#exploitcode search results
Demo #ExploitCode Published for #RemoteCode Execution via #Microsoft Edge buff.ly/2TaqKO8 #informedsecurity

KILLER! Unpatched WinRAR Vulnerability Puts 500 Million Users… rd.cempal.com/CJd1b5 #compressfiles #exploitcode

#Memcached #DDoS #ExploitCode and List of 17,000 Vulnerable Servers Released bit.ly/2oXwPjL #TechNews #Hacking #Hackers #CyberSecurity #Privacy #CyberAttacks


Critical Zoho Zero-Day Flaw Disclosed news.sofiaitc.com/RRNdgX #Vulnerabilities #Exploit #exploitcode #pocexploit #ProofofConcept

Publicly Available #ExploitCode Gives #Attackers 47-Day Head Start. bit.ly/3pIGXeD #informedsecurity

The CSW team has put together a code that can exploit CVE-2022-22965. Watch our video that demonstrates how to execute the #exploitcode. Understand the impact an attacker can create, if the #vulnerability is exploited. Follow for updates- bit.ly/3JYNgnY #Spring4Shell

Exploit Development webinar FREE! infosecaddicts.com/free-exploit-d… #exploitdevelopment #webinar #exploitcode #penetrationtests #freewebinar
Cisco IOS/IOS XE の脆弱性 CVE-2023-20109:RCE 悪用が観測されている iototsecnews.jp/2023/09/28/cis… #AuthNAuthZ #CyberAttack #ExploitCode #Vulnerability
SharePoint の脆弱性 CVE-2023-29357/CVE-2023-24955:PoC エクスプロイトが登場 iototsecnews.jp/2023/09/28/res… #ExploitCode #TTP #Vulnerability
#Exploitcode published for dangerous #ApacheSolr #remotecodeexecution flaw buff.ly/2DbsL6S via @ZDNet & @campuscodi #informedsecurity

"I feel it helps explain why ASLR+DEP r not a mitigation to put a lot of faith in,especially on x86 platforms" bit.ly/dyJWwa #ExploitCode
#Exploitcode released for three iOS #0days that #Apple failed to patch | #CyberSecurity bleepingcomputer.com/news/security/…
securityweek.com/exploit-code-p… #VMware #exploitcode #SSHauthentication #ThreatIntelligence #CyberSecurity
Linksys Malware 'The Moon' Spreading from Router to Router dlvr.it/4xrHvd #exploitcode #hackingBelkinrounter #infosec #kaminfo
Disqus Wordpress Plugin Flaw Leaves Millions of Blogs... dlvr.it/69Ct5P #Disquscommenthacking #exploitcode #infosec #kaminfo
Internet-Connected Medical Washer-Disinfector Found… dlvr.it/NkgLzR #directorytraversalvulnerability #exploitcode #infosec #kaminfo
WordPress Cookie Flaw Lets Hackers to Hijack Your Account dlvr.it/5nxt4N #cookiesstealing #exploitcode #infosec #kaminfo
CVE-2024-55591 Exploit Code Released for FortiOS Flaw #CVE-2024-55591 #ExploitCode #Fortinet thecyberthrone.in/2025/01/30/cve…
CVE-2025-21298 Exploit Code Released #CVE-2025-21298 #Microsoft #ExploitCode thecyberthrone.in/2025/01/24/cve…
CVE-2024-53691: PoC Exploit Code Release for QNAP Flaw #CVE-2024-53691 #QNAP #ExploitCode thecyberthrone.in/2025/01/20/cve…
CVE-2024-54498: Exploit Code Released for macOS Flaw #CVE-2024-54498 #macOS #ExploitCode thecyberthrone.in/2025/01/13/cve…
Exploit Code released for Apache Traffic Control Flaw CVE-2024-45387 #ApacheTrafficControl #CVE-2024-45387 #ExploitCode thecyberthrone.in/2024/12/30/exp…
thecyberthrone.in
Exploit Code released for Apache Traffic Control Flaw CVE-2024-45387
What is CVE-2024-45387? CVE-2024-45387 is a critical vulnerability identified in Apache Traffic Control, specifically affecting the Traffic Ops module in versions 8.0.0 to 8.0.1. The nature of this…
Exploit code released for Microsoft CVE-2024-30085 #Microsoft #CVE-2024-30085 #ExploitCode thecyberthrone.in/2024/12/28/exp…
Exploit Code for Apache Struts CVE-2024-53677 released #ApacheStruts #CVE-2024-53677 #ExploitCode thecyberthrone.in/2024/12/18/exp…
thecyberthrone.in
Exploit Code for Apache Struts CVE-2024-53677 released
The proof-of-concept (PoC) exploit code for the critical Apache Struts vulnerability, designated as CVE-2024-53677, has been released. This vulnerability poses a severe risk to systems running Apac…
A researcher revealed that GPT-4o can generate exploit code by bypassing security using hex-encoded instructions, highlighting AI vulnerabilities. market-news24.com/ai/a-researche… #AIsafety #Cybersecurity #exploitcode #GPT4o #hexadecimalencoding #OpenAI #Vulnerability

Windows Kernel Vulnerability - CVE-2024-21338 PoC Exploit Released #WindowsKernel #CVE-2024-21338 #ExploitCode thecyberthrone.in/2024/04/17/win…
thecyberthrone.in
Windows Kernel Vulnerability – CVE-2024-21338 PoC Exploit Released
Security researchers published the technical details and proof-of-concept (PoC) exploit code for a zero-day CVE-2024-21338 vulnerability that was recently exploited by the state-backed North Korean…
SharePoint の脆弱性 CVE-2023-29357/CVE-2023-24955:PoC エクスプロイトが登場 iototsecnews.jp/2023/09/28/res… #ExploitCode #TTP #Vulnerability
Cisco IOS/IOS XE の脆弱性 CVE-2023-20109:RCE 悪用が観測されている iototsecnews.jp/2023/09/28/cis… #AuthNAuthZ #CyberAttack #ExploitCode #Vulnerability
How to Find and Use Public #ExploitCode j.mp/2aHytyz #cybersecurity #mediabodyguard #hackers #zeroday

#ExploitCode that could be used to achieve #RemoteCodeExecution on #VMware #vCenter Server vulnerable to CVE-2021-22005 is currently spreading online. #Cybersecurity ow.ly/nyNp50GgaXt

Critical Zoho Zero-Day Flaw Disclosed news.sofiaitc.com/RRNdgX #Vulnerabilities #Exploit #exploitcode #pocexploit #ProofofConcept

#Memcached #DDoS #ExploitCode and List of 17,000 Vulnerable Servers Released bit.ly/2oXwPjL #TechNews #Hacking #Hackers #CyberSecurity #Privacy #CyberAttacks


A researcher revealed that GPT-4o can generate exploit code by bypassing security using hex-encoded instructions, highlighting AI vulnerabilities. market-news24.com/ai/a-researche… #AIsafety #Cybersecurity #exploitcode #GPT4o #hexadecimalencoding #OpenAI #Vulnerability

KILLER! Unpatched WinRAR Vulnerability Puts 500 Million Users… rd.cempal.com/CJd1b5 #compressfiles #exploitcode

The CSW team has put together a code that can exploit CVE-2022-22965. Watch our video that demonstrates how to execute the #exploitcode. Understand the impact an attacker can create, if the #vulnerability is exploited. Follow for updates- bit.ly/3JYNgnY #Spring4Shell

Demo #ExploitCode Published for #RemoteCode Execution via #Microsoft Edge buff.ly/2TaqKO8 #informedsecurity

Publicly Available #ExploitCode Gives #Attackers 47-Day Head Start. bit.ly/3pIGXeD #informedsecurity

.@Cisco warnt vor einer gravierenden Sicherheitslücke in seiner neuesten Generation an IP-Telefonen. Laut Hersteller existiert ein #ExploitCode für die Schwachstelle. dlvr.it/Sf5MXb

μTorrent Forum Hacked; Change your Password… rd.cempal.com/LW9TGv #accounthacking #databreach #exploitcode

FBI paid Hacker $1.3 Million to Unlock San Bernardino… rd.cempal.com/L6wrB4 #blackhathacker #exploitcode #FBI

#Exploitcode published for dangerous #ApacheSolr #remotecodeexecution flaw buff.ly/2DbsL6S via @ZDNet & @campuscodi #informedsecurity

Here's the Exploit to Bypass Apple Security Feature… rd.cempal.com/Kx9vYw #AppleMacOSX #AppleMacOS #exploitcode

Cisco Exploit Leaked in NSA Hack Modifies to Target Latest… rd.cempal.com/M603pF #cisco #exploitcode #Firewall

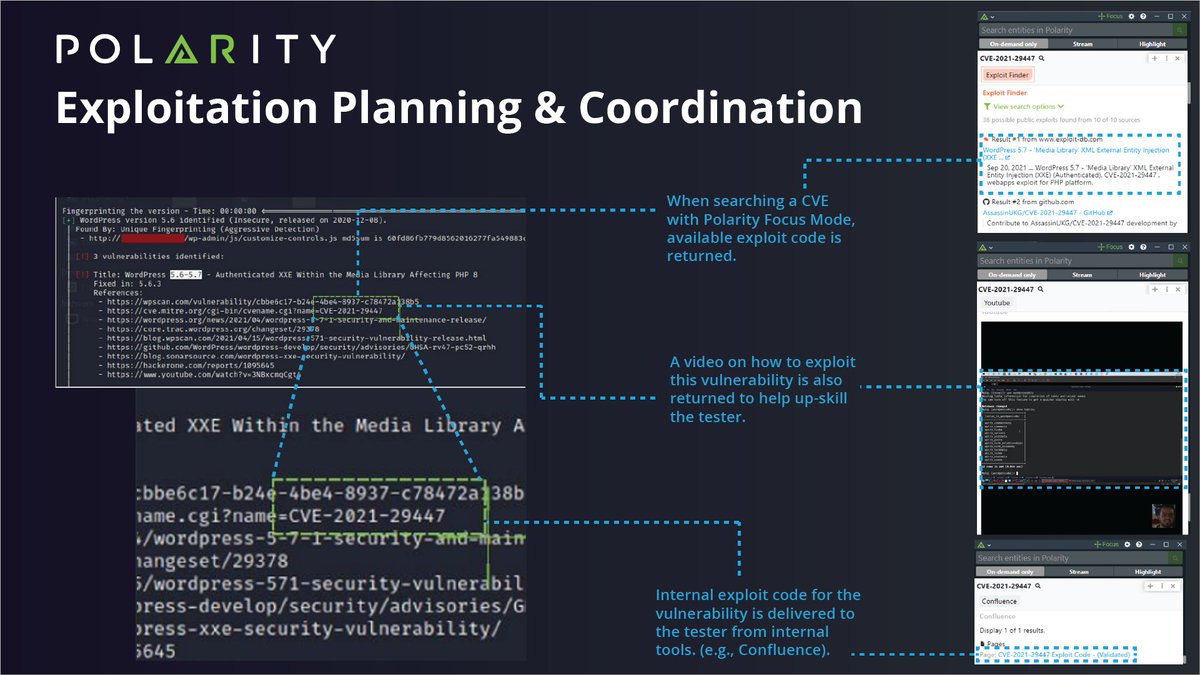
Polarity reduces the time required to search for #exploitcode, and arms practitioners with the means to achieve #offensivesecurity objectives. To see a demo of this use case, watch the recording of last week's webinar: hubs.ly/Q01GSPNH0
Something went wrong.
Something went wrong.
United States Trends
- 1. Columbus 67.9K posts
- 2. #SwiftDay 8,402 posts
- 3. #WWERaw 22.3K posts
- 4. #IDontWantToOverreactBUT N/A
- 5. #IndigenousPeoplesDay 2,826 posts
- 6. #TSTheErasTour 2,161 posts
- 7. Knesset 119K posts
- 8. Marc 35.2K posts
- 9. Good Monday 39.6K posts
- 10. Victory Monday 1,551 posts
- 11. Thanksgiving 42.6K posts
- 12. Flip 48.1K posts
- 13. Branch 47.8K posts
- 14. Kairi 9,921 posts
- 15. Broadcom 1,744 posts
- 16. Rod Wave 3,103 posts
- 17. Penta 4,691 posts
- 18. Happy 250th 2,040 posts
- 19. The Final Show 27.2K posts
- 20. Egypt 152K posts
































