#securecoding search results
El #OWASP Top 10 versión 2025 RC1 es una guía esencial para desarrolladores y profesionales de la #ciberseguridad. Resume el consenso global sobre las vulnerabilidades más críticas que deben abordarse para proteger los sistemas ante amenazas reales #SecureCoding #WebSecurity ↘️

Building security into every line of code. @PieterDanhieux from @SecCodeWarrior joins @ashimmy to discuss how AI is reshaping development, the new risks it introduces, and why mastering secure coding is more important than ever. Watch: buff.ly/uQ7TG3g #AI #SecureCoding
"There are some things that are too sensitive to exist". This is such a powerful and important statement. Really interesting chat with Mike Loewy from TideCloak #DevSecOps #SecureCoding #SoftwareSecurity #AppSec
I’m excited to share that I have officially passed the "Certified Security Code Review – Beginners (CSCRB)" certificate exam, issued by Red Team Leaders (RTL). #CyberSecurity #SecureCoding #CodeReview #AppSec #CSCRB #EthicalHacking #SecurityByDesign #OWASP #VAPT

Security starts at line one. 💻 @beyond__tech Protocol adheres to strict Secure Development Practices, including mandatory code reviews and security-focused development frameworks. Building defense into the DNA of the protocol from day one. #SecureCoding #DevSecOps

We just launched the SecDim Patch Reward System. Review patches, give feedback, level up your skills, and earn bonus score. A new community-driven way to grow as a security-minded developer. Check it out: 👉 secdim.com/news/secdim-pa… #appsec #securecoding #programming

#AI tools can generate code in seconds, but can expose your apps. In this week’s AI/LLM Security Intro Series: 💻 How unvalidated AI outputs = vulnerabilities ⚙️ Examples + #SecureCoding tips 🛡️ Best practices for reviewing 🎥 Full video on YouTube: youtu.be/1hpiF_A6c7E
Vibe Coding Will Get You HACKED (Here's the Fix) Thank you to @ThreatLocker for sponsoring this video and my trip to Black Hat USA 2025! #blackhat #threatlocker #securecoding
Stop Trusting Input: 3 RULES Thank you to ThreatLocker for sponsoring this video and my trip to Black Hat USA 2025. #securecoding #threatlocker #blackhat
Most breaches still come down to bad code. 😬 This demo shows how teams are changing that—by giving devs hands-on practice in real tools like VS Code. Short, standards-aligned training. Real impact. ▶️ sans.org/u/1D14 #DevSecOps #SecureCoding

Super smart! TideClock co-founder Mike Loewy on the academic principles behind why ineffable cryptography works. #DevSecOps #SecureCoding #SoftwareSecurity #AppSec
Embracing the idea that we can share evidence (a key fragment was used) without ever having to share the key fragment. Digging into ineffable crypto chat with Mike Loewy from TideCloak #DevSecOps #SecureCoding #SoftwareSecurity #AppSec
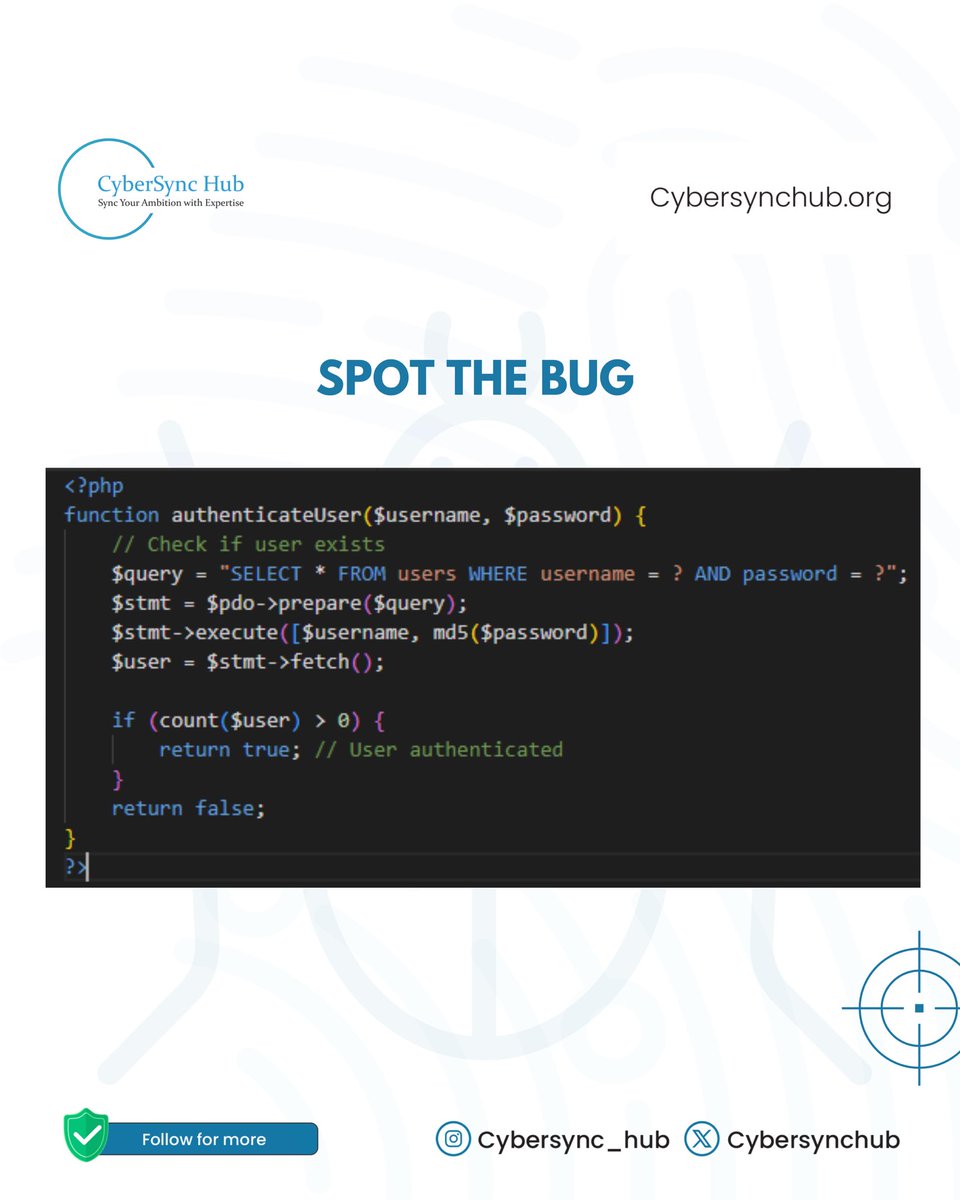
🐛 SPOT THE BUG CHALLENGE 🐛 Can you identify the critical vulnerability in this PHP authentication function? Drop your answer in the comments! 👇 #CyberSecurity #SecureCoding #PHP #Authentication #SpotTheBug #InfoSec #CyberSyncHub
☕️ Java cumple 30 años y yo fui testigo desde el “Hello, World!” del SDK 1.2 Fui dev, arquitecto y también instructor certificado por Sun y Oracle. Java no solo cambió el desarrollo: Cambió mi vida. Gracias por 30 años de café, comunidad y código. #Java30 #SrJava #SecureCoding

🛡️Strengthen your #SecureCoding skills! Join the Workshop on Secure Coding Practices by STPI Thiruvananthapuram & LDRA 📅28 Oct 2025 | 🕙10 AM–4 PM 📍Technopark,Thiruvananthapuram Learn #CERTC standards, secure design, and compliance tools. #STPI #CyberSecurity #NCSAM2025 #LDRA

Moving to passwordless/ineffable cryptography-based IAM in just one SDK 🤯 Fascinating chat with Mike Loewy from TideCloak about overcoming the key problem. #DevSecOps #SecureCoding #SoftwareSecurity #AppSec
4. Code Quality vs Code Speed Yes, AI helps write more code quickly, but not always better code. The study found AI-written code had a higher chance of being inefficient or insecure if used blindly. Review remains essential. #CleanCode #SecureCoding #AIDevTools

This is how you use SAST findings to upskill developers in security, right in your Claude IDE. Brought to you by @dryrunsec + @secdim #sast #training #securecoding
🤖 #AI systems are gaining autonomy — but what happens when they act beyond their intended scope? This week’s episode: Excessive Agency – Controlling AI Autonomy Risks. 🎥 Watch the full episode: youtu.be/2xaLDa2J6sE #LLMSecurity #SecureCoding #AIgovernance #SecureDevelopment
AI speeds up code, but security comes from you. Master Secure Java Development — become the layer AI can’t replace. 🔐⚡ #JavaDeveloper #CyberSecurity #SecureCoding #AIinTech #JavaSecurity #DevSecOps #AIxDeveloper #CodeSmart #TechInnovation #PrinceMonga

Coding, Languages and Oracle. - petefinnigan.com/weblog/archive… - #oracleace #securecode #securecoding #plsql

#Ciberseguranca #SecureCoding #DevSecOps #Programacao #Cybersecurity #InfoSec #DesenvolvimentoSeguro
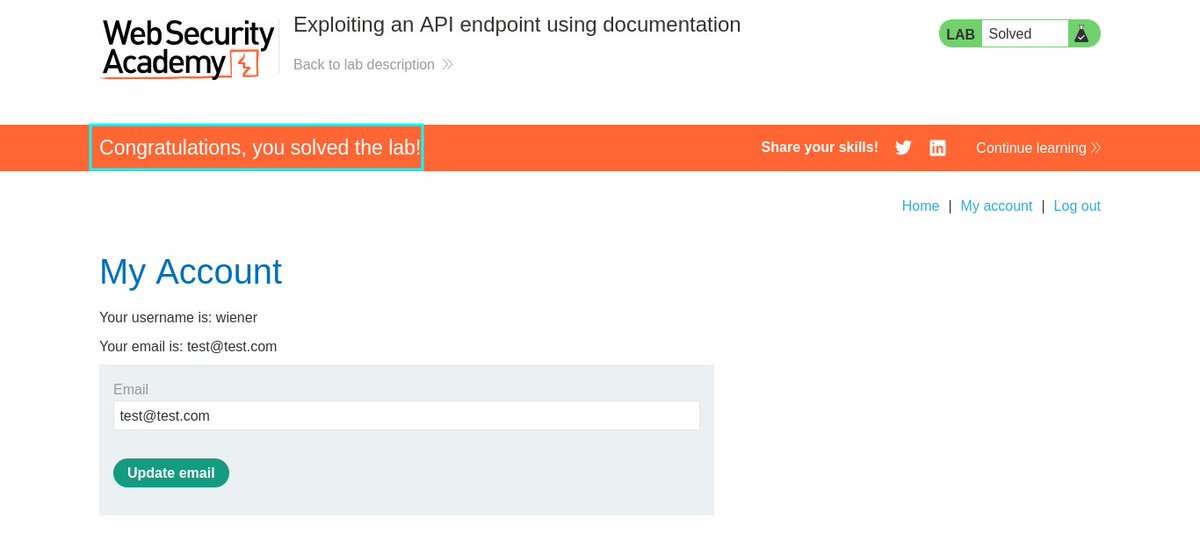
🎉 Lab Success: All because the API documentation was exposed publicly. 🔐 Lesson: APIs aren’t just backend endpoints. They’re potential entry points. Protect your docs, and protect your data. #WebSecurity #SecureCoding #PortSwigger #APIExploitation #CyberAwareness
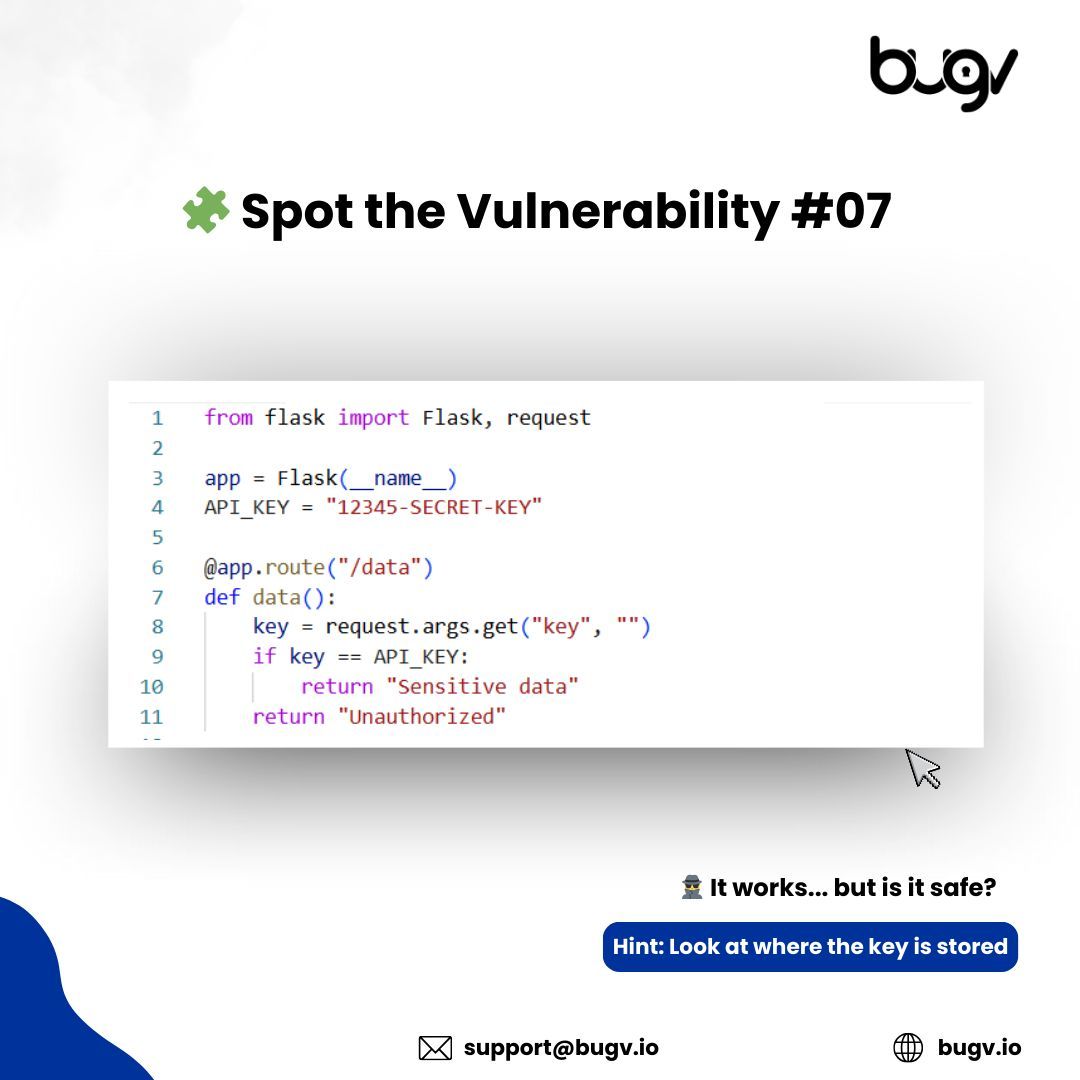
𝗖𝗮𝗻 𝗼𝗻𝗲 𝗹𝗶𝗻𝗲 𝗰𝗼𝗺𝗽𝗿𝗼𝗺𝗶𝘀𝗲 𝗮𝗻 𝗲𝗻𝘁𝗶𝗿𝗲 𝘀𝘆𝘀𝘁𝗲𝗺? 𝗬𝗲𝘀 𝗮𝗻𝗱 𝗵𝗲𝗿𝗲’𝘀 𝗽𝗿𝗼𝗼𝗳. What’s the vulnerability you see here? Drop your answer in the comments. #CyberSecurity #SecureCoding #AppSec #InfoSec #BugBounty #RiskManagement #DevSecOps
🚫 Stop blacklisting tokens manually! Learn smarter strategies for token revocation using Spring Security. #SecureCoding
Developers often overlook how prompts can introduce vulnerabilities. Here’s why insecure prompt handling matters and what to watch for. redsecuretech.co.uk/blog/post/inse… #CyberSecurity #SecureCoding #PromptSecurity #DevSecOps #InsecureCode #InputValidation

Our 2025 Seasonal Recap is live: big features, big releases, big year for SecDim. 👉 Read it: secdim.com/news/season-re… 🎉 Black Friday: 35% off Pro Membership runs untl Dec 4, 23:59 AEDT. #appsec #securecoding #blackfriday

Step 2: Hackers tunnel via Panama VPN to mask IP, pivot to core banking server. ₹11.55 Cr siphoned in 48 hrs. Indian banks: Enable geo-fencing NOW. Lesson: Log all VPN traffic in your endpoints. #SecureCoding #prasunchakra
Step 1: Victim installs fake "HimPaisa" app (malware disguised as legit). It grabs OTPs & session tokens. Boom—remote access to bank API. Lesson: Always verify app signatures before pushing to Play Store! #SecureCoding
On November 26, 2024, a critical XSS vulnerability was detected in Copilot Studio, CVE-2024-49038. We made challenges inspired by this incident, they are available for a limited time in our Weekly Incident Game. 👉 secdim.com/news/xss-in-co… #appsec #securecoding #microsoft

I’m excited to share that I have officially passed the "Certified Security Code Review – Beginners (CSCRB)" certificate exam, issued by Red Team Leaders (RTL). #CyberSecurity #SecureCoding #CodeReview #AppSec #CSCRB #EthicalHacking #SecurityByDesign #OWASP #VAPT

El #OWASP Top 10 versión 2025 RC1 es una guía esencial para desarrolladores y profesionales de la #ciberseguridad. Resume el consenso global sobre las vulnerabilidades más críticas que deben abordarse para proteger los sistemas ante amenazas reales #SecureCoding #WebSecurity ↘️

🫶 Huge thanks to @shehackspurple for joining us at #BlackHat booth 3261 yesterday! She spoke with attendees about her essential book: Alice & Bob Learn #SecureCoding. Go Tanya 💯



We just launched the SecDim Patch Reward System. Review patches, give feedback, level up your skills, and earn bonus score. A new community-driven way to grow as a security-minded developer. Check it out: 👉 secdim.com/news/secdim-pa… #appsec #securecoding #programming

Security starts at line one. 💻 @beyond__tech Protocol adheres to strict Secure Development Practices, including mandatory code reviews and security-focused development frameworks. Building defense into the DNA of the protocol from day one. #SecureCoding #DevSecOps


Insecure (de)serialization in Go (encoding/gob) by overwriting a field that cause encoder to confuse, use a lot of CPU and result in stack-overflow. If you develop a backend service, you must choose Go, when you care about security. #securecoding #challenge #go

4. Code Quality vs Code Speed Yes, AI helps write more code quickly, but not always better code. The study found AI-written code had a higher chance of being inefficient or insecure if used blindly. Review remains essential. #CleanCode #SecureCoding #AIDevTools

Is "whitelisted IPs" just the bouncer keeping unwanted hosts out at DigitalOcean's nightclub? Source: devhubby.com/thread/how-to-… #SecureCoding #Deployment #TechTips #CodeNewbie #digitalocean #set

Most breaches still come down to bad code. 😬 This demo shows how teams are changing that—by giving devs hands-on practice in real tools like VS Code. Short, standards-aligned training. Real impact. ▶️ sans.org/u/1D14 #DevSecOps #SecureCoding

🛡️Strengthen your #SecureCoding skills! Join the Workshop on Secure Coding Practices by STPI Thiruvananthapuram & LDRA 📅28 Oct 2025 | 🕙10 AM–4 PM 📍Technopark,Thiruvananthapuram Learn #CERTC standards, secure design, and compliance tools. #STPI #CyberSecurity #NCSAM2025 #LDRA

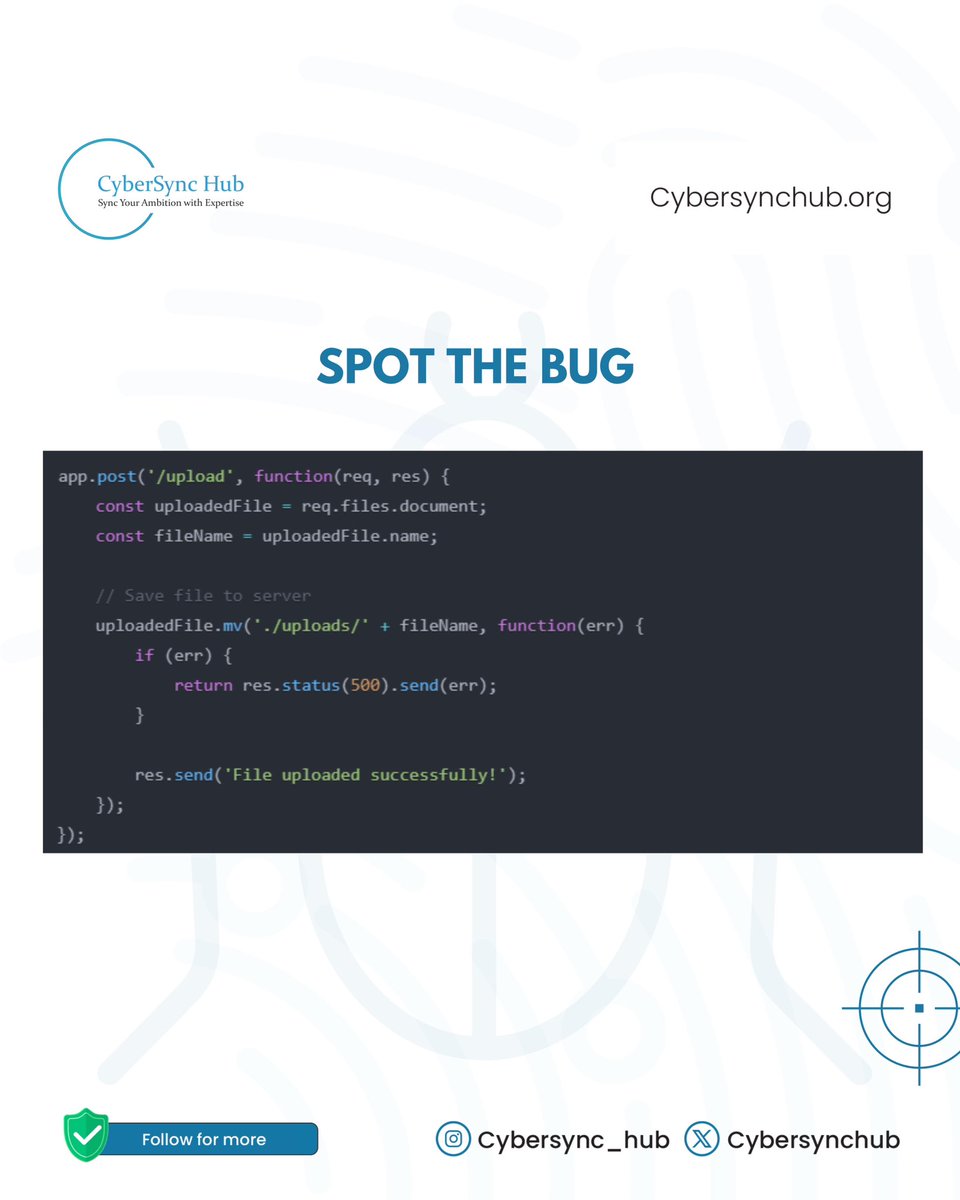
Can you find the security vulnerability in this code? Take a look and share your thoughts in the comments #DevSecOps #AppSec #SecureCoding #LearnCybersecurity #CyberSyncHub #TechLiteracy #CyberSecurity
Datei-Uploads in #Java sicher machen? Schütze dich vor: - CWE-22 (Path Traversal) - CWE-377 (Temp File Risks) - CWE-778 (Insufficient Logging) Baue mit @SvenRuppert & #Vaadin sichere Datei-Apps – inkl. NIO, Logging & Security-Fokus: javapro.io/de/erstellen-e… #SecureCoding #CWE

Ready for real ROI from #AppSec? 🚀 Paysafe boosted developer productivity by 45%, cut early vulnerabilities & topped the SCW Trust Score® Financial benchmark with our #securecoding program. Build a lasting developer-driven security culture! Learn how: ow.ly/VFhe50Xc48k

My friend Yabing Wang and I are doing a fireside chat about MODERN #AppSec. Yabing wrote '97 things an appsec professional needs to know', she's a CISO, and a great conversation partner! July 2nd at 9AM PT 🚀 twp.ai/ImoSyK @justworks #SecureCoding

Most breaches still come down to bad code. 😬 This demo shows how teams are changing that—by giving devs hands-on practice in real tools like VS Code. Short, standards-aligned training. Real impact. ▶️ sans.org/u/1D14 #DevSecOps #SecureCoding

Secure Vibe Coding: The Complete New Guide dlvr.it/TM1hfv #SecureCoding #AICoding #CyberSecurity #VibeCoding #AI

🛡️ New to API security? This beginner-friendly guide from @massimo_nardone walks you through securing #RESTful APIs with real-world examples—no fluff, just practical solutions. 📚 #APIDevelopment #SecureCoding #WebSecurity #Java #RESTAPI #DevTips 🔗 ow.ly/peez50Wf7Ts

Your backlog called. It said: “I'm full of stuff we could’ve caught upstream.” 🙄 Turns out, secure code training in the dev workflow prevents a lot of that. 👉 sans.org/u/1D14 #DevSecOps #SecureCoding


OWASP Secure Coding Practices Checklist👇 Link: 0xkayala.github.io/OWASP-Secure-C… #OWASPSecureCodingChecklist #OWASP #SecureCoding #Checklist #SecureCodingChecklist

Something went wrong.
Something went wrong.
United States Trends
- 1. #AEWDynamite 19.4K posts
- 2. Giannis 77.6K posts
- 3. #Survivor49 2,558 posts
- 4. #TheChallenge41 1,947 posts
- 5. Ryan Leonard N/A
- 6. Jamal Murray 5,507 posts
- 7. Claudio 28.7K posts
- 8. #TusksUp N/A
- 9. Ryan Nembhard 3,305 posts
- 10. Kevin Overton N/A
- 11. Will Wade N/A
- 12. #ALLCAPS 1,183 posts
- 13. Steve Cropper 4,756 posts
- 14. Tyler Herro 1,722 posts
- 15. Achilles 5,298 posts
- 16. Dark Order 1,748 posts
- 17. Yeremi N/A
- 18. Bucks 51.9K posts
- 19. Orlov N/A
- 20. Toluca 7,680 posts

































