#securecoding ผลการค้นหา
Jaime Jorge, CEO of @codacy, warns that exploiting vulnerabilities in AI-generated code is becoming a game. In his chat with @Richard Stiennon, Jorge explains that this isn’t just a tech issue; it is a mindset shift. 👉EM360TECH.short.gy/j1H6mJ #AIinDevOps #SecureCoding #EM360Tech
🛡️Strengthen your #SecureCoding skills! Join the Workshop on Secure Coding Practices by STPI Thiruvananthapuram & LDRA 📅28 Oct 2025 | 🕙10 AM–4 PM 📍Technopark,Thiruvananthapuram Learn #CERTC standards, secure design, and compliance tools. #STPI #CyberSecurity #NCSAM2025 #LDRA

Stop Trusting Input: 3 RULES Thank you to ThreatLocker for sponsoring this video and my trip to Black Hat USA 2025. #securecoding #threatlocker #blackhat
🫶 Huge thanks to @shehackspurple for joining us at #BlackHat booth 3261 yesterday! She spoke with attendees about her essential book: Alice & Bob Learn #SecureCoding. Go Tanya 💯



🦇 The battle begins. Meet Promptgeist Prime – the LLM monster that poisons your data & flips your context. 🎥 Watch the teaser (no spoilers here!) 👉 Full walkthrough: youtu.be/ed_zZzkcL14 👾 Join #Cybermon2025 & prove your #securecoding skills. #LLMSecurity
👾 Just 11 days until #Cybermon2025 kicks off! This year brings Cybermon Prime – AI-powered boss levels for devs ready to level up. Are you up for the challenge? Learn more: ow.ly/CBsX50X1RG4 #AppSec #SecureCoding #CyberSecurityAwarenessMonth
☕️ Java cumple 30 años y yo fui testigo desde el “Hello, World!” del SDK 1.2 Fui dev, arquitecto y también instructor certificado por Sun y Oracle. Java no solo cambió el desarrollo: Cambió mi vida. Gracias por 30 años de café, comunidad y código. #Java30 #SrJava #SecureCoding

🤖🚫 AI-powered "vibe coding" promises speed, but it's risky when developers treat AI output as fact. In @CSOonline, our CTO @mmadou warns that skipping review of generated code is a fast track to insecure code. Read more: ow.ly/859550XaHhn #AICoding #SecureCoding
🎮 Countdown starts now: 20 days to go! #Cybermon2025: The Age of AI launches Oct 6. Face off against monsters inspired by real-world vulnerabilities & sharpen your #securecoding skills. #CyberSecurityAwarenessMonth
#Securecode lovers! 👋 We've launched tons of new learning content & features on the SCW platform: AI Challenges, AI Security Rules on GitHub, Quests innovations, Vulnerability Insights & more. Ready to increase your #securecoding posture? Request a demo: ow.ly/aEkT50WQEsK
4. Code Quality vs Code Speed Yes, AI helps write more code quickly, but not always better code. The study found AI-written code had a higher chance of being inefficient or insecure if used blindly. Review remains essential. #CleanCode #SecureCoding #AIDevTools

Security isn't something that happens TO your code—it's something that happens IN your code. The best developers take ownership of security from design through deployment. How do you make security part of your development identity? #SecureCoding #DeveloperOwnership #CodeQuality

This is how you use SAST findings to upskill developers in security, right in your Claude IDE. Brought to you by @dryrunsec + @secdim #sast #training #securecoding
⏳ One week left! #Cybermon2025 arrives Oct 6. ⚡ Fun, fast, hands-on #SecureCoding activities 🕒 Just 20–30 mins per week 👾 New monsters every Monday Ready to battle? Learn more: ow.ly/HYJl50X3UuF #CyberSecurityAwarenessMonth
Vibe Coding Will Get You HACKED (Here's the Fix) Thank you to @ThreatLocker for sponsoring this video and my trip to Black Hat USA 2025! #blackhat #threatlocker #securecoding
10,000+ secure code learning activities — powered by this crew. Here’s how we celebrated behind the scenes → #10KLessons #SecureCoding #Cybersecurity #WeAreSCW
What’s the #1 piece of advice Michael Howard gives developers about security? In this #OneDevQuestion, he explains why every input should be questioned. Learn more: msft.it/6017sOucJ #AppSec #SecureCoding
🚨 #AICoding tools boost productivity but can hide security risks. Learn how to get complete visibility & control over AI-assisted coding to keep your software secure. Eliminate #ShadowAI risk & empower #SecureCoding! Read the blog: ow.ly/pOPt50X7Yhu
Jaime Jorge, CEO of @codacy, warns that exploiting vulnerabilities in AI-generated code is becoming a game. In his chat with @Richard Stiennon, Jorge explains that this isn’t just a tech issue; it is a mindset shift. 👉EM360TECH.short.gy/j1H6mJ #AIinDevOps #SecureCoding #EM360Tech
🤖🚫 AI-powered "vibe coding" promises speed, but it's risky when developers treat AI output as fact. In @CSOonline, our CTO @mmadou warns that skipping review of generated code is a fast track to insecure code. Read more: ow.ly/859550XaHhn #AICoding #SecureCoding
🦇 The battle begins. Meet Promptgeist Prime – the LLM monster that poisons your data & flips your context. 🎥 Watch the teaser (no spoilers here!) 👉 Full walkthrough: youtu.be/ed_zZzkcL14 👾 Join #Cybermon2025 & prove your #securecoding skills. #LLMSecurity
Google’s CodeMender AI has fixed 70+ security flaws in open-source code—fast, autonomous, and proactive. Powered by Gemini models, it’s reshaping secure coding. Would you trust AI to patch your code? #AvmConsulting #CodeMender #SecureCoding #AIInnovation

🛡️Strengthen your #SecureCoding skills! Join the Workshop on Secure Coding Practices by STPI Thiruvananthapuram & LDRA 📅28 Oct 2025 | 🕙10 AM–4 PM 📍Technopark,Thiruvananthapuram Learn #CERTC standards, secure design, and compliance tools. #STPI #CyberSecurity #NCSAM2025 #LDRA

🚨 #AICoding tools boost productivity but can hide security risks. Learn how to get complete visibility & control over AI-assisted coding to keep your software secure. Eliminate #ShadowAI risk & empower #SecureCoding! Read the blog: ow.ly/pOPt50X7Yhu
Avoid insecure deserialization: never trust serialized objects from clients. Prefer safe formats (JSON), sign payloads, and whitelist types. #AppSec #Deserialization #SecureCoding #Pentesting




Want to learn all the best security features of Vue.js? Download my free cheat sheet and sign up for my newsletter at the same time! #vuejs #appsec #securecoding twp.ai/ImpwZv

Developers struggle with AI-generated code full of bugs & risks—CodeMender flips the script with autonomous, rock-solid security fixes that don’t break your app. This could change how we trust AI and protect our data forever #AIEthics #SecureCoding
🚀 It’s here! #Cybermon2025: The Age of AI starts today. 👾 Battle vulnerabilities ⚡ Conquer Cybermon Prime 🏆 Become a Cyberhero Join devs worldwide this #CyberSecurityAwarenessMonth. Where to find it: ow.ly/Ak0r50X7mVn #SecureCoding #AppSec
Never trust user input — even JSON. Always validate and sanitize using whitelists, not blacklists. Framework validation ≠ full protection. #CyberSecurityMonth #InputValidation #SecureCoding
🛡️Strengthen your #SecureCoding skills! Join the Workshop on Secure Coding Practices by STPI Thiruvananthapuram & LDRA 📅28 Oct 2025 | 🕙10 AM–4 PM 📍Technopark,Thiruvananthapuram Learn #CERTC standards, secure design, and compliance tools. #STPI #CyberSecurity #NCSAM2025 #LDRA

🫶 Huge thanks to @shehackspurple for joining us at #BlackHat booth 3261 yesterday! She spoke with attendees about her essential book: Alice & Bob Learn #SecureCoding. Go Tanya 💯



☕️ Java cumple 30 años y yo fui testigo desde el “Hello, World!” del SDK 1.2 Fui dev, arquitecto y también instructor certificado por Sun y Oracle. Java no solo cambió el desarrollo: Cambió mi vida. Gracias por 30 años de café, comunidad y código. #Java30 #SrJava #SecureCoding

Security isn't something that happens TO your code—it's something that happens IN your code. The best developers take ownership of security from design through deployment. How do you make security part of your development identity? #SecureCoding #DeveloperOwnership #CodeQuality

Is "whitelisted IPs" just the bouncer keeping unwanted hosts out at DigitalOcean's nightclub? Source: devhubby.com/thread/how-to-… #SecureCoding #Deployment #TechTips #CodeNewbie #digitalocean #set


Attacking PHP Application Read more on our blog at blog.devsecopsguides.com/attacking-php Attacking NodeJS Application: Attacking APIs: Attacking Docker Container: #php #securecoding #appsec #devsecopsguides

Attacking Docker Container Read more on our blog at blog.devsecopsguides.com/attacking-dock… Attacking AWS: Secure Coding Cheatsheets: #docker #container #aws #cloud #bucket #ec2 #iam #appsec #devops #DevSecOps

Insecure (de)serialization in Go (encoding/gob) by overwriting a field that cause encoder to confuse, use a lot of CPU and result in stack-overflow. If you develop a backend service, you must choose Go, when you care about security. #securecoding #challenge #go

4. Code Quality vs Code Speed Yes, AI helps write more code quickly, but not always better code. The study found AI-written code had a higher chance of being inefficient or insecure if used blindly. Review remains essential. #CleanCode #SecureCoding #AIDevTools

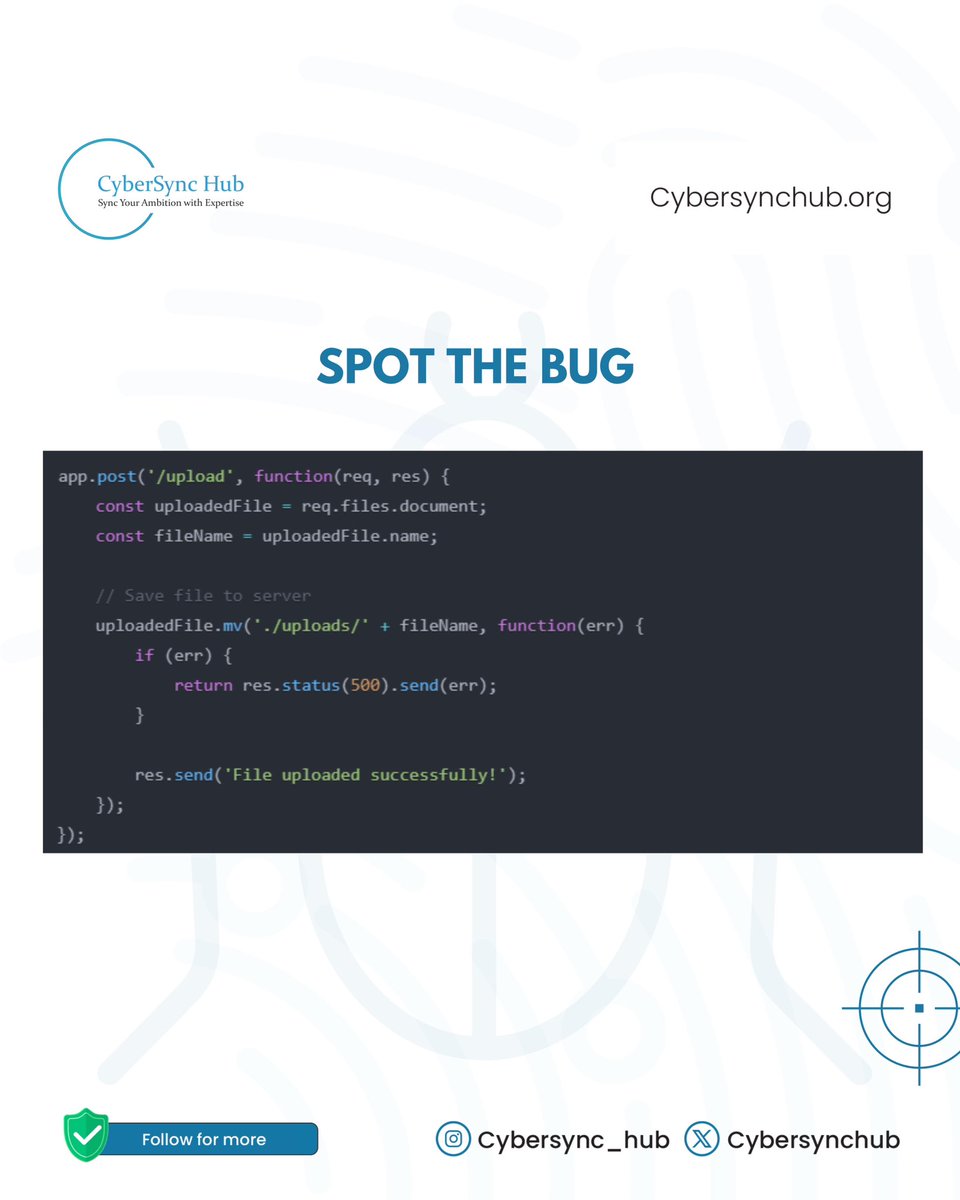
Can you find the security vulnerability in this code? Take a look and share your thoughts in the comments #DevSecOps #AppSec #SecureCoding #LearnCybersecurity #CyberSyncHub #TechLiteracy #CyberSecurity
Hashing collisions are a serious threat! 🚨 Our new video explains the "Birthday Problem" & how it can be exploited. 🤖 Learn to defend your code: ow.ly/2XFL50VnwCG #hashing #securecoding #cybersecurity

One does not simply patch security after deployment. Know how to secure code from the start with this ebook! ➡️ store.expliot.io/products/the-e… #infosec #securecoding #cybersecurity

🔐 Want to build secure Vue.js apps? In our latest blog, we’ve listed 5 essential security practices—from XSS prevention to safe data handling. 👇 🔗 resources.s4e.io/blog/5-essenti… #VueJS #CyberSecurity #SecureCoding #S4E #CTEM

#OnlineTraining 🚨 1 Day Left! Ready to build secure, AI-powered software? Join our certification program and get hands-on with AI Security & SSDLC essentials. 🔐 Learn. Build. Secure the future. 👉 Register now: docs.google.com/forms/d/e/1FAI… #SecureCoding #AIinSecurity…

Datei-Uploads in #Java sicher machen? Schütze dich vor: - CWE-22 (Path Traversal) - CWE-377 (Temp File Risks) - CWE-778 (Insufficient Logging) Baue mit @SvenRuppert & #Vaadin sichere Datei-Apps – inkl. NIO, Logging & Security-Fokus: javapro.io/de/erstellen-e… #SecureCoding #CWE

👩💻 Your daily npm pull may carry unexpected risks! The malicious npm attack impacted 18 packages with 2.6B downloads weekly. IT admins, find out how the infection propagates & steps to mitigate it. 🚨 #hacking #securecoding #NetworkSecurity #NPM bit.ly/4psy8ER

OWASP Secure Coding Practices Checklist👇 Link: 0xkayala.github.io/OWASP-Secure-C… #OWASPSecureCodingChecklist #OWASP #SecureCoding #Checklist #SecureCodingChecklist

Shifting left means catching vulnerabilities early, right in your DevOps pipeline. Find out how it strengthens your pipeline: blog.checkpoint.com/infinity-globa… #DevSecOps #SecureCoding #cybersecurity

#AIcoding tools are incredible helpers -- until attackers turn them against you. In @DEVOPSdigest, our CTO @mmadou explores how AI-assisted development can be exploited & why #securecoding practices are more important than ever: ow.ly/R1g850WyOvU

SecDim values community contributions. Challenges from AppSec Village at DEF CON 33 are featured in our Weekly Incident game for those missed it. Thanks again to @zi0Black and @Becojo for their contributions 👉 play.secdim.com/game/weekly-in… #appsec #programming #securecoding

Something went wrong.
Something went wrong.
United States Trends
- 1. Happy Birthday Charlie Kirk 7,756 posts
- 2. #Worlds2025 20.8K posts
- 3. Bears 90.9K posts
- 4. Jake Moody 14.1K posts
- 5. Falcons 52.3K posts
- 6. Blake Snell 17.2K posts
- 7. Josh Allen 27.3K posts
- 8. Caleb 50.4K posts
- 9. Joji 33.3K posts
- 10. Jayden 23.2K posts
- 11. #BearDown 2,424 posts
- 12. Commanders 53.1K posts
- 13. Ben Johnson 4,524 posts
- 14. Swift 292K posts
- 15. #Dodgers 15.6K posts
- 16. Treinen 4,748 posts
- 17. Turang 4,420 posts
- 18. Roki 6,192 posts
- 19. Bijan 33.8K posts
- 20. #RaiseHail 8,475 posts