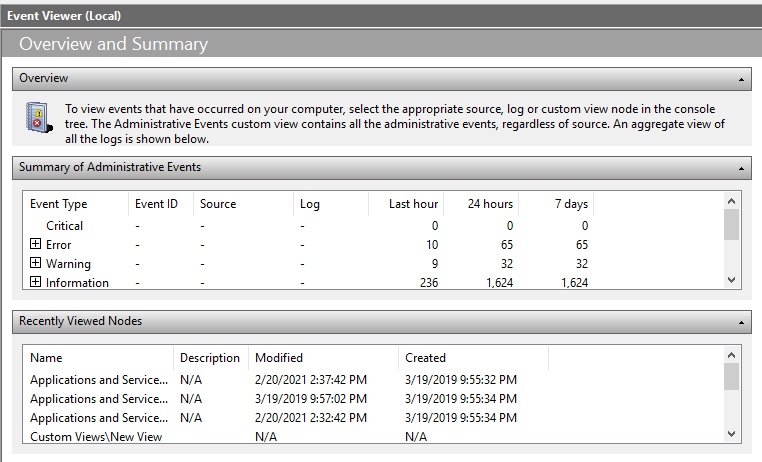
#windowslogs search results
Windows Logging for SOC on @TryHackMe transformed my Windows threat hunting! Correlating Event IDs for brute-force detection, tracking suspicious account creation, and analyzing PowerShell history felt genuinely rewarding. #WindowsLogs #SOC #ThreatHunting

Windows logs are your first line of defense. 🔒 Learn how to monitor Windows logs for security threats and detect attacks before they spread. 👉businesspcsupport.com/how-to-use-win… #CyberSecurity #WindowsLogs #InfoSec
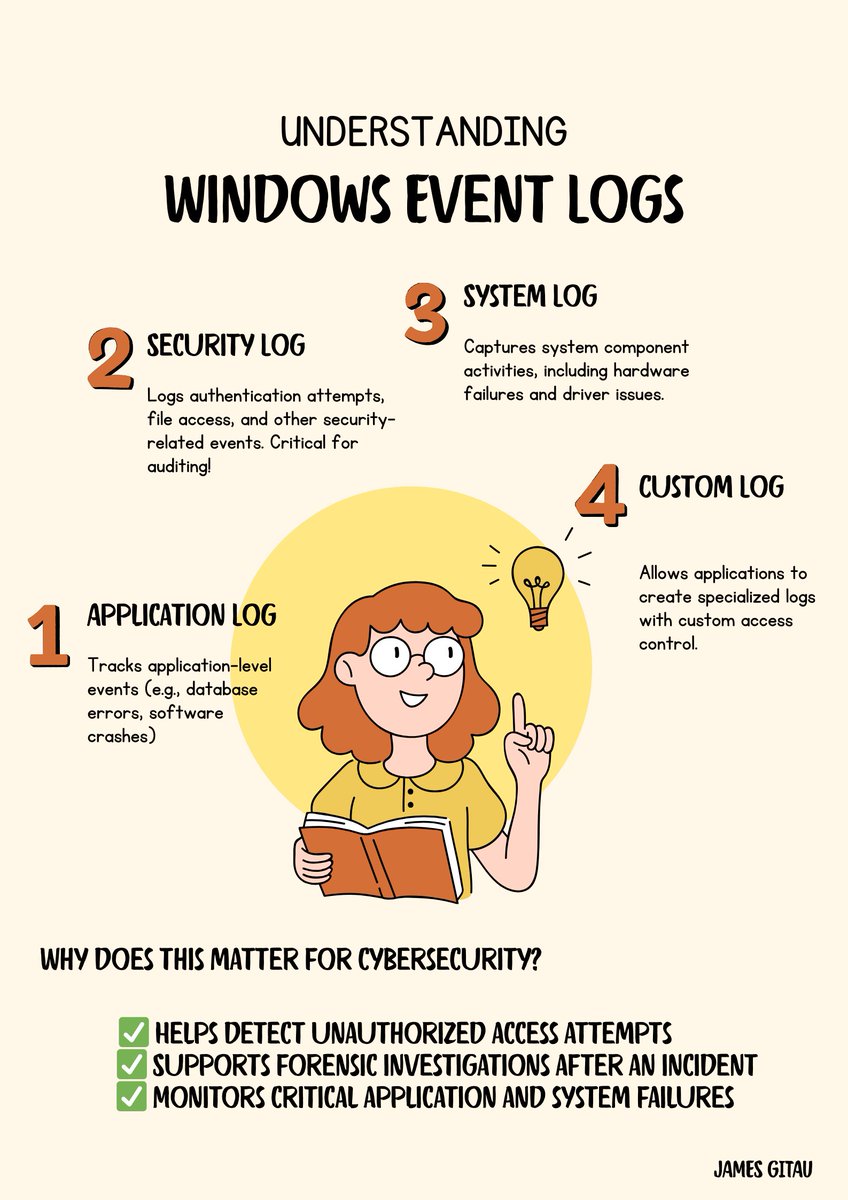
🛠️ Understanding Windows Event Logs for Cybersecurity Professionals 🛠️ Windows Event Logs play a crucial role in monitoring system activity, detecting security incidents, and troubleshooting issues. Here’s a quick breakdown of the key log types:#CyberSecurity #WindowsLogs #SIEM
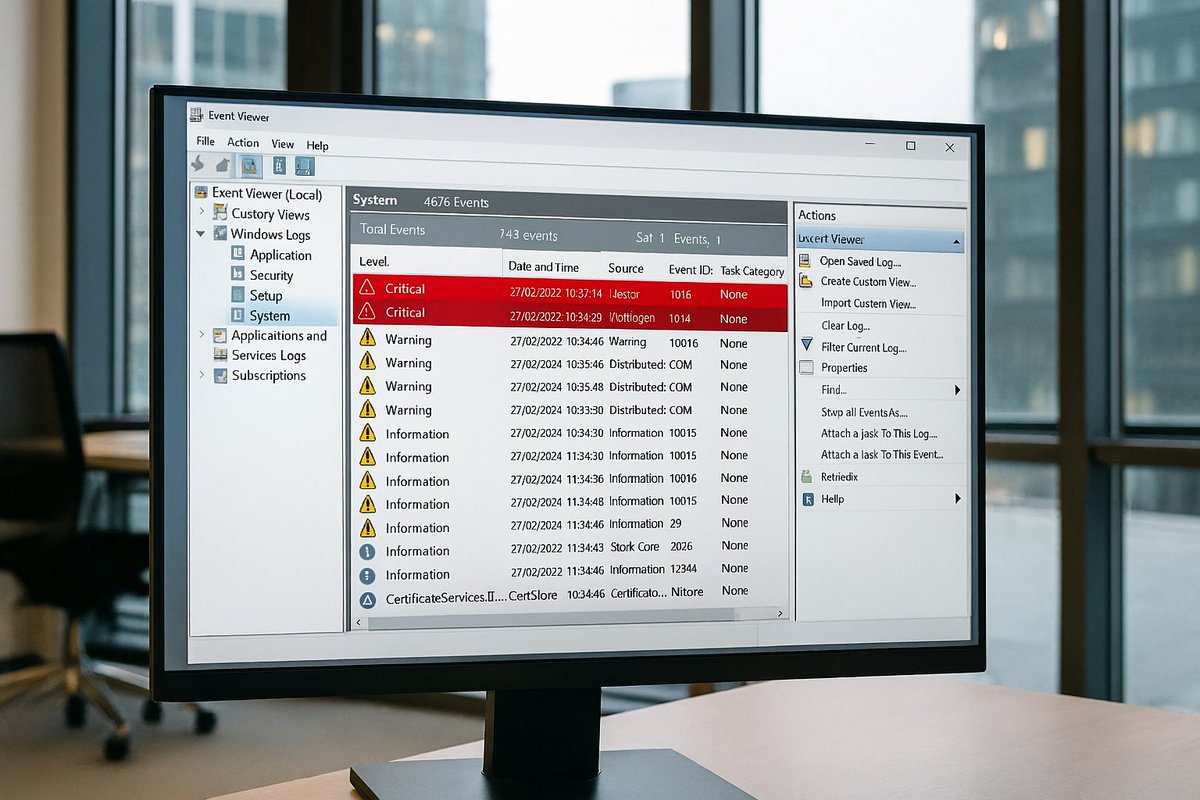
Diving Deeper to Understand the Windows Event logs for Cyber Security Operation Center (SOC) bit.ly/343XXTa #SOC #windowslogs

🛡️ Join the workshop on "Attacks & the Windows Logs" at #Hacktivity2023 and uncover common techniques employed by attackers during lateral movement. Get your ticket: t.ly/5xuMP #Hacktivity #WindowsLogs

“Ekip arkadaşımız Ceyda Ünsal’ın yazdığı ‘Windows Log Dosyalarının Güvenliği ve Yönetimi’ blog yazısını web sitemizden okuyabilirsiniz! 🥳 Blog 👉🏻 dpusec.org/windows-gunluk… #cybersecurity #sibergüvenlik #windowslogs #logmanagement #infosec #DPUSEC #itsecurity #loganalysis

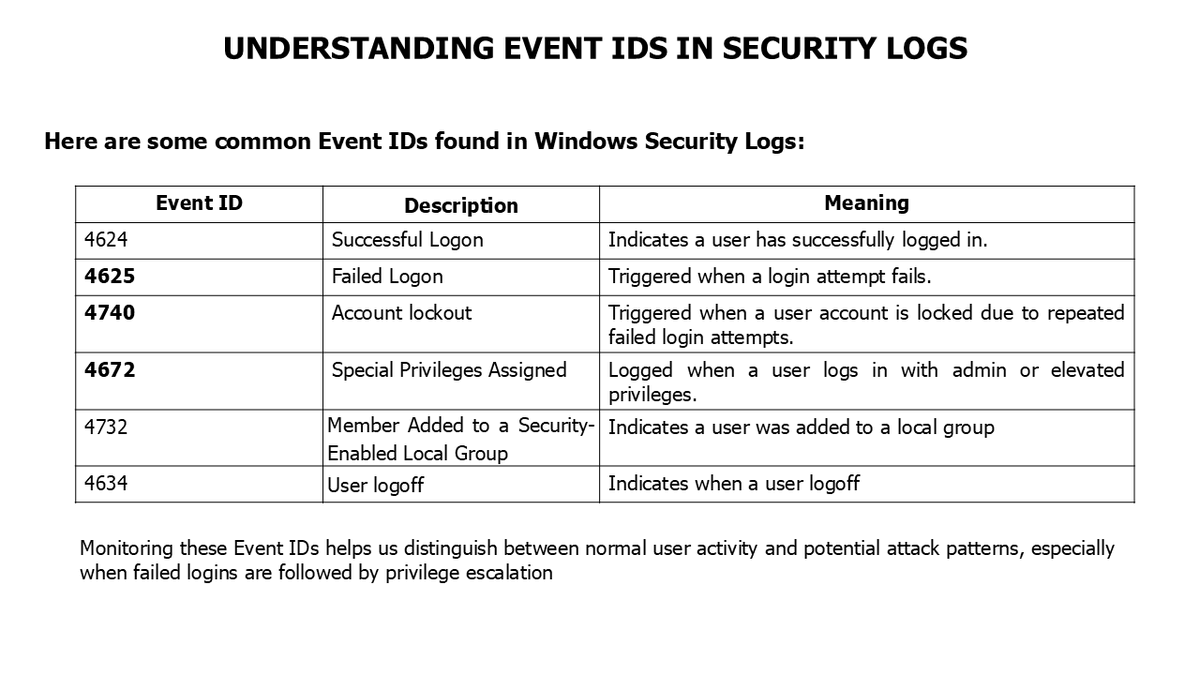
Just concluded a 14-slide breakdown on detecting brute-force attacks using Windows Event Logs. 🧠 Event ID 4625, 4624 & 4672 decoded 🔐 Lockout policies, MFA, SIEM alerts 🔗 link drive.google.com/file/d/1LZ7PN4… #SOCAnalyst #WindowsLogs #ThreatDetection #IncidentResponse #SIEM #BlueTeam



Most Windows Event Log errors look scary—but they’re usually harmless. Don’t panic. Filter the noise. Focus on what matters. 📖 programmingeveryday.com/2025/09/window… #WindowsLogs #ITLeadership #SignalVsNoise #ProgrammingEveryDay
I just published The Windows Logs👨💻 link.medium.com/V2aZewBm2Qb #WindowsSecurity #WindowsLogs #CyberSecurity #EthicalHacking #InfoSec #RedTeam #LogAnalysis
link.medium.com
The Windows Logs👨💻
Learn about Windows logs, including how to view, filter, and manipulate event IDs. This knowledge will assist you in Windows analysis and…
Explore how overlooked Windows event logs can reveal critical forensic details, aiding in incident detection and analysis. nasbench.medium.com/finding-forens… #Forensics #WindowsLogs
Seeking community insights! What tools or methods do you recommend for detecting PowerView/BloodHound/SharpHound activity through Windows log events? 🕵️♂️ Share your expertise! #CyberSecurity #WindowsLogs #ThreatDetection
Windows Event Logs Deep Dive - tryhackme.com/room/windowsev… #ethicalhacking #eventviewer #windowslogs
🔐 En kritik Windows Event ID'leri: - 4624 → Başarılı oturum açma - 4625 → Başarısız oturum açma - 4688 → Yeni işlem oluşturuldu - 1102 → Güvenlik günlüğü temizlendi Bu ID’leri SIEM’de alarm olarak kurmak hayat kurtarır! #CyberSecurity #BlueTeam #WindowsLogs #DFIR
Now testing windows 10 on lumia 730. #WindowsLogs @Microsoft #LetTheGamesBegin
How to centralise and search your IIS logs blog.logit.io/how-to-central… #IIS #logging #windowslogs #DevOps
Lateral Movement Detection with Windows Event Logs socinvestigation.com/lateral-moveme…
New eBook out now! Don't miss it! #AWS #WindowsLogs #AI bit.ly/3xOY9DW
Windows Logging for SOC on @TryHackMe transformed my Windows threat hunting! Correlating Event IDs for brute-force detection, tracking suspicious account creation, and analyzing PowerShell history felt genuinely rewarding. #WindowsLogs #SOC #ThreatHunting

Windows logs are your first line of defense. 🔒 Learn how to monitor Windows logs for security threats and detect attacks before they spread. 👉businesspcsupport.com/how-to-use-win… #CyberSecurity #WindowsLogs #InfoSec

Most Windows Event Log errors look scary—but they’re usually harmless. Don’t panic. Filter the noise. Focus on what matters. 📖 programmingeveryday.com/2025/09/window… #WindowsLogs #ITLeadership #SignalVsNoise #ProgrammingEveryDay
Just concluded a 14-slide breakdown on detecting brute-force attacks using Windows Event Logs. 🧠 Event ID 4625, 4624 & 4672 decoded 🔐 Lockout policies, MFA, SIEM alerts 🔗 link drive.google.com/file/d/1LZ7PN4… #SOCAnalyst #WindowsLogs #ThreatDetection #IncidentResponse #SIEM #BlueTeam




🚀 WinLog-MCP a cool MCP tool for retrieving and analyzing Windows event logs (e.g., Application, System, Security). Ideal for security monitoring, incident response, and log analysis automation. 🔗 Check it out: github.com/XD3an/winlog-m… #CyberSecurity #WindowsLogs #MCP
github.com
GitHub - XD3an/winlog-mcp: a mcp tool for retrieving and analyzing Windows event logs (e.g....
a mcp tool for retrieving and analyzing Windows event logs (e.g. Application, System, Security). - XD3an/winlog-mcp
🛠️ Understanding Windows Event Logs for Cybersecurity Professionals 🛠️ Windows Event Logs play a crucial role in monitoring system activity, detecting security incidents, and troubleshooting issues. Here’s a quick breakdown of the key log types:#CyberSecurity #WindowsLogs #SIEM

I just published The Windows Logs👨💻 link.medium.com/V2aZewBm2Qb #WindowsSecurity #WindowsLogs #CyberSecurity #EthicalHacking #InfoSec #RedTeam #LogAnalysis
link.medium.com
The Windows Logs👨💻
Learn about Windows logs, including how to view, filter, and manipulate event IDs. This knowledge will assist you in Windows analysis and…
“Ekip arkadaşımız Ceyda Ünsal’ın yazdığı ‘Windows Log Dosyalarının Güvenliği ve Yönetimi’ blog yazısını web sitemizden okuyabilirsiniz! 🥳 Blog 👉🏻 dpusec.org/windows-gunluk… #cybersecurity #sibergüvenlik #windowslogs #logmanagement #infosec #DPUSEC #itsecurity #loganalysis

Explore how overlooked Windows event logs can reveal critical forensic details, aiding in incident detection and analysis. nasbench.medium.com/finding-forens… #Forensics #WindowsLogs
🎥 Learn how of monitor Windows event logs and custom log files in our #Checkmk video tutorial. The Windows agent handles event logs, but you can create custom rules for custom files. Watch here: checkmk.io/3PkuoEE !🔍 #Monitoring #WindowsLogs

Seeking community insights! What tools or methods do you recommend for detecting PowerView/BloodHound/SharpHound activity through Windows log events? 🕵️♂️ Share your expertise! #CyberSecurity #WindowsLogs #ThreatDetection
🎥 Learn how of monitor Windows event logs and custom log files in our Checkmk video tutorial. The Windows agent handles event logs, but you can create custom rules for custom files. 🖥️ Watch here: checkmk.io/3GoK4Su 🔍 #Monitoring #WindowsLogs #Checkmk #Tutorial
youtube.com
YouTube
Monitoring Windows Event Log and Custom Log Files with Checkmk...
🛡️ Join the workshop on "Attacks & the Windows Logs" at #Hacktivity2023 and uncover common techniques employed by attackers during lateral movement. Get your ticket: t.ly/5xuMP #Hacktivity #WindowsLogs

Windows Event Logs Deep Dive - tryhackme.com/room/windowsev… #ethicalhacking #eventviewer #windowslogs
Windows Logging for SOC on @TryHackMe transformed my Windows threat hunting! Correlating Event IDs for brute-force detection, tracking suspicious account creation, and analyzing PowerShell history felt genuinely rewarding. #WindowsLogs #SOC #ThreatHunting

“Ekip arkadaşımız Ceyda Ünsal’ın yazdığı ‘Windows Log Dosyalarının Güvenliği ve Yönetimi’ blog yazısını web sitemizden okuyabilirsiniz! 🥳 Blog 👉🏻 dpusec.org/windows-gunluk… #cybersecurity #sibergüvenlik #windowslogs #logmanagement #infosec #DPUSEC #itsecurity #loganalysis

Windows logs are your first line of defense. 🔒 Learn how to monitor Windows logs for security threats and detect attacks before they spread. 👉businesspcsupport.com/how-to-use-win… #CyberSecurity #WindowsLogs #InfoSec

🛡️ Join the workshop on "Attacks & the Windows Logs" at #Hacktivity2023 and uncover common techniques employed by attackers during lateral movement. Get your ticket: t.ly/5xuMP #Hacktivity #WindowsLogs

🛠️ Understanding Windows Event Logs for Cybersecurity Professionals 🛠️ Windows Event Logs play a crucial role in monitoring system activity, detecting security incidents, and troubleshooting issues. Here’s a quick breakdown of the key log types:#CyberSecurity #WindowsLogs #SIEM

Just concluded a 14-slide breakdown on detecting brute-force attacks using Windows Event Logs. 🧠 Event ID 4625, 4624 & 4672 decoded 🔐 Lockout policies, MFA, SIEM alerts 🔗 link drive.google.com/file/d/1LZ7PN4… #SOCAnalyst #WindowsLogs #ThreatDetection #IncidentResponse #SIEM #BlueTeam




Diving Deeper to Understand the Windows Event logs for Cyber Security Operation Center (SOC) bit.ly/343XXTa #SOC #windowslogs

🎥 Learn how of monitor Windows event logs and custom log files in our #Checkmk video tutorial. The Windows agent handles event logs, but you can create custom rules for custom files. Watch here: checkmk.io/3PkuoEE !🔍 #Monitoring #WindowsLogs

Something went wrong.
Something went wrong.
United States Trends
- 1. Colts 35.2K posts
- 2. Chiefs 71K posts
- 3. Giants 79.6K posts
- 4. Gibbs 15.2K posts
- 5. Jameis 39.3K posts
- 6. Lions 57.2K posts
- 7. Steelers 50.1K posts
- 8. Bears 65.7K posts
- 9. JJ McCarthy 7,176 posts
- 10. Mahomes 17.9K posts
- 11. Vikings 29.5K posts
- 12. #OnePride 5,009 posts
- 13. Tomlin 7,183 posts
- 14. Shane Bowen 2,412 posts
- 15. Ravens 26.8K posts
- 16. Tony Romo 3,568 posts
- 17. AJ Brown 4,247 posts
- 18. Daniel Jones 3,451 posts
- 19. Bengals 22.1K posts
- 20. Patriots 100K posts