#securityascode ผลการค้นหา
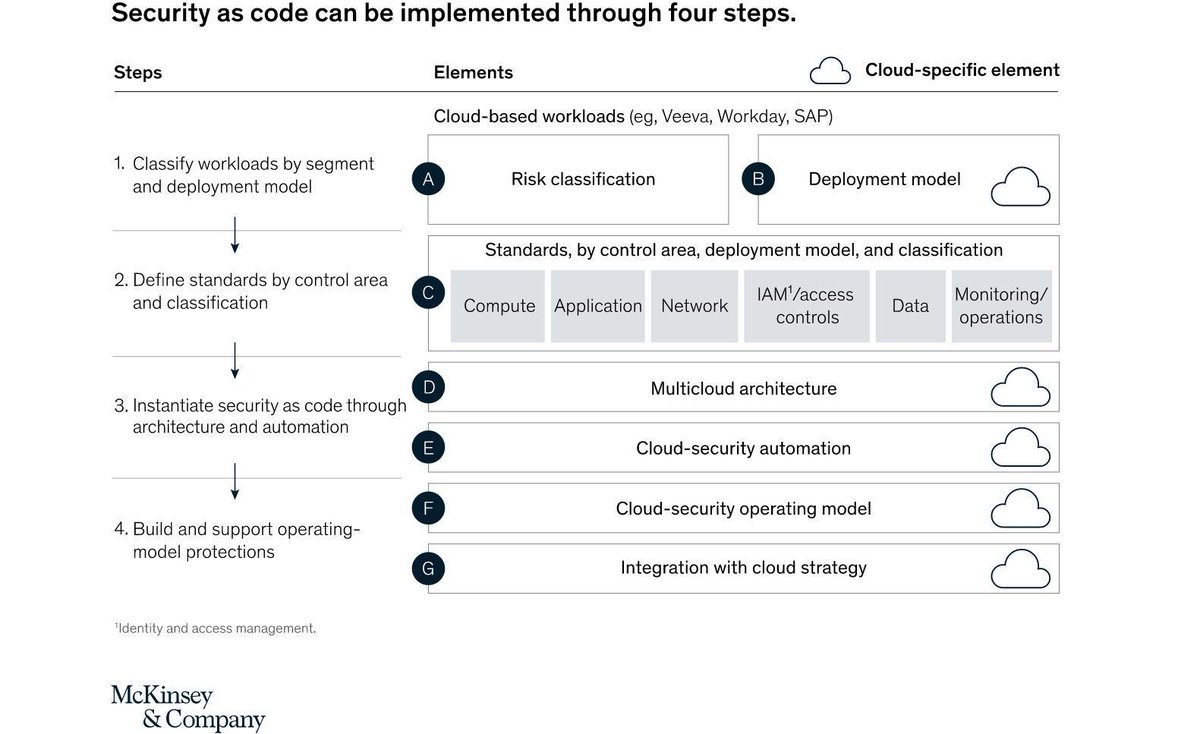
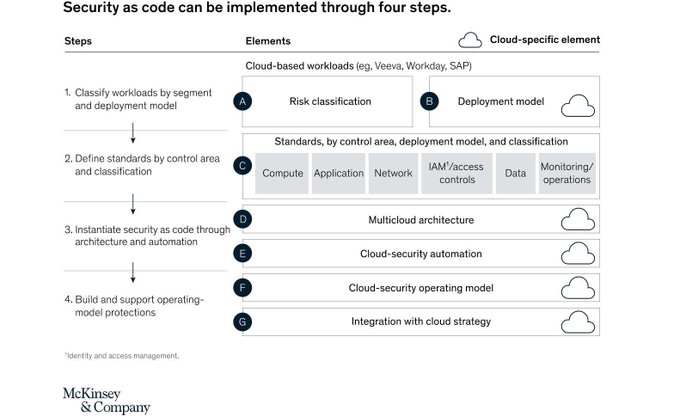
The Security as Code framework defines how the company's operating model must change to extract the full benefits of cloud adoption. Source @McKinsey Link mck.co/3kWGPse rt @antgrasso #CloudComputing #CyberSecurity #SecurityasCode

Secret scanning saved my team once. We almost pushed AWS keys to GitHub. Security-as-code isn’t buzz—it's survival. Automate it before your interns make you famous on Reddit 😅 #DevSecOps #SecurityAsCode #CloudSecurity
Security-as-code is just DevOps growing up. No more PDFs of 'guidelines'. Your pipeline enforces them, every commit, every deploy. #DevSecOps #SecurityAsCode #Automation
IBM says 25% of #cyberattacks in 2022 involved the exploitation of public-facing applications. Reduce your web app risks with #SecurityAsCode. hubs.la/Q01DdNlD0

Enhance Your CI/CD Pipeline with Security as Code #CICDSecurity #SecurityAsCode #DevOps #ContinuousMonitoring #VulnerabilityManagement #Automation #Collaboration #SoftwareSecurity #RealTimeDetection #Cybersecurity
New research shows half of Java & .NET #application flaws still impact the apps after 243 days & 158 days, respectively. Waratek fixes flaws in minutes, not months. Take a guided tour of #SecurityAsCode now. hubs.la/Q01ygJc10

#SecurityAsCode can empower businesses to more proactively protect themselves and their data. Learn how: bit.ly/3UFHJuH

The Security as Code framework defines how the company's operating model must change to extract the full benefits of cloud adoption. @McKinsey Link mck.co/3kWGPse rt @antgrasso #CloudComputing #CyberSecurity #SecurityasCode

What does it cost to fix a #vulnerability the traditional way? Save time & money with Waratek's #SecurityAsCode solution that patches flaws in minutes, not months. hubs.la/Q01BZ48Z0

What is Security as Code (SaC)? Read Here: infosec-train.blogspot.com/2024/01/what-i… #SecurityAsCode #SaC #Cybersecurity #InfoSec #CyberSecInsights #SecurityTrends #SecurityInnovation #infosectrain #learntorise

The Security as Code framework defines how the company's operating model must change to extract the full benefits of cloud adoption. Source @McKinsey Link mck.co/3kWGPse rt @antgrasso #CloudComputing #CyberSecurity #SecurityasCode

The Security as Code framework defines how the company's operating model must change to extract the full benefits of cloud adoption. Source @McKinsey Link mck.co/3kWGPse rt @antgrasso #CloudComputing #CyberSecurity #SecurityasCode

The Security as Code framework defines how the company's operating model must change to extract the full benefits of cloud adoption. Source @McKinsey Link mck.co/3kWGPse rt @antgrasso #CloudComputing #CyberSecurity #SecurityasCode

Ready to take a more proactive approach to your #Cybersecurity? See how starting with #SecurityAsCode can make a huge difference. How would being proactive help your organization? Share your thoughts in the comments! #DevOps dy.si/HfrBpx

The Security as Code framework defines how the company's operating model must change to extract the full benefits of cloud adoption. Source @McKinsey Link mck.co/3kWGPse rt @antgrasso #CloudComputing #CyberSecurity #SecurityasCode

Ready to take a more proactive approach to your #Cybersecurity? See how starting with #SecurityAsCode can make a huge difference. How would being proactive help your organization? Share your thoughts in the comments! #DevOps dy.si/q3irfS2

Ready to take a more proactive approach to your #Cybersecurity? See how starting with #SecurityAsCode can make a huge difference. How would being proactive help your organization? Share your thoughts in the comments! #DevOps dy.si/V7oRTs

Ready to take a more proactive approach to your #Cybersecurity? See how starting with #SecurityAsCode can make a huge difference. How would being proactive help your organization? Share your thoughts in the comments! #DevOps dy.si/fp42f

Can Policy As Code be explained in less than 5 minutes?! 👀 The topic of this episode of Quick Bites of #CloudEngineering "What is #policyascode" 👉 pulumip.us/qb-policy #securityascode #cloudsecurity #DevOps #DevSecOps

The Security as Code framework defines how the company's operating model must change to extract the full benefits of cloud adoption. Source @McKinsey Link mck.co/3kWGPse rt @antgrasso #CloudComputing #CyberSecurity #SecurityasCode

Secret scanning saved my team once. We almost pushed AWS keys to GitHub. Security-as-code isn’t buzz—it's survival. Automate it before your interns make you famous on Reddit 😅 #DevSecOps #SecurityAsCode #CloudSecurity
The Security as Code framework defines how the company's operating model must change to extract the full benefits of cloud adoption. Source @McKinsey Link mck.co/3kWGPse RT @antgrasso #CloudComputing #CyberSecurity #SecurityasCode

Security-as-code is just DevOps growing up. No more PDFs of 'guidelines'. Your pipeline enforces them, every commit, every deploy. #DevSecOps #SecurityAsCode #Automation
The Security as Code framework defines how the company's operating model must change to extract the full benefits of cloud adoption. Source @McKinsey Link mck.co/3kWGPse rt @antgrasso #CloudComputing #CyberSecurity #SecurityasCode

The Security as Code framework defines how the company's operating model must change to extract the full benefits of cloud adoption. Source @McKinsey Link mck.co/3kWGPse RT @antgrasso #CloudComputing #CyberSecurity #SecurityasCode

The Security as Code framework defines how the company's operating model must change to extract the full benefits of cloud adoption. Source @McKinsey Link mck.co/3kWGPse rt @antgrasso #CloudComputing #CyberSecurity #SecurityasCode

The Security as Code framework defines how the company's operating model must change to extract the full benefits of cloud adoption. Source @McKinsey Link mck.co/3kWGPse RT @antgrasso #CloudComputing #CyberSecurity #SecurityasCode

The Security as Code framework defines how the company's operating model must change to extract the full benefits of cloud adoption. Source @McKinsey Link mck.co/3kWGPse rt @antgrasso #CloudComputing #CyberSecurity #SecurityasCode

The Security as Code framework defines how the company's operating model must change to extract the full benefits of cloud adoption. Source @McKinsey Link mck.co/3kWGPse RT @antgrasso #CloudComputing #CyberSecurity #SecurityasCode

The Security as Code framework defines how the company's operating model must change to extract the full benefits of cloud adoption. Source @McKinsey Link mck.co/3kWGPse rt @antgrasso #CloudComputing #CyberSecurity #SecurityasCode

Security as Code is like putting security on autopilot, catching threats before they pop up. Our platform makes implementing it across your DevOps pipelines effortless ➡ skyu.io/book-a-demo/ Read more: linkedin.com/feed/update/ur… #SecurityAsCode #DevSecOps #Automation #SkyU


The Security as Code framework defines how the company's operating model must change to extract the full benefits of cloud adoption. Source @McKinsey Link mck.co/3kWGPse RT @antgrasso #CloudComputing #CyberSecurity #SecurityasCode

Enhance Your CI/CD Pipeline with Security as Code #CICDSecurity #SecurityAsCode #DevOps #ContinuousMonitoring #VulnerabilityManagement #Automation #Collaboration #SoftwareSecurity #RealTimeDetection #Cybersecurity
The Security as Code framework defines how the company's operating model must change to extract the full benefits of cloud adoption. Source @McKinsey Link mck.co/3kWGPse rt @antgrasso #CloudComputing #CyberSecurity #SecurityasCode

The Security as Code framework defines how the company's operating model must change to extract the full benefits of cloud adoption. Source @McKinsey Link mck.co/3kWGPse RT @antgrasso #CloudComputing #CyberSecurity #SecurityasCode

📽️ The #securityascode on #Azure session is live on YT 👉 lnkd.in/gygJnCvS #sharingiscaring ❤️ #securitycode #AzureBicep #DevOps #SecurityPosture
The Security as Code framework defines how the company's operating model must change to extract the full benefits of cloud adoption. Source @McKinsey Link mck.co/3kWGPse rt @antgrasso #CloudComputing #CyberSecurity #SecurityasCode

The Security as Code framework defines how the company's operating model must change to extract the full benefits of cloud adoption. Source @McKinsey Link mck.co/3kWGPse RT @antgrasso #CloudComputing #CyberSecurity #SecurityasCode

The Security as Code framework defines how the company's operating model must change to extract the full benefits of cloud adoption. Source @McKinsey Link mck.co/3kWGPse rt @antgrasso #CloudComputing #CyberSecurity #SecurityasCode

IBM says 25% of #cyberattacks in 2022 involved the exploitation of public-facing applications. Reduce your web app risks with #SecurityAsCode. hubs.la/Q01DdNlD0

Tout savoir sur #SecurityAsCode c'est aujourd'hui à 16h à Monaco @Les_Assises @EdouardViot @sdesaintalbin @Manuej #DevSecOps #microwaf #WAF #appsecurity #AssisesSI

Excited to spend the afternoon at the new @oak9io world headquarters. The team is about to release some amazing tech to turbo-charge securing Infrastructure as Code. #securityascode

The Security as Code framework defines how the company's operating model must change to extract the full benefits of cloud adoption. Source @McKinsey Link mck.co/3kWGPse via @antgrasso #CloudComputing #CyberSecurity #SecurityasCode

Get started with "Security as Code" bit.ly/2MjNdKO -- #devops #securityascode #infrastructureascode #cybersecurity #securityoperations

#DevOps teams must validate security requirements in a short time. @jctechno shares on @TechBeaconCOM how #securityascode can play a big role in this, automating the process of secure deployment, which makes the process easier and faster #MicroFocus bit.ly/2B34NJI

Vulnerability and Port Scanning now as #SecurityAsCode. Download our recently published NMap Robot Framework Library - bit.ly/2oLRasN @robotframework @nmap #DevSecOps

Securing DevOps: The ABCs of Security-as-Code bit.ly/3IsZSm7 #devops #secdevops #securityascode #infosec #cybersecurity

Incorporating #SecurityAsCode into #DevOps aligns businesses toward the #GDPR’s goal of data protection. See how: bit.ly/2MKS9nh

The Security as Code framework defines how the company's operating model must change to extract the full benefits of cloud adoption. Link > mck.co/3Aj0es8 @McKinsey @antgrasso via @LindaGrass0 #CloudComputing #CyberSecurity #SecurityasCode
New research shows half of Java & .NET #application flaws still impact the apps after 243 days & 158 days, respectively. Waratek fixes flaws in minutes, not months. Take a guided tour of #SecurityAsCode now. hubs.la/Q01ygJc10

#Securityascode #AssisesSI c’est maintenant ! #microwaf #DevSecOps @EdouardViot @sdesaintalbin @RS_CyberFR @Les_Assises

Listening to securing the cloud presentation panel hosted by @jessrobin96 at @cybersec_summit Silicon Valley #cybersecurity #cloudsecurity #securityascode #devops @googlecloud Assad Namer weighing in.

The Security as Code framework defines how the company's operating model must change to extract the full benefits of cloud adoption. Source @McKinsey Link mck.co/3kWGPse rt @antgrasso #CloudComputing #CyberSecurity #SecurityasCode

#SecurityAsCode runs on-premises or public clouds like AWS, Azure, or GCP, providing security teams control through policy, giving them everything needed to scale visibility and protection. hubs.la/Q01l24tv0

The Security as Code framework defines how the company's operating model must change to extract the full benefits of cloud adoption. @McKinsey Link mck.co/3kWGPse rt @antgrasso #CloudComputing #CyberSecurity #SecurityasCode
#SecurityAsCode can empower businesses to more proactively protect themselves and their data. Learn how: bit.ly/3UFHJuH

The Security as Code framework defines how the company's operating model must change to extract the full benefits of cloud adoption. Source @McKinsey Link mck.co/3kWGPse RT @antgrasso #CloudComputing #CyberSecurity #SecurityasCode

Something went wrong.
Something went wrong.
United States Trends
- 1. Clay Higgins 18K posts
- 2. Trent Grisham 1,077 posts
- 3. Saudi 232K posts
- 4. #UNBarbie 12.6K posts
- 5. Gemini 3 46.9K posts
- 6. Peggy 5,899 posts
- 7. Khashoggi 45K posts
- 8. Nicki 105K posts
- 9. Mary Bruce 3,173 posts
- 10. #UnitedNationsBarbie 11.5K posts
- 11. Salman 73.1K posts
- 12. Gleyber Torres N/A
- 13. Bellinger 1,639 posts
- 14. Robinhood 5,248 posts
- 15. Shota Imanaga 1,113 posts
- 16. Cashman N/A
- 17. Pat Bev 2,429 posts
- 18. #NXXT2Run 1,392 posts
- 19. McTominay 18.5K posts
- 20. Epstein Files Transparency Act 15.4K posts