#knownexploitedvulnerabilities zoekresultaten
📢#CISA added six vulnerabilities to #KnownExploitedVulnerabilities catalog, confirming active #exploitation. The vulnerabilities impact #SysAid, and #JuniperNetworks' #JunosOS. Explore the details of the SysAid #vulnerability🔻 socradar.io/path-traversal…

📢In a recent update, #CISA has included the CVE-2023-29552 #vulnerability in its #KnownExploitedVulnerabilities (#KEV) catalog. The agency has set the due date for organizations to #patch CVE-2023-29552 as November 29, 2023. Read more on SOCRadar👇 socradar.io/severe-slp-vul…
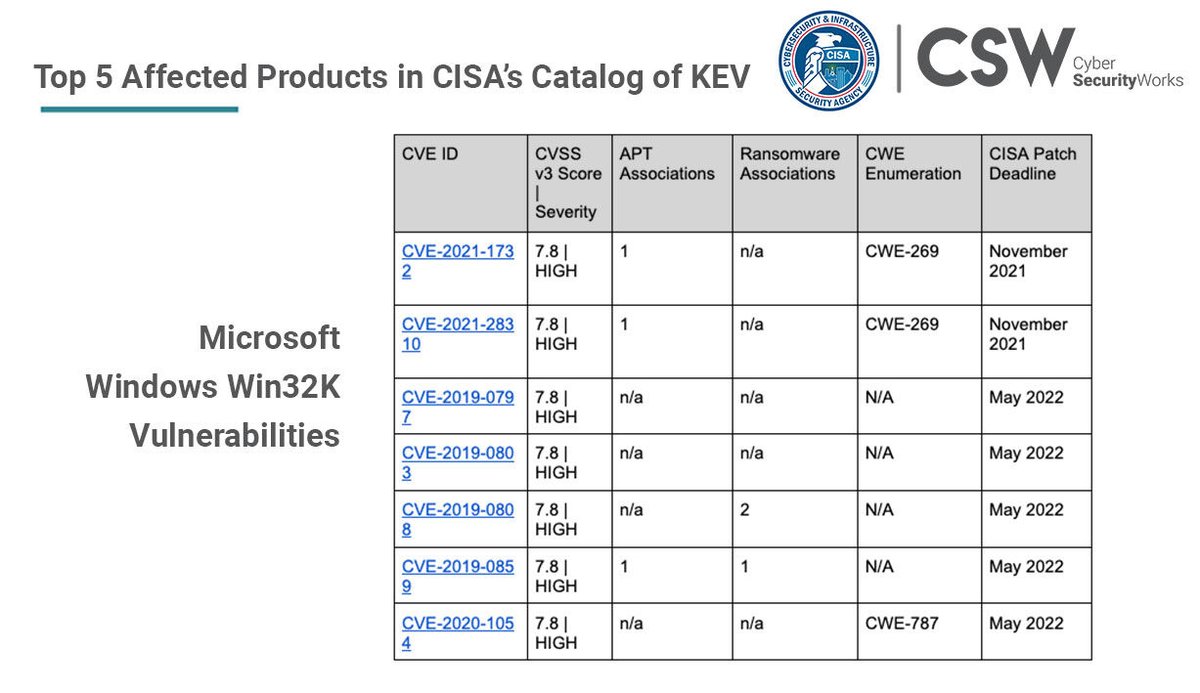
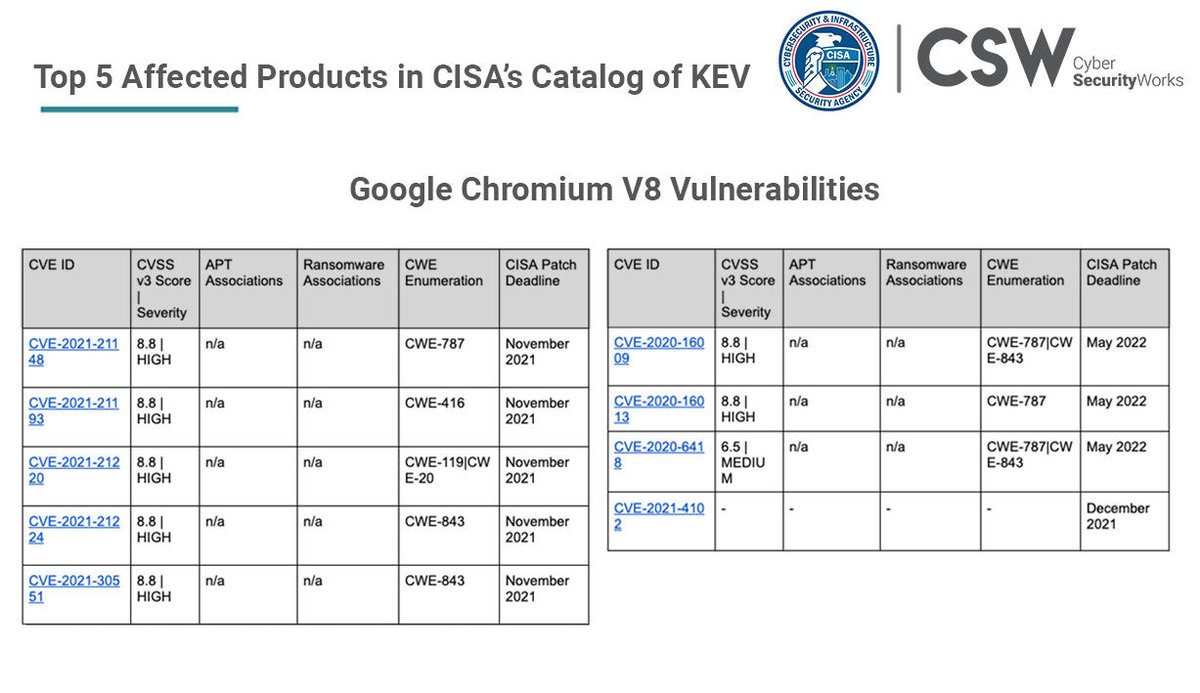
Microsoft Windows Win32K, with 7 unique CVEs affecting its products, ties Microsoft alongside Google with two products each in the top 5. Read the blog - bit.ly/3zGY1qK #CISA #KEVcatalog #knownexploitedvulnerabilities #securitydebt #securityhygiene
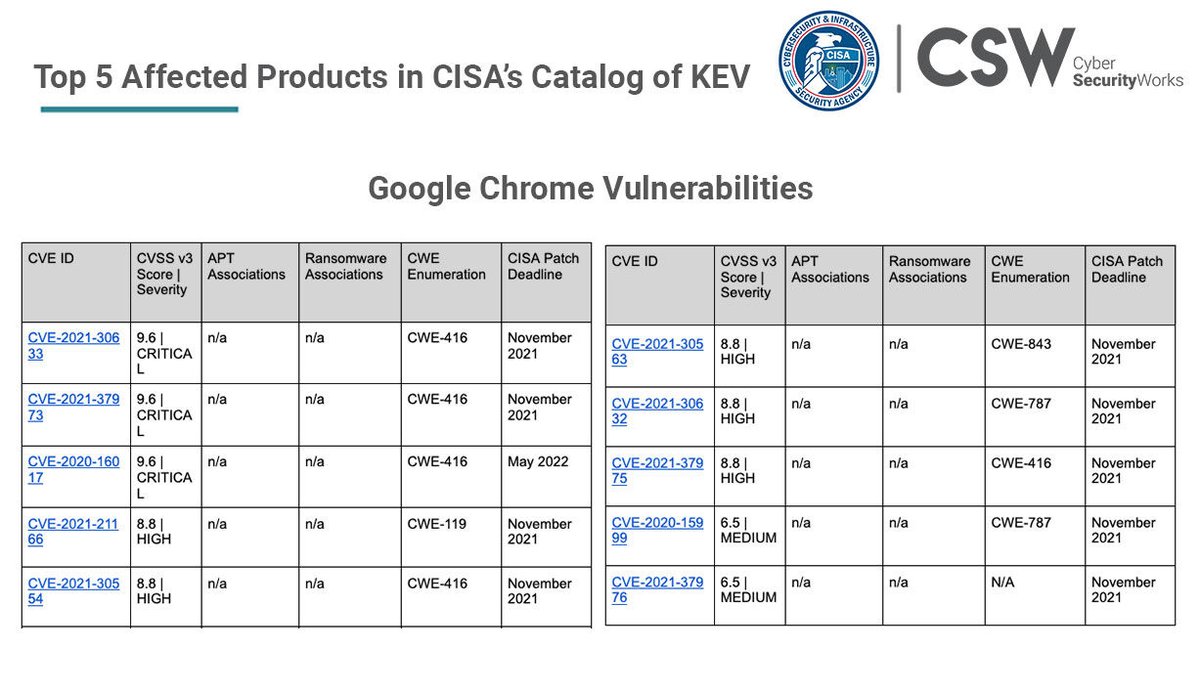
Google Chrome has the highest number of vulnerabilities affecting it. With a total of 10 unique CVEs, it stands atop the product density list, alongside Microsoft Exchange Server. Read the blog - bit.ly/3zGY1qK #CISA #KEVcatalog #knownexploitedvulnerabilities #infosec
CISA updated its KEV again! Here is how March is looking like for security teams! You have 12 KEVs to patch this month! Get the list here - zurl.co/2fah #CISAKEV #KnownExploitedVulnerabilities #cyberhygiene #cyberattacks
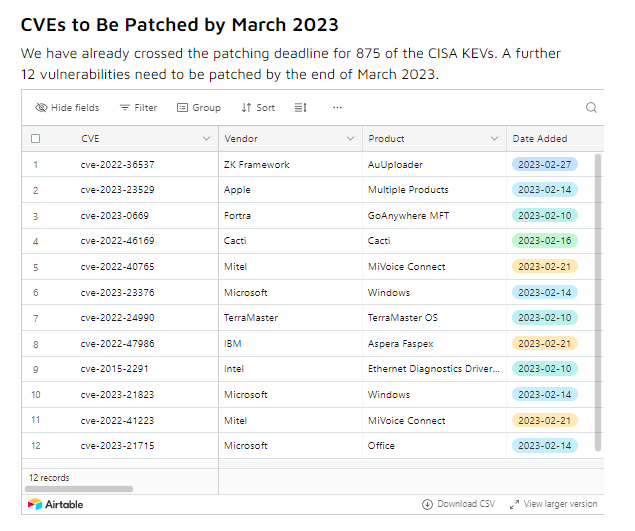
Google appears twice in the list of Top products affected, with Chromium V8 affected by 8 vulnerabilities. Read the blog - bit.ly/3zGY1qK #CISA #KEVcatalog #knownexploitedvulnerabilities #securitydebt #securityhygiene #vulnerabilitymanagement #infosec #google
We have already looked at the top vendors affected, where Microsoft, Apple, and Google share the top three positions with the most vulnerabilities. Read the blog - bit.ly/3zGY1qK #CISA #KEVcatalog #knownexploitedvulnerabilities #securitydebt #securityhygiene
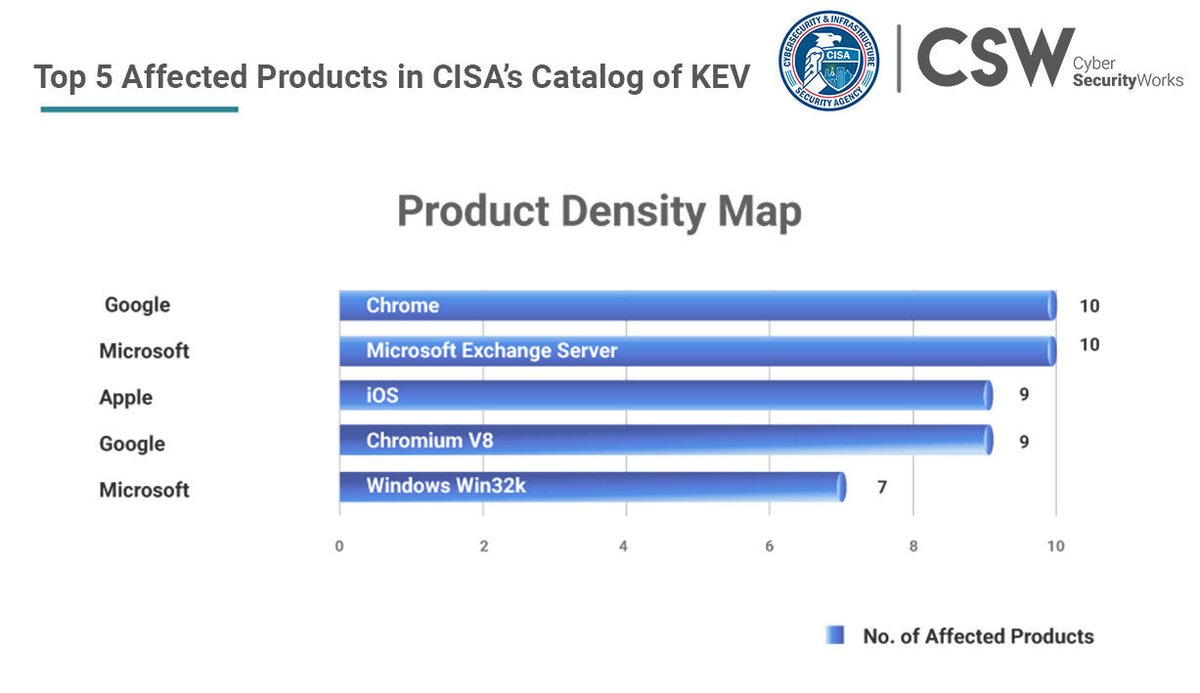
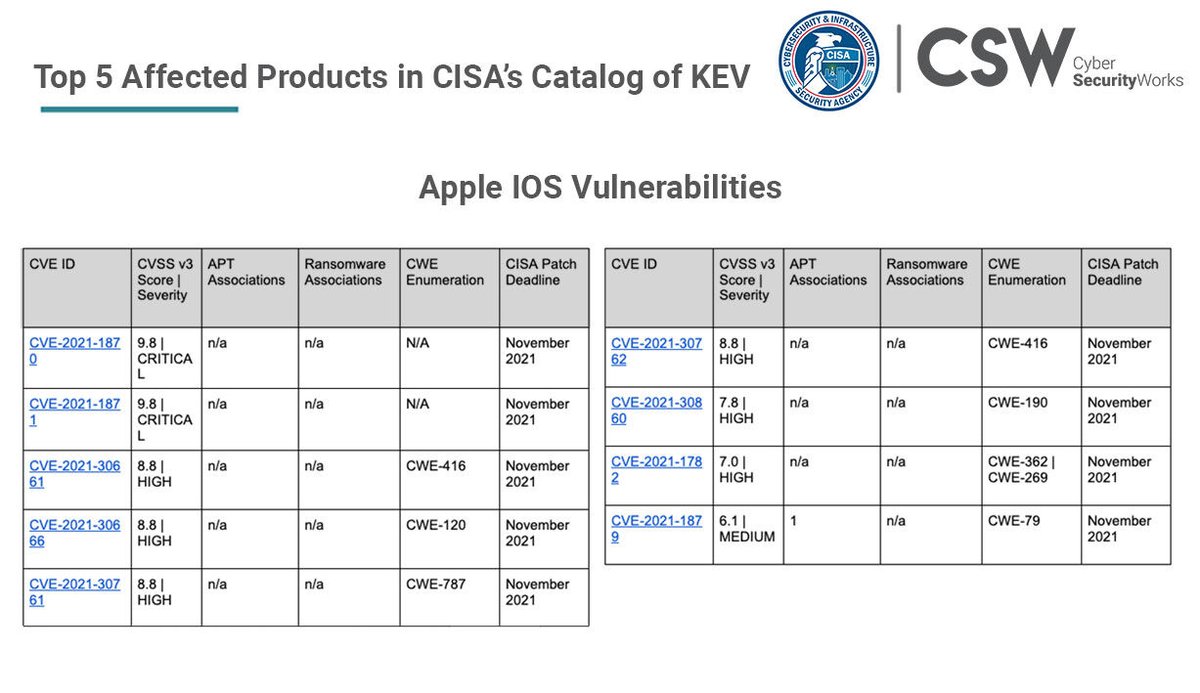
Apple’s iOS has a total of nine vulnerabilities associated with it, giving Apple the third position on the products affected list. Read the blog - bit.ly/3zGY1qK #CISA #KEVcatalog #knownexploitedvulnerabilities #securitydebt #securityhygiene #infosec #apple
We took a deep dive into CISA’s catalog of 311 Known Exploited Vulnerabilities (KEV) reveals a plethora of vendors who have multiple products affected by several vulnerabilities. Read the blog - bit.ly/3zGY1qK #CISA #KEVcatalog #knownexploitedvulnerabilities #infosec

#KnownExploitedVulnerabilities: aggiunte al catalogo @CISACyber #vulnerabilità presenti in prodotti #Zyxel, #ProjectSend e #CyberPanel (una con CVSS 10, il massimo della gravità). Misure di mitigazione in attesa delle #patch👉🏽securityinfo.it/2024/12/09/vul… #cybersecurity @wcs_cloud #WCS

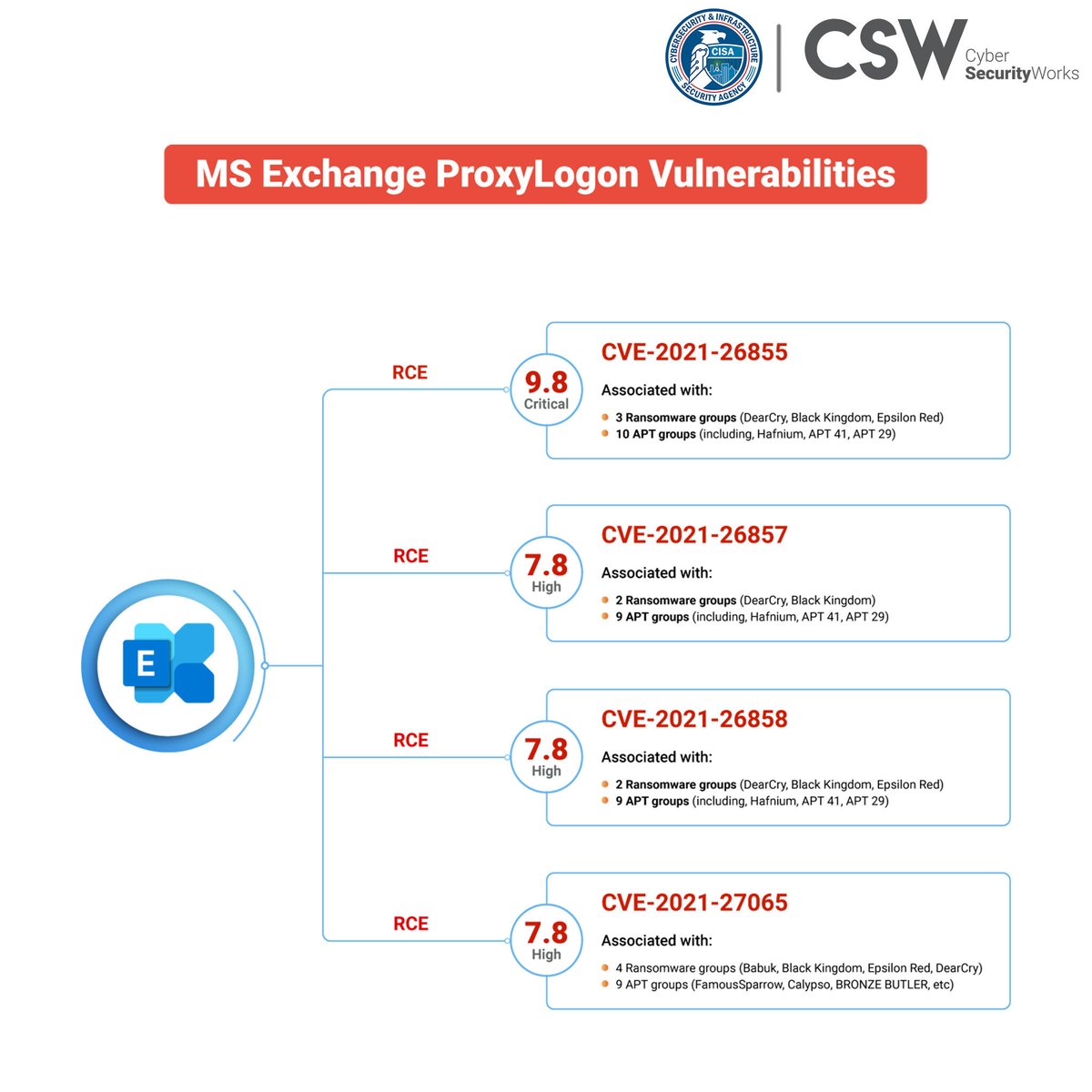
The ProxyLogon vulnerabilities comprise four flaws each being crucial for organizations to fix since multiple ransomware and APT groups have exploited them. Read the blog - bit.ly/3zGY1qK #CISA #KEVcatalog #knownexploitedvulnerabilities #informationtechnology
Stay ahead of the curve in #CyberSecurity looking at #KnownExploitedVulnerabilities from Samsung, D-Link, and Apple. Stay safe! 🛡️ #InfoSec #TechNew
7/10 CISA's Warning: 🚨 @CISAgov adds #GeoServer flaw to KEV catalog. Time to update! #CyberSecurity #KnownExploitedVulnerabilities 🛑🔒
CISA KEV の効果:連邦政府機関における脆弱性を 72% も減少させた iototsecnews.jp/2023/09/22/fas… #CISAKEV #KnownExploitedVulnerabilities #NCS #Vulnerability
iototsecnews.jp
CISA KEV の効果:連邦政府機関における脆弱性を 72% も減少させた
Faster Patching Pace Validates CISA’s KEV Catalog Initiative 2023/09/22 SecurityWeek — 米国のサイバーセキュリティ機関 CISA が管理する KEV (Known Exploited Vulnerabilities) カタログにより、連邦政府機関のパッチ適用作業が大幅に改善されたという。現在では…
securityaffairs.com/149382/securit… #vulnerability #KnownExploitedVulnerabilities #NETvulnerability #VisualStudiovulnerability
securityaffairs.com
CISA adds actively exploited flaw in .NET, Visual Studio to its Known Exploited Vulnerabilities...
US CISA added zero-day vulnerability CVE-2023-38180 affecting .NET and Visual Studio to its Known Exploited Vulnerabilities catalog.
Huge news! #Vulnerabilities utilized by commercial surveillance #spyware are now included in the #KnownExploitedVulnerabilities catalog, according to CISA! This highlights the importance of staying up-to-date with security. #CyberSecurity #NetworkSecurity
The IRS is not Remediating all Known Exploited Vulnerabilities. Want to find out more? Our recent article by Kyle Rose discusses the matter in more detail: bit.ly/3PC47kR #IRS #KnownExploitedVulnerabilities #KEVCatalog

#KnownExploitedVulnerabilities: aggiunte al catalogo @CISACyber #vulnerabilità presenti in prodotti #Zyxel, #ProjectSend e #CyberPanel (una con CVSS 10, il massimo della gravità). Misure di mitigazione in attesa delle #patch👉🏽securityinfo.it/2024/12/09/vul… #cybersecurity @wcs_cloud #WCS

When only 35% of exploited vulnerabilities are included on CISA’s #KnownExploitedVulnerabilities list, it's no wonder our 2023 Global Threat Roundup is still making headlines 📰. It is critical to stay proactive, read now @helpnetsecurity 🔗 bit.ly/42QVOYD #VedereLabs
📢#CISA added six vulnerabilities to #KnownExploitedVulnerabilities catalog, confirming active #exploitation. The vulnerabilities impact #SysAid, and #JuniperNetworks' #JunosOS. Explore the details of the SysAid #vulnerability🔻 socradar.io/path-traversal…

📢In a recent update, #CISA has included the CVE-2023-29552 #vulnerability in its #KnownExploitedVulnerabilities (#KEV) catalog. The agency has set the due date for organizations to #patch CVE-2023-29552 as November 29, 2023. Read more on SOCRadar👇 socradar.io/severe-slp-vul…

The IRS is not Remediating all Known Exploited Vulnerabilities. Want to find out more? Our recent article by Kyle Rose discusses the matter in more detail: bit.ly/3PC47kR #IRS #KnownExploitedVulnerabilities #KEVCatalog

「1000を超えたアレ」については、こんな報告もあります。 iototsecnews.jp/2023/09/22/fas… #CISA #KEV #KnownExploitedVulnerabilities
iototsecnews.jp
CISA KEV の効果:連邦政府機関における脆弱性を 72% も減少させた
Faster Patching Pace Validates CISA’s KEV Catalog Initiative 2023/09/22 SecurityWeek — 米国のサイバーセキュリティ機関 CISA が管理する KEV (Known Exploited Vulnerabilities) カタログにより、連邦政府機関のパッチ適用作業が大幅に改善されたという。現在では…
ポッドキャストの新作エピソード公開されてますよ! ・BlackCatのアレ ・1000を超えたアレ ・MFAがMFAじゃないアレ の3アレです。聴いてくださいまし。 第195回 KEVとOTPとMFA!スペシャル! « podcast - #セキュリティのアレ tsujileaks.com/?p=1606

CISA KEV の効果:連邦政府機関における脆弱性を 72% も減少させた iototsecnews.jp/2023/09/22/fas… #CISAKEV #KnownExploitedVulnerabilities #NCS #Vulnerability
iototsecnews.jp
CISA KEV の効果:連邦政府機関における脆弱性を 72% も減少させた
Faster Patching Pace Validates CISA’s KEV Catalog Initiative 2023/09/22 SecurityWeek — 米国のサイバーセキュリティ機関 CISA が管理する KEV (Known Exploited Vulnerabilities) カタログにより、連邦政府機関のパッチ適用作業が大幅に改善されたという。現在では…
securityaffairs.com/149382/securit… #vulnerability #KnownExploitedVulnerabilities #NETvulnerability #VisualStudiovulnerability
securityaffairs.com
CISA adds actively exploited flaw in .NET, Visual Studio to its Known Exploited Vulnerabilities...
US CISA added zero-day vulnerability CVE-2023-38180 affecting .NET and Visual Studio to its Known Exploited Vulnerabilities catalog.
securityboulevard.com/2023/07/rezili… #vulnerability #KnownExploitedVulnerabilities #ResilionKEV #CyberSecurity
In our latest blog post, we share where Known Exploited Vulnerabilities (#KEVs) come from, how they fit into existing security strategies, & why it’s important to prioritize these vulnerabilities. #knownexploitedvulnerabilities #cybersecurity #ASM #EASM blog.halosecurity.com/kevs-explained…
blog.halosecurity.com
What are KEVs? Known Exploited Vulnerabilities Explained
See where Known Exploited Vulnerabilities (KEVs) come from, how they fit into existing security strategies, and why it’s important to prioritize these vulnerabilities.
What are Known Exploited Vulnerabilities or KEVs, & why do they matter? Learn more about #KEVs in our latest video. #KnownExploitedVulnerabilities #ASM #EASM #cybersecuritytips youtube.com/watch?v=lhrbPL…
youtube.com
YouTube
What are KEVs? Known Exploited Vulnerabilities Explained
Protect yourself from cyberattacks! Millions of systems remain exposed to #KnownExploitedVulnerabilities. Stay safe and up-to-date with the #KEV catalog from @CISAgov. #CyberSecurity #CyberAwareness Stay safe online: a777web.com/x tmcnet.com/usubmit/-new-r…
CISA updated its KEV again! Here is how March is looking like for security teams! You have 12 KEVs to patch this month! Get the list here - zurl.co/2fah #CISAKEV #KnownExploitedVulnerabilities #cyberhygiene #cyberattacks

Microsoft Windows Win32K, with 7 unique CVEs affecting its products, ties Microsoft alongside Google with two products each in the top 5. Read the blog - bit.ly/3zGY1qK #CISA #KEVcatalog #knownexploitedvulnerabilities #securitydebt #securityhygiene

#KnownExploitedVulnerabilities: aggiunte al catalogo @CISACyber #vulnerabilità presenti in prodotti #Zyxel, #ProjectSend e #CyberPanel (una con CVSS 10, il massimo della gravità). Misure di mitigazione in attesa delle #patch👉🏽securityinfo.it/2024/12/09/vul… #cybersecurity @wcs_cloud #WCS

📢In a recent update, #CISA has included the CVE-2023-29552 #vulnerability in its #KnownExploitedVulnerabilities (#KEV) catalog. The agency has set the due date for organizations to #patch CVE-2023-29552 as November 29, 2023. Read more on SOCRadar👇 socradar.io/severe-slp-vul…

CISA updated its KEV again! Here is how March is looking like for security teams! You have 12 KEVs to patch this month! Get the list here - zurl.co/2fah #CISAKEV #KnownExploitedVulnerabilities #cyberhygiene #cyberattacks

📢#CISA added six vulnerabilities to #KnownExploitedVulnerabilities catalog, confirming active #exploitation. The vulnerabilities impact #SysAid, and #JuniperNetworks' #JunosOS. Explore the details of the SysAid #vulnerability🔻 socradar.io/path-traversal…

Microsoft Windows Win32K, with 7 unique CVEs affecting its products, ties Microsoft alongside Google with two products each in the top 5. Read the blog - bit.ly/3zGY1qK #CISA #KEVcatalog #knownexploitedvulnerabilities #securitydebt #securityhygiene

Apple’s iOS has a total of nine vulnerabilities associated with it, giving Apple the third position on the products affected list. Read the blog - bit.ly/3zGY1qK #CISA #KEVcatalog #knownexploitedvulnerabilities #securitydebt #securityhygiene #infosec #apple

Google appears twice in the list of Top products affected, with Chromium V8 affected by 8 vulnerabilities. Read the blog - bit.ly/3zGY1qK #CISA #KEVcatalog #knownexploitedvulnerabilities #securitydebt #securityhygiene #vulnerabilitymanagement #infosec #google

We have already looked at the top vendors affected, where Microsoft, Apple, and Google share the top three positions with the most vulnerabilities. Read the blog - bit.ly/3zGY1qK #CISA #KEVcatalog #knownexploitedvulnerabilities #securitydebt #securityhygiene

Google Chrome has the highest number of vulnerabilities affecting it. With a total of 10 unique CVEs, it stands atop the product density list, alongside Microsoft Exchange Server. Read the blog - bit.ly/3zGY1qK #CISA #KEVcatalog #knownexploitedvulnerabilities #infosec

We took a deep dive into CISA’s catalog of 311 Known Exploited Vulnerabilities (KEV) reveals a plethora of vendors who have multiple products affected by several vulnerabilities. Read the blog - bit.ly/3zGY1qK #CISA #KEVcatalog #knownexploitedvulnerabilities #infosec

The ProxyLogon vulnerabilities comprise four flaws each being crucial for organizations to fix since multiple ransomware and APT groups have exploited them. Read the blog - bit.ly/3zGY1qK #CISA #KEVcatalog #knownexploitedvulnerabilities #informationtechnology

The IRS is not Remediating all Known Exploited Vulnerabilities. Want to find out more? Our recent article by Kyle Rose discusses the matter in more detail: bit.ly/3PC47kR #IRS #KnownExploitedVulnerabilities #KEVCatalog

Something went wrong.
Something went wrong.
United States Trends
- 1. #WWENXT 8,111 posts
- 2. Notre Dame 31.1K posts
- 3. Notre Dame 31.1K posts
- 4. Bama 20.8K posts
- 5. Van Epps 115K posts
- 6. Boogie Fland N/A
- 7. Jaylen Brown 3,051 posts
- 8. Syracuse 8,297 posts
- 9. Duke 24.7K posts
- 10. Cam Boozer N/A
- 11. Paul Dano 4,681 posts
- 12. Tennessee 204K posts
- 13. Ament N/A
- 14. Behn 67.1K posts
- 15. Haugh N/A
- 16. Tarantino 11.4K posts
- 17. #TADCFriend 2,765 posts
- 18. #PumpRules N/A
- 19. #CFPRankings N/A
- 20. Hugo Gonzalez N/A