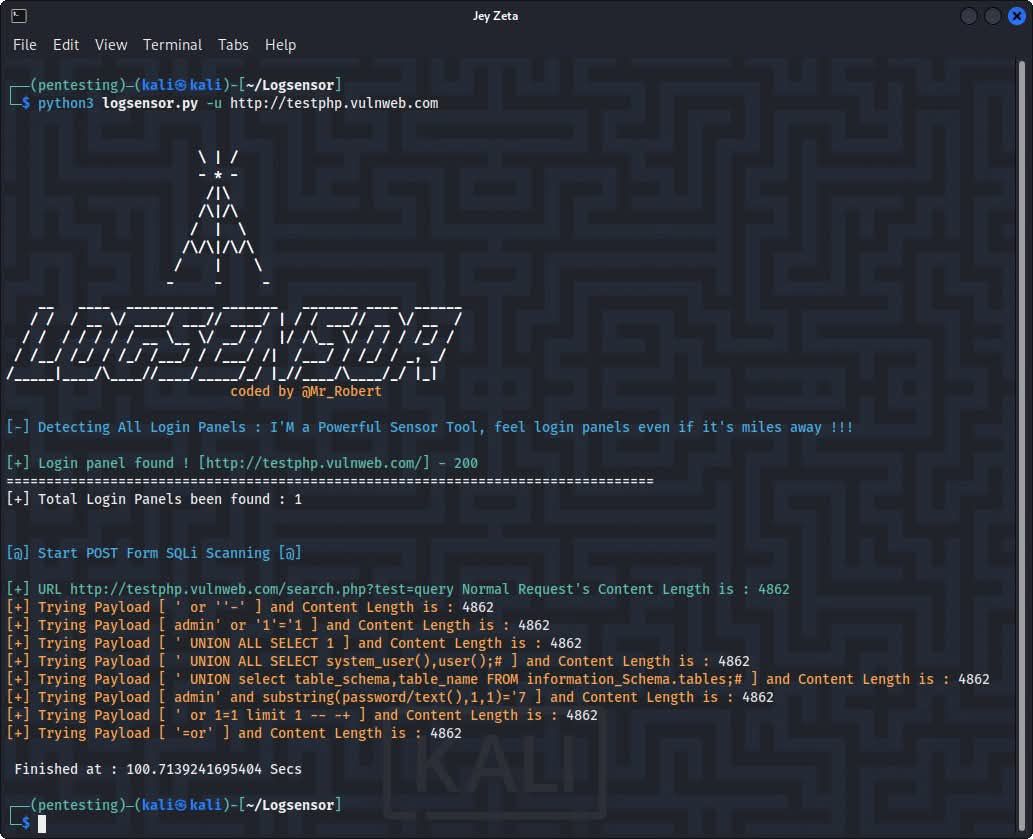
#sqli نتائج البحث
𝗟𝗼𝗴𝘀𝗲𝗻𝘀𝗼𝗿 🕵🏽♂️ Herramienta en Python para descubrir paneles de login y escaneo de SQLi en formularios POST. Soporta escaneo de múltiples hosts, escaneo dirigido de formularios SQLi y proxies. 🛡️ 🌐 github.com/Mr-Robert0/Log… #Logsensor #SQLI #Pentesting #CyberSecurity…
#WooCommerce — #SQLi CVE in Payment Extensions 🚨 Why it matters: SQL injection in WooCommerce payment add-ons can leak customer info, alter orders, and inject malicious scripts 🛡️ Action: Block SQLi attempts and scan your store for injected code quttera.com #CVE…

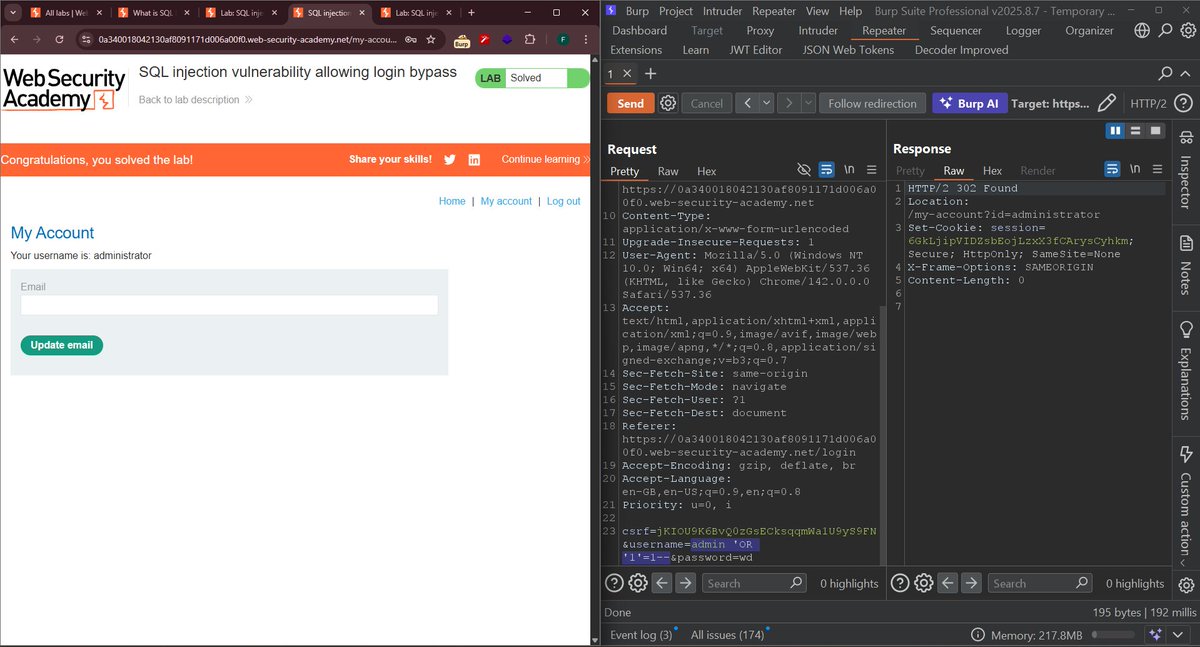
Just bypassed the admin login in a PortSwigger lab using classic SQLi 😎 Payload: admin' OR '1'='1-- No sanitization = full authentication bypass. Burp Repeater FTW 💥 #CyberSecurity #SQLi #BugBounty #WebSecurity
⚠️ Website Security Alert Why it matters: Outdated plugins expose sites to #SQLi, #RCE, and #XSS exploit chains. 🛡️ Action: Enable auto-updates, remove unused components, and run regular CVE-driven vulnerability scans #CVE #CyberSecurity #Malware

⚠️ #Drupal Alert Exploited modules open #SQLi → #RCE chains that deploy 0-day malware 🛡️ Action: Audit modules and scan with Quttera’s heuristic detection engine quttera.com #CyberSecurity #Malware #WebsiteSecurity

Devolutions Server patched a Critical SQLi flaw (CVE-2025-13757) allowing authenticated users to exfiltrate or modify data via log parameters. Update to v2025.2.21 or v2025.3.9 immediately. #Devolutions #PasswordManager #SQLi #Cybersecurity securityonline.info/critical-devol…
🚨 WordPress users, attention! The 'My auctions allegro' plugin (v3.6.32 & earlier) has a critical SQL Injection vulnerability. Unauthenticated attackers can steal sensitive database info! 🛡️ Update NOW to protect your site. tenable.com/cve/CVE-2025-1… #WordPressSecurity #SQLi #CVE
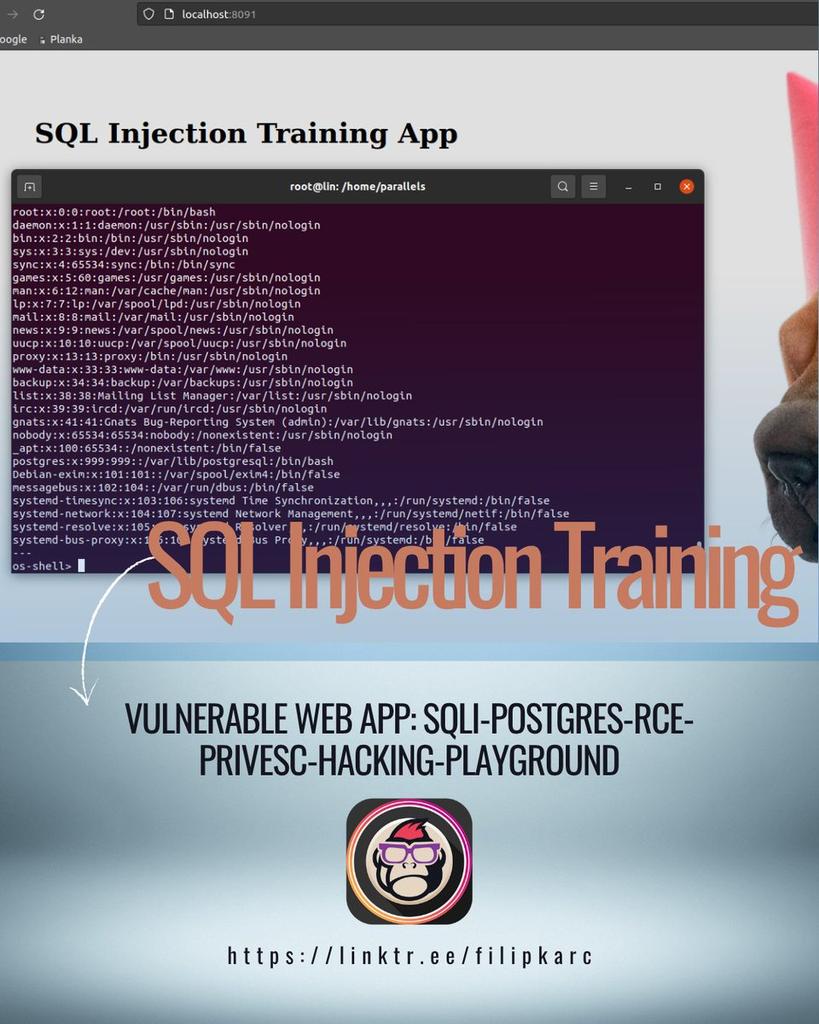
Domina la cadena de ataque completa: SQLi ➡️ RCE ➡️ PrivEsc. Este playground en Docker te permite practicar la explotación de PostgreSQL en un entorno seguro y realista. ¡Un desafío esencial para todo pentester! Link: github.com/filipkarc/sqli… 💥🧪 #SQLi #HackingEtico #Pentest
#PrestaShop — Payment Form Injection via SQLi 🚨 Why it matters: SQL injection in outdated PrestaShop plugins injects fake payment forms and steals customer info 🛡️ Action: Use Quttera Malware Scanner to detect injected forms early quttera.com/website-malwar… #Malware #SQLi…

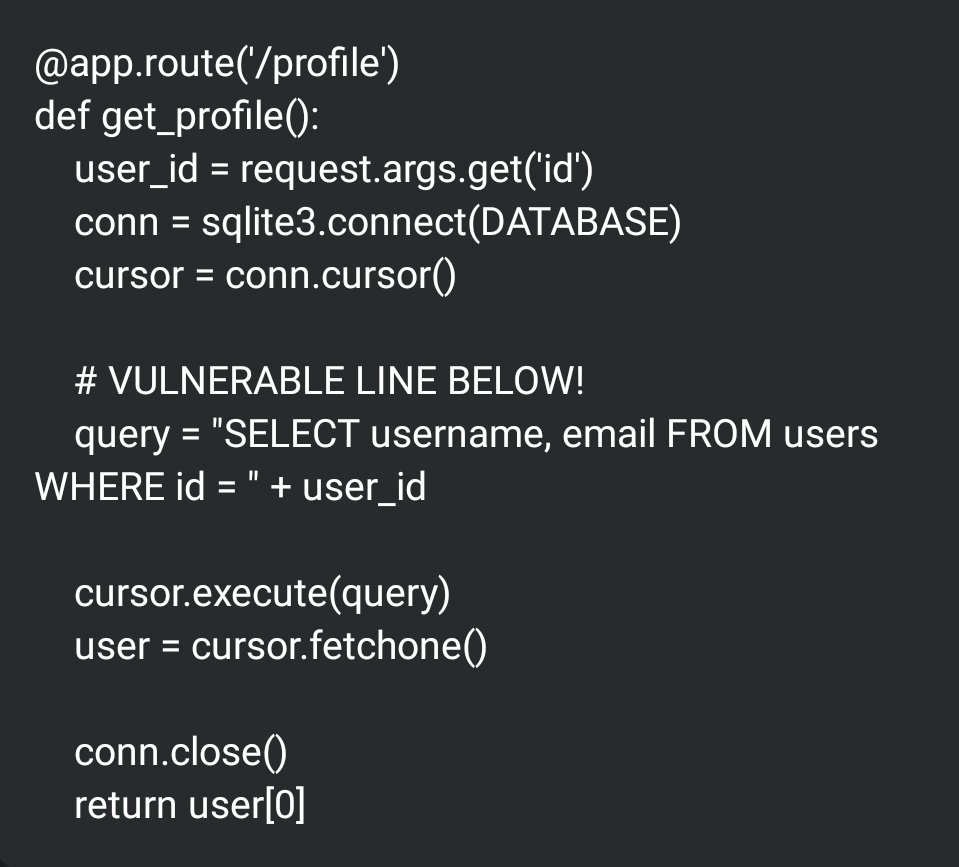
🚨 SPOT THE VULN: 3 Words. If a user enters ' OR 1=1 -- as the ID... What. Happens. Next? Find the major flaw in this Flask API. #SQLi #Flask #infosec #bugbounty #Cybersecurity #hacking
🚨 WordPress users, attention! The 'My auctions allegro' plugin (v3.6.32 & earlier) has a critical SQL Injection vulnerability. Unauthenticated attackers can steal sensitive database info! 🛡️ Update NOW to protect your site. tenable.com/cve/CVE-2025-1… #WordPressSecurity #SQLi #CVE
⚠️ WordPress: el plugin Tag, Category, and Taxonomy Manager – AI Autotagger con OpenAI (≤3.40.1) permite SQL Injection a usuarios Contributor+. CVSS 6.5. Actualiza a 3.41.0. #WordPress #Seguridad #SQLi t.me/vulnerabilityw…
⚠️ #Drupal Alert Exploited modules open #SQLi → #RCE chains that deploy 0-day malware 🛡️ Action: Audit modules and scan with Quttera’s heuristic detection engine quttera.com #CyberSecurity #Malware #WebsiteSecurity

Domina la cadena de ataque completa: SQLi ➡️ RCE ➡️ PrivEsc. Este playground en Docker te permite practicar la explotación de PostgreSQL en un entorno seguro y realista. ¡Un desafío esencial para todo pentester! Link: github.com/filipkarc/sqli… 💥🧪 #SQLi #HackingEtico #Pentest

⚠️ Website Security Alert Why it matters: Outdated plugins expose sites to #SQLi, #RCE, and #XSS exploit chains. 🛡️ Action: Enable auto-updates, remove unused components, and run regular CVE-driven vulnerability scans #CVE #CyberSecurity #Malware

𝗟𝗼𝗴𝘀𝗲𝗻𝘀𝗼𝗿 🕵🏽♂️ Herramienta en Python para descubrir paneles de login y escaneo de SQLi en formularios POST. Soporta escaneo de múltiples hosts, escaneo dirigido de formularios SQLi y proxies. 🛡️ 🌐 github.com/Mr-Robert0/Log… #Logsensor #SQLI #Pentesting #CyberSecurity…

#WooCommerce — #SQLi CVE in Payment Extensions 🚨 Why it matters: SQL injection in WooCommerce payment add-ons can leak customer info, alter orders, and inject malicious scripts 🛡️ Action: Block SQLi attempts and scan your store for injected code quttera.com #CVE…

Just bypassed the admin login in a PortSwigger lab using classic SQLi 😎 Payload: admin' OR '1'='1-- No sanitization = full authentication bypass. Burp Repeater FTW 💥 #CyberSecurity #SQLi #BugBounty #WebSecurity

#PrestaShop — Payment Form Injection via SQLi 🚨 Why it matters: SQL injection in outdated PrestaShop plugins injects fake payment forms and steals customer info 🛡️ Action: Use Quttera Malware Scanner to detect injected forms early quttera.com/website-malwar… #Malware #SQLi…

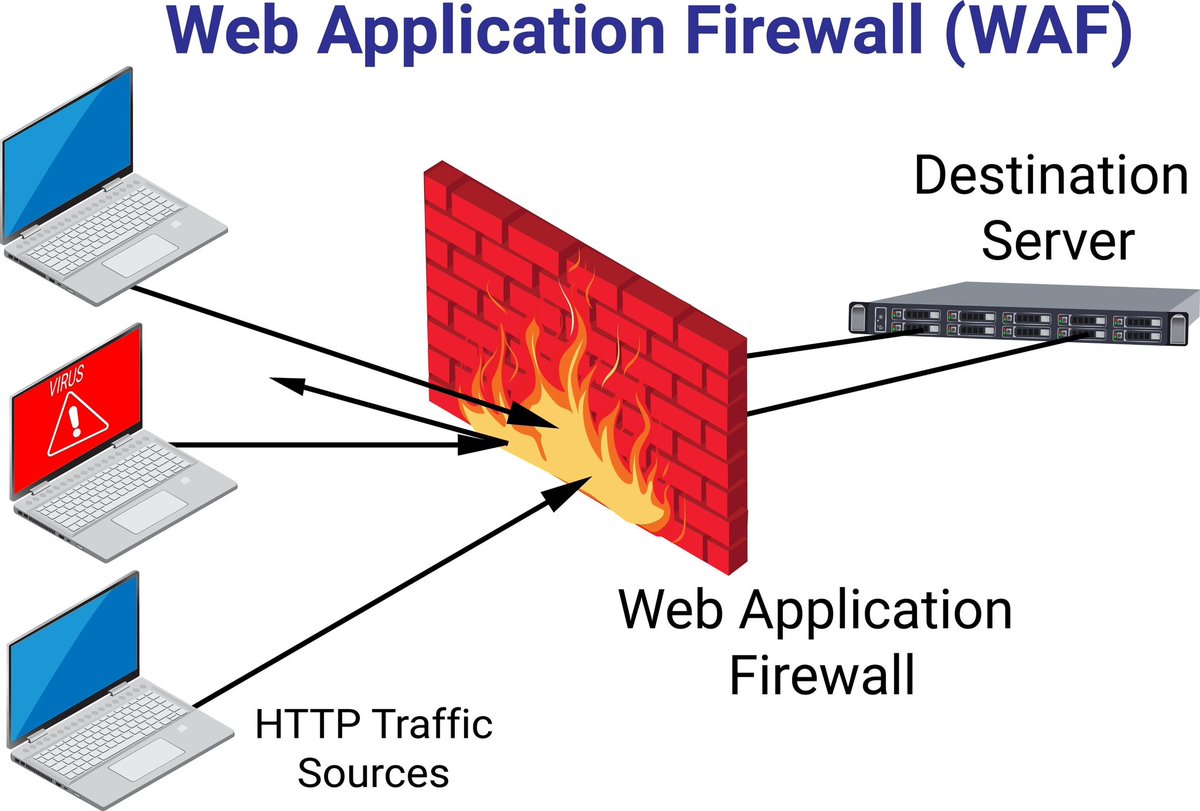
#WordPress — SQL Injection → Malware Deployment 🚨 Why it matters: #SQLi injects malware directly into core WP database tables 🛡️ Action: Block attacks with Quttera WAF and protect your perimeter quttera.com/web-applicatio… #CVE #CyberSecurity

The one defense against SQL Injection that still works 99% of the time? Parameterized Queries. They teach the database to treat user input as DATA, not executable CODE. Stop using string concatenation for queries! #SQLi #AppSec #HackingTip #CyberSecurity

Null Byte SQL injection attempt today for registration from a Russian IP. Thought to share because I found it interesting. HF backend handled it properly. #sqli

Basic Detection Start with simple URL testing: sqlmap -u "site.com/page?id=1" For POST requests: sqlmap -u "site.com/login" --data="user=admin&pass=test" #SQLi #PenetrationTesting
🚨WordPress Alert Why it matters: WordPress plugins targeted by SQL Injection can expose your entire database 🛡️ Action: Scan with WordPress Malware Scanner to detect injected queries early quttera.com/wordpress-malw… #WordPress #SQLi #Quttera #CyberSecurity #InfoSec

Something went wrong.
Something went wrong.
United States Trends
- 1. Villa 146K posts
- 2. Arteta 26.3K posts
- 3. #AVLARS 12.3K posts
- 4. Saliba 12.2K posts
- 5. namjoon 143K posts
- 6. Odegaard 11K posts
- 7. Unai Emery 8,911 posts
- 8. Good Saturday 30.2K posts
- 9. Hincapie 10.5K posts
- 10. GAME DAY 33.1K posts
- 11. #MeAndTheeSeriesEP4 922K posts
- 12. Merino 23.9K posts
- 13. Trossard 19.1K posts
- 14. Gyokeres 13.1K posts
- 15. #SaturdayVibes 3,613 posts
- 16. #Caturday 3,007 posts
- 17. #Arsenal 4,712 posts
- 18. Saka 43K posts
- 19. The EU 422K posts
- 20. Buendia 14.8K posts













