#socialengineering search results
Amazon Web Services (#AWS) was hit by one of the biggest outages in years in October. @KateOflaherty shares how supplier disruptions can cascade into customer-facing risks, including #Phishing and #SocialEngineering: isms.online/cyber-security…

🚨#Deepfakes are here — and they’re calling you This isn’t sci-fi It’s #SocialEngineering 2.0: → Manipulation powered by AI → No malware needed. Just trust. Watch this short video to learn how to spot the signs Then share it — because awareness saves accounts #CyberSecurity
Not every hacker can—or should—cross the ethical line. One trainee once told me, “I can’t lie to someone.” He wasn’t weak. He was self-aware. Integrity is still the sharpest tool in cybersecurity. #CyberSecurity #Ethics #SocialEngineering
Social engineering doesn’t hack systems—it hacks people. One convincing call or email can cost millions. Train your teams, raise awareness, and protect your data. #CyberSecurity #SocialEngineering #Netwrix

In crypto hackers don’t always attack the code.. Sometimes they attack you.. This is called Social Engineering the art of exploiting human psychology.. @defiaudit #Web3 #CryptoSecurity #SocialEngineering #BlockchainSafety

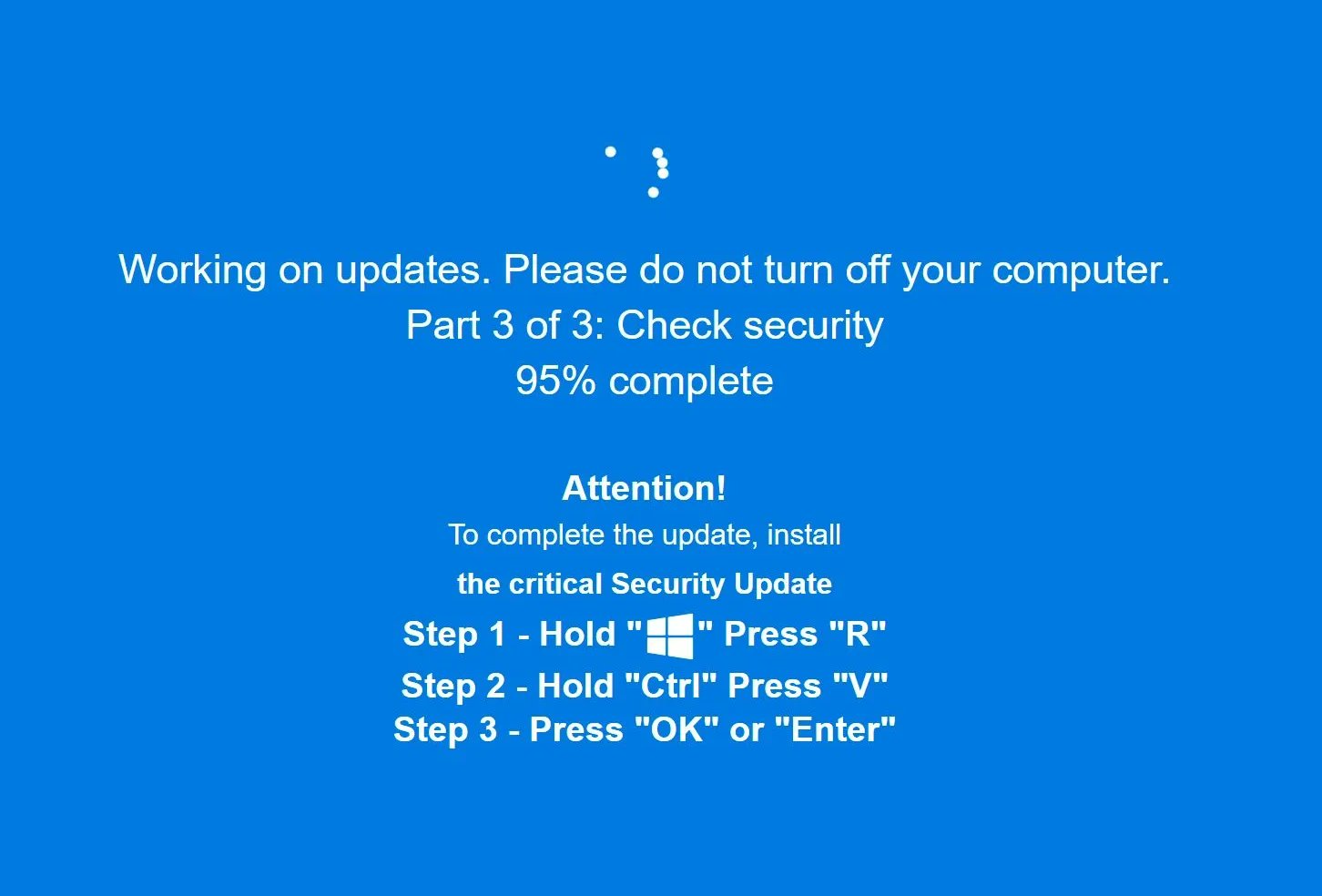
⚠️ A new ClickFix attack uses fake Windows update screens to deliver malware — proving that the most dangerous prompts look familiar. Don’t trust every dialog box. 💻☣️ #MalwareTactics #SocialEngineering buff.ly/7LMcplJ
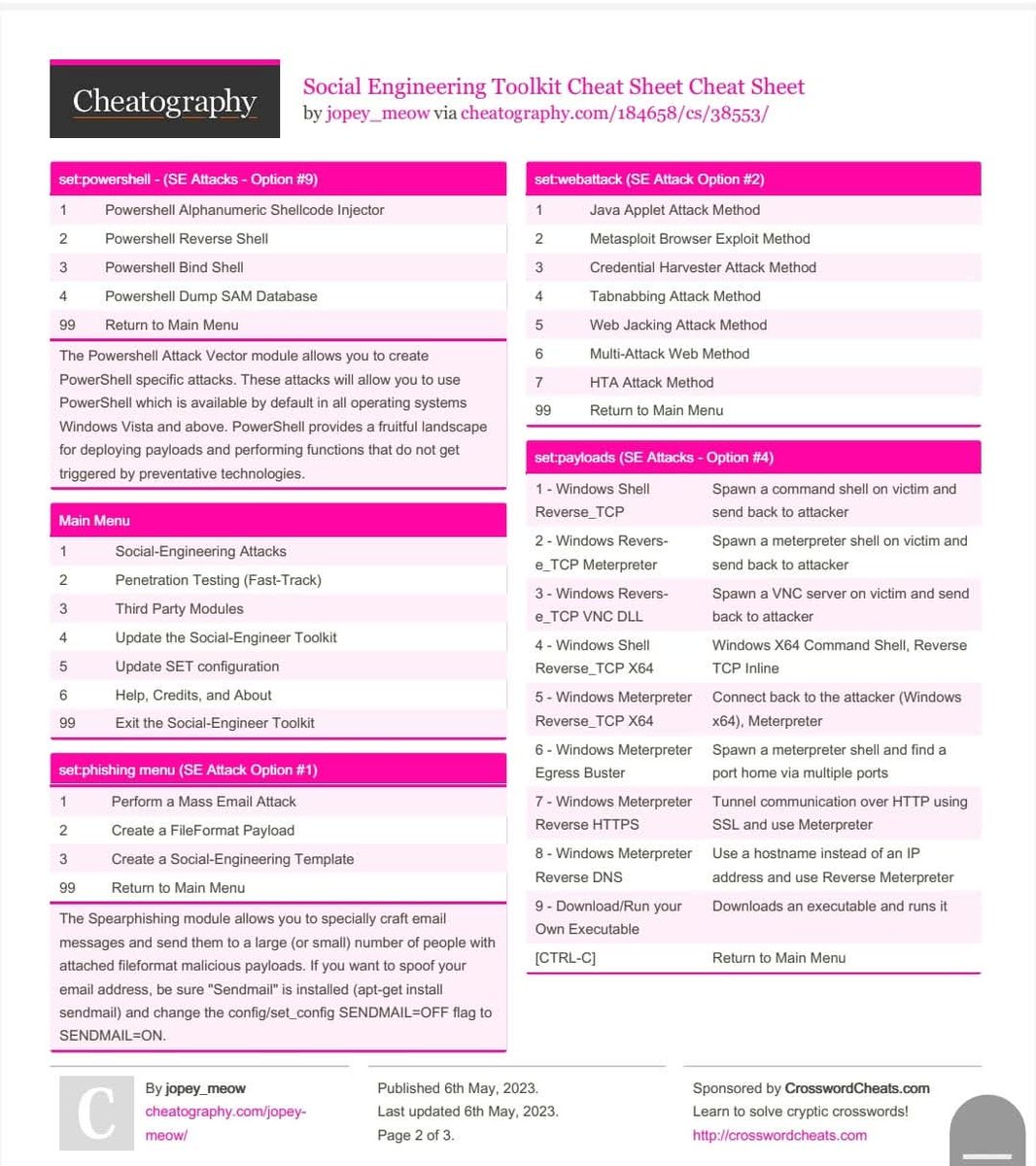
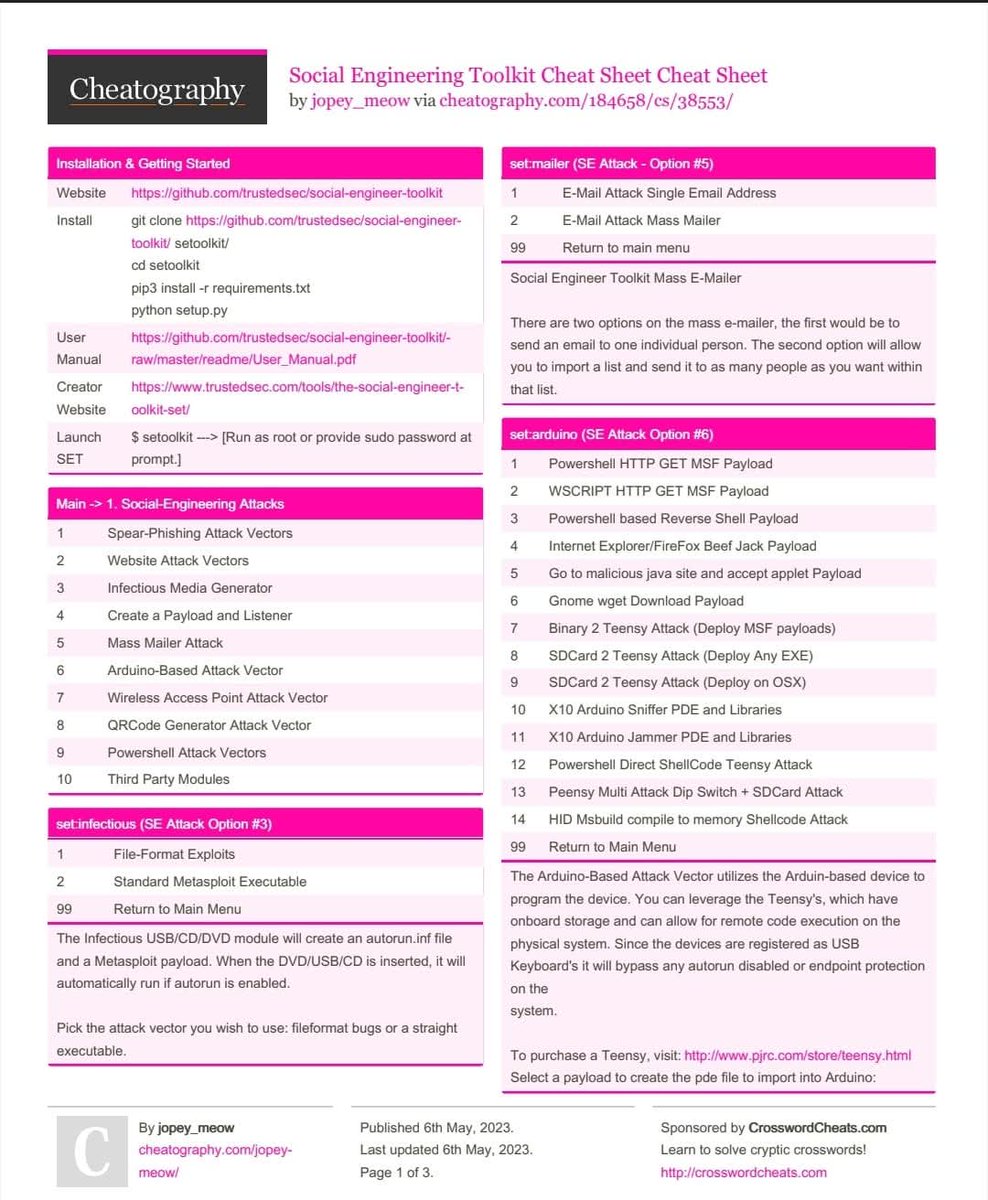
🎭 Social Engineering Cheatsheet A practical, awareness-focused guide on understanding and defending against human-focused manipulation techniques. 🔖 #SocialEngineering #InfoSec #CyberSecurity #SecurityAwareness #HumanSecurity #Phishing #OnlineSafety


⚠️ Phishing bancario: la truffa del finto “aggiornamento di sicurezza” Email apparentemente da Intesa Sanpaolo invita a “verificare l’account”. Tutto falso. Ma è costruita come una landing funnel perfetta. #phishing #socialengineering




Tech security relies too much on systems, not enough on human nature. A tight sweater & some...charm can still bypass the strongest firewalls. Exploit desires, not just vulnerabilities. #CyberSecurity #SocialEngineering
“Pay us or we’ll leak your webcam footage.” It’s one of the oldest fear-based scams — and it still works. Don’t panic. Don’t pay. Awareness > fear. #CyberSecurity #Phishing #SocialEngineering #Awareness
Social engineering attacks keep evolving, and with AI in the mix, they’re becoming harder to spot. How is your organisation preparing your people to be the first line of defence? #Cybersecurity #SocialEngineering #Smarttech247 #CyberResilience

Cybercriminals are finding new ways to steal personal information, leading to financial loss, damaged credit scores, and even identity fraud. Visit my blog at terrycutler.com/dont-let-ident… #IdentityTheft #socialengineering #GlobalEthicalHacker

VPL SERIES ke-11 — ASN TALENT ACADEMY EXPLORE 2025 Di era digital, keamanan data bukan lagi sekadar kewajiban, tetapi keharusan! Serangan social engineering, kebocoran data & ancaman siber bisa terjadi kapan saja! #SocialEngineering #KeamananSiber #ASNBelajar #MakartiBhaktiNagari

Honored to win the 2025 Most Innovative Anti-Phishing award. Optery finds and removes the personal data that fuels phishing, reducing attacks before they begin. A proactive defense that makes security teams stronger. #cybersecurity #phishing #socialengineering #privacy

Not all threats wear hoodies. Sometimes they flash a fake badge or tailgate into your office. Can your team spot the difference? 🔗 hubs.li/Q03Mgsgj0 #CyberAwarenessMonth #PhysicalSecurity #SocialEngineering #RedLegg

Social Engineering: The human firewall is often the weakest link. Phishing, pretexting, baiting - all manipulate human psychology, not technical systems. Training is your first line of defense. #SocialEngineering #HumanFirewall #Phishing

Military-themed lure targeting using weaponized ZIPs and hidden tunneling infrastructure cyble.com/blog/weaponize… #Malware #Backdoor #SocialEngineering #Tunnelling #Cyberespionage

Deepfakes are a real and growing threat. Join us for a live demonstration of #SocialEngineering by #Deepfake Technology at the Cyber Risk Summit Philly. See how these scams work and learn how to defend against them. hubs.la/Q03J0DdW0 #Cybersecurity #NetDiligence
You love talking about yourself? Great. So do cybercriminals. #SocialEngineering #DataProtection #UTMStack

⚠️ A new ClickFix attack uses fake Windows update screens to deliver malware — proving that the most dangerous prompts look familiar. Don’t trust every dialog box. 💻☣️ #MalwareTactics #SocialEngineering buff.ly/7LMcplJ
48 HOURS LEFT! Social Engineering Webinar - FINAL CALL 📅 Nov 28 | ⏰ 11:00 AM 🆓 Free In 2 days, you'll either: Know how to defend yourself Still be an easy target Your choice. Register NOW → bit.ly/DYICT_CyberSec… #CyberSecurity #LastChance #SocialEngineering
💸 $262M lost to account takeover scams! AI & fake sites on the rise.⚠️ #AccountFraud #SocialEngineering #CyberSecurity #FraudAlert #AIscams #OnlineSafety #PhishingScams #DigitalSafety #IdentityTheft #DataBreach #SecurityAwareness #CyberCrime #ScamAlert #CyberProtection #Viral

The Australian Prudential Regulation Authority warns that vishing (phone‑based social engineering) is one of the fastest‑growing threats. Ask: Does your business train for phone‑based hacks too? #socialengineering
$262 million lost in account takeover fraud schemes this year as cybercriminals exploit social engineering via texts, calls, and emails. Over 5,100 complaints reported, with AI-driven scams and fake sites surging. #AccountFraud #SocialEngineering ift.tt/NfYtjdF
Yes. The new VIP lane for mates. Reduces hospital waiting lists, saves on sick benefits, pensions etc. #socialengineering
linkedin.com/posts/odaseva_… #Salesforce #CyberSecurity #SocialEngineering #DataProtection #ZeroTrust
Part 4 of our 5-part series on #SocialEngineering in the #GenAI Era is now live, highlighting how Generative AI supercharges deception! Dive in: hubs.ly/Q03VNFGD0 Part 5 drops next Tuesday — follow us for the latest insights! #AI #Vishing #Phishing #VoiceSecurity
Could you tell the difference between authenticity and algorithm? Watch the full episode: Inside the Silicon Mind | Ep 15 - The Rise of Deepfakes #ai #cybersecurity #socialengineering #techthreats
youtube.com/live/jqFQQGlbk… In this session, we break down how social engineers manipulate human psychology to gain unauthorized access, steal sensitive data, and compromise entire systems—without ever touching a line of code. LIVE TODAY #CyberSecurity #SocialEngineering #cybersensei

Social engineering attacks are getting smarter, and merchants are paying the price. 🎭 Our latest Knowledge Guide breaks down how criminals manipulate customers, employees, and even support teams. Read more: hubs.li/Q03VHzDT0 #FraudPrevention | #SocialEngineering
Fake “Windows Update” screens fuels new wave of ClickFix attacks - helpnetsecurity.com/2025/11/25/fak… - @HuntressLabs @polygonben #Malware #SocialEngineering #Windows #Cybersecurity #CybersecurityNews
Cybercriminals don’t need malware when they can manipulate people. A well-trained team can stop the attacks technology never sees coming. Empower your people with the right training → cyber5.com #Cybersecurity #Cybercrime #SocialEngineering #EmployeeTraining…

Amazon Web Services (#AWS) was hit by one of the biggest outages in years in October. @KateOflaherty shares how supplier disruptions can cascade into customer-facing risks, including #Phishing and #SocialEngineering: isms.online/cyber-security…

VPL SERIES ke-11 — ASN TALENT ACADEMY EXPLORE 2025 Di era digital, keamanan data bukan lagi sekadar kewajiban, tetapi keharusan! Serangan social engineering, kebocoran data & ancaman siber bisa terjadi kapan saja! #SocialEngineering #KeamananSiber #ASNBelajar #MakartiBhaktiNagari

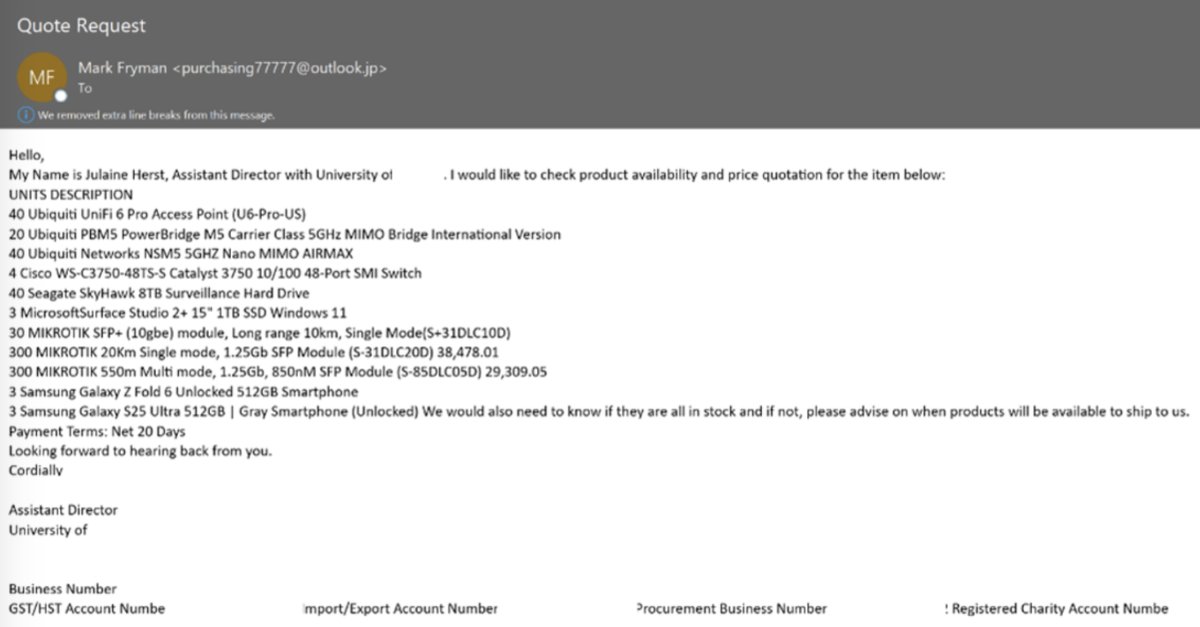
⚠️ Request For Quote (RFQ) scams are among the top five most frequently observed #socialengineering themes used by fraud actors. Learn how this scam works and see examples caught by our threat researchers here: brnw.ch/21wUP3a #finance #phishing #quote #fraud #BEC #scam
Group-IB’s Threat Intelligence team has investigated the #ClickFix technique—a new #SocialEngineering technique leveraging fake reCAPTCHAs and bot verification prompts to auto-copy malicious PowerShell commands straight to victims’ clipboards and lead them to executing it.

In crypto hackers don’t always attack the code.. Sometimes they attack you.. This is called Social Engineering the art of exploiting human psychology.. @defiaudit #Web3 #CryptoSecurity #SocialEngineering #BlockchainSafety

Social engineering doesn’t hack systems—it hacks people. One convincing call or email can cost millions. Train your teams, raise awareness, and protect your data. #CyberSecurity #SocialEngineering #Netwrix

You love talking about yourself? Great. So do cybercriminals. #SocialEngineering #DataProtection #UTMStack

Social Engineering: The human firewall is often the weakest link. Phishing, pretexting, baiting - all manipulate human psychology, not technical systems. Training is your first line of defense. #SocialEngineering #HumanFirewall #Phishing

The most dangerous vulnerability!!!! Human trust. This week, I’m diving into Social Engineering — where hackers exploit people, not just systems. 🔍 What it is 🎭 Common tricks 🛡️ How to stay safe Stay tuned. Let’s secure the human layer. #Cybersecurity #SocialEngineering #

🎭 Social Engineering Cheatsheet A practical, awareness-focused guide on understanding and defending against human-focused manipulation techniques. 🔖 #SocialEngineering #InfoSec #CyberSecurity #SecurityAwareness #HumanSecurity #Phishing #OnlineSafety




RedHook is a new Android banking trojan that targets Vietnamese users via phishing sites posing as trusted financial and government institutions. cyble.com/blog/redhook-n… #Phishing #Trojan #SocialEngineering #Spyware #ThreatIntel

My latest book is out!! You want to know how society got to where it's at? My Rooted series is for you! Check out my latest book here! amzn.to/3Jnv1xG #amazonbooks #SocialEngineering #history #distraction #wakeup

Check out my new post! I wrote a piece that breaks down the deepfake threat. open.substack.com/pub/briangreen… #DeepFakes #AI #SocialEngineering #security #privacy #cloud #infosec #cybersecurity

⚠️ Phishing bancario: la truffa del finto “aggiornamento di sicurezza” Email apparentemente da Intesa Sanpaolo invita a “verificare l’account”. Tutto falso. Ma è costruita come una landing funnel perfetta. #phishing #socialengineering




🎤 Speaker: Teresa Pereira(@starmtp_) — You Had Me at “Hello”: How Social Engineers Win Pretexts, micro-tells, defenses that work. Nov 28–29 @ ISEP · PT/EN · ~500 · bsidesporto.org #BSidesPorto #SocialEngineering #Cybersecurity

#PrimaFacie @X need lots of texplaining @Grok the #SocialEngineering #StatisticalSigns continue unabated, as evident is presented in *Exhibits A, B, C, D*! Care to clarify exactly what's going on here, and why the statistical data doesn't match, why mislead those that trust you ?
Military-themed lure targeting using weaponized ZIPs and hidden tunneling infrastructure cyble.com/blog/weaponize… #Malware #Backdoor #SocialEngineering #Tunnelling #Cyberespionage

Not all threats wear hoodies. Sometimes they flash a fake badge or tailgate into your office. Can your team spot the difference? 🔗 hubs.li/Q03Mgsgj0 #CyberAwarenessMonth #PhysicalSecurity #SocialEngineering #RedLegg

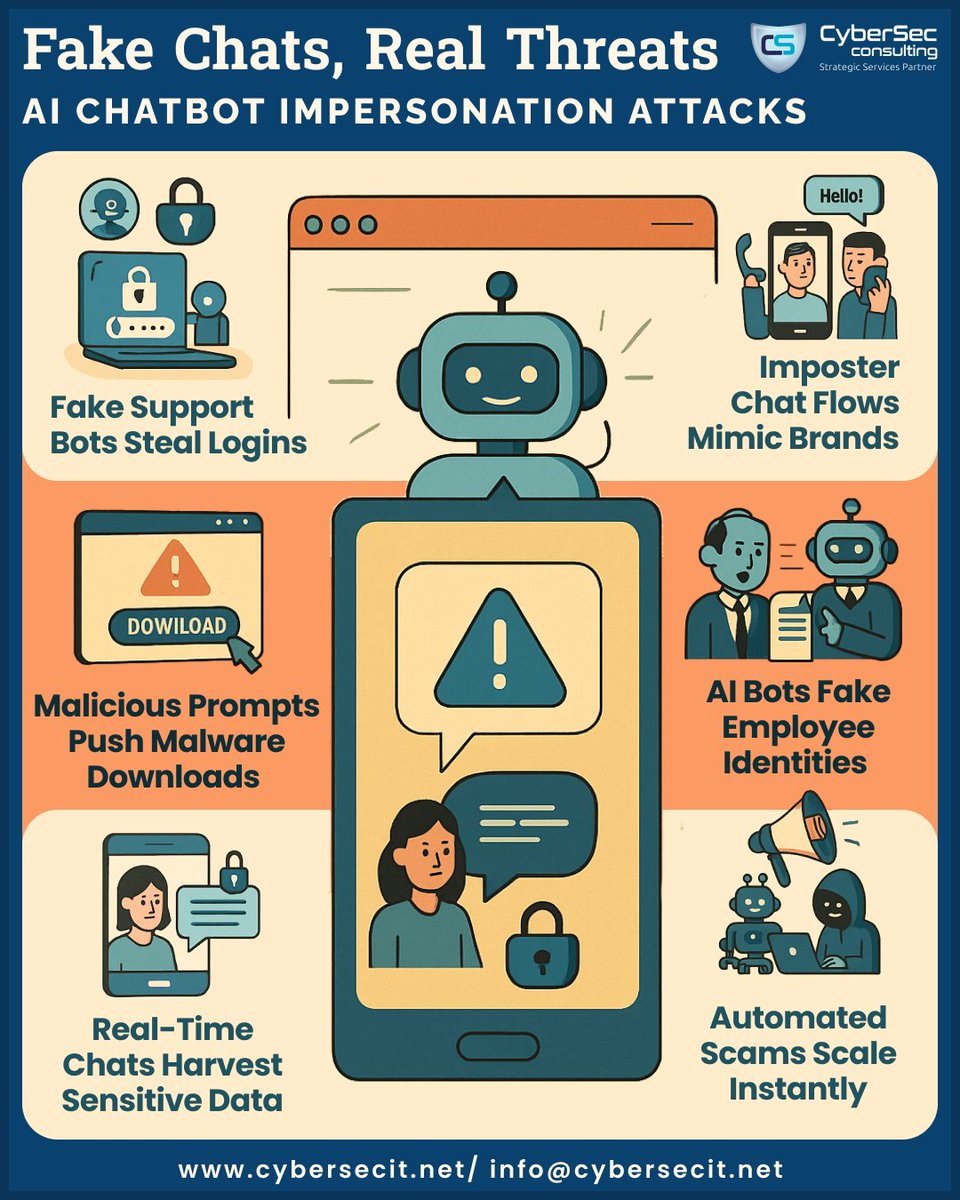
AI-powered fake chatbots are becoming a major social engineering weapon. They mimic support teams, trick users in real time, and steal sensitive data fast. @CyberSecCo49870 offers top-notch cybersecurity services and solutions. #AI #SocialEngineering #CyberSec
🚨 Privacy Protectors Spotlight! 🚨 Read what Ray Heffer — a world-renowned privacy & security expert — shares in our latest Privacy Protectors Spotlight series. Check out his insights in the full feature (link in the comments)! #Optery #OSINT #SocialEngineering #PrivacyMatters

Live calls, AI bots & great improv! @SEC_defcon brought bold #SocialEngineering action to @DEFCON 33! ☎️ 🎣 Thanks to @RachelTobac @_sn0ww @kminx @rekdt @jamieantisocial @PerryCarpenter @JC_SoCal @cxstephens @st0_ic & others! All #DEFCON33 villages 👇🏽 infosecmap.com/event/def-con-… .

Something went wrong.
Something went wrong.
United States Trends
- 1. Thanksgiving 316K posts
- 2. Good Wednesday 28K posts
- 3. #wednesdaymotivation 4,491 posts
- 4. Colorado State 3,200 posts
- 5. #Wednesdayvibe 2,239 posts
- 6. Nuns 7,511 posts
- 7. Mora 21.4K posts
- 8. Stranger Things Day 3,078 posts
- 9. Hump Day 11K posts
- 10. Happy Hump 7,298 posts
- 11. Karoline Leavitt 25.6K posts
- 12. Luka 69.5K posts
- 13. Hong Kong 53.7K posts
- 14. Brett Favre 1,025 posts
- 15. Food Network N/A
- 16. Gretzky N/A
- 17. Clippers 20.1K posts
- 18. El Salvador 48.7K posts
- 19. Witkoff 181K posts
- 20. Tina Turner 5,075 posts