#simplehelp resultados de búsqueda
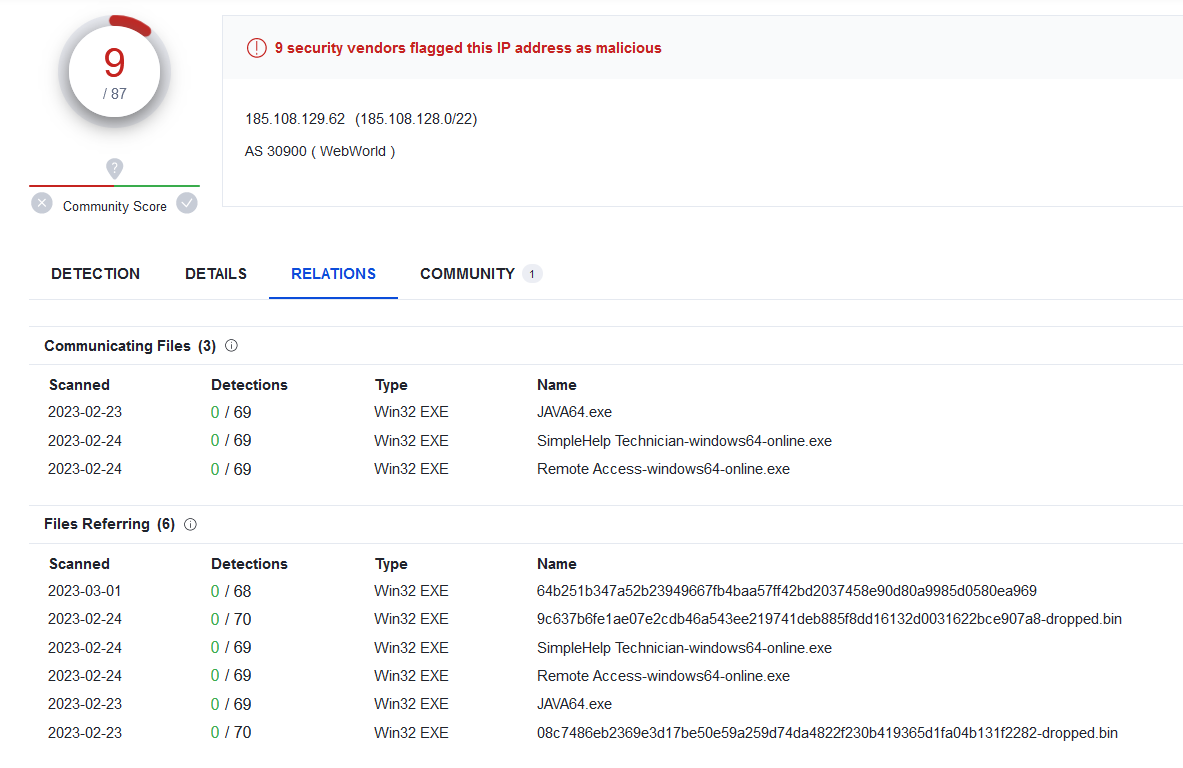
#SimpleHelp is another remote administration tool that is being actively used to maintain access on victim networks. IP 185.108.129.62 was recently seen in a #Medusa ransomware incident and apparently also in a #BianLian case 🧐 The main difference with other tools, is that…

@Giverep��s blockchain tech simplifies giving��no jargon, just a way to help. #SimpleHelp
csirt_it: ‼️ #SimpleHelp: ricercatori di sicurezza hanno recentemente rilevato vulnerabilità, con gravità “critica” e “alta”, relative al noto software di supporto remoto Rischio: 🟠 Tra le tipologie: 🔶 Arbitrary File Write/Read 🔗 …

csirt_it: #SimpleHelp: risolte due vulnerabilità, di cui una con gravità “alta”, nel noto software di supporto remoto Rischio:🟡 Tipologia: 🔸Remote Code Execution 🔗acn.gov.it/portale/w/vuln… 🔄Aggiornamenti disponibili🔄

Los ataques de #ransomware han afectado a aproximadamente 900 organizaciones 📊 y recientemente involucraron la explotación de vulnerabilidades de #SimpleHelp.⚠️☠️




🐾Struggling to keep pet hair under control at home? Let us handle the cleaning so you can relax in a spotless, pet-friendly home.🏡 #Home #PeTHairFree #SimpleHelp #PetFriendly #Cleanzen #Philadelphia #CleanzenPhiladelphia #Spotless #RegularGrooming #FurRemoval

Hackers are exploiting vulnerabilities in SimpleHelp RMM software, with active threats linked to CVE-2024–57726, CVE-2024–57727, and CVE-2024–57728. Significant risks for affected organizations. 🔓🇺🇸 #SimpleHelp #RMMFlaws link: ift.tt/jR8wD5J

Field Effect thwarted a cyberattack exploiting SimpleHelp vulnerabilities, preventing the Sliver backdoor from escalating into a ransomware threat. A reminder of the risks in RMM tools. 🔒⚠️ #SimpleHelp #CyberThreats #Canada link: ift.tt/V4rIebZ

Intel-Ops has also observed what we believe to be a new TTP, using DNS records to host command line queries in TXT records. Continued use of #TacticalRMM, #SimpleHelp and #ReNgine. We will release more information soon.

Multiple critical vulnerabilities found in SimpleHelp could lead to file theft and remote code execution. Immediate patching is essential to secure systems. 😱 #SimpleHelp #RemoteAccess #USA #CybersecurityNews link: ift.tt/8TJxiyR

Critical vulnerabilities found in SimpleHelp remote support software could compromise both servers and clients. Users should upgrade to avoid risks. 🛡️ #SimpleHelp #RemoteAccess #USA #CybersecurityNews link: ift.tt/wYjC2T4

Need help with your crowdfunding campaign? 🎯 I’ll create, promote, and make it shine! Let’s make your ideas a success. Order now! 🚀 #Crowdfunding #SimpleHelp"

Recent vulnerabilities in SimpleHelp RMM (CVE-2024-57726, CVE-2024-57727, CVE-2024-57728) are being exploited by hackers for network breaches. Upgrading is crucial. 🛡️ #SimpleHelp #ArcticWolf #USA link: ift.tt/eWT34Ow

🚨 Vulnerabilities in SimpleHelp remote access software could expose users to unauthenticated access and remote code execution. Patches are available—updating is crucial! 🛡️ #SimpleHelp #RemoteAccess #CyberThreats #CybersecurityNews link: ift.tt/RuMfxOA

Recent cybersecurity updates reveal ongoing ransomware exploits like DragonForce targeting SimpleHelp vulnerabilities, McLean Mortgage data breaches by BlackBasta, and Predator spyware emerging in Mozambique. ⚠️ #SimpleHelp #Mozambique ift.tt/YRaUidm
Ransomware gangs like DragonForce are exploiting unpatched SimpleHelp RMM versions 5.5.7 and earlier since Jan 2025, targeting utility billing systems. CISA recommends updates, server isolation, and vigilant monitoring. 🔒 #SimpleHelp #USA ift.tt/zRYMmsE
hendryadrian.com
Ransomware Gangs Exploit Unpatched SimpleHelp Flaws to Target Victims with Double Extortion
Ransomware actors are exploiting unpatched SimpleHelp RMM instances to target utility billing software customers, emphasizing the need for updates and threat mitigation. The attack pattern highlights...
Researchers warn of a cyberattack exploiting SimpleHelp RMM vulnerabilities (CVE-2024-57726, CVE-2024-57727, CVE-2024-57728), allowing unauthorized device access. Ensure software is updated! 🔒💻 #SimpleHelp #CyberThreats #USA link: ift.tt/72MSJgs

Hackers are exploiting vulnerabilities in SimpleHelp RMM to create admin accounts and deploy Sliver malware. Active exploits linked to Akira ransomware discovered. Stay vigilant. 🔒 #SliverMalware #SimpleHelp #USA link: ift.tt/ucSr5nV

@Giverep��s blockchain tech simplifies giving��no jargon, just a way to help. #SimpleHelp
CISA avvisa di vulnerabilità critiche in #SimpleHelp già sfruttate da gruppi #ransomware per colpire #MSP e i loro clienti. 👉 Scopri i 3 passaggi fondamentali per proteggere i tuoi clienti: watchguard.com/it/wgrd-news/b… #Cybersecurity #MSP #Ransomware #ZeroTrust #WGBlog
watchguard.com
SimpleHelp: CISA avverte di gravi vulnerabilità nel software di accesso remoto
La CISA avverte di gravi vulnerabilità in SimpleHelp sfruttate da gruppi ransomware. Il tuo ambiente MSP è pronto a prevenire accessi non autorizzati?
csirt_it: #SimpleHelp: risolte due vulnerabilità, di cui una con gravità “alta”, nel noto software di supporto remoto Rischio:🟡 Tipologia: 🔸Remote Code Execution 🔗acn.gov.it/portale/w/vuln… 🔄Aggiornamenti disponibili🔄

Ransomware actors are exploiting CVE-2024-57727 in SimpleHelp RMM versions 5.5.7 and earlier to access files and deploy ransomware, impacting utility billing providers. Threat groups like DragonForce and Hive linked to these attacks. 🔐 #SimpleHelp #Rans… ift.tt/XDihYTQ
Ransomware gangs are exploiting unpatched SimpleHelp RMM flaws (CVE-2024-57726, 57727, 57728) for double extortion attacks. Versions 5.5.7 and earlier are vulnerable. Isolate servers and patch now to stay secure. #SimpleHelp #CVE2024 #Ransomware #CyberSecurity #PatchNow
#SimpleHelp is another remote administration tool that is being actively used to maintain access on victim networks. IP 185.108.129.62 was recently seen in a #Medusa ransomware incident and apparently also in a #BianLian case 🧐 The main difference with other tools, is that…


Los ataques de #ransomware han afectado a aproximadamente 900 organizaciones 📊 y recientemente involucraron la explotación de vulnerabilidades de #SimpleHelp.⚠️☠️




🐾Struggling to keep pet hair under control at home? Let us handle the cleaning so you can relax in a spotless, pet-friendly home.🏡 #Home #PeTHairFree #SimpleHelp #PetFriendly #Cleanzen #Philadelphia #CleanzenPhiladelphia #Spotless #RegularGrooming #FurRemoval

Hackers are exploiting vulnerabilities in SimpleHelp RMM software, with active threats linked to CVE-2024–57726, CVE-2024–57727, and CVE-2024–57728. Significant risks for affected organizations. 🔓🇺🇸 #SimpleHelp #RMMFlaws link: ift.tt/jR8wD5J

Need help with your crowdfunding campaign? 🎯 I’ll create, promote, and make it shine! Let’s make your ideas a success. Order now! 🚀 #Crowdfunding #SimpleHelp"

Field Effect thwarted a cyberattack exploiting SimpleHelp vulnerabilities, preventing the Sliver backdoor from escalating into a ransomware threat. A reminder of the risks in RMM tools. 🔒⚠️ #SimpleHelp #CyberThreats #Canada link: ift.tt/V4rIebZ

csirt_it: ‼️ #SimpleHelp: ricercatori di sicurezza hanno recentemente rilevato vulnerabilità, con gravità “critica” e “alta”, relative al noto software di supporto remoto Rischio: 🟠 Tra le tipologie: 🔶 Arbitrary File Write/Read 🔗 …

Recent vulnerabilities in SimpleHelp RMM (CVE-2024-57726, CVE-2024-57727, CVE-2024-57728) are being exploited by hackers for network breaches. Upgrading is crucial. 🛡️ #SimpleHelp #ArcticWolf #USA link: ift.tt/eWT34Ow

Researchers warn of a cyberattack exploiting SimpleHelp RMM vulnerabilities (CVE-2024-57726, CVE-2024-57727, CVE-2024-57728), allowing unauthorized device access. Ensure software is updated! 🔒💻 #SimpleHelp #CyberThreats #USA link: ift.tt/72MSJgs

Intel-Ops has also observed what we believe to be a new TTP, using DNS records to host command line queries in TXT records. Continued use of #TacticalRMM, #SimpleHelp and #ReNgine. We will release more information soon.


Hackers are exploiting vulnerabilities in SimpleHelp RMM to create admin accounts and deploy Sliver malware. Active exploits linked to Akira ransomware discovered. Stay vigilant. 🔒 #SliverMalware #SimpleHelp #USA link: ift.tt/ucSr5nV

🚨 Vulnerabilities in SimpleHelp remote access software could expose users to unauthenticated access and remote code execution. Patches are available—updating is crucial! 🛡️ #SimpleHelp #RemoteAccess #CyberThreats #CybersecurityNews link: ift.tt/RuMfxOA

Multiple critical vulnerabilities found in SimpleHelp could lead to file theft and remote code execution. Immediate patching is essential to secure systems. 😱 #SimpleHelp #RemoteAccess #USA #CybersecurityNews link: ift.tt/8TJxiyR

Critical vulnerabilities found in SimpleHelp remote support software could compromise both servers and clients. Users should upgrade to avoid risks. 🛡️ #SimpleHelp #RemoteAccess #USA #CybersecurityNews link: ift.tt/wYjC2T4

Last week, @CISAgov added #SimpleHelp CVE-2024-57727 to the KEV: cisa.gov/known-exploite…. ➡️ This vulnerability has been available as a Rapid Response test in #NodeZero for over a month, giving users plenty of time to patch their systems. Don't wait for malicious actors to…

Is your remote support tool a silent risk? Critical flaws in #SimpleHelp expose systems to attacks Find out how to protect yourself—fast! Details: secureblink.com/cyber-security… #RCE #Exploit #Hack #RemoteSupport #Vulnerability #Threatfeed #SecureBlink

: 🚨 CYBER ALERT: DragonForce Ransomware Attack Hackers from DragonForce are actively exploiting SimpleHelp software flaws to deploy ransomware across customer endpoints! #CyberSecurity #Ransomware #SimpleHelp #DragonForce #Infosec #ThreatIntel #MalwareAlert #EndpointSecurity

Сетевые злоумышленники эксплуатируют недавно исправленные уязвимости в программном обеспечении SimpleHelp Remote Monitoring and Management, чтобы получить начальный доступ к целевым сетям: securitymedia.org/news/khakery-i… #SimpleHelp #RemoteMonitoring #RMM #CVE #ИБ

csirt_it: #SimpleHelp: risolte due vulnerabilità, di cui una con gravità “alta”, nel noto software di supporto remoto Rischio:🟡 Tipologia: 🔸Remote Code Execution 🔗acn.gov.it/portale/w/vuln… 🔄Aggiornamenti disponibili🔄

Something went wrong.
Something went wrong.
United States Trends
- 1. Steelers 53.2K posts
- 2. Rodgers 21.4K posts
- 3. Mr. 4 4,742 posts
- 4. Chargers 38.3K posts
- 5. Resign 112K posts
- 6. Tomlin 8,395 posts
- 7. #ITZY_TUNNELVISION 20.9K posts
- 8. Schumer 232K posts
- 9. Tim Kaine 21.8K posts
- 10. Sonix 1,332 posts
- 11. Rudy Giuliani 11.7K posts
- 12. 8 Democrats 10.1K posts
- 13. Dick Durbin 14.2K posts
- 14. #BoltUp 3,106 posts
- 15. 8 Dems 7,767 posts
- 16. Angus King 18.2K posts
- 17. Voltaire 8,300 posts
- 18. Keenan Allen 5,107 posts
- 19. #ITWelcomeToDerry 4,976 posts
- 20. #RHOP 7,183 posts