#exploitdevelopment search results
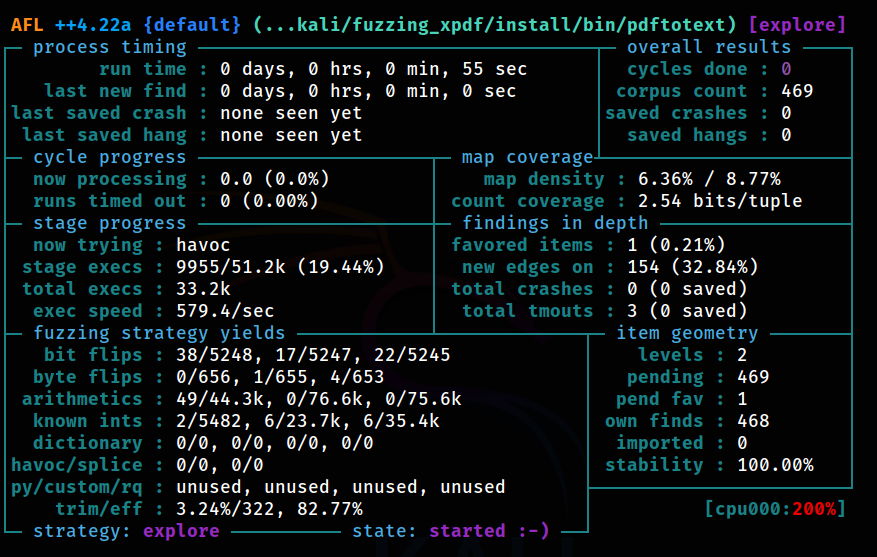
Exploit Development: Fuzzing Applications to Find Zero-Day Vulnerabilities in Software #afl #exploitdevelopment #fuzzing #cybersecurity #cyberwarriors #zeroday hackers-arise.com/post/exploit-d…
fireELF - Fileless Linux Malware Framework j.mp/2VXkETl #ELF #ExploitDevelopment #ExploitationFramework #fireELF #Framework

At #NullconBerlin2025, Emanuele Barbeno took us behind the scenes of Pwn2Own 2024, revealing how his team exploited a vulnerability in the Ubiquiti AI Bullet IP camera to achieve unauthenticated RCE. Watch Now: youtube.com/watch?v=l-7N6h… #Pwn2Own #ExploitDevelopment #Cybersecurity

youtube.com
YouTube
#NullconBerlin2025 | DHCPwned: Owning Cameras One Lease at a Time by...
CVE-2023-26083 is a kernel address disclosure in Mali GPU drivers. Read how this Mali GPU bug impacts Pixel & other ARM64 devices - 8ksec.io/cve-2023-26083… #Android #CyberSecurity #ExploitDevelopment

Are you attending our #exploitdevelopment webinar for a chance to #win either a FREE XDS Elite Edition or XDS Full Edition? 🎁

How does XDS fit into our catalog of practical #cybersecurity courses? #exploitdevelopment #exploitdev #InfoSec #ITSecurity #redteam #blueteam
Attending fulll power packed session on Exploit development 101 by @malav_vyas1 @NullAhm @null0x00 #exploitdevelopment #nullahm #exploitdevelopment
The virtual waiting room is now open! The live launch webinar of XDS starts soon 🙌 #exploitdevelopment #exploitdev #redteam #pentesting #vulnerability #research #infosec #ITsecurity

What do I get myself into? Throwing myself back into x86 assembly. Can’t wait to polish up on #ExploitDevelopment with @offsectraining #EXP301. Send help and bourbon.

XDS may have student in the title, but it provides not only the fundamentals of Windows and Linux #exploitdevelopment but also covers advanced Windows and Linux #exploitdev techniques, as well as anti-exploit mechanism bypasses! #ITSecurity #cybersecurity #InfoSec

Need more convincing to enroll in our XDS course? 😎 #exploitdev #exploitdevelopment #redteam #cybersecurity #ITsecurity #InfoSec

freeFTPd 1.0.10 pwned!!! Another SEH stack-based buffer overflow. This was a fun exploit to develop, island hopping was a bit tricky, but worth the effort! #exploitdevelopment #osed


Kick your #cybersecurity career into high gear with our newest training course, Exploit Development Student! 💪 Join us for the live launch webinar on September 17th: bit.ly/2lzXuow #InfoSec #ExploitDevelopment
Now it's time for a closer look at the importance of #exploitdevelopment as an #ITSecurity skill and a live demo of XDS! #InfoSec #cybersecurity #redteam #exploitdev

☑️This is one of the finest and most advanced courses you will find on Win32 stack based #exploitdevelopment. ☑️This course is a truly unique opportunity to learn both basic & advanced techniques from an experienced exploit developer. #CenterforCyberSecurityTraini

Exploit Development, Part 3: Fuzzing with Spike to Find Vulnerabilities #fuzzing #spike #exploitdevelopment #cybersecurity #cyberwarrior bit.ly/2tt1syJ

مجموعة مقالات بالعربية كتبتها منذ فترة لشرح بعض المواضيع المتعلقة بـ #ExploitDevelopment -Intro to x86 Shellcoding -Writing Linux Shellcode -Writing Windows Shellcode -SEH Exploits -Egg Hunters nakerah.net/community/reso… #exploitDev #cybersecurity #redteam #أمن_المعلومات

📣 XDS launches TOMORROW! Reserve your spot for the live webinar now: bit.ly/2kAo6FV #exploitdevelopment #redteam #pentesting #InfoSec #ITSecurity

Exploit Development: Fuzzing Applications to Find Zero-Day Vulnerabilities in Software #afl #exploitdevelopment #fuzzing #cybersecurity #cyberwarriors #zeroday hackers-arise.com/post/exploit-d…

How does XDS fit into our catalog of practical #cybersecurity courses? #exploitdevelopment #exploitdev #InfoSec #ITSecurity #redteam #blueteam

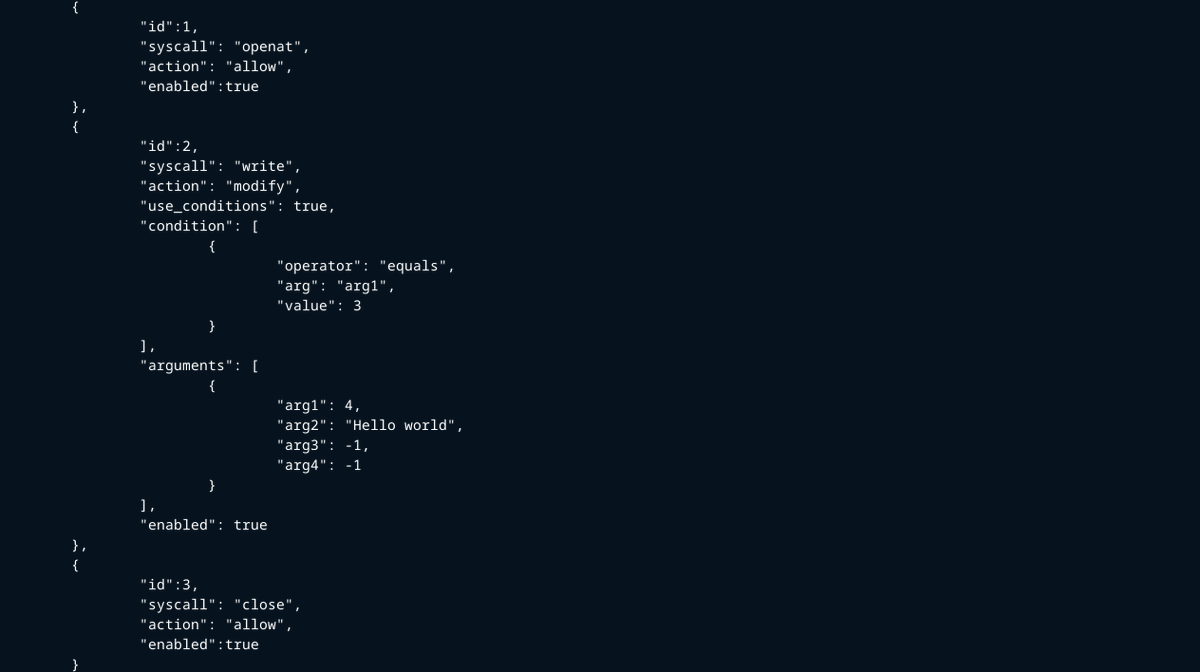
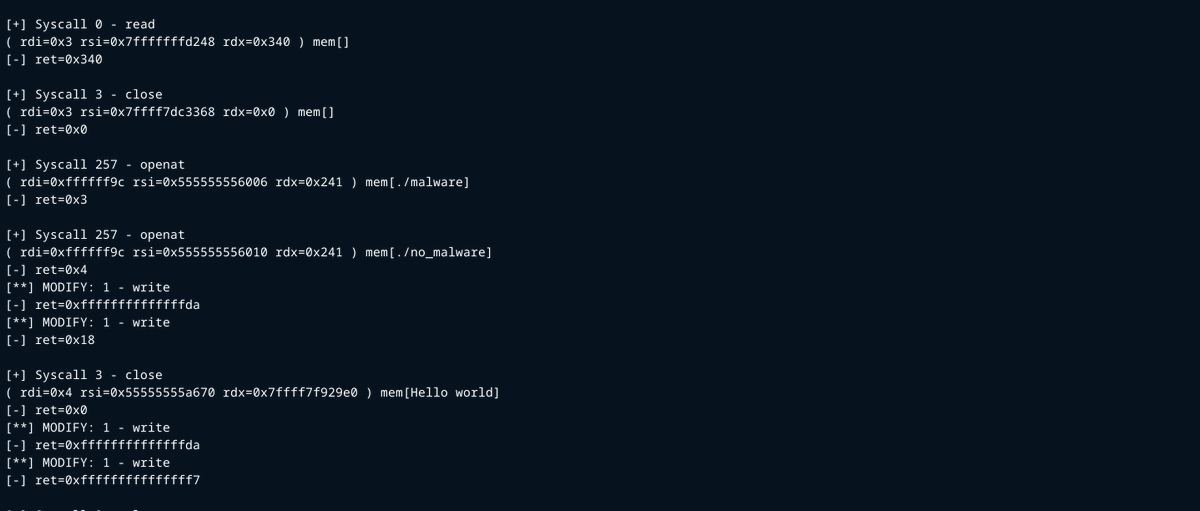
Implemented logic to modifying syscalls during process execution using a policy configuration file github.com/t1b4n3/pwntrace #reverseengineering #exploitdevelopment
The virtual waiting room is now open! The live launch webinar of XDS starts soon 🙌 #exploitdevelopment #exploitdev #redteam #pentesting #vulnerability #research #infosec #ITsecurity

Attending fulll power packed session on Exploit development 101 by @malav_vyas1 @NullAhm @null0x00 #exploitdevelopment #nullahm #exploitdevelopment

Kick your #cybersecurity career into high gear with our newest training course, Exploit Development Student! 💪 Join us for the live launch webinar on September 17th: bit.ly/2lzXuow #InfoSec #ExploitDevelopment

fireELF - Fileless Linux Malware Framework j.mp/2VXkETl #ELF #ExploitDevelopment #ExploitationFramework #fireELF #Framework

Now it's time for a closer look at the importance of #exploitdevelopment as an #ITSecurity skill and a live demo of XDS! #InfoSec #cybersecurity #redteam #exploitdev

I explain how Windows implements ASLR, how it affects reverse engineering and exploitation, and practical ways to analyze or bypass it when needed. reverselabs.dev/blog/aslr-addr… #WindowsSecurity #ReverseEngineering #ExploitDevelopment #MemoryProtection

Are you attending our #exploitdevelopment webinar for a chance to #win either a FREE XDS Elite Edition or XDS Full Edition? 🎁

Need more convincing to enroll in our XDS course? 😎 #exploitdev #exploitdevelopment #redteam #cybersecurity #ITsecurity #InfoSec

📣 XDS launches TOMORROW! Reserve your spot for the live webinar now: bit.ly/2kAo6FV #exploitdevelopment #redteam #pentesting #InfoSec #ITSecurity

XDS may have student in the title, but it provides not only the fundamentals of Windows and Linux #exploitdevelopment but also covers advanced Windows and Linux #exploitdev techniques, as well as anti-exploit mechanism bypasses! #ITSecurity #cybersecurity #InfoSec

Exploit Development, Part 3: Fuzzing with Spike to Find Vulnerabilities #fuzzing #spike #exploitdevelopment #cybersecurity #cyberwarrior bit.ly/2tt1syJ

CVE-2023-26083 is a kernel address disclosure in Mali GPU drivers. Read how this Mali GPU bug impacts Pixel & other ARM64 devices - 8ksec.io/cve-2023-26083… #Android #CyberSecurity #ExploitDevelopment

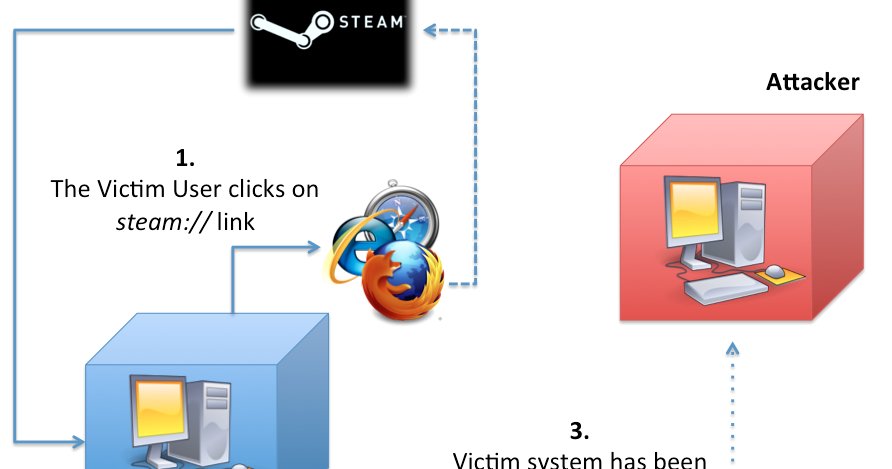
Steam Browser Protocol Insecurity (When Local Bugs Go Remote) revuln.blogspot.com/2018/12/steam-… #NetworkSecurity #ExploitDevelopment #SoftwareSecurity #Infosec
freeFTPd 1.0.10 pwned!!! Another SEH stack-based buffer overflow. This was a fun exploit to develop, island hopping was a bit tricky, but worth the effort! #exploitdevelopment #osed


Exploit Development, Part 3: Finding Security Vulnerabilities Using the Spike Fuzzer #fuzz #exploitdevelopment #spike #cybersecurity #cyberwarrior hackers-arise.com/post/2017/06/2…

مجموعة مقالات بالعربية كتبتها منذ فترة لشرح بعض المواضيع المتعلقة بـ #ExploitDevelopment -Intro to x86 Shellcoding -Writing Linux Shellcode -Writing Windows Shellcode -SEH Exploits -Egg Hunters nakerah.net/community/reso… #exploitDev #cybersecurity #redteam #أمن_المعلومات

Something went wrong.
Something went wrong.
United States Trends
- 1. Good Wednesday 21.7K posts
- 2. #PercyJackson 10.6K posts
- 3. Immanuel 2,568 posts
- 4. Hump Day 6,397 posts
- 5. #MerryChristmasJustin 6,339 posts
- 6. annabeth 7,569 posts
- 7. grover 2,993 posts
- 8. clarisse 1,286 posts
- 9. #HumanRightsDay 18K posts
- 10. Oslo 241K posts
- 11. Bicycle 5,518 posts
- 12. Slept 20.2K posts
- 13. María Corina Machado 192K posts
- 14. Keanu 2,941 posts
- 15. #bb27 1,193 posts
- 16. Gowdy 6,195 posts
- 17. Danity Kane 2,882 posts
- 18. Aundrea 1,271 posts
- 19. Premio Nobel de la Paz 126K posts
- 20. Eileen Higgins 35.4K posts















