#hackwithautomation نتائج البحث
CVE-2023-26469 - Jorani 1.0.0 - Remote Code Execution 💣 Shodan: http.favicon.hash:-2032163853 Nuclei Template:- github.com/projectdiscove… @pdnuclei Reference: github.com/Orange-Cyberde… Follow this thread to see How this Template made? #hackwithautomation #pdteam #cve2023

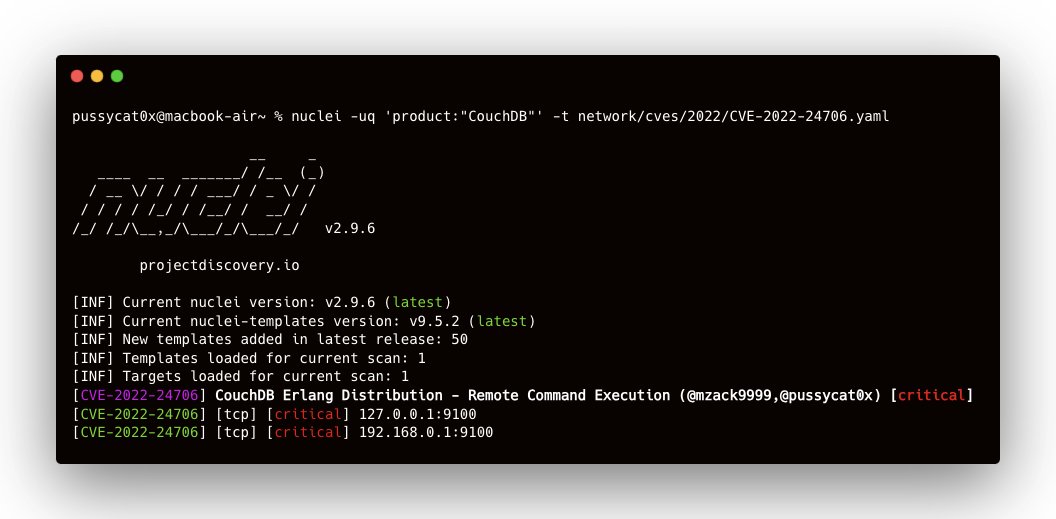
CouchDB Erlang Distribution - Remote Command Execution(CVE-2022-24706) CRITICAL 🚨 nuclei -t /network/cves/2022/CVE-2022-24706.yaml -l ips.txt @pdnuclei Link: github.com/projectdiscove… Follow the thread to see how the template created 😼 #hackwithautomation #pdteam #nuclei
How to extract a list of enpoints from JS files with katana! 👇 #hacking #cybersecurity #hackwithautomation #bugbounty

How to use httpx and the -path flag to check for juicy paths 👇 #hackwithautomation #cybersecurity #hacking #bugbounty #opensource

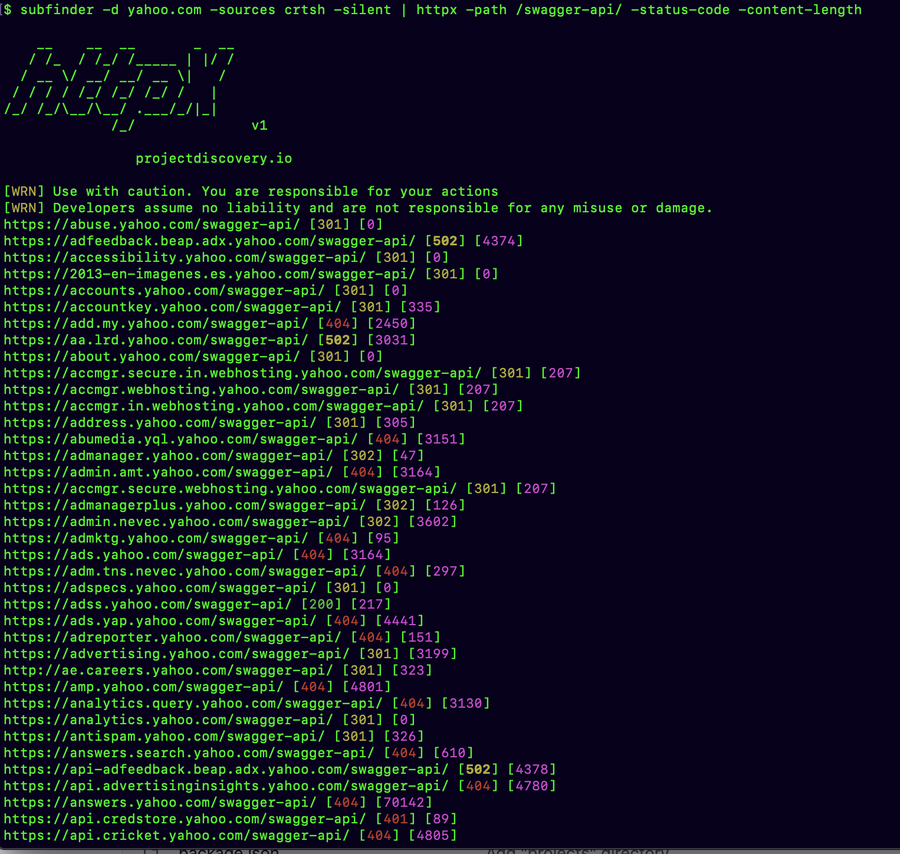
⚡You can use #httpx to request any path and see the status code and other details on the go, filter, or matcher flags if you want to be more specific. ✅httpx -path /swagger-api/ -status-code -content-length 👉Credit:@pdnuclei #hackwithautomation #recon #bugbountytips…

🥳🥳🥳With @pdiscoveryio/Uncover, now easily search for exposed assets through HUNTER.HOW API github.com/projectdiscove… THX @xm1k3_ #hackwithautomation #recon #assetdiscovery #security #bugbounty #bugbountytips #infosecurity #infosec

🚨 CVE-2024-21893 - Ivanti SAML - Server Side Request Forgery (SSRF) - [HIGH] Nuclei Template : github.com/projectdiscove… @pdnuclei #hackwithautomation #bugbounty #cve2023 #Ivanti
![DhiyaneshDK's tweet image. 🚨 CVE-2024-21893 - Ivanti SAML - Server Side Request Forgery (SSRF) - [HIGH]
Nuclei Template : github.com/projectdiscove… @pdnuclei
#hackwithautomation #bugbounty #cve2023 #Ivanti](https://pbs.twimg.com/media/GFZpBpeWoAAE8fI.jpg)
How to query all DNS records for single host using dnsx 👇 #hackwithautomation #cybersecurity #hacking #bugbounty #opensource

Detect CyberPanel RCE with Nuclei 🚀 🔹 Template: cloud.projectdiscovery.io/?template=cybe… 🔹 Research by @dreyand_: dreyand.rs/code/review/20… #hackwithautomation #BugBounty #Cybersecurity

Detect Sitecore RCE (CVE-2024-46938) with Nuclei 🚀 🔹 Nuclei Template: cloud.projectdiscovery.io/?template=CVE-… by @DhiyaneshDK 🔹 Research: assetnote.io/resources/rese… by @assetnote #hackwithautomation #Cybersecurity #AppSec #BugBounty

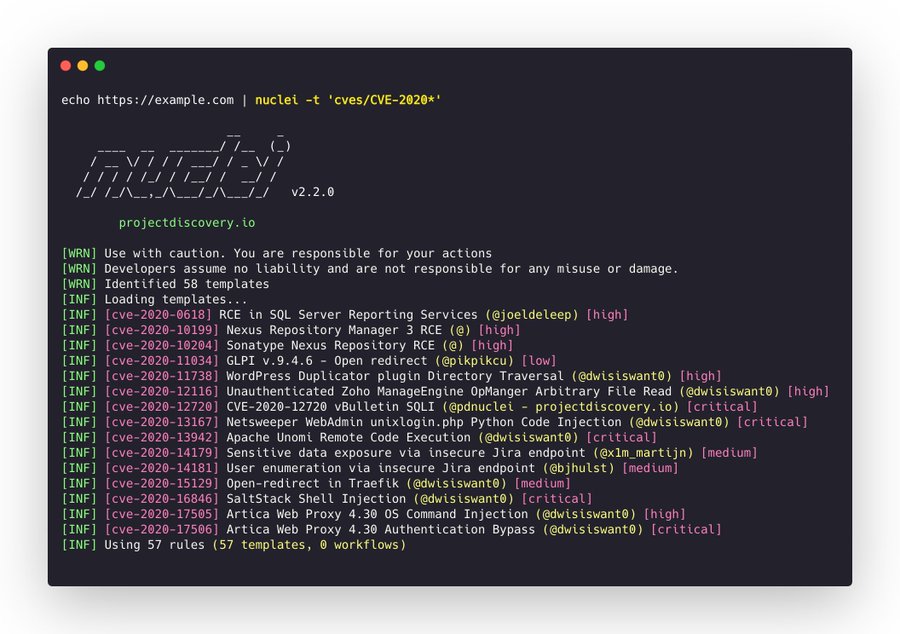
Using wildcard glob support in nuclei, you can quickly scan for CVEs of specific years, for example, 𝗻𝘂𝗰𝗹𝗲𝗶 -𝘁 '𝗰𝘃𝗲𝘀/𝗖𝗩𝗘-𝟮𝟬𝟮𝟬*' will scan for all the CVEs assigned in 2020 from nuclei templates project. credit:@pdnuclei #nucleitips #hackwithautomation
Have you tried using the ✨OSINT✨ templates yet? Here's how you would look for OSINT regarding the username "johnsmith" 🕵️ ⚛️ nuclei -tags osint -var user=johnsmith #nuclei101 #hackwithautomation #opensource

Did you know you can scan UDP ports with naabu? Here's how 👇 #opensource #hackwithautomation #naabu #portscanning #hacking

You can use #httpx to request any path and see the status code and other details on the go, filter, or matcher flags if you want to be more specific. httpx -path /swagger-api/ -status-code -content-length credit:@pdnuclei #hackwithautomation #recon #bugbountytips #infosec
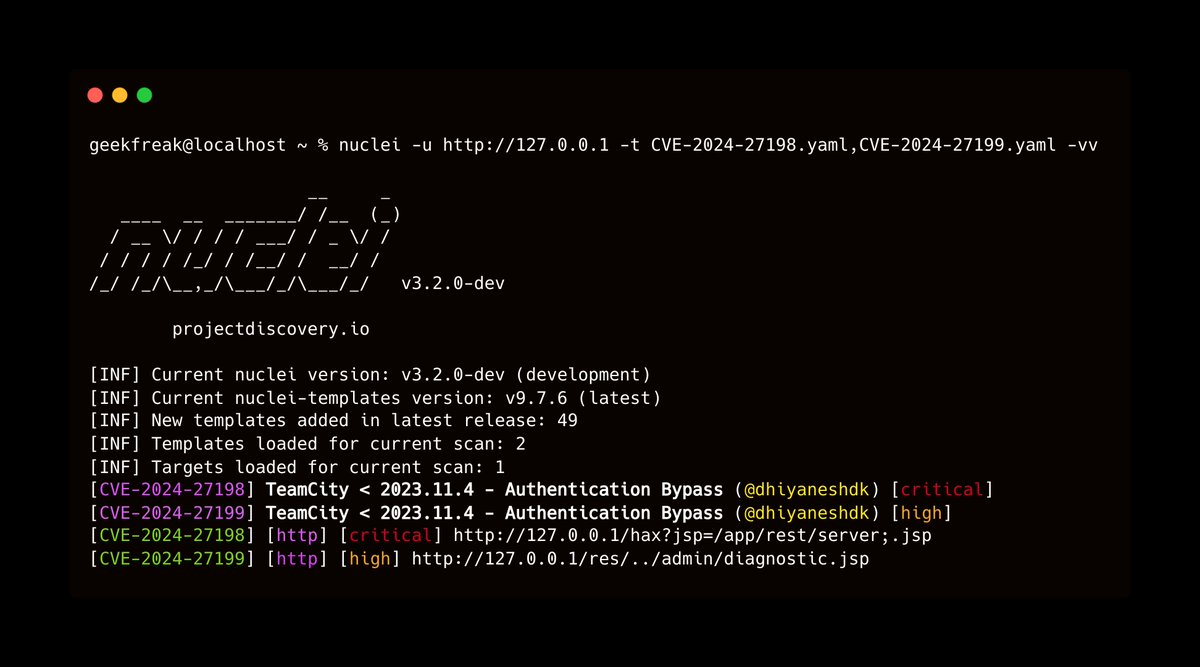
Scan for JetBrains TeamCity Authentication Bypass Vulnerabilities using @pdnuclei CVE-2024-27198 (Critical) - github.com/projectdiscove… CVE-2024-27199 (High) - github.com/projectdiscove… #pdteam #hackwithautomation #jetbrains #CVE
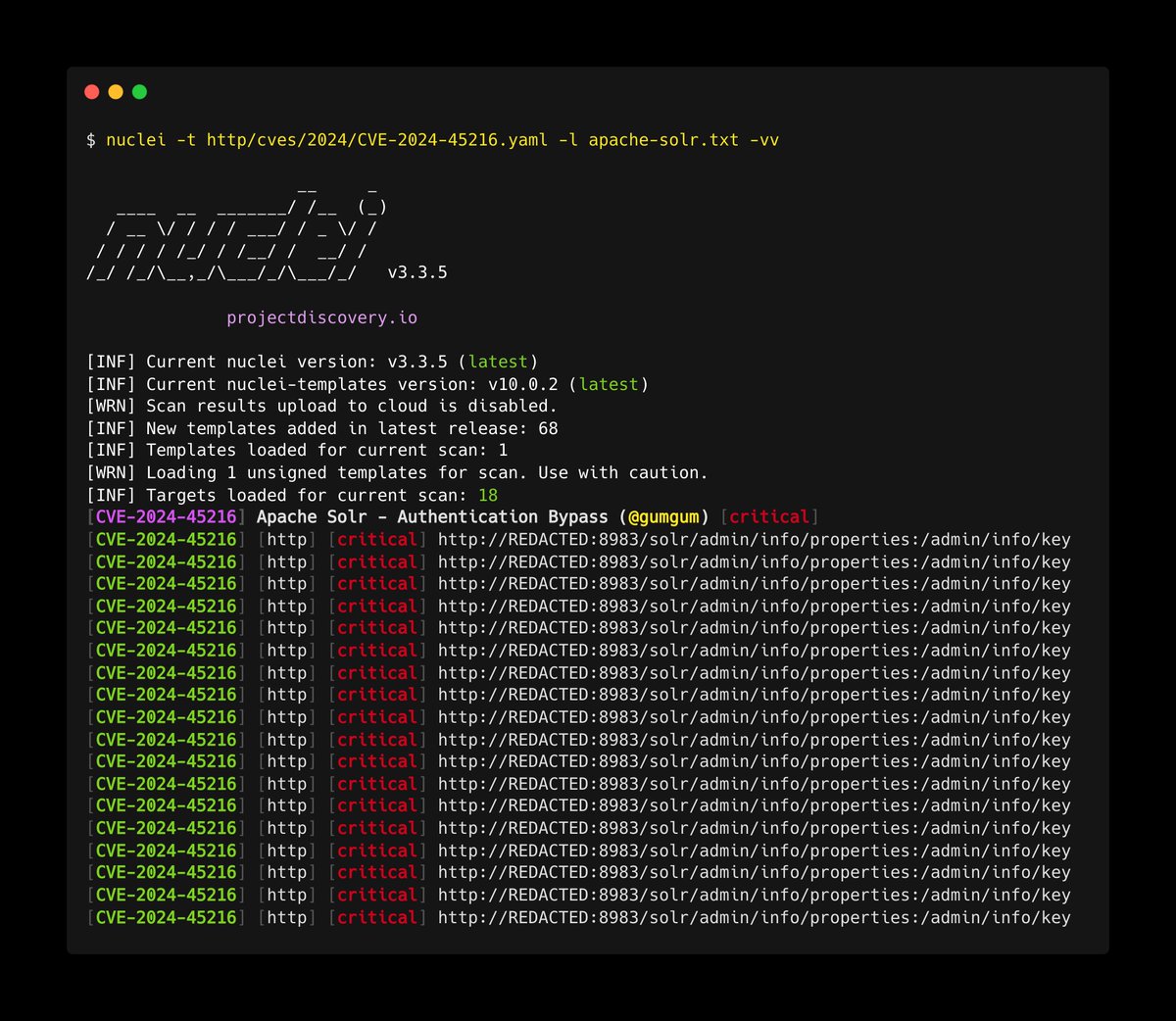
🚀Detect Apache Solr Authentication Bypass (CVE-2024-45216) with @pdnuclei Template: cloud.projectdiscovery.io/?template=CVE-… Research by shfsec.com/cve-2024-45216… #hackwithautomation #bugbounty #cybersecurity
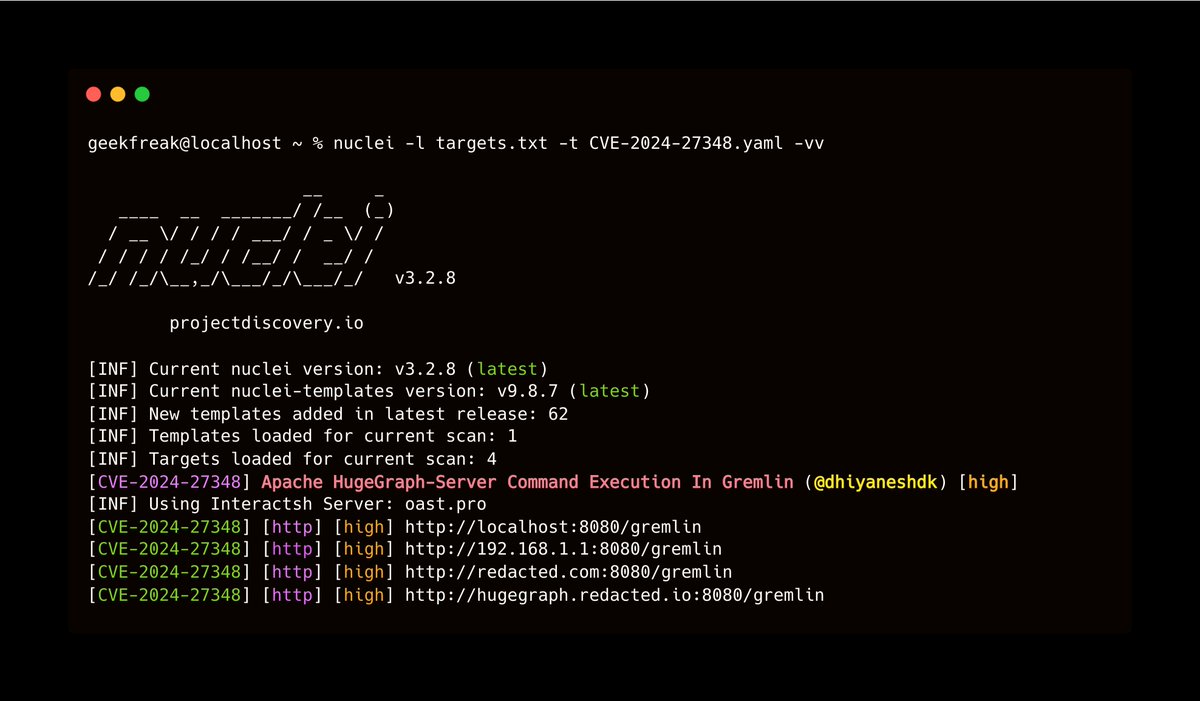
CVE-2024-27348 - Apache HugeGraph-Server Command Execution In Gremlin @pdnuclei Nuclei Template - github.com/projectdiscove… #hackwithautomation #pdteam #cve #apache #bugbounty
🚨 Scanning Ivanti Cloud Services Appliance - Path Traversal (CVE-2024-8963) Using Nuclei Template shared by johnk3r 🔍 Template : cloud.projectdiscovery.io/?template=CVE-… #ivanti #kev #hackwithautomation

Something went wrong.
Something went wrong.
United States Trends
- 1. $TCT 1,584 posts
- 2. Cyber Monday 30.8K posts
- 3. Good Monday 35.6K posts
- 4. #MondayMotivation 7,031 posts
- 5. TOP CALL 11.1K posts
- 6. #IDontWantToOverreactBUT N/A
- 7. #MondayVibes 3,037 posts
- 8. Victory Monday N/A
- 9. Market Focus 2,284 posts
- 10. New Month 394K posts
- 11. Alina Habba 8,316 posts
- 12. Check Analyze N/A
- 13. Token Signal 2,445 posts
- 14. Clarie 2,548 posts
- 15. #NavidadConMaduro 1,589 posts
- 16. John Denver 1,626 posts
- 17. Rosa Parks 2,884 posts
- 18. #MondayMood 1,279 posts
- 19. Happy 1st 24.9K posts
- 20. Jillian 1,969 posts