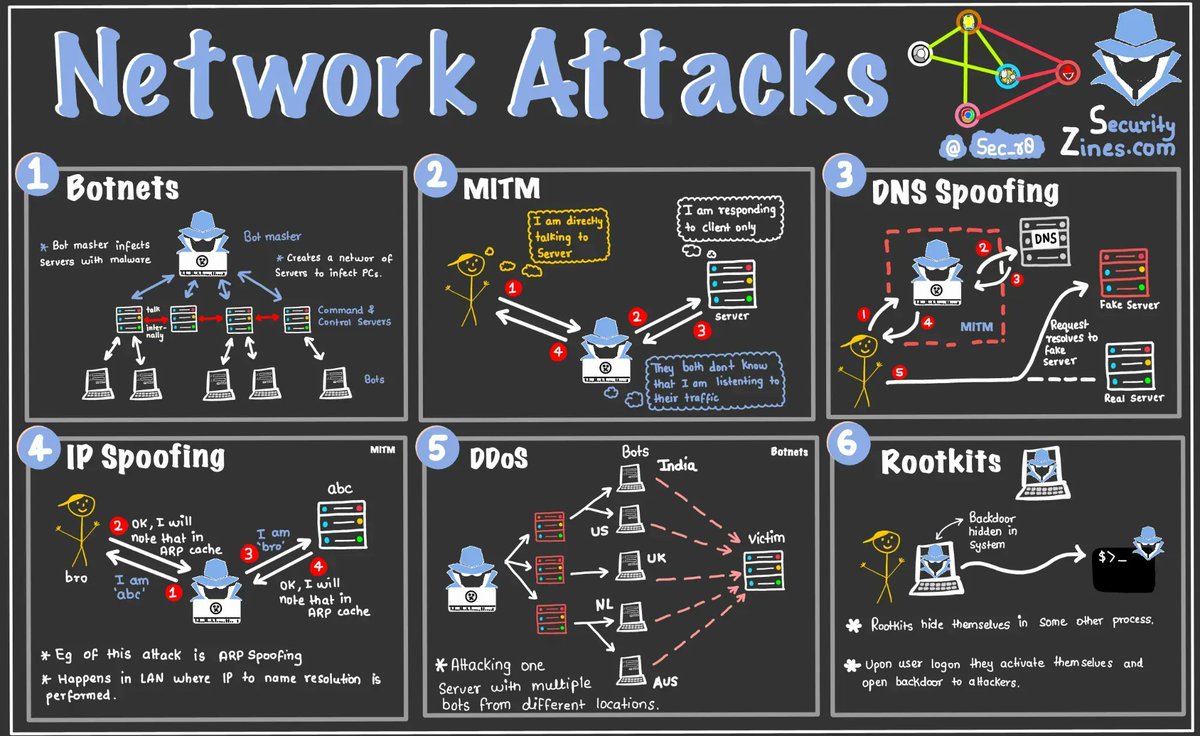
#networkattacks come in many methods and via different methodologies. It is crucial that every organization properly secures their #networks, educates their #endusers, and performs proper #networkmonitoring to ensure #threatactors are not accessing your #data.

Completed section 10 and closing in on section 11 of the #CompTIA Pentest+ exam. 📚 Network attacks had me hooked, especially the thrilling VLAN hacking and other mind-boggling techniques 💪 #PentestPlus #NetworkAttacks #Cybersecurity #infosec

Understanding various cyber attacks is crucial for cybersecurity professionals, as it enables them to effectively mitigate and defend against potential threats. #cybersecurity #networkattacks




เคยสงสัยไหมว่าแฮกเกอร์โจมตีระบบยังไง 🤔 มาเจาะลึกโลกของการโจมตีเครือข่าย (Network Attacks) กันเถอะ รู้ไว้ ป้องกันได้✨💙 #NetworkAttacks #CyberAttack #Cybersecurity #NetworkSecurity #การโจมตีเครือข่าย #เทคโนโลยี #ความรู้ #KIRZ #KIRZInternetThailand #ความรู้ไอที #โพยความรู้

8/ Teardrop Attack 💧 Teardrop Attack 💔 Maliciously fragmented packets confuse systems, causing crashes. Keep systems updated to fix vulnerabilities! 🛡️ #CyberSecurity #Infosec #NetworkAttacks

5/ IP Spoofing 📡 IP Spoofing Explained 🌐 Attackers disguise their IP address as a trusted source to bypass firewalls or impersonate systems. Verify packet origins to mitigate this! 🔍🔒 #Infosec #CyberSecurity #NetworkAttacks

Today's understanding #networkattacks is crucial for safeguarding your online presence. So, we've decided to showcase some of the common attacks 🌐 But these are just the tip of the iceberg. What other types of network attacks have you come across? Share in the comments! 💬




More Information Security News: What is Zero Trust Model ☁️🔐 | #cybersecurity #networkattacks #informationsecurity #fyp youtube.com/watch?v=lKdnoL…

More Information Security News: What is NLP in ai security | #networkattacks #cybersecurity #ai #informationsecurity youtube.com/watch?v=jgFD2U…

IDS versus IPS! #IntrusionPrevention #IntrusionDetection #NetworkAttacks #threats #SIEM #DLP #DataSecurity #security #dataprotection cc: @SpirosMargaris @FrankJSchwab @BarbaraLampl @BarkowConsult

NETWORK ATTACKS. Man-in-The-Middle ATTACKS #NetworkAttacks #Cybersecurity #middleman #foreducationalpurposesonly
#highlycitedpaper Intelligent Techniques for Detecting Network Attacks: Review and Research Directions mdpi.com/1424-8220/21/2… #NetworkSecurity #NetworkAttacks

Researchers discovered compromised containers due to an insecure #DockerAPI. The attack led to resource hijacking for #cryptomining and external #NetworkAttacks. #ThreatIntelligence #CyberSecurity securelist.com/dero-miner-inf…
5 common network attacks ............... #NetworkSecurity #CyberSecurity #NetworkAttacks #CyberThreats #Hacking #DataBreach #Phishing #Malware #Ransomware #DenialOfService #ManInTheMiddle #SQLInjection #SocialEngineering #ThreatDefense #WebSecurity #ITSecurity #SecurityAwareness

What type of attacks will we see in 2025? From #bootkits to #networkattacks to #firmwaresecurity vulnerabilities, Chase Snyder & Paul Asadoorian review #cybersecurity happenings in 2024, and what to watch for as the year unfolds. On-demand #webinar here: hubs.ly/Q034VdHP0
info.eclypsium.com
2025 Threat Landscape Trends to Watch - OnDemand
2025 Threat Landscape Trends to Watch - OnDemand
What type of attacks will we see in 2025? From #bootkits to #networkattacks to #firmwaresecurity vulnerabilities, Chase Snyder & Paul Asadoorian review #cybersecurity happenings in 2024, and what to watch for as the year unfolds. On-demand #webinar here: hubs.ly/Q034VJmq0
info.eclypsium.com
2025 Threat Landscape Trends to Watch - OnDemand
2025 Threat Landscape Trends to Watch - OnDemand
Read about our honeypot experiment revealing the risks of exposing a public IP address to the internet in this article 👉 buff.ly/42wF8r9 Contact Spitfire on 020 7501 3333 for advice on how to secure your network 🔒 #networksecurity #cybersecurity #networkattacks
Read about our honeypot experiment revealing the risks of exposing a public IP address to the internet in this article 👉 buff.ly/42wF8r9 Contact Spitfire on 020 7501 3333 for advice on how to secure your network 🔒 #networksecurity #cybersecurity #networkattacks
#networkattacks come in many methods and via different methodologies. It is crucial that every organization properly secures their #networks, educates their #endusers, and performs proper #networkmonitoring to ensure #threatactors are not accessing your #data.

เคยสงสัยไหมว่าแฮกเกอร์โจมตีระบบยังไง 🤔 มาเจาะลึกโลกของการโจมตีเครือข่าย (Network Attacks) กันเถอะ รู้ไว้ ป้องกันได้✨💙 #NetworkAttacks #CyberAttack #Cybersecurity #NetworkSecurity #การโจมตีเครือข่าย #เทคโนโลยี #ความรู้ #KIRZ #KIRZInternetThailand #ความรู้ไอที #โพยความรู้

8/ Teardrop Attack 💧 Teardrop Attack 💔 Maliciously fragmented packets confuse systems, causing crashes. Keep systems updated to fix vulnerabilities! 🛡️ #CyberSecurity #Infosec #NetworkAttacks

5/ IP Spoofing 📡 IP Spoofing Explained 🌐 Attackers disguise their IP address as a trusted source to bypass firewalls or impersonate systems. Verify packet origins to mitigate this! 🔍🔒 #Infosec #CyberSecurity #NetworkAttacks

Effective strategies to strengthen your API Security bit.ly/4gQhyu1 #APISecurity #networkattacks #DevOps #cyberattacks #Cybercriminals #DevSecOps #TechUnity

🚨 Understanding #NetworkAttacks is crucial for cybersecurity! Here are some common types: DDoS- Overwhelming a network with traffic. Man-in-the-Middle - Intercepting communication between two parties. Stay informed & protect your network! 🔒💻 #CyberSecurity #InfoSec
#CyberSecurity #NetworkAttacks! #BigData #Analytics #DataScience #AI #MachineLearning #IoT #IIoT #PyTorch #Python #RStats #TensorFlow #Java #JavaScript #ReactJS #GoLang #CloudComputing #Serverless #DataScientist #Linux #Programming #Coding #100DaysofCode geni.us/CyberSecurityN…

#CyberSecurity #NetworkAttacks! #BigData #Analytics #DataScience #AI #MachineLearning #IoT #IIoT #PyTorch #Python #RStats #TensorFlow #Java #JavaScript #ReactJS #GoLang #CloudComputing #Serverless #DataScientist #Linux #Programming #Coding #100DaysofCode geni.us/CyberSecurityN…

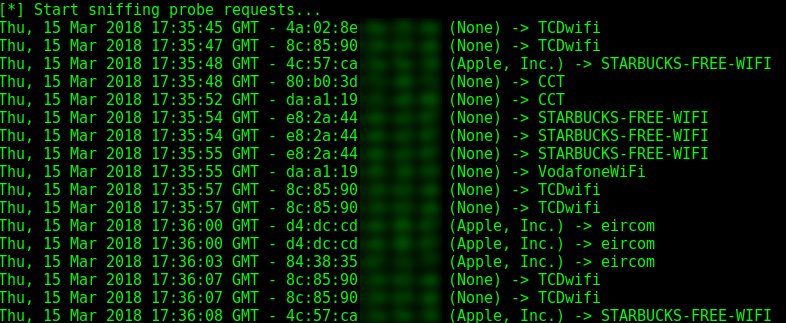
Probequest - Toolkit For Playing With Wi-Fi Probe Requests j.mp/2JWT2rz #Linux #Monitoring #NetworkAttacks #Probequest #Python
ARP SPOOFING ATTACKS! | IPCisco . Please Retweet.:) . #network #networksecurity #networkattacks #cisco

通常情况下攻击者会利用代理或其它方法模糊位置,但研究人员观察到攻击者多次没有使用代理直接访问了受害者机器。攻击者使用的 IP 段被发现是 221.216.0.0/13,属于北京西城区的联通网络 #China #networkattacks【一系列错误曝光了中国情报机构操纵的网络攻击】中文详细:iyouport.wixsite.com/iyouport/blog/…

Protect your business from #ITdowntime, #dataleakages, #networkattacks and other possible danger! IT #securityplan should cover your entire system based on the solutions you use. One plan does not fit all! t2m.io/13ApcEyj #ITprotection #ITsecurity #dataprotection
IDS versus IPS! #IntrusionPrevention #IntrusionDetection #NetworkAttacks #threats #SIEM #DLP #DataSecurity #security #dataprotection cc: @SpirosMargaris @FrankJSchwab @BarbaraLampl @BarkowConsult

Smominru Botnet Affecting Over 4,000 Windows Systems Every Day ehackingnews.com/2019/10/smomin… #Botnet #malware #NetworkAttacks

Explore various types of network attacks and learn about the ways to prevent them. Read the blog: bit.ly/3CrAiLV #NetworkAttacks #CyberSecurityTraining #NetComLearning #LifeLonglearning #Cybersecurity

Probequest - Toolkit For Playing With Wi-Fi Probe Requests j.mp/2JWT2rz #Linux #Monitoring #NetworkAttacks #Probequest #Python

Introduction of C++ Sockets simpliv.com/networkingands… #NetworkAttacks #cyberattacks #BeCybersafe #networksecurity #cybersecurity #cybercrime #Network #networking #security #infosecurity #DDoS #Malware #Internet #privacy #ITSecurity #cybersec #infosec #technology #tech

Parsing TCP Socket Data with C/C++ simpliv.com/networkingands… #NetworkAttacks #cyberattacks #BeCybersafe #networksecurity #cybersecurity #cybercrime #Network #networking #security #infosecurity #DDoS #Malware #Internet #privacy #ITSecurity #cybersec #infosec #technology #tech

➡️Types of DNS HIJACKING Attacks⬅️ ✅Local DNS Hijacking ✅OnPath DNS Hijacking ✅Router DNS Hijacking ✅Rogue Server DNS Hijacking ✅DNS Spoofing #DNSHijacking #DNS #NetworkAttacks #NetworkSecurity #Cybersecurity #Technology #Tech #SecuriumSolutions

In the digital era, businesses must be hyperaware of potential #NetworkAttacks. Learn about #NetworkSecurity best practices in our #Webinar with Renan Huguenin on June 23. Register now: bit.ly/3LRTINO #Cybersecurity #CyberThreats #InformationSecurity #ECCouncil

RT KitPloit "Probequest - Toolkit For Playing With Wi-Fi Probe Requests j.mp/2JWT2rz #Linux #Monitoring #NetworkAttacks #Probequest #Python https://t.co/a1yD8MZmzz"

Cyber adversaries have weaponized #CobaltStrike for #networkattacks. Find out about Raindrop #malware and its emergence post-SolarWinds. Read the full story: bit.ly/2XVWFq5

Threats like malware, ransomware, and phishing attacks continue to make headlines, inflicting pain on businesses of all sizes. Hackers are sophisticated and continuously creating new approaches to attack your network & access your data. #networkattacks #ransomware #cybersecurity

Something went wrong.
Something went wrong.
United States Trends
- 1. Jets 64.2K posts
- 2. Justin Fields 4,021 posts
- 3. Aaron Glenn N/A
- 4. Peart 1,377 posts
- 5. #BroncosCountry 2,181 posts
- 6. Garrett Wilson N/A
- 7. #JetUp 1,245 posts
- 8. Tyrod N/A
- 9. Sherwood 1,192 posts
- 10. #DENvsNYJ 1,382 posts
- 11. Good Sunday 65.3K posts
- 12. #AskFFT N/A
- 13. #sundayvibes 6,401 posts
- 14. Bam Knight N/A
- 15. Rich Eisen N/A
- 16. Kurt Warner N/A
- 17. Brownlee 1,004 posts
- 18. Nate Adkins N/A
- 19. Troy Franklin N/A
- 20. George Stephanopoulos 2,495 posts